https://www.offensive-security.com/kali-linux-vmware-virtualbox-image-download/
Any version of Kali will do; in general, I recommend the 32-bit version.
Unzip the 7-zip file into a new folder. In S214, use the VMs drive, not drive C:.
Launch VMware Player and click "Open a Virtual Machine". Browse to the folder you unzipped the VM into, and launch the VM.
To run two VMs at the same time, launch two instances of VMware Player.
nc -l -p 5555

Note: on some Linux versions you need to use
this command instead: nc -l 5555
On the Linux target machine, open another Terminal window and execute this command:
watch "netstat -an | grep 5555"
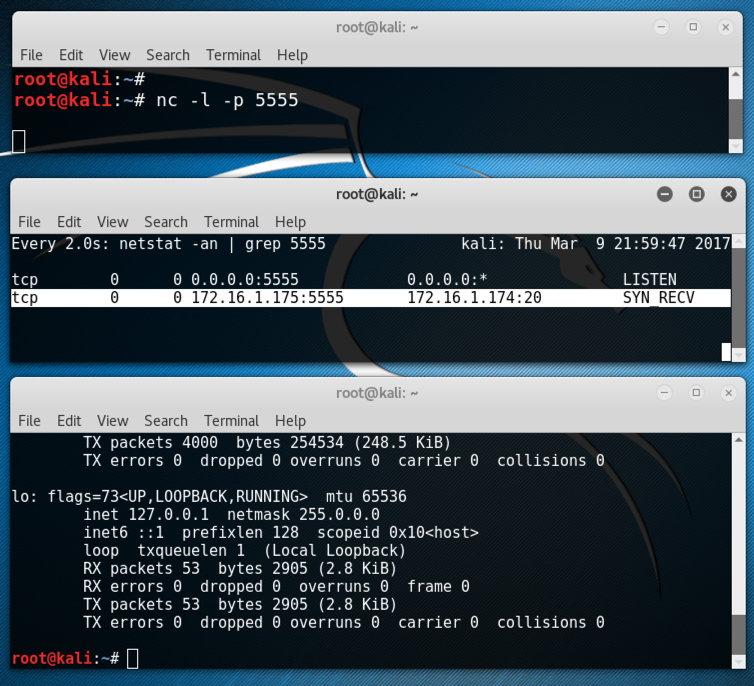
You should have two windows open now, one with netcat running, and the other running netstat. The netstat window shows a process in the LISTEN state on port 5555, as shown below on this page.
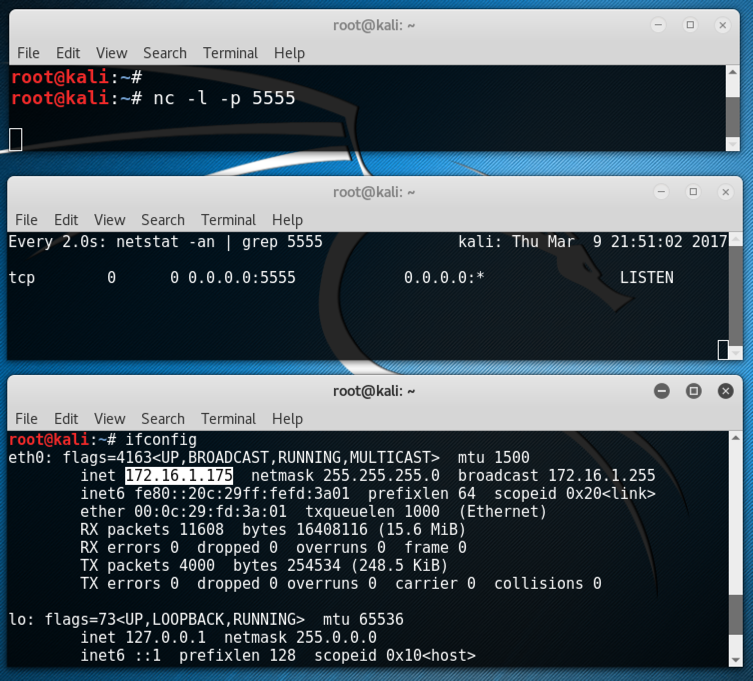
Execute this command to find your IP address.
ifconfig
This will make it easier to see scapy's output.
Then, like the Great Firewall of China, it will send a RST packet to cancel the improper connection.
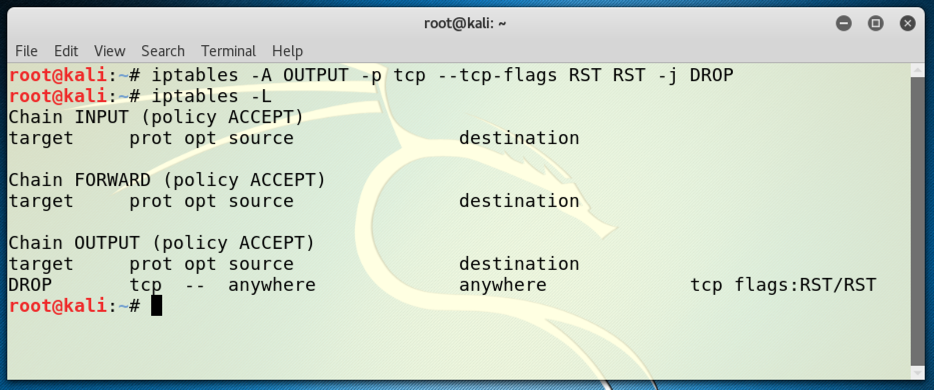
To prevent that, we need to add an iptables firewall rule.
On the Linux Sender machine, open a Terminal window. From the menu bar, click Edit, "Profile Preferences", Colors. I used "Black on light yellow". execute these commands.
iptables -A OUTPUT -p tcp --tcp-flags RST RST -j DROP
iptables -L
scapy
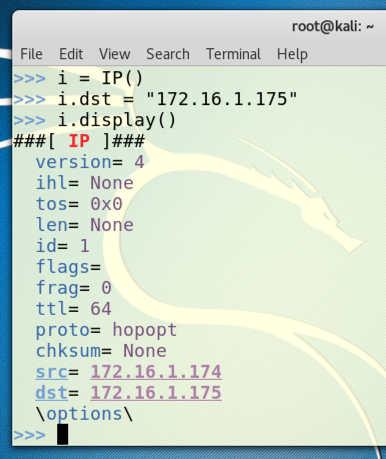
i = IP()
i.dst = "172.16.1.175"
i.display()
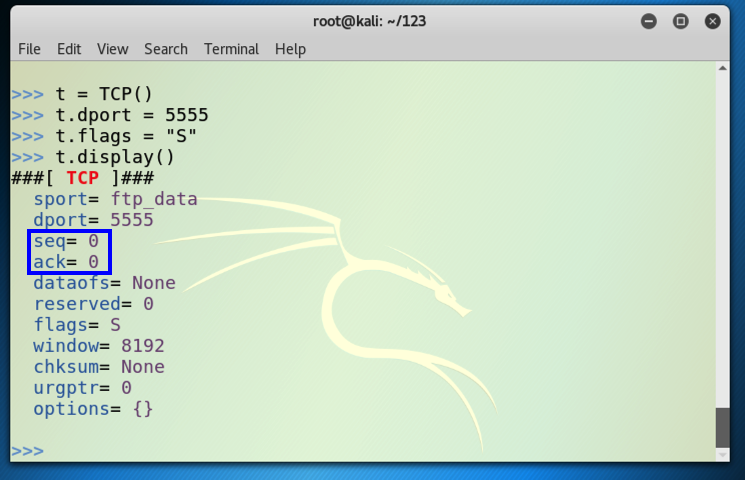
t = TCP()
t.dport = 5555
t.flags = "S"
t.display()
Note that the third character is the numeral 1, not a lowercase L:
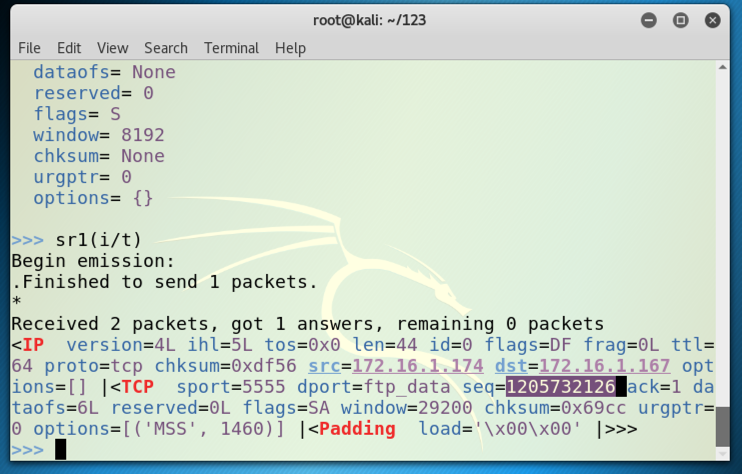
sr1(i/t)
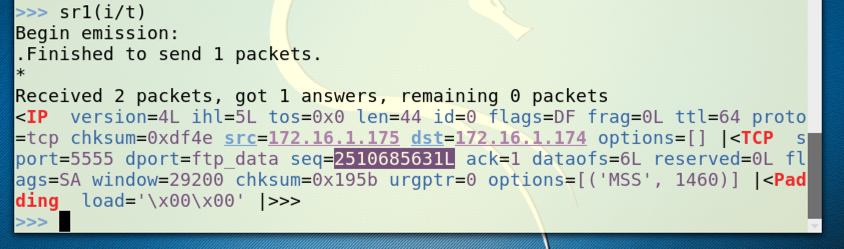
Find the seq number in the SYN/ACK reply. It's highlighted in the figure below. Later, you will add one to this number to find the ack value you must use in the ACK packet that completes the handshake.
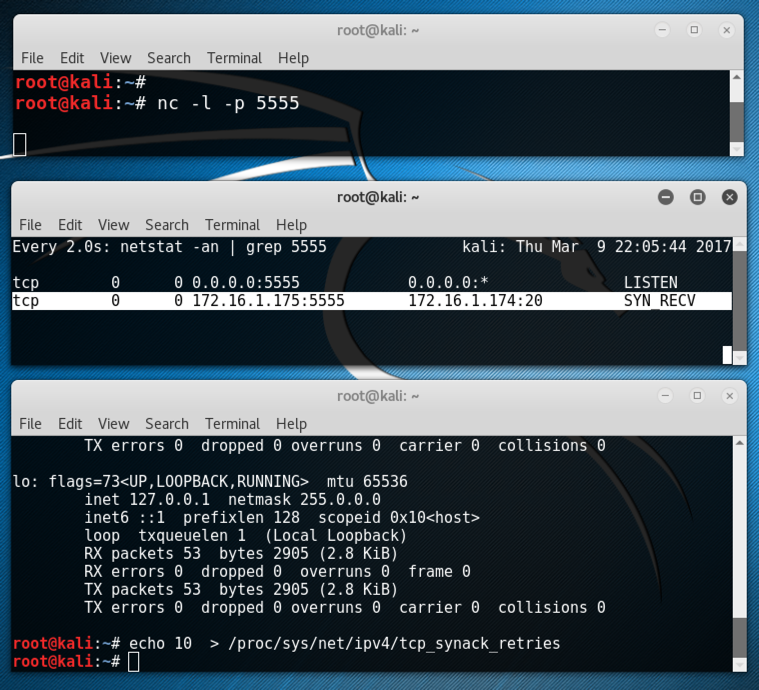
You should see a connection in the state SYN_RECV, as highlighted in the image below.
This means the Target has received a SYN, amd sent a SYN/ACK, and it is now waiting for the ACK to complete the handshake.
Wait for 60 seconds. You should see the connection time out--it will vanish from the netstat list.
This is the default setting in Kali Linux, to wait 60 seconds before giving up on the connection. You can complete the project this way if you work fast, but for most students 60 seconds isn't long enough to complete the handshake.
This setting defaults to 5, which means sessions time out after 60 seconds.
On the Linux target machine, in the third, unused Terminal window, excute this command to lengthen the timeout to 10 minutes:
echo 10 > /proc/sys/net/ipv4/tcp_synack_retries
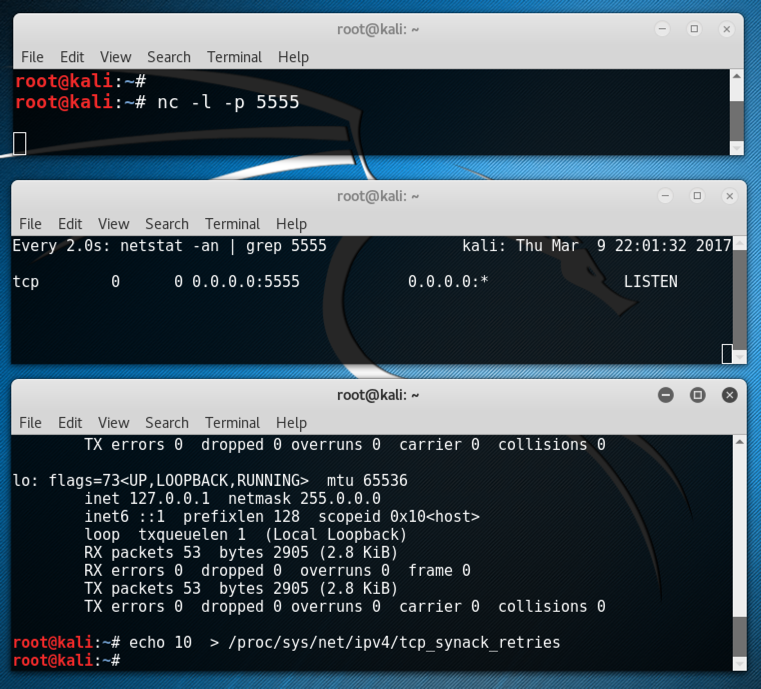
Note: this setting is not wise for normal use, because I expect it to make your machine far more vulnerable to SYN floods. But it's not permanent--when the machine restarts it will reset to the default value of 5 (one minute).
Note that the third character is the numeral 1, not a lowercase L:
sr1(i/t)
Look at your Target machine. It should now show a connection in the SYN-RECV state again:

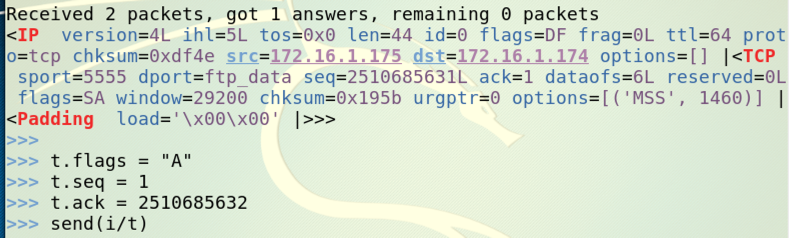
The important parts of the reply are highlighted in blue` above:
Find your seq number and add one to it. Ignore the "L" at the end.
Replace "1" with your ack number.
Replace "2510685632" with the value you calculated above; your seq value plus 1.
t.flags = "A"
t.seq = 1
t.ack = 2510685632
send(i/t)
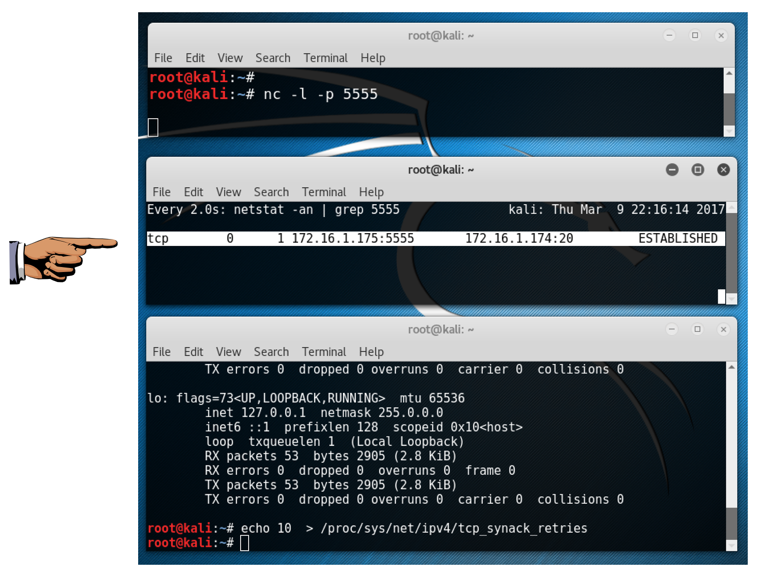
Make sure you can see the ESTABLISHED connection.
Save a screen image with the filename Proj 10 from Your Name.
Email the image to cnit.123@gmail.com with a Subject line of Proj 10 from Your Name.
http://blog.facilelogin.com/2010/12/hand-crafting-tcp-handshake-with-scapy.html
http://linux.die.net/man/7/tcp
http://www.cyberciti.biz/tips/linux-increasing-or-decreasing-tcp-sockets-timeouts.html