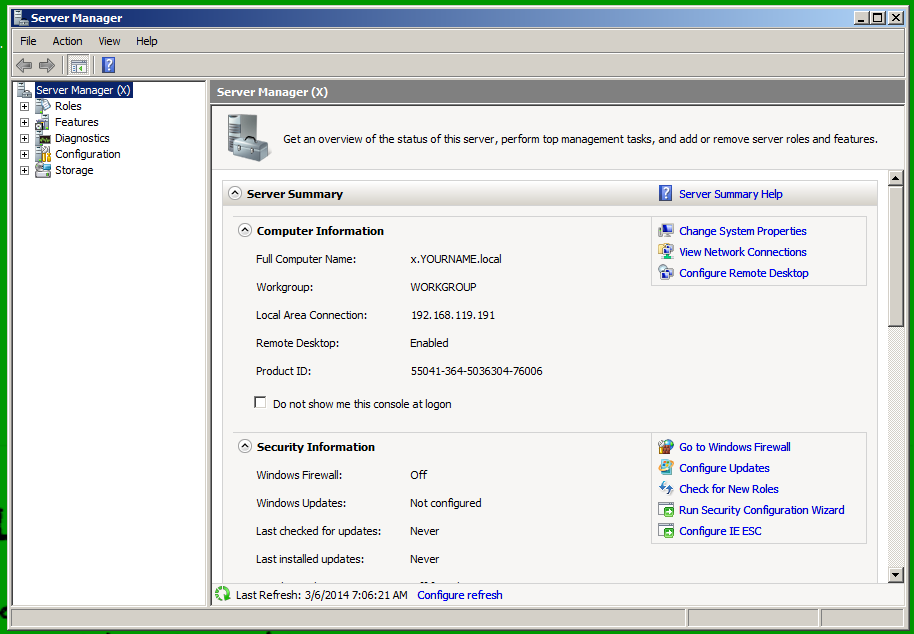
If you are using the Windows Server 2008 machine from the "S13" DVD handed out in class, log in as Administrator with a password of P@ssw0rd
In the lower right of Server Manager, in the "Security Information" section, click the "Configure IE ESC" link, as shown below.

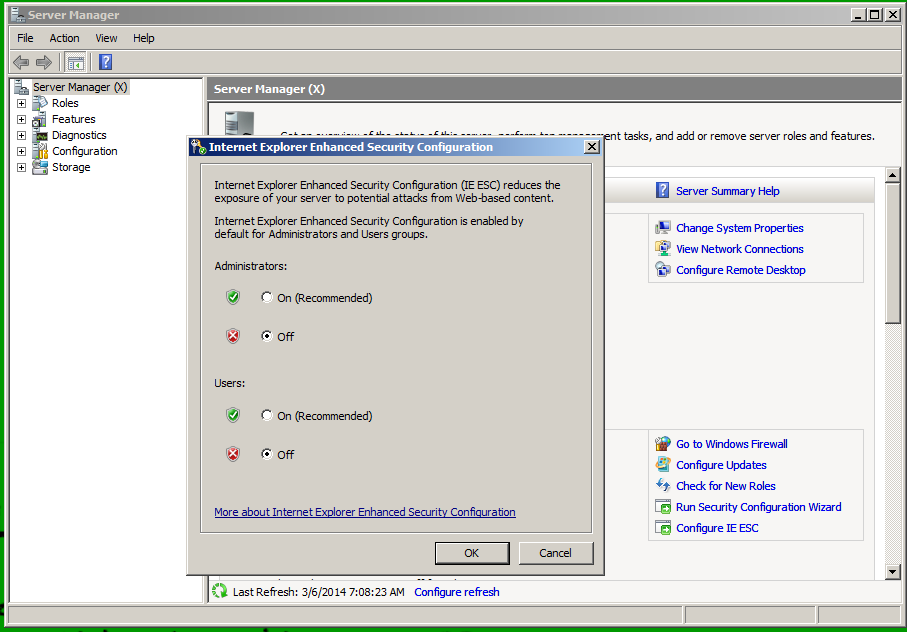
Click both Off buttons, as shown below. Then click OK.
http://www.ipbackupanalyzer.com/downloads
In the "Windows EXE build" section, click the "View releases in this category" button.
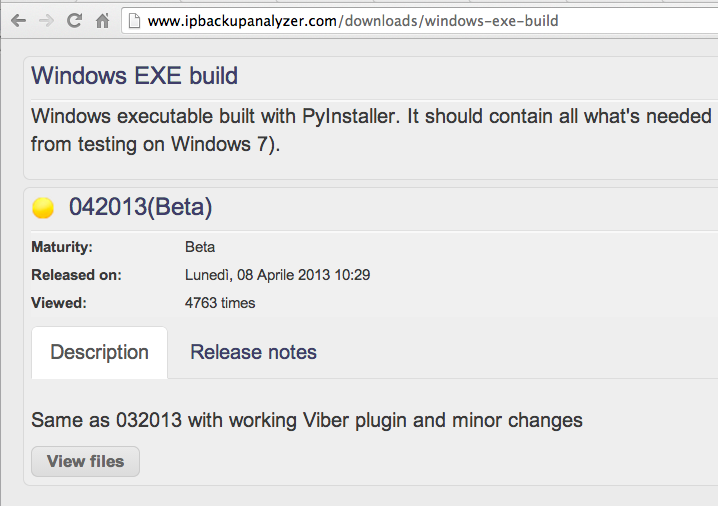
On the next page, find the latest version. When I did it, that was 042013(Beta), as shown below.
Click the "View files" button.
The next page shows the file size and hash values, as shown below.
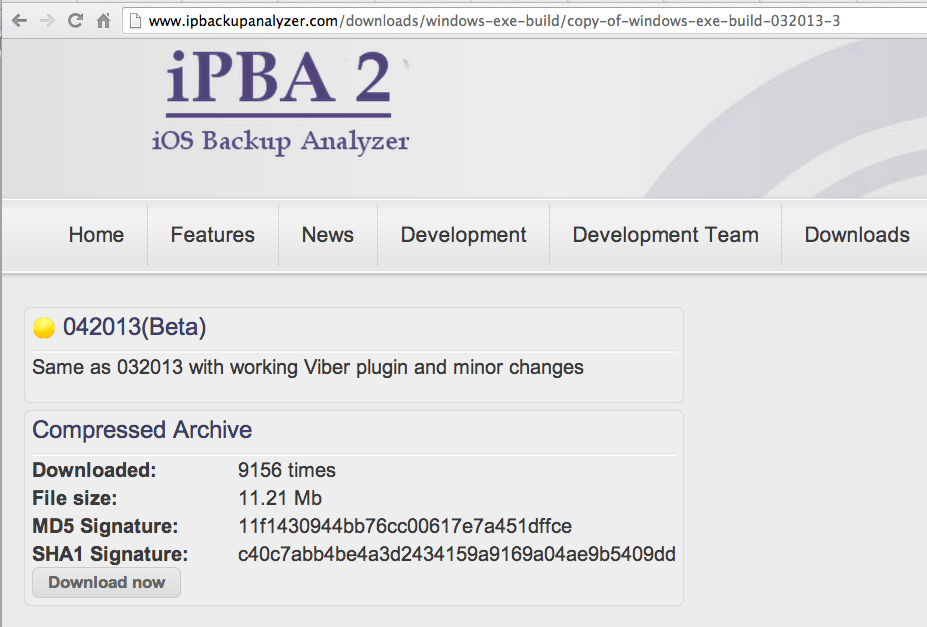
Click the "Download now" button.
http://www.slavasoft.com/hashcalc/
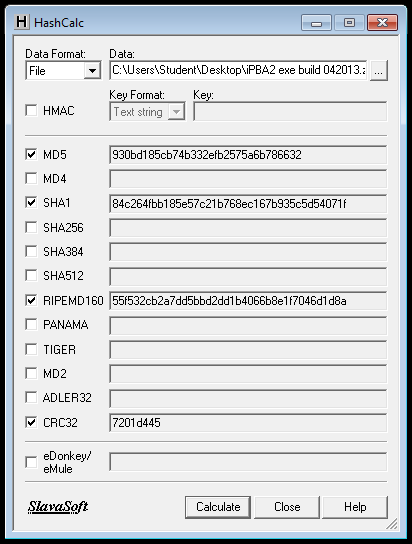
Use Hashcalc to check the SHA-1 hash value of the downloaded iPBA file.
Unfortunately, the hash did not match when I did it, as shown below. The file size is also wrong.
I suspect that the download was updated and the hash values are not accurate. Let's proceed anyway.
An "iPBA2 exe build 042013" window opens. Double-click the main folder.
Double-click the iPBA2 icon.
iPBA2 opens, as shown below.
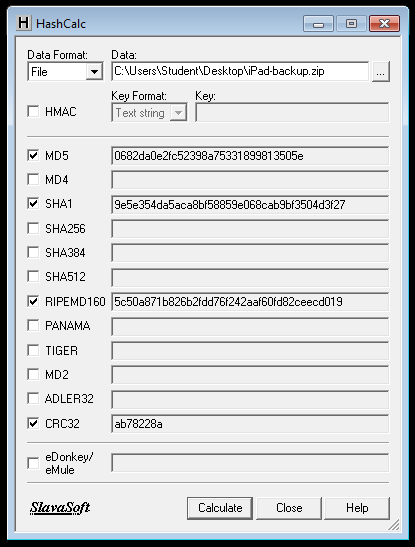
Use Hashcalc to verify the SHA-1 hash of the file. It should match the value shown below.
Right-click the iPad-backup.zip file and click "Extract All...", Extract.
Browse to your desktop, double-click the iPad-backup folder, and click the folder inside with the long hexadecimal name.
Click the "Select Folder" button.
A "Repair datbase files" box pops up, warning that iPBA2 is about to alter the evidence file. That's OK because we are using a copy, not the original file, so click Yes.
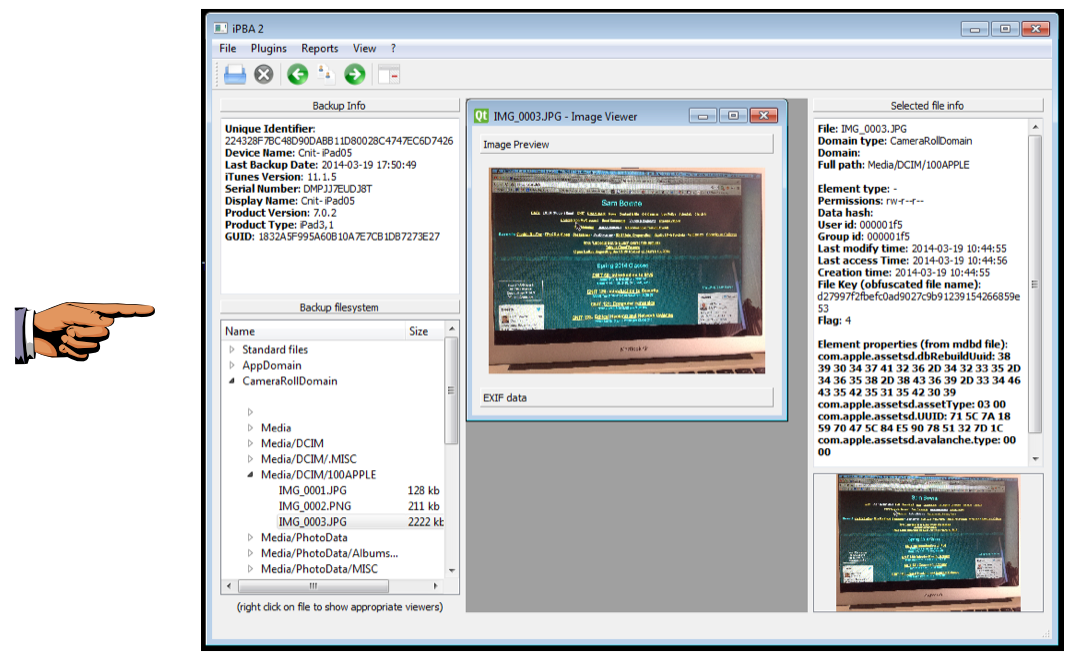
Expand the "CameraRollDomain" and hunt through the folders until you find the photo of a computer showing my Web page.
Right-click IMG_003.JPG and click "Open with image Viewer".
The image appears in the center pane, as shown below.
Press the PrntScrn key to capture the whole desktop. Open Paint and paste in the image.
Save the image as "Proj 14a from YOUR NAME".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Notice that the date and time the photo was taken appears as "DateTimeOriginal", as shown below.
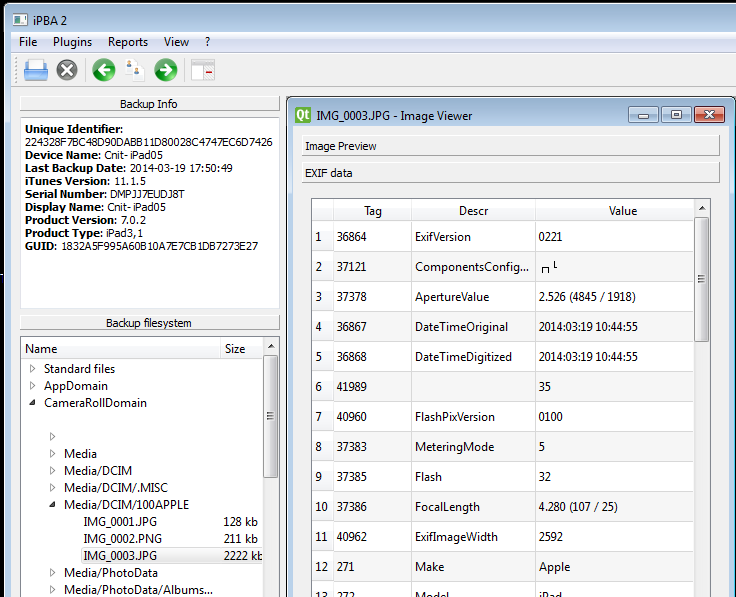
Some cameras also record the GPS location in the EXIF data, but the iPad I used didn't do that.
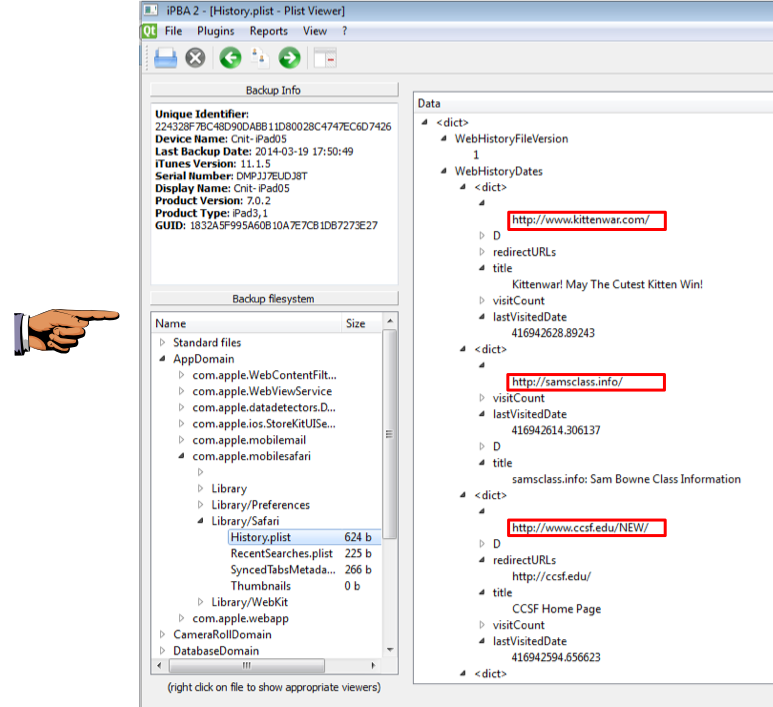
Save the image as "Proj 14b from YOUR NAME".
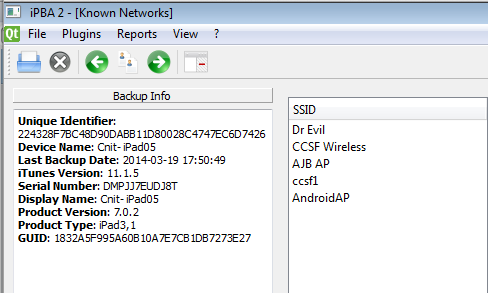
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT In iPBA2, from the menu bar, click Plugins, "Known WiFi Networks".
The "Dr Evil" network appears, as shown below.