Once the USB drive has been recognized, eject it and remove it.
http://accessdata.com/product-download/digital-forensics
On the upper right of the page, point to Resources. In the "Product Downloads" section, click "Digital Forensics".
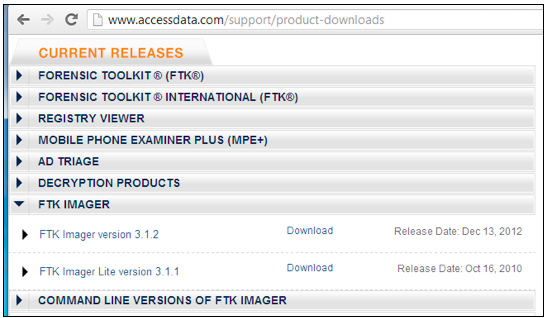
In the "Current Releases" section, expand the "FTK Imager" section, as shown below. On the "FTK Imager Lite version 3.1.1" line, click Download.
Enter your email address if you are prompted to.
Save the file in your Downloads folder.

Save the file in your Downloads folder.
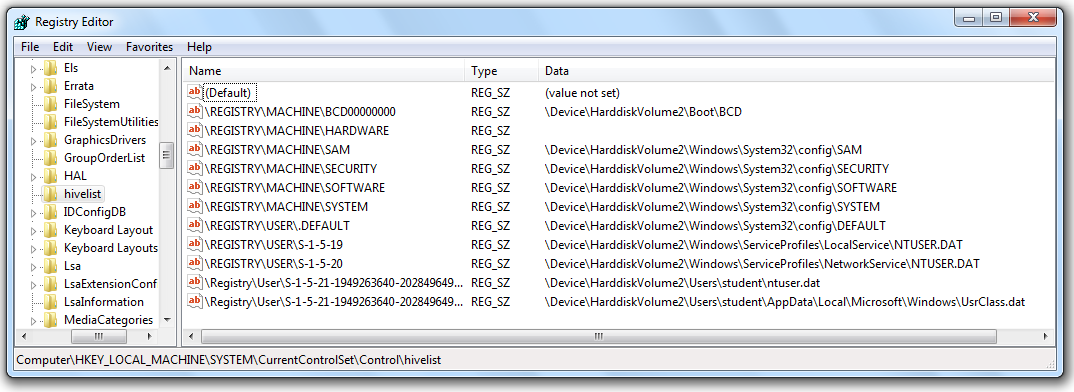
In Registry Editor, navigate to
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\HiveList
You should see a list of the files that store the Registry, as shown below. For this project, we want to capture those files, and not all the other files on the disk. FTK Imager will make that really easy!
If a "User Account Control" box pops up, click Yes.
In the "AccessData FTK Imager 3.1.1" window, click File, "Obtain Protected Files".
The "Obtain System Files" box opens. Notice the Warning at the top of this box. You are obtaining data from your own computer, not from an evidence image. At least one forensic examiner actually went to court and submitted data accidentally gathered from his own forensic workstation by ignoring this warning.
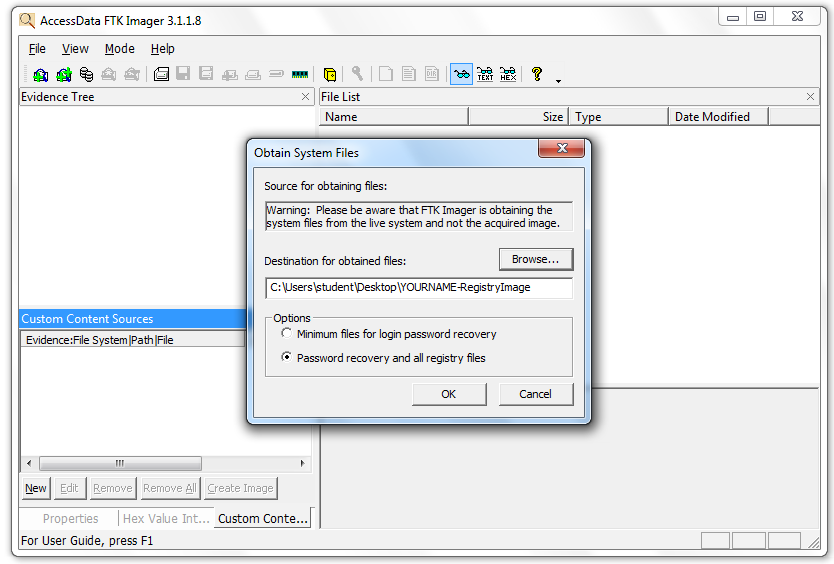
In the "Obtain System Files" box, click the Browse button and navigate to your desktop. Click the "Make New Folder" button, and name the new folder YOURNAME-RegistryImage. Select the YOURNAME-RegistryImage folder and click OK.
Click the "Password recovery and all registry files" radio button, as shown in the image above. Click OK.
Wait until the process finishes. It should only take a few seconds. Close FTK Imager.
On your desktop, open the YOURNAME-RegistryImage folder. It should contain the five files and one folder shown below. You should get used to seeing these names--they are the Hive Files, and a lot of forensics involves working with them.
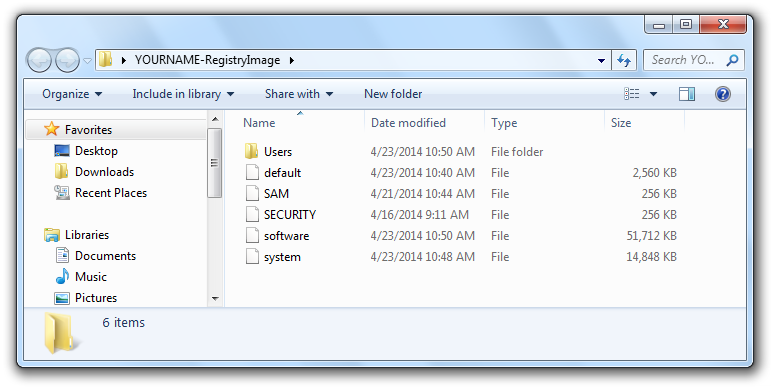
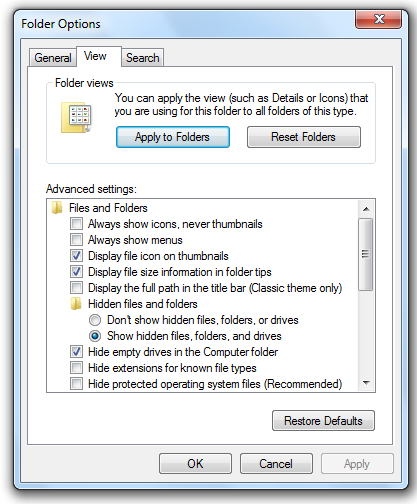
On the View tab, click the "Show hidden files, folders, and drives" button and clear the "Hide protected operating system files (Recommended)" box, as shown below.
If a "Warning" box pops up, click Yes.
In the "Folder Options" box, click OK.
On your desktop, click Start, Registry Viewer.
A box pops up saying "No security device was found." This is warning you that you are using the product in Demo mode, not the full version. Click No.
A box pops up saying "No dongle found" Click OK.
In Registry Viewer, click File, Open. Navigate to your Desktop, and open this file:
YOURNAME-RegistryImage\Users\Student\NTUSER.DAT
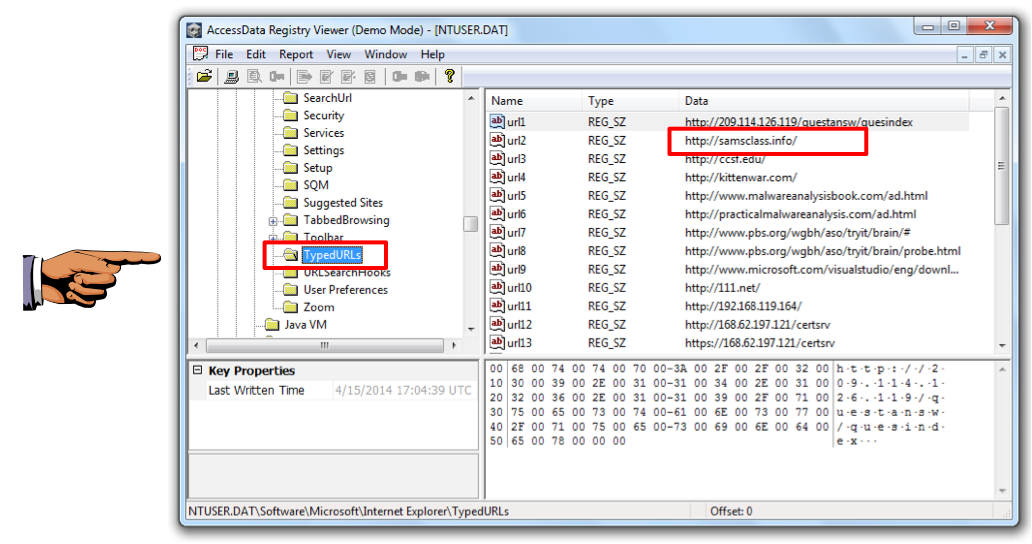
Registry Viewer is similar to REGEDIT. In the left pane, navigate to
NTUSER.DAT\Software\Microsoft\Internet Explorer\TypedURLs
Save a whole-desktop image with a filename of "Proj 17a from YOUR NAME".
In the left pane of Registry Viewer, navigate to
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist
In the left pane of Registry Viewer,
click the + sign to expand the
UserAssist key.
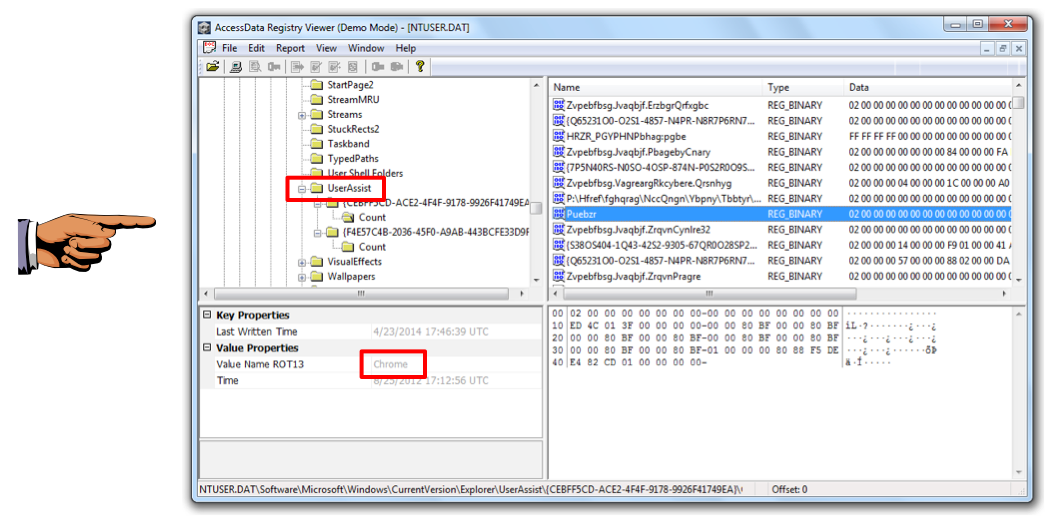
One or more subkeys with long names consisting of random letters and numbers appear, as shown below.
Expand one of the subkeys and click the Count subkey.
The upper right pane of Registry Viewer now shows strange unreadable "Name" values. Believe it or not, these are obfuscated with ROT-13--moving each letter 13 values in the alphabet, an ancient and very weak form of encryption.
Click one of the In the upper right pane of Registry Viewer, click one of the names. Look in the lower left pane to see the deobfuscated name in the "Value Properties" section, in the "Value Name ROT13" row.
Hunt through the values until you find something readable, such as "Chrome", or "Microsoft.InternetExplorer.Default", as shown below.
Save a whole-desktop image with a filename of "Proj 17b from YOUR NAME".
In a Web browser, go to
https://code.google.com/p/regripper/downloads/list
Click rrv2.8.zip. On the next page, click rrv2.8.zip. Save the file on your desktop.
In your browser, click the Back button to return to the main "regripper" page.
Click plugins20130404.zip. On the next page, click plugins20130404.8.zip. Save the file on your desktop.
On your desktop, right-click rrv2.8.zip. Click "Extract All..., Extract.
A "rrv2.8" window opens, as shown below.
On your desktop, right-click plugins20130404.zip. Click "Extract All..., Extract.
A "plugins20130404" window opens, as shown below.
Resize the windows so you can see both of them, as shown below.
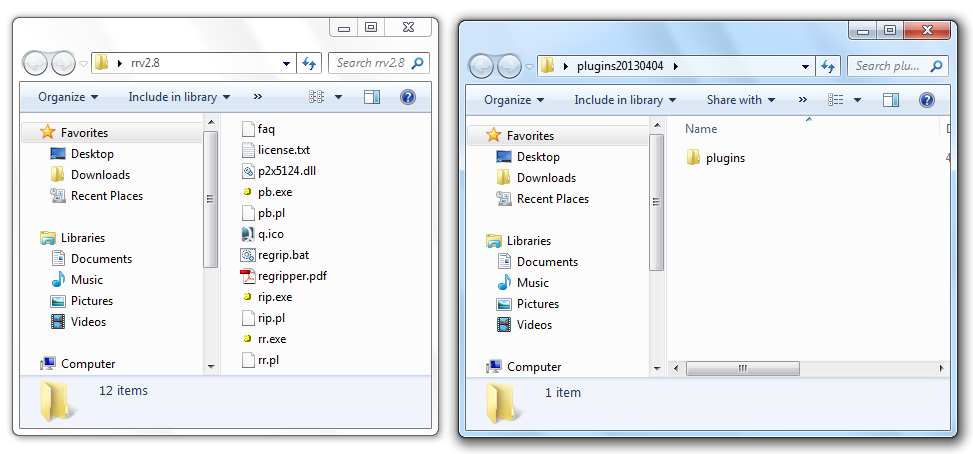
Drag the plugins folder from the "plugins20130404" window and drop it into the "rrv2.8" window.
The "rrv2.8" window should now include the "plugins" folder, as shown below.
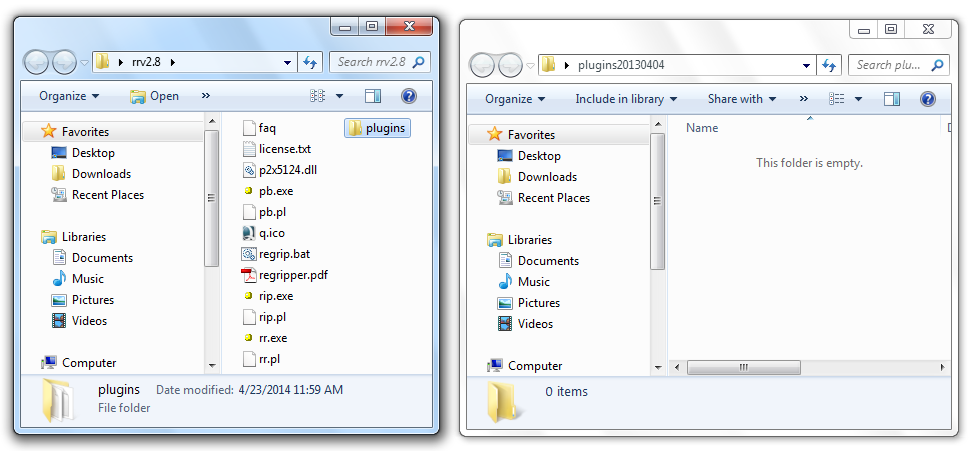
In the "rrv2.8" window, double-click rr.exe. RegRipper opens, as shown below.
In RegRipper, in the "Hive File:" line click the Browse button.
Navigate to your Desktop, and open this file:
YOURNAME-RegistryImage\Users\Student\NTUSER.DAT
In RegRipper, in the "Report File:" line click the Browse button.
Navigate to your Desktop. Enter a File name of YOURNAME-RegRipReport and click Save.
In the "Profile" line, select ntuser-all, as shown below.
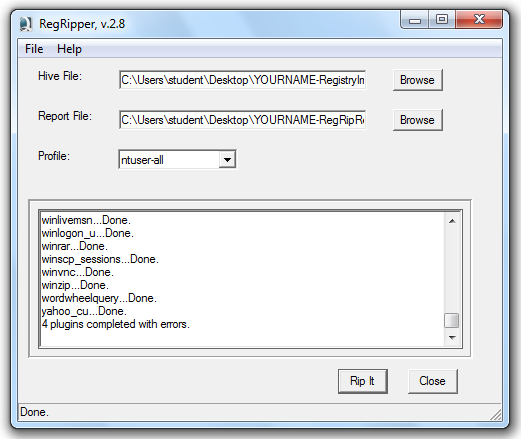
In RegRipper, click the "Rip It" button.
Messages scroll by, ending with "4 plugins completed with errors", as shown above.
Close RegRipper.
On your desktop, double-click the YOURNAME-RegRipReport file.
The report opens in Notepad.
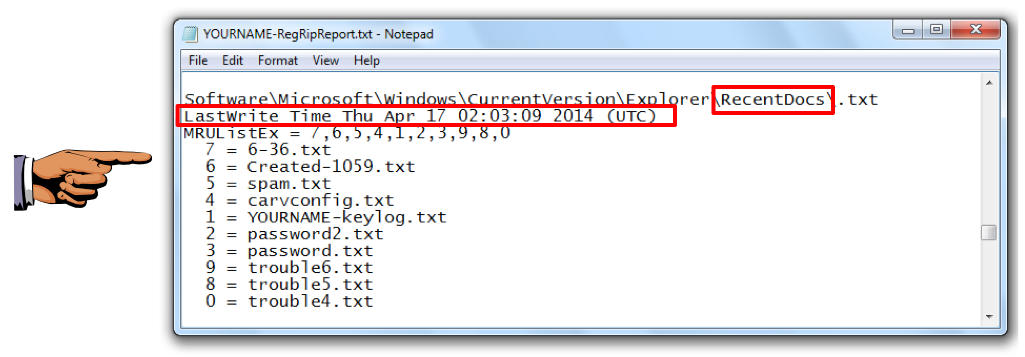
Press Ctrl+F. In the Find box, type RecentDocs\ as shown below, and press Enter.
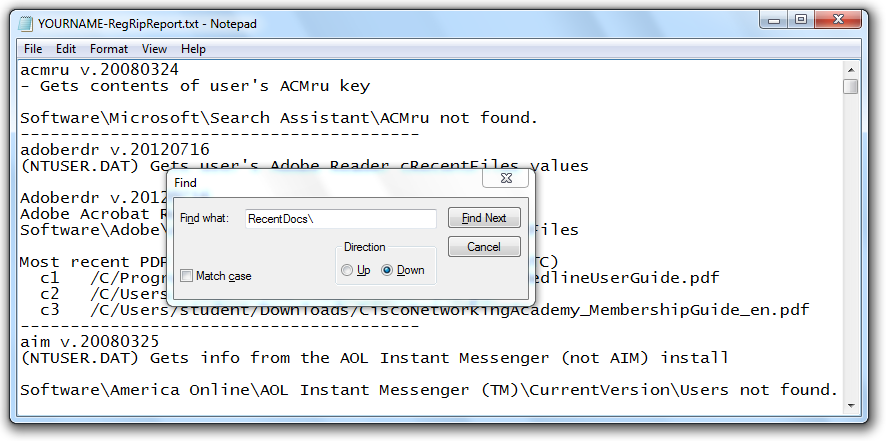
Close the Find box.
Scroll down to see some recently opened files and the "LastWrite Time", as shown below.
Save a whole-desktop image with a filename of "Proj 17c from YOUR NAME".
However, this key is not visible in an acquired registry. Instead, you will see two control sets, and you must determine which one was "Current" at the last login.
In Registry Viewer, click File, Open.
If a box pops up saying "Warning: There is currently a file open", click Yes.
Navigate to your Desktop, and open this file:
YOURNAME-RegistryImage\SYSTEM
In the left pane of Registry Viewer, click Select, as shown below:
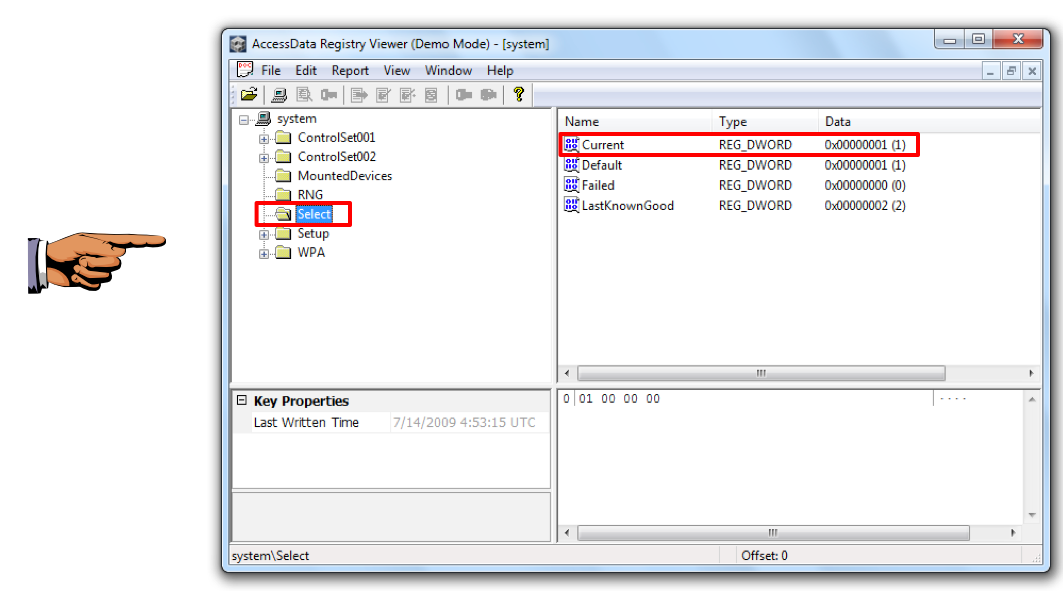
In the upper right pane, you see four values:
Save a whole-desktop image with a filename of "Proj 17d from YOUR NAME".
In Registry Viewer, click File, Open.
If a box pops up saying "Warning: There is currently a file open", click Yes.
Navigate to your Desktop, and open this file:
YOURNAME-RegistryImage\SYSTEM
In the left pane of Registry Viewer, navigate to
SYSTEM\ControlSet001\Enum\USBSTOR
(If your Current Control Set is 2, go to
ControlSet002 instead.)
In the left pane of Registry Viewer, click the + sign to expand the USBSTOR key.
One or more subkeys with long names appear, as shown below.
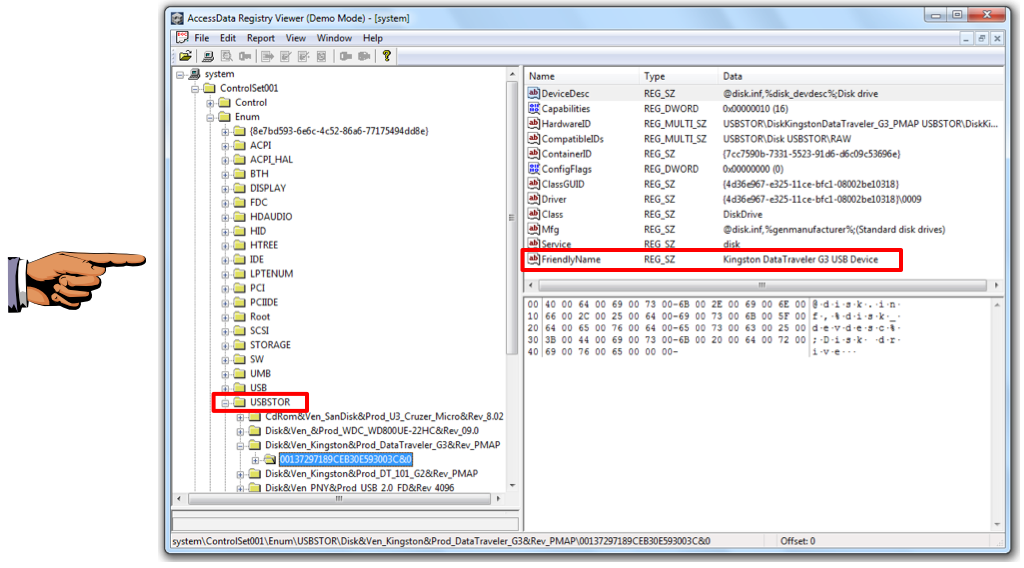
Expand one of the subkeys and click its long numerical subkey.
In the upper right pane of Registry Viewer, find the "FriendlyName value.
This should be a readable brand name of the device, as shown below.
Save a whole-desktop image with a filename of "Proj 17e from YOUR NAME".