http://technet.microsoft.com/en-us/sysinternals/bb897439
Click the "Download Strings" link.
Save the Strings.zip file on your desktop. Unzip it, and copy strings.exe to the C:\Windows\System32 folder.
http://samsclass.info/121/proj/message.exe
Save the message.exe file on your desktop.
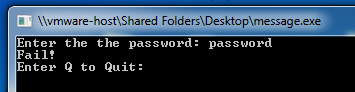
A box opens, with the message "Enter the password", as shown below:

If you see a message saying "This application has failed to start because MSVCR100D.dll was not found", download that file here, and put it in the same folder as message.exe:
If you try a password, you see the message "Fail!".
Your task is to find the correct password. Guessing is impractical, but finding the password should be easy with Strings.
Type Q and press Enter to close the message.exe box.
On your desktop, right-click message.exe and click Copy.
In the C:\Temp window, right-click and click Paste.
Now you have a copy of message.exe in C:\Temp for analysis.
Open a Command Prompt window. Execute these commands:
cd \Temp
strings message.exe > s.txt
notepad s.txt
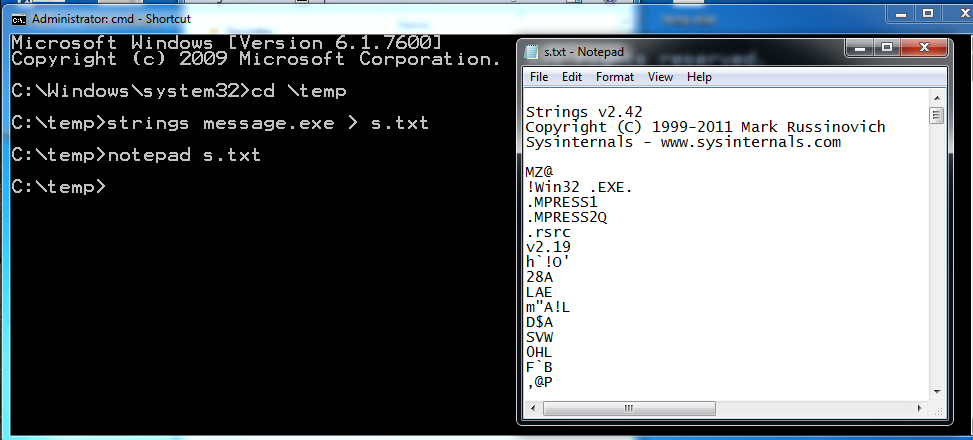
Hunt through this file and look for likely candidates for the password. There are only fragments--the password cannot be seen.
In the "Open File - Security Warning" box, click Run.
A box opens, with the message "Enter the password".
The "Enter the password" message is readable. That suggests that the image of the running program in RAM has readable strings, even though the disk file message.exe does not.
So to find the password, we'll analyze the RAM image.
Click the "Locally archived copy" link.
Download the Bin_LordPE_2010-6-29_3.9_LordPE_1.41_Deluxe_b.zip file. Right-click the file and click "Extract All...", Extract. Two more Zip archives appear in a folder, as shown below:
Right-click the LPE-DLX_1.4.zip file and click "Extract All...", Extract.
A folder appears, as shown below. Double-click the LordPE.EXE file.
If an "Open File - Security Warning" box pops up, click Run.
LordPE opens, showing all the currently running processes, as shown below.
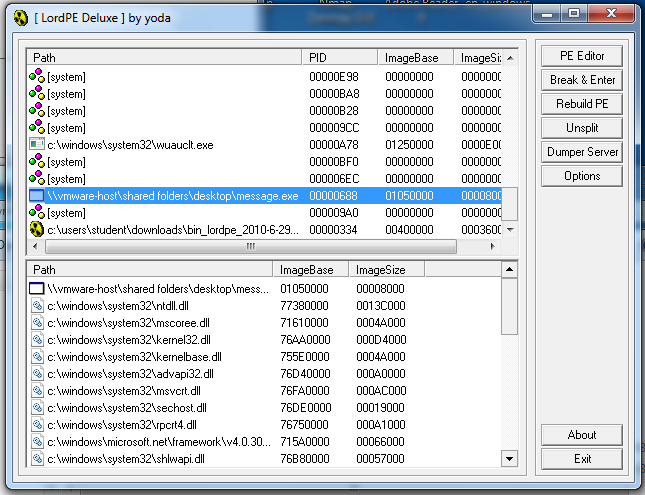
Scroll down and find the "message.exe" process, as shown above. The folder path on the left will be different, but it should end in "message.exe".
Right-click the "message.exe" line and click "Dump Full...", as shown below:
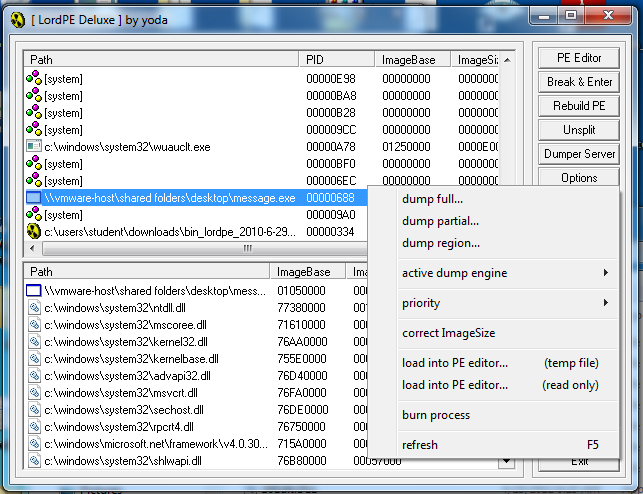
A "Save As" box appears. Save the file on your desktop with the name dumped.exe
In a Command Prompt window. Execute these commands:
cd \Temp
strings dumped.exe > s.txt
notepad s.txt
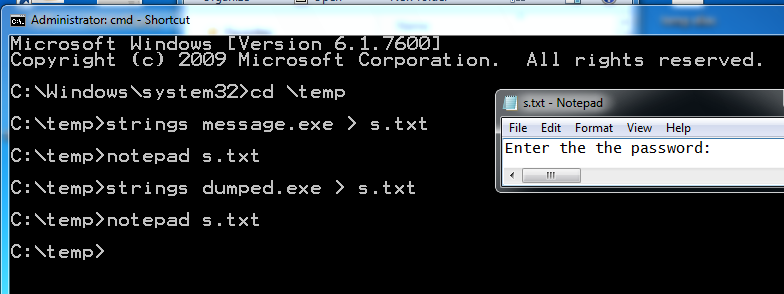
Now all the strings are visible. Find the "Enter the password". message, as shown above, and look for the password.
When you find it, enter it into the running message.exe box to see the secret message, as shown below:
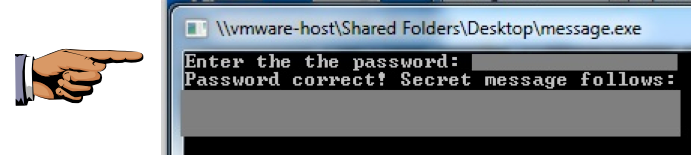
Make sure the secret message is visible.
Save this image with the filename Proj X14 from YOUR NAME
I made the executable with Visual Studio Express, following these excellent tutorials:
http://msdn.microsoft.com/en-us/library/dd492171.aspx
I packed it with MPRESS:
http://www.matcode.com/mpress.htm