http://technet.microsoft.com/en-us/sysinternals/bb897439
Click the "Download Strings" link.
Save the Strings.zip file on your desktop. Unzip it, and copy strings.exe to the C:\Windows\System32 folder.
https://technet.microsoft.com/en-us/sysinternals/dd996900.aspx
Click the "Download ProcDump" link.
Save the Procdump.zip file on your desktop. Unzip it, and copy procdump.exe and procdump64.exe to the C:\Windows\System32 folder.
https://www.teamviewer.com/en/
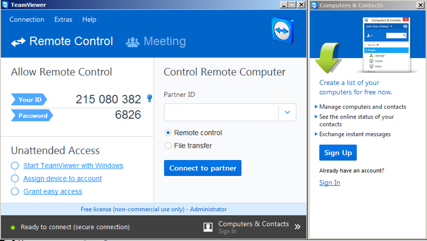
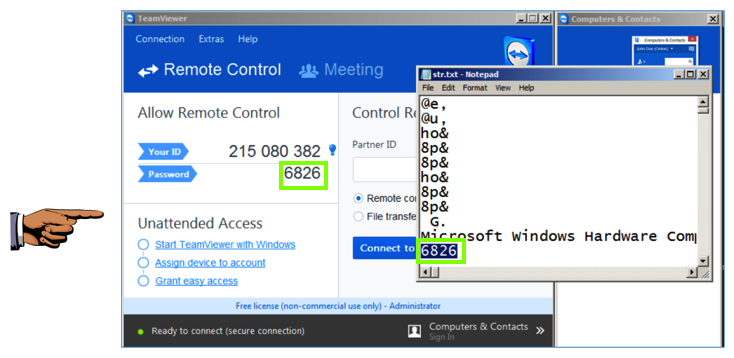
Click the "Download Teamviewer" button. Install the software with the default options. TeamViewer opens, as shown below, showing an ID and Password.

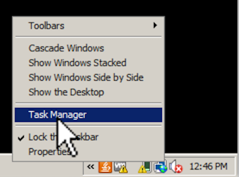
In Task Manager, cick the Process tab. From the menu, click View, "Select Columns...".
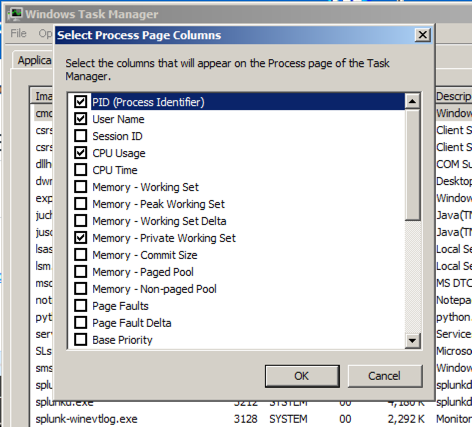
In the "Select Process Page Columns" box, check "PID (Process Identifier)", as shown below. Click OK.
Find the TeamViewer.exe process, as shown below. Make a note of it's PID. In the image below, the PID was 2296, but yours will be different.
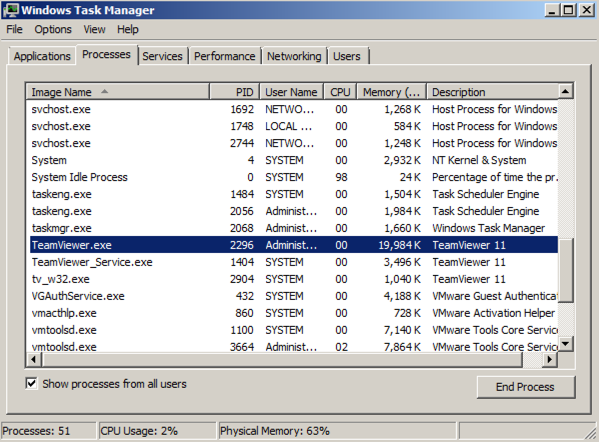
If you don't see the word "Administrator" in the title bar, you haven't successfully opened the correct window. Microsoft changes the procedure in each Windows version--Google how to open it for your version of Windows.
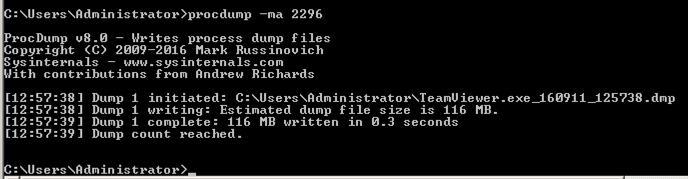
procdump -ma 2296
Procdump finishes, producing a memory capture file only 116 MB in size, as shown below.
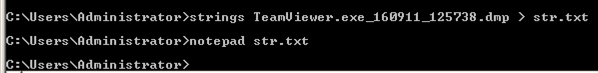
The first command extracts the readable strings from the RAM capture and puts them in a file named "str.txt".
The second command opens "str.txt" in Notepad.
strings TeamViewer.exe_160911_125738.dmp > str.txt
notepad str.txt
After a few seconds, the file appears in Notepad. In Notepad, click Edit, Find.
Search for your TeamViewer password. You should find it, as shown below.
Click the host computer's desktop. Press Shift+PrntScrn key to capture the entire desktop.
YOU MUST SUBMIT A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Save this image as a PNG file, named "Proj X7 from YOUR NAME"
Posted 9-11-16
modified 9-14-16
Sam Bowne