root with password toor
startx
cd /pentest/web/w3af
./w3af_gui
w3af starts with a pretty GUI. When it asks whether you want to update w3af, click No. (Updating is probably a good idea, but not necessary for this project. I used revision 4287 and it worked.)
In the "Update Report" window, click the OK button.
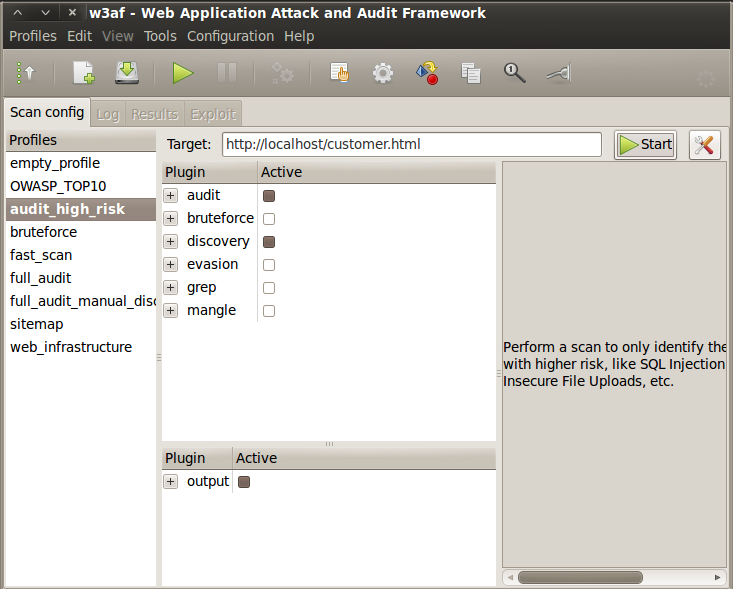
In the main w3af window, on the left side, click "audit_high_risk". Click in the "Target:" field and enter this URL:
http://localhost/customer.html
Your screen should look like the image below:

Click the Start button. The scan should only take a few seconds, and find the "Blind SQL injection", as shown below on this page:
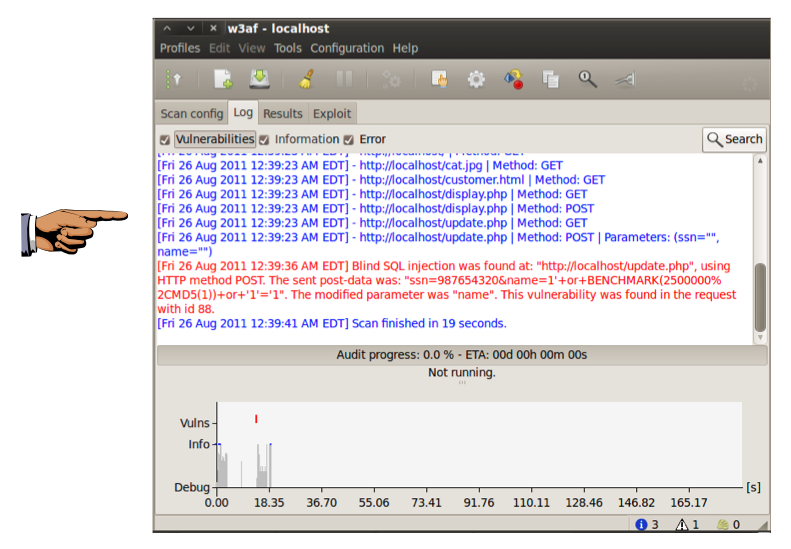
Save this screen shot with a filename of Proj 4 from Your Name.
Email the image to cnit.122sam@gmail.com with a subject of "Project 4 from YOUR NAME".