The developer provides a free version, which is detected by antivirus products, but at one point the Poison Ivy developer ("Jonas") was offering custom-built versions guaranteed to avoid antivirus detection.
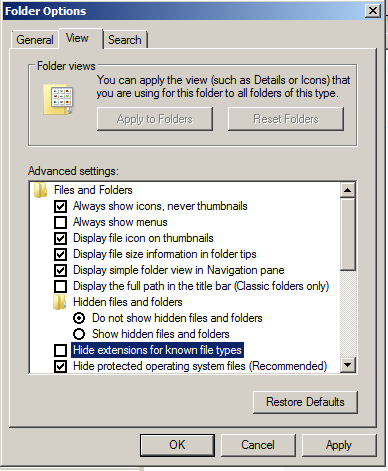
Click Organize, "Folder and Search Options".
Clear the "Hide extensions for known file types" box, as shown below.
Click OK.

In the Command Prompt window, enter the IPCONFIG command and press the Enter key. Several IP addresses appear.
Find the adapter that goes to your LAN. In S214, it's the adapter with an IP address starting with "192.168.1". Make a note of that IP address.
Click Downloads.
Alternative Download Location
If that page is blocked, which it is at CCSF, download it here. This is a 7-zip encrypted archive with the password of sam
Download the latest version.
Save the PI2.3.2.rar file on your desktop.
On your desktop, right-click the PI2.3.2.rar file.
Click 7-Zip, Extract to "PI2.3.2\".
When the file is extracted, open the PI2.3.2 folder and double-click the "Poison Ivy 2.3.2.exe" file.
Troubleshooting
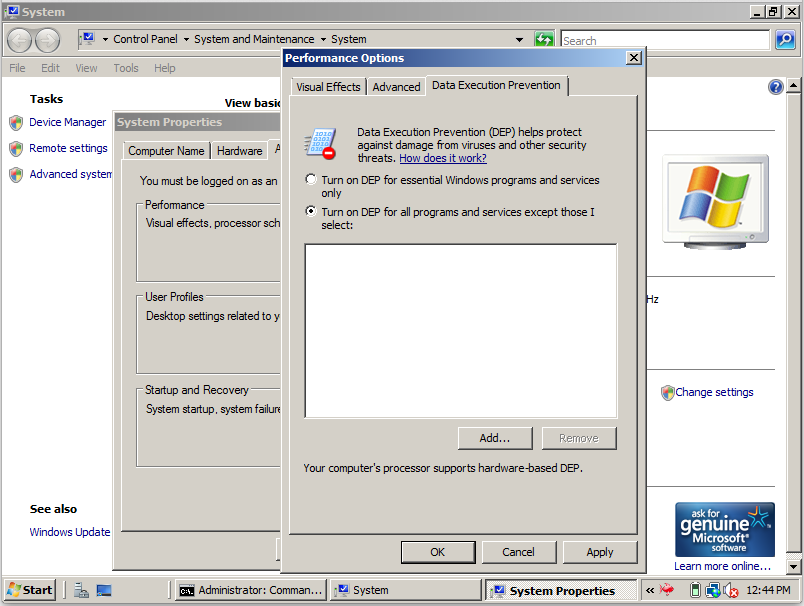
If Poison Ivy refuses to launch at all, and a message says it "has stopped working", Windows Data Execution Prevention (DEP) may be blocking it.To turn off DEP, go into Advanced System Settings as you did in project 2.
If the DEP is set as shown below, it's wrong. Set it to "Turn on DEP for essential Windows programs and services only".
Then restart your Windows server.
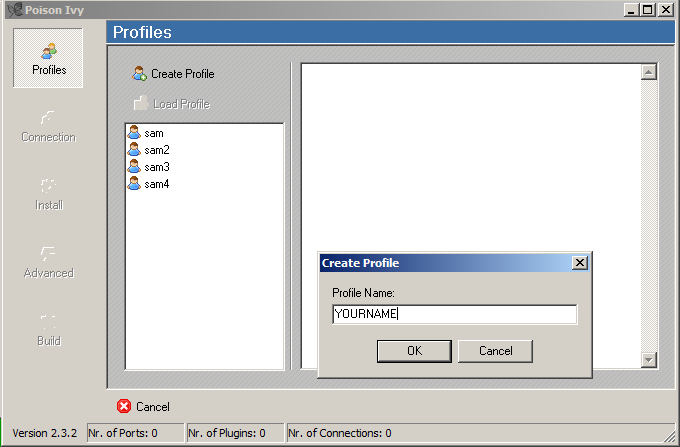
A "Profiles" screen appears, as shown below.
Click "Create Profile". Enter your name in the box and click OK.
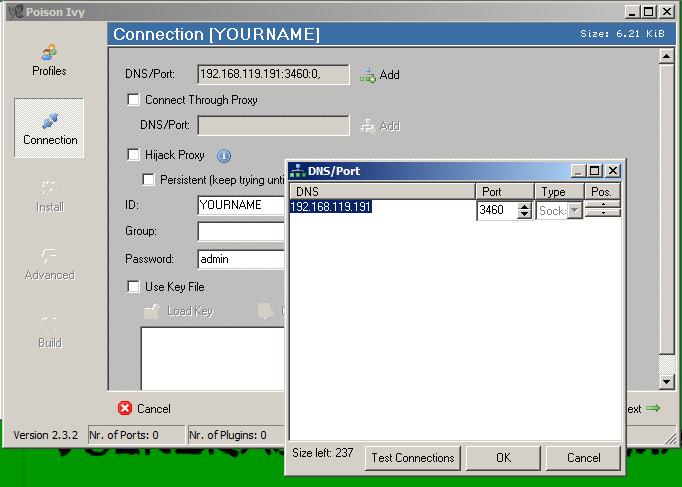
In the "Connection" box, change the address in the DNS/Port box from "127.0.0.1" to your real IP address, as shown below.
This is the Command & Control (C&C) server for your bots. It will be hardcoded into the Trojan.
Click Add. A "DNS/Port" box opens. Click your IP address to highlight it.
In the "DNS/Port" box, click OK.
In the lower right of the "Poison Ivy" window, click Next.
In the "Install" section, you can make the trojan more stealthy.
For now, leave the settings unchanged and click Next.
In the "Advanced" page, don't change anything. The "Key logger" is tempting, but it froze my target when I tried to use it.
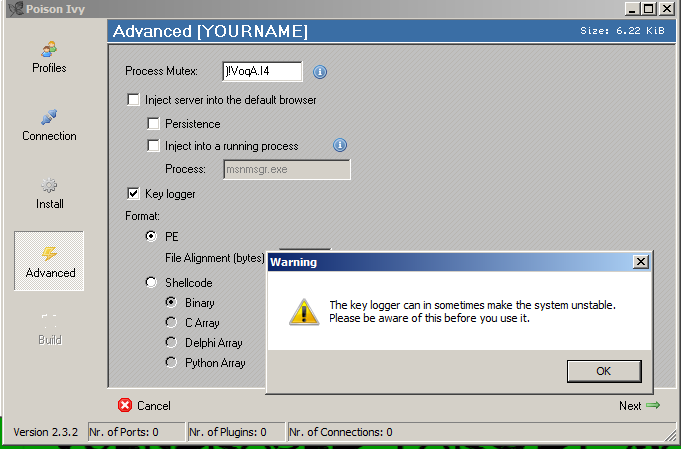
Click Next.
On the "Build" page, in the lower right, click Generate.
A "Save As" box pops up.
Save the trojan as YOURNAME.exe on your desktop.
In the "Poison Ivy" window, click OK.
A page appears, showing options to change the port, or add a password.
Leave everything unchanged and click Start.
A "Poison Ivy - [Listening on Port: 3460 (Connections: 0)]" window appears, as shown below.
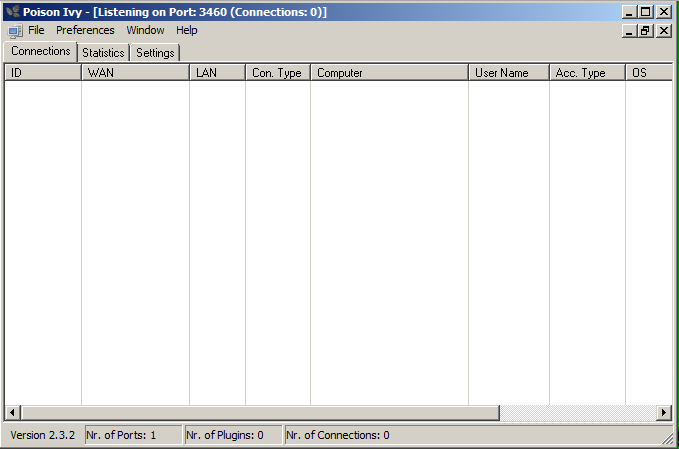
Open a Command prompt and ping your C&C server. If you don't get responses, you must troubleshoot your networking before proceeding.
Move the YOURNAME.exe file from the C&C server to the target machine. You should be able to drag and drop the file from one desktop to another. If that fails, use email, or a USB stick, or shared folders.
On the target machine, double-click the YOURNAME.exe file.
This machine is now your bot, under your control.
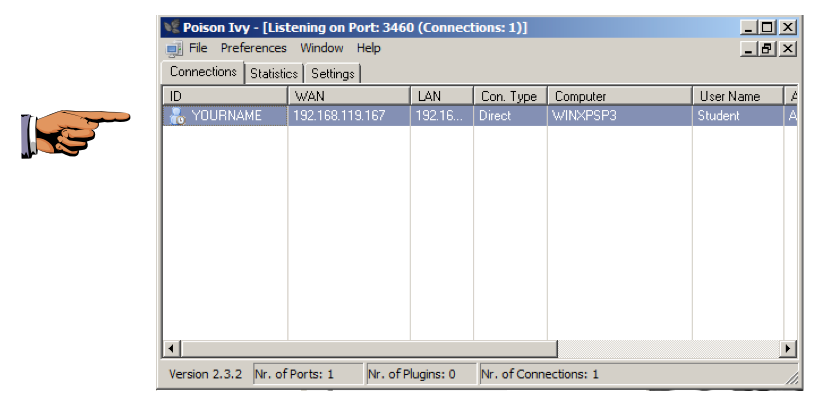
Click the taskbar at the bottom of your host Windows 7 desktop, to make the host machine listen to the keyboard, instead of the virtual machine.
Press the PrintScrn key in the upper-right portion of the keyboard. That will copy the whole desktop to the clipboard.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
On the host machine, not the virtual machine, click Start.
Type mspaint into the Search box and press the Enter key.
Click in the untitled - Paint window, and press Ctrl+V on the keyboard. The desktop appears in the Paint window.
Save the document with the filename "YOUR NAME Proj 11a", replacing "YOUR NAME" with your real name.
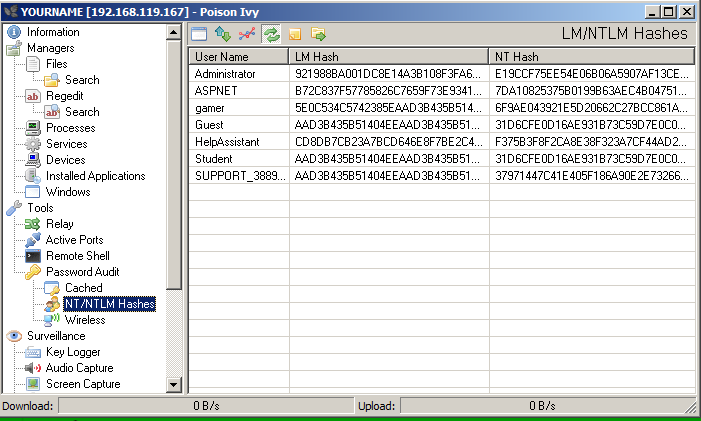
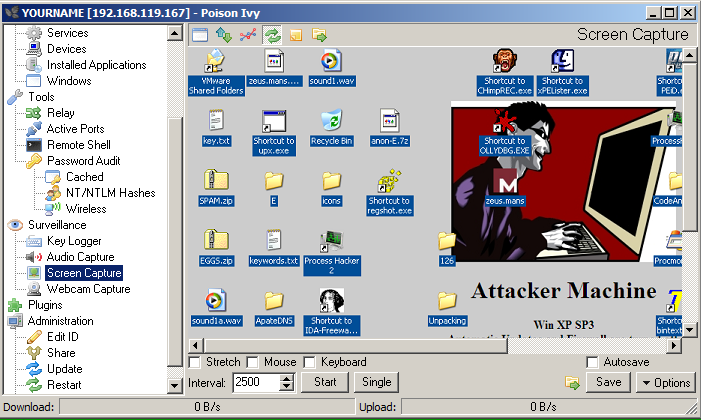
A box appears showing all the things you can do to the target, as shown below.
Try out the options. Here are the ones that worked best for me.
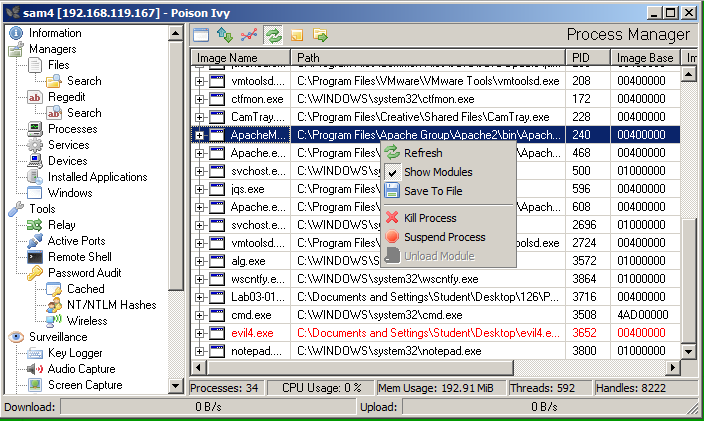
Send a Cc to yourself.
Last Modified: 12:32 pm 3-22-14
http://www.darkztar.com/forum/showthread.php?13696-Guide-to-Poison-Ivy-(a-RAT)
http://dwaterson.com/2013/04/14/a-rat-named-poison-ivy/
http://www.securityweek.com/poison-ivy-kit-enables-easy-malware-customization-attackers
poison-ivy RAT in vmware xp -ROOTRULERZ - YouTube