ifconfig
ping 172.16.1.203
Press Ctrl+C to stop the pinging.
wireshark
In the lower left of the Wireshark window, under the Start button, click eth0 to highlight it.
Click the Start button.
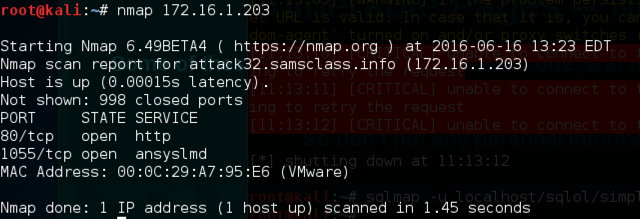
nmap 172.16.1.203

tcp.port==80
The Info column should show this pattern of three packets, as shown below:
[SYN]
[SYN, ACK]
[RST, ACK]
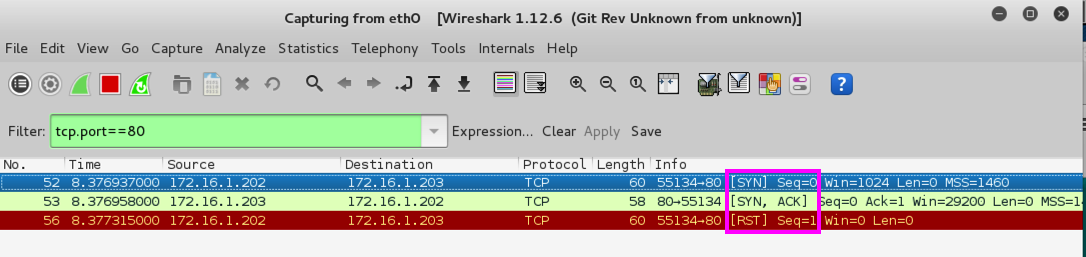
This is an incomplete TCP three-way handshake, terminated prematureky by a RST.
Last Modified: 3:22 pm 9-12-13
Modified for NETLAB 6-16-16