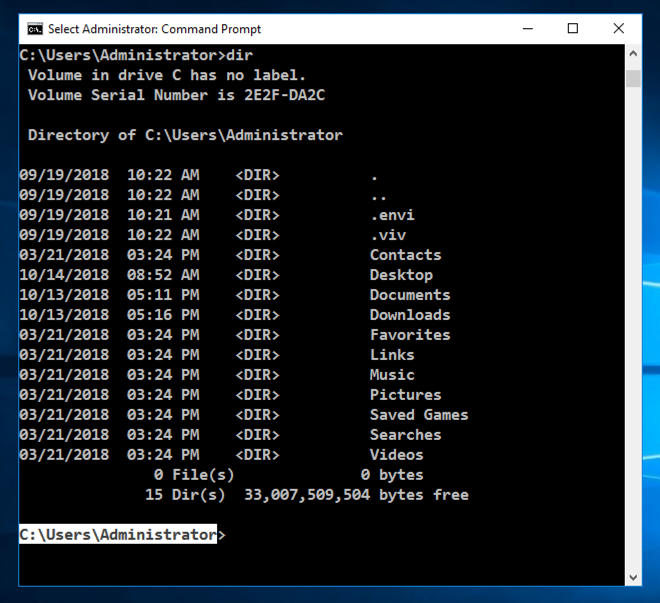
In the Command Prompt window, execute this command:
dir
Your working directory is at its default starting value; your home directory, which is usually C:\Users\username. The working directory appears at the start of every prompt, before the > character, as highlighted in the image below.
In Windows, "directories" are also called "folders".

mkdir steve
cd steve
dir
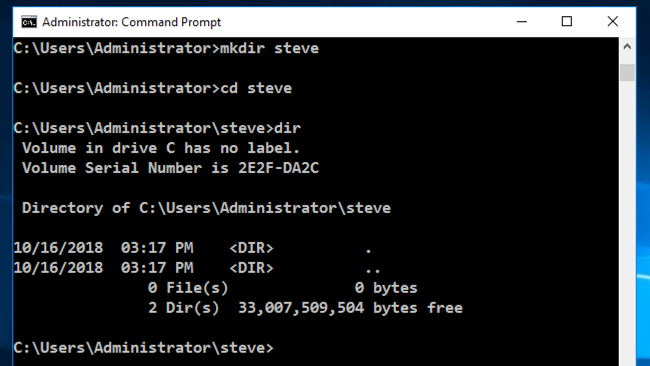
echo MARK > stevefile
dir
type stevefile
The new file appears in the directory list.
The "type" command displays the contents of the "stevefile" file.
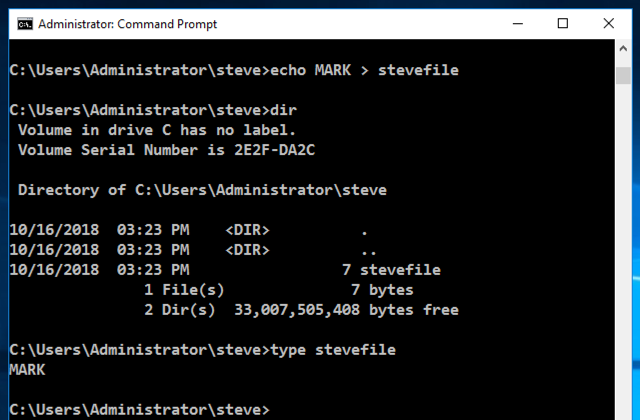
mkdir sally
cd sally
echo MARK2 > sallyfile
dir
dir ..
The "dir" command shows the contents of the "sally" folder.
The "dir .." command shows the contents of the folder above "sally" folder, also called its parent. Notice that ".." allows you to use a folder that is outside the working directory, by specifying a relative path, which specifies how to get to the desired directory from the current working directory. This is called "directory traversal".
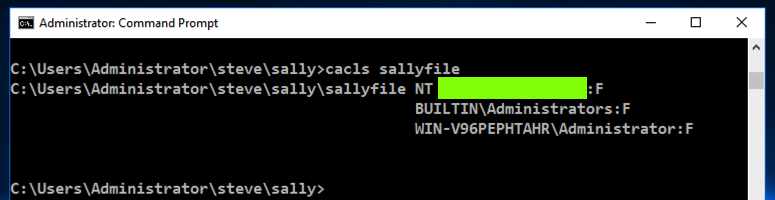
cacls sallyfile
As shown below, several accounts have "Full Control", indicated by the ":F" after the account names.
One of the accounts has a name beginning with "NT", and is covered by a green box in the image below.
Enter that name into the form below to record your success.
If you don't have a Canvas account, see the instructions here.
There is a folder named "secret" on the server, containing a file named "flag.txt". Read the contents of that file and enter it into the form below the frame to record your success.
If you don't have a Canvas account, see the instructions here.
If you don't have a Canvas account, see the instructions here.
Find it and enter it into the form below the frame to record your success.
If you don't have a Canvas account, see the instructions here.