Note: URL Changed
Originally this project used "attack.samsclass.info" but now you must use "attackdirect.samsclass.info" instead because the other URL has been upgraded to HTTPS.
https://www.google.com/chrome/browser/desktop/
http://www.editthiscookie.com/
At the bottom of the page, in the "Get it now" section, click "for Google Chrome".
A box pops up asking "Add "EditThisCookie"?". Click the "Add extension" button.
http://attackdirect.samsclass.info/cookielogin/
Log in with a Name of root and a Password of toor
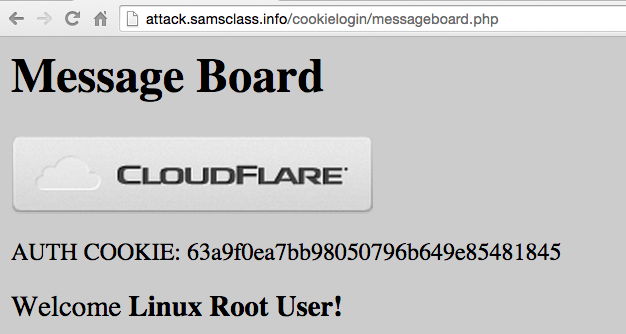
A "Message Board" page appears, saying "Welcome Linux Root User", as shown below.

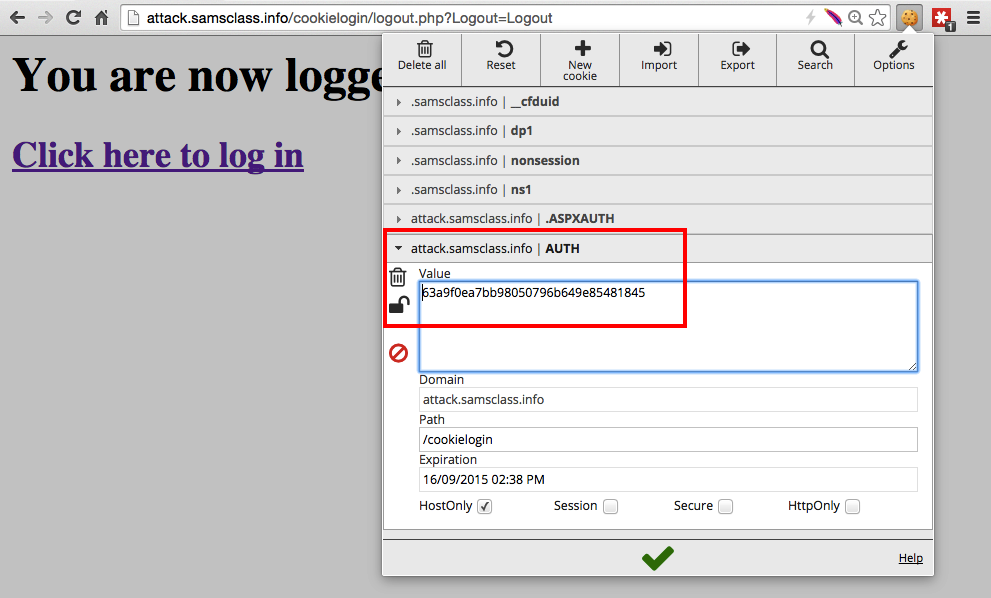
Find the AUTH value, outlined in red in the image below. This cookie indicates that a user has logged in.
At the bottom, there's a list of interfaces. Double-click the interface that connects to the Internet, showing a wavy line indicating network traffic. When I did it, the interface was "Wi-Fi:en0", as shown below.
http.cookie
Press Enter. This shows only HTTP requests that contain cookies. Even when filtered this way, I found a lot of packets, as shown below.
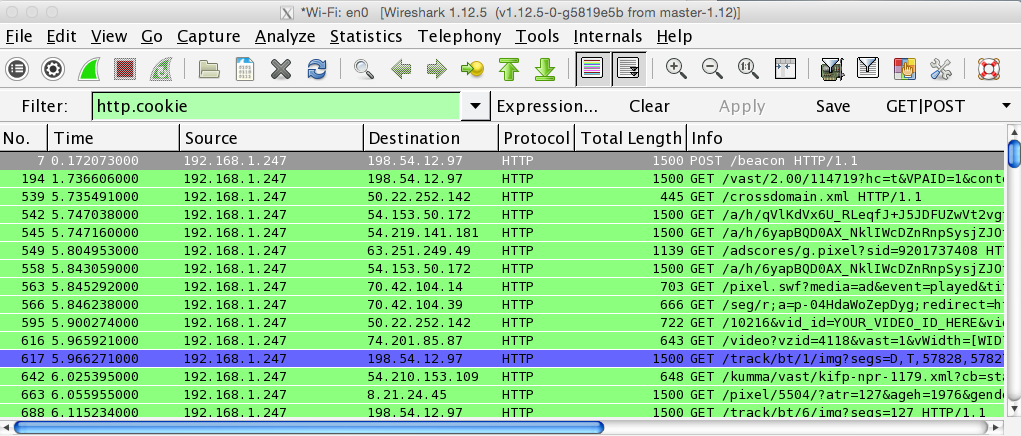
In the Filter bar, change the filter to:
http.cookie && frame contains samsclass
Press Enter. This shows only a few requests.
Find a request labelled "GET /cookielogin/messageboard.php" in the top pane, and click it to select it, as shown below.
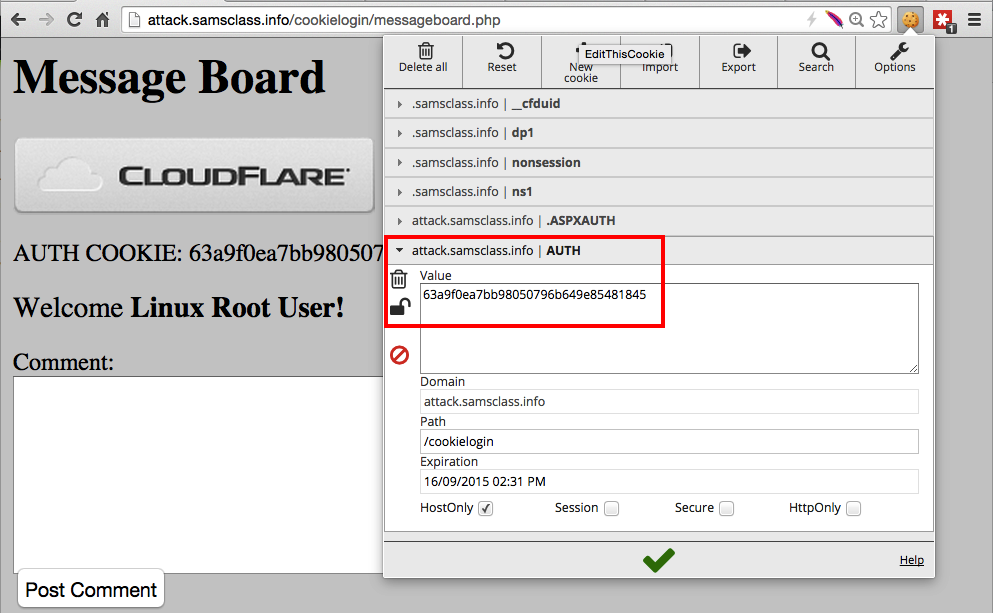
In the middle pane of Wireshark, expand "Hypertext Transfer Protocol" and expand "[truncated]Cookie".
You should see several Cookie pairs, including the one that sets AUTH to a long hexadecimal value, as outlined in the image below.
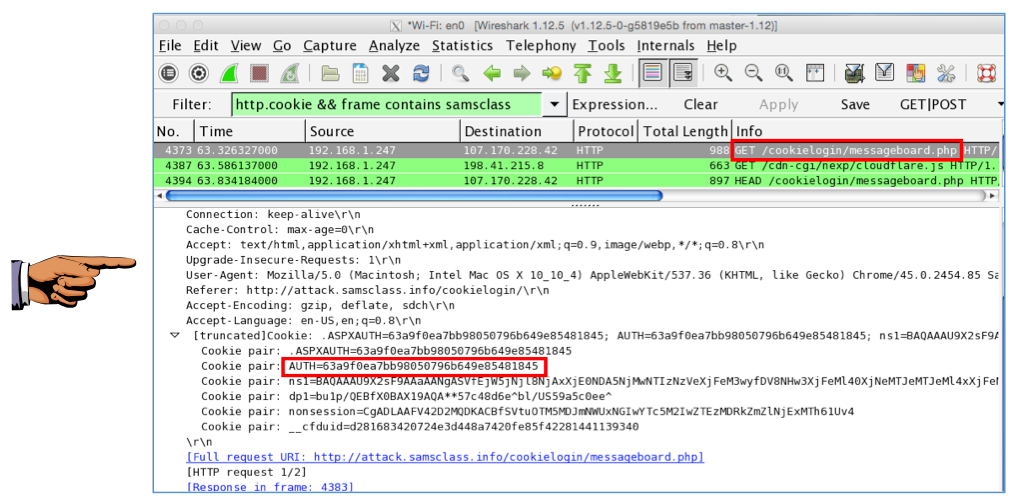
Make sure you can see AUTH=63a9f0ea7bb98050796b649e85481845.
Save a FULL DESKTOP image with the filename Proj 11a from Your Name.
A page appears, saying "You are now logged out!".
In Chrome, go to this URL:
http://attackdirect.samsclass.info/cookielogin/messageboard.php
You see the message: "INVALID FAIL", as shown below.
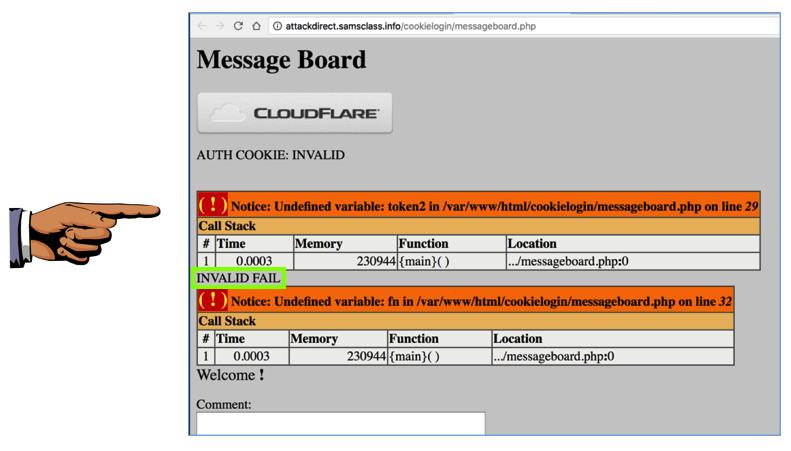
Make sure you can see the message: "INVALID FAIL".
Save a FULL DESKTOP image with the filename Proj 11b from Your Name.
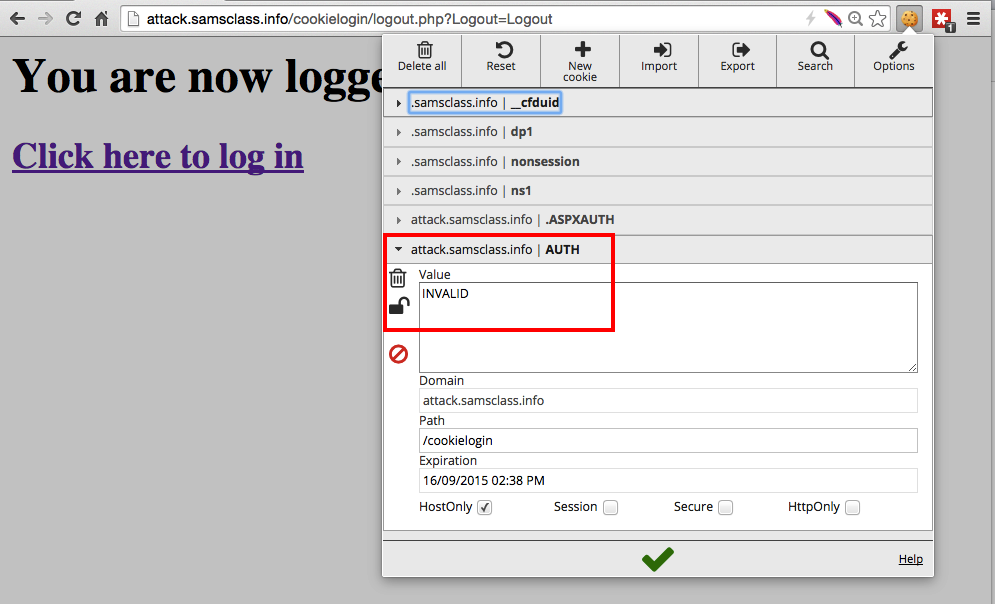
Click in the box showing INVALID, erase that text, and paste in the contents of your clipboard. Remove the "AUTH=" at the start of the data, so only the long hexadecimal string remains, as shown below.
Then click the green checkmark at the bottom of the EditThisCookie window to save your change.
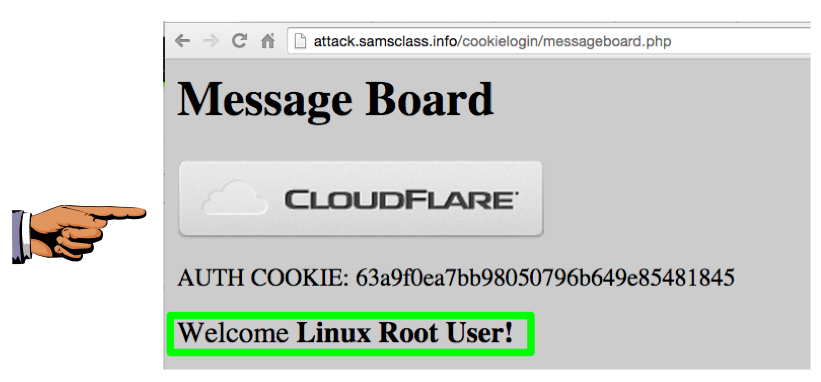
You see the message "Welcome Linux Root User", as shown below.
You got into the user's account without entering a password, using a stolen cookie. This is called Cross-Site Request Forgery (CSRF).
Save a FULL DESKTOP image with the filename Proj 11c from Your Name.