If you go to a wireless network and capture frames in Monitor mode, you see traffic from other users, but you can't decrypt it because each user has a different encryption key.
However, the process of assigning that key uses a four-way EAPOL handshake, which can be captured. If you capture the EAPOL packets, Wireshark can determine that user's key and decrypt the traffic.
https://wiki.wireshark.org/SampleCaptures?action=AttachFile&do=get&target=wpa-Induction.pcap
Troubleshooting
If that link doesn't work, use this alternate download link:
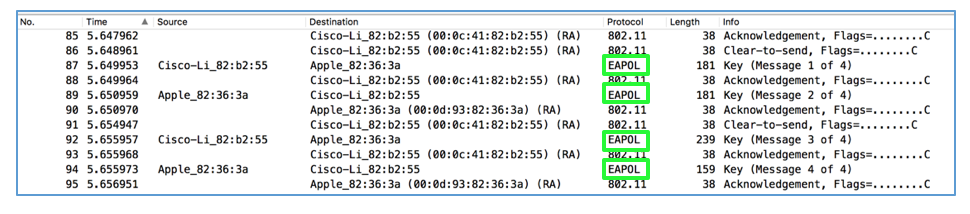
Scroll down to find the four frames with a Protocol of "EAPOL", as shown below. Here an Apple device is joining a Cisco wireless network, and the four EAPOL packets are used to negotiate a private key for that user.

For Wireshark 2.0.0 on Mac OS X:
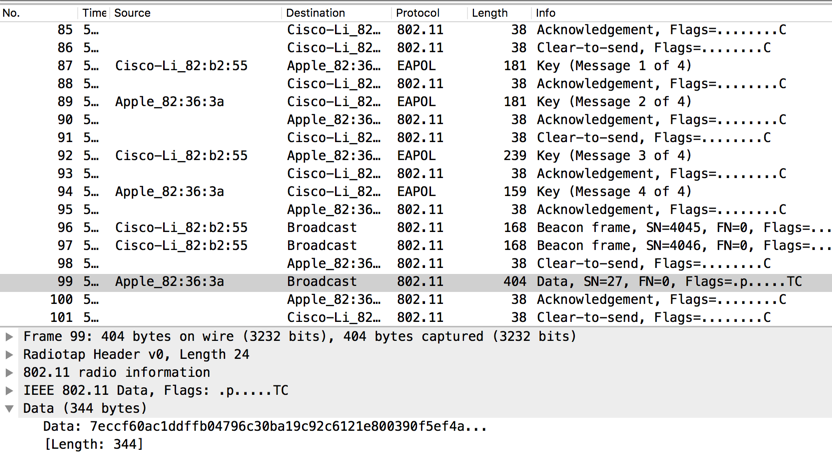
From the menu bar, click Wireshark, Preferences. In the left pane, expand Protocols. Scroll down and click "IEEE 802.11", as shown below.
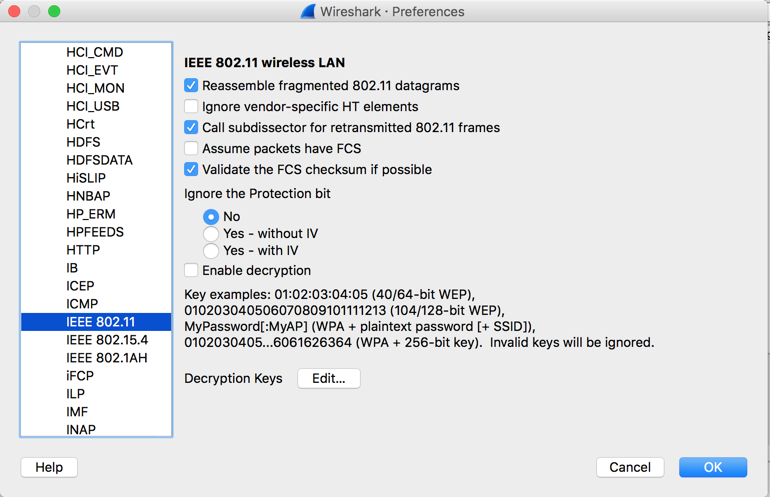
In the "Decryption Keys" line, click the Edit... button.
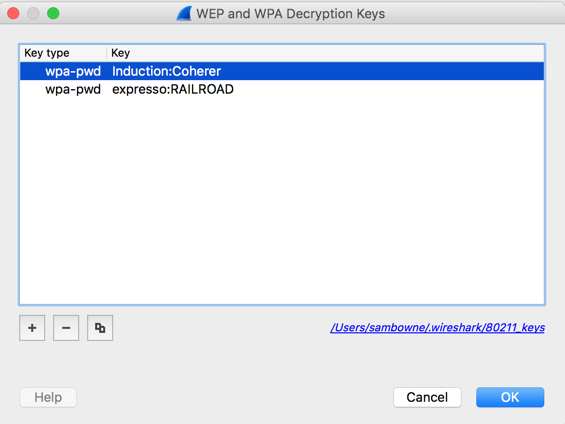
Enter a key of type wpa-pwd, with the value Induction:Coherer, as shown below.
The key is "Induction" and the SSID of the network is "Coherer".
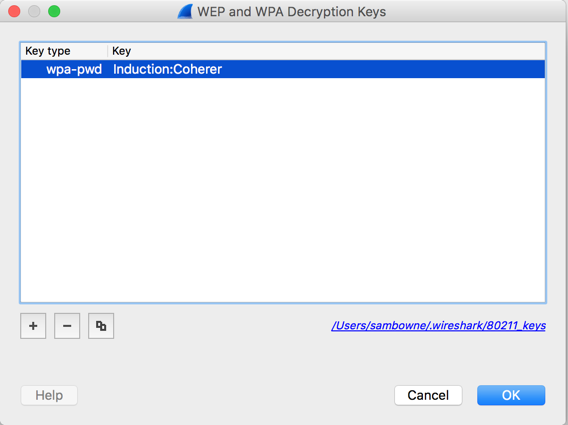
In the "WEP and WPA Decryption Keys" box, click the OK button.
In the "Wireshark Preferences" box, check the "Enable decryption" box. Click the OK button.
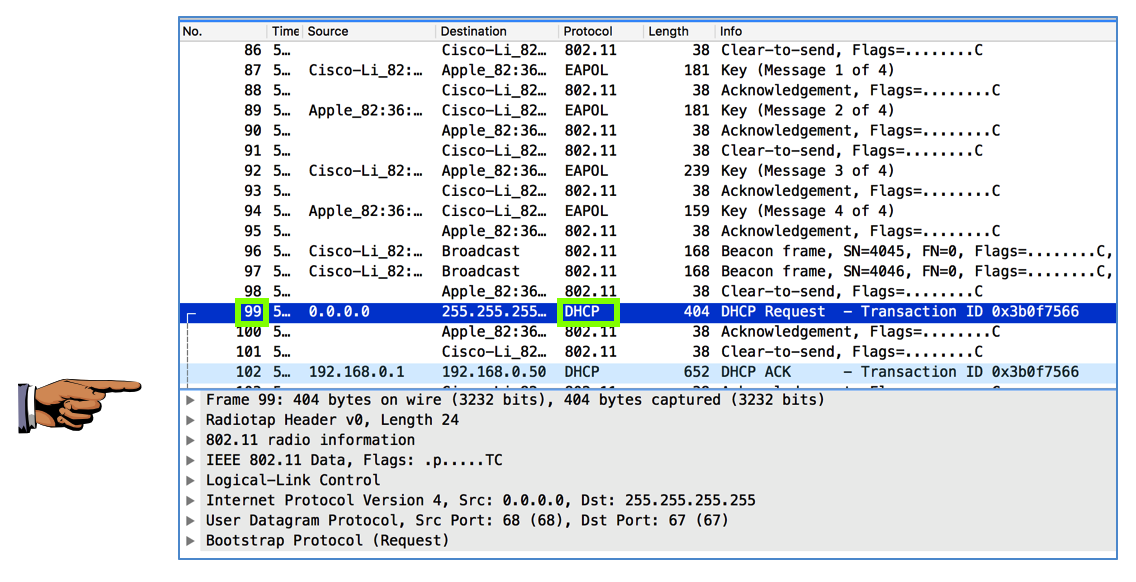
Frame 99 is now decrypted, revealing that it contains a DHCP packet, as shown below.
Save a FULL DESKTOP image with the filename Proj 11xa from Your Name.
But to capture EAPOL frames, you must use Monitor mode. I know the MacBook Air and MacBook Pro can do it, and the Asus Eee machines in the closet in S214. The computers in S214 with wireless cards can also do it if you boot them using Kali Linux DVDs.
Unless you are very lucky, your personal laptop won't be able to do this.
Here are the steps I performed to do it on a MacBook.
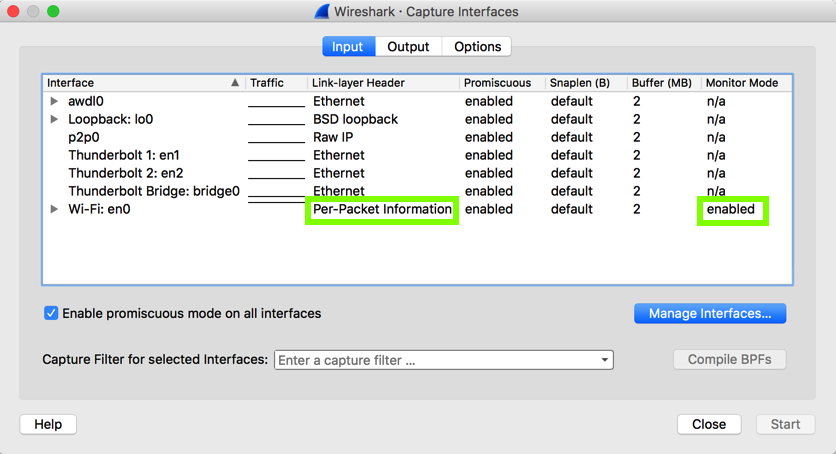
In the "en0" line, change "Link-Layer Header" to "Per-Packet Information", and change "Monitor Mode" to enabled, as shown below.
To make the project easier, we'll prepare the target machine to connect quickly.
Get another wireless device to use as the target. I used an iPad. Join it to the wireless network, and set it to automatically join. Then disable the wireless card.
Once the target connects, stop the Wireshark capture.
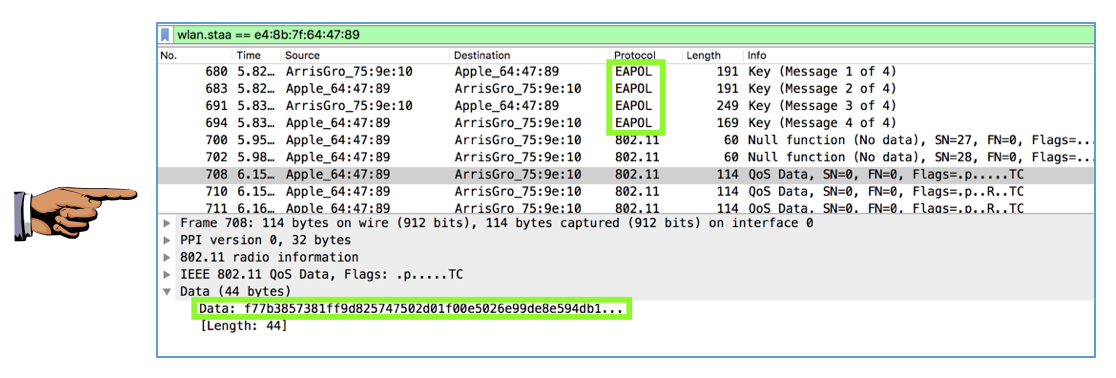
You should be able to see the four EAPOL frames, and a frames after that containing encrypted Data, as shown below.
Save a FULL DESKTOP image with the filename Proj 11xb from Your Name.
Now view the same frame in Wireshark. It should be decrypted, showing the higher-level protocol, a shown below.
Save a FULL DESKTOP image with the filename Proj 11xc from Your Name.