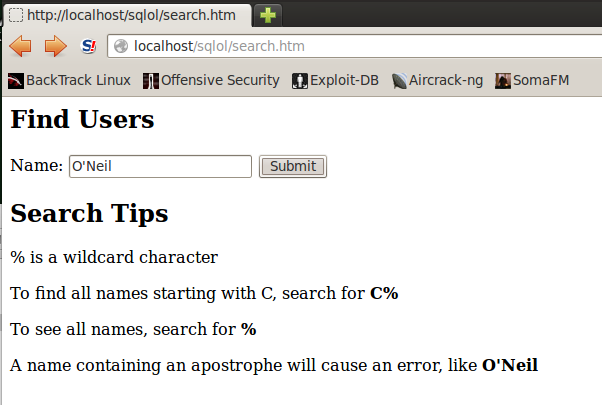
A "Find Users" page opens, as shown below:

In the Name field, type
O'Neil
You should see a SQL syntax error, as shown below:
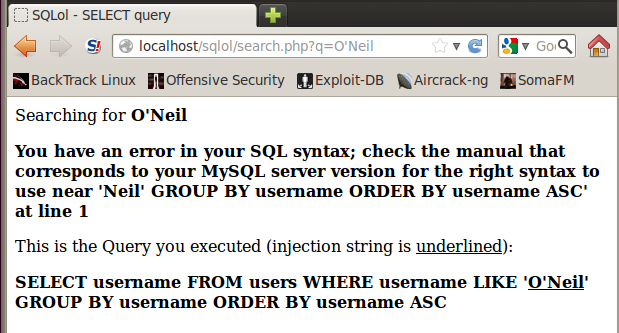
This error indicates a SQL injection vulnerability.
cd /var/www/sqlol
cp search.php old-search.php
nano search.php
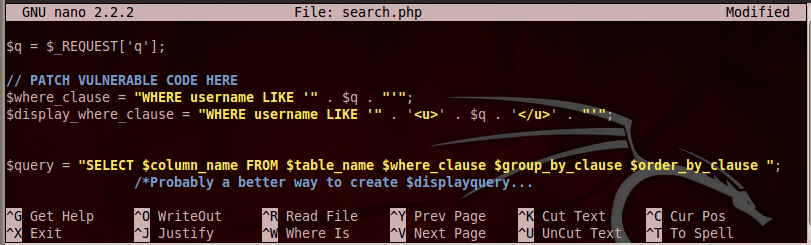
Add this line under the comment:
$q = mysql_real_escape_string($q);
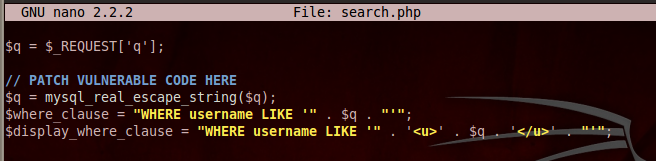
Save the page with Ctrl+X, Y, Enter.
This line adds backslash characters before quotation marks, which will prevent SQL syntax errors.
A "Find Users" page opens, as shown below:

In the Name field, type
O'Neil
Now, instead of an error, you see a chart showing that no results were found, as shown below:
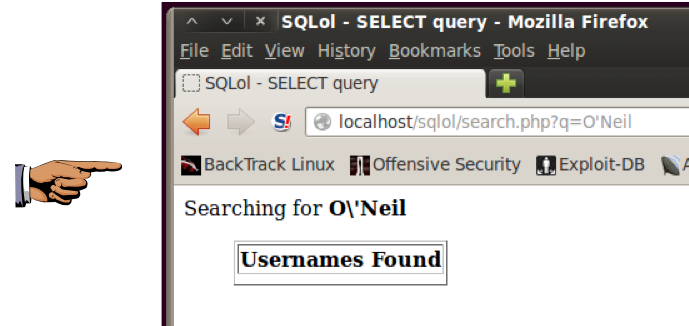
You can see how the fix works: the URL shows the original search string of O'Neil but the top of the results Web page shows the escaped version O\'Neil
Save a screen image with the filename Proj SQL-X2 from Your Name.
Email the image to cnit.123@gmail.com with a Subject line of Proj SQL-X2 from Your Name.
Last modified: 3:18 pm 12-31-12