import socket
s = socket.socket()
s.settimeout(2)
target = 'target1.bowneconsulting.com'
s.connect((target, 80))
req = 'HEAD / HTTP/1.1\r\nHost: ' + target + '\r\n\r\n'
s.send(req.encode())
print(s.recv(1024).decode())
s.close()
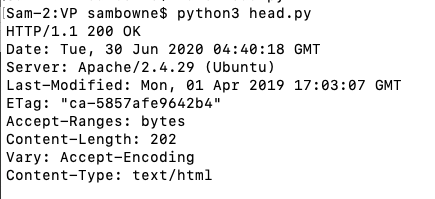
You should see an HTTP banner, telling you that my server uses Apache on Ubuntu Linux, as shown below:
Explanation
This code connects on TCP port 80 just like the scanner you made in a previous project, but once it connects, it sends an HTTP request like this:The HEAD method grabs only the banner, without getting any pages from the server.
Open this page in another browser window:
http://target1.bowneconsulting.com/php/login1.php
It's a simple login form.
Try to log in with a username of a and a password of b
In Wireshark, stop the capture.
Find the packet in Wireshark with an "Info" column of "GET /php/login1.php HTTP/1.1". Right-click that line and click Follow, "TCP Stream", as shown below:
The POST request appears, as shown below. The red text shows the HTTP request your browser sent to the server, and the blue text shows the server's reply.
Notice that the blue text is largely zipped and unreadable. That will be a problem for us a bit later.
Replace the HEAD request with the entire GET request copied from Wireshark, as shown below. Notice that a multiline string must be enclosed in triple quotes, and that each line must have a "\r" character added to it, as shown below.
Run the script.
You may see unreadable gibberish, or a Unicode error, as shown below.
This happened because the response came in zipped. To prevent that, delete the "Accept-Encoding" line outlined in blue in the image above.
Run the program again. Now you get a readable response, as shown below.
Open this page in another browser window:
http://target1.bowneconsulting.com/php/login2.php
Try logging in, and capture the request in Wireshark, as shown below.
Notice that the username and password now appear on a separe line after the blank line at the end of the headers, and that a "Content-Length" header must be set to specify the total number of characters in the POST data. In the image below, the POST data is seven characters long:
u=a&p=b
Flag VP 210.1: POST Login (10 pts)
Make a Python script that logs in to this page:http://target1.bowneconsulting.com/php/login2.php
with these parameters:
The server will reply with a flag, as shown below.
- Username: dumbo
- Password: dumbo
- User-Agent: python
Flag VP 210.2: POST Brute Force (10 pts)
Make a Python script that logs in to this page:http://target1.bowneconsulting.com/php/login3.php
with these parameters:
You will need to use a loop.
- Username: admin
- Password: a two-digit number
The server will reply with a flag, as shown below.
Then open this page:
http://target1.bowneconsulting.com/protected/dumbo
A login box appears. Log in with a username of dumbo and a password of dumbo
Wireshark shows two GET requests for a URL in the "protected" directory, as shown below.
The first request fails with a "401 Unauthorized" status, but the second one succeeds.
In the top pane, click the successful GET request. In the middle pane, expand the "Hypertext Transfer Protocol" section.
The Basic authentication string is shown, and decoded by Wireshark to show the credentials
dumbo:dumbo
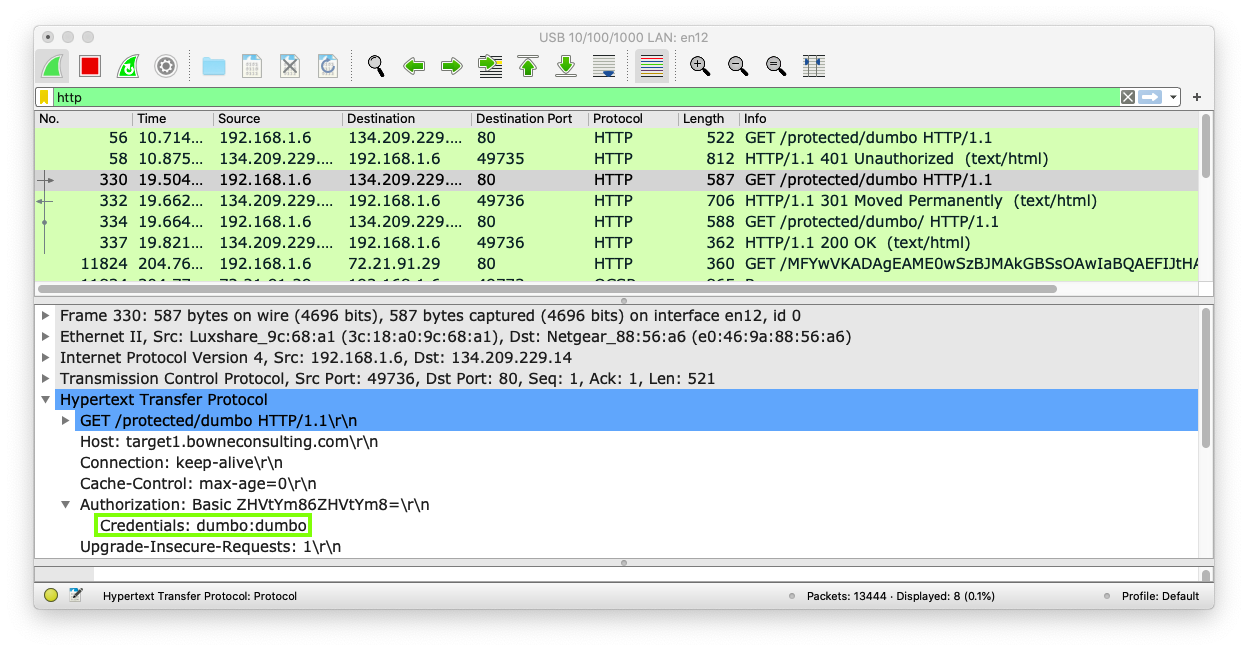
The request contains an "Authorization" header line, as shown below:
import base64
cred = "dumbo:dumbo"
auth = base64.b64encode(cred.encode())
print("Base64-encoded credentials", auth.decode())
Flag VP 210.3: Basic Authentication (10 pts)
Make a Python script that logs in to this page:http://target1.bowneconsulting.com/protected/A2.3/index.php
with these parameters:
The server will reply with a flag.
- Username: admin
- Password: P@ssw0rd
- User-Agent: python
Flag VP 210.4: Brute Force Basic Authentication (10 pts)
Make a Python script that logs in to this page:http://target1.bowneconsulting.com/protected/A2.4
with these parameters:
The server will reply with a flag.
- Username: admin
- Password: a two-digit number
- User-Agent: python
Instead, we'll use Firefox Developer Tools. If you don't have Firefox, get it here.
Open this page in Firefox:
http://target1.bowneconsulting.com/php/login1.php
In the Firefox window, at the top right, click the three-bar "hamburger" icon.
Click "Web Developer", Network.
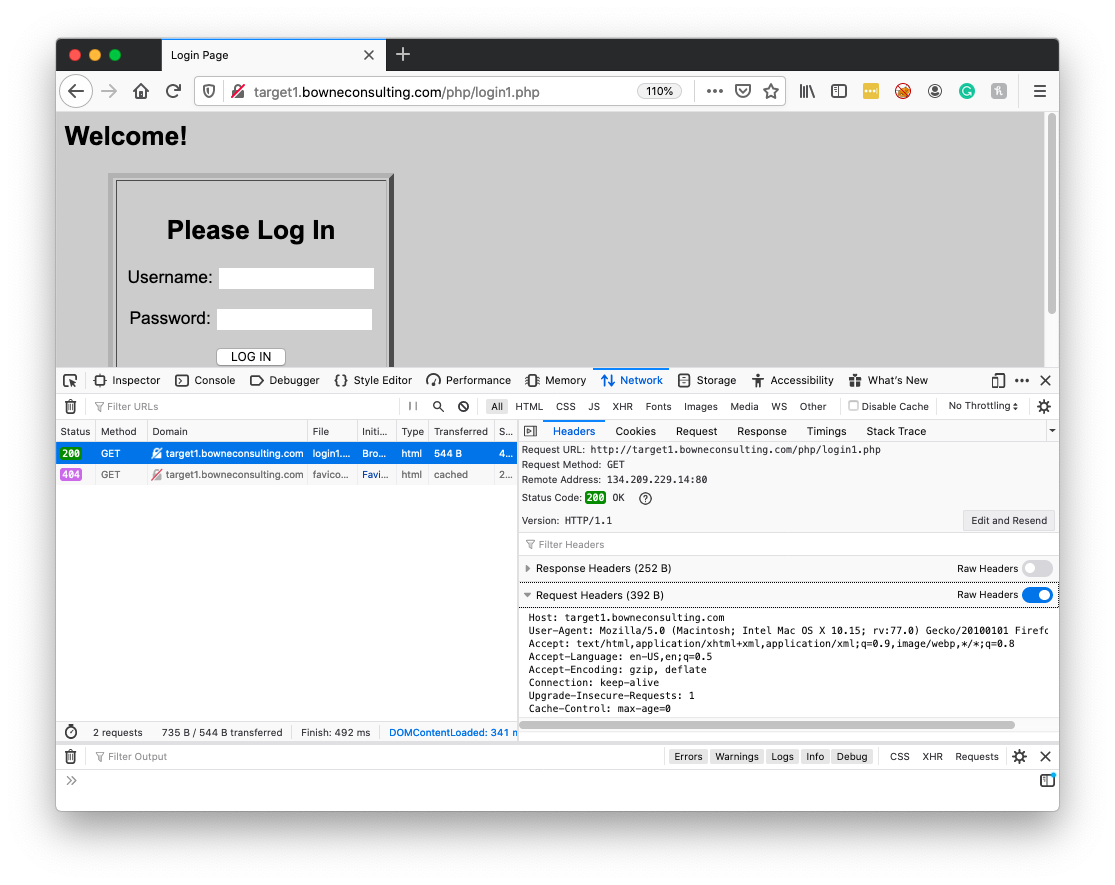
Refresh the page.
You can find the raw Request Headers in the Developer Tools pane, as shown below.
This works for HTTPS sites also.
Flag VP 210.5: HTTPS Basic Auth (10 pts)
Make a Python script that logs in to this page:https://bowneconsultingcontent.com/BASIC0/index.php
with these parameters:
The server will reply with a flag.
- Username: admin0
- Password: password
- User-Agent: python
Hint: use requests.
Hint: First repeat VP 210.3 using "requests".
The server will reply with a flag.
Flag VP 210.6: HTTPS Basic Brute (10 pts)
Make a Python script that logs in to this page:https://bowneconsultingcontent.com/BASIC/index.php
with these parameters:
The server will reply with a flag.
- Username: admin
- Password: password with a two-digit number appended to it, like password11
- User-Agent: python
Flag VP 210.7: HTTPS Basic Brute (10 pts)
Make a Python script that logs in to this page:https://bowneconsultingcontent.com/A2.5/index.php
with these parameters:
The server will reply with a flag.
- Username: admin with a two-digit number appended to it, like admin11
- Password: password with a two-digit number appended to it, like password11
- User-Agent: python