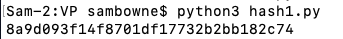
Here's a simple test case. A password of
password
8846f7eaee8fb117ad06bdd830b7586c
Execute this command to import an md4 library from my site, in a Bash terminal:
curl https://samsclass.info/ML/proj/md4.pyx -o md4.py
from md4 import md4
h = md4('password'.encode())
print(h)
This is a hexadecimal hash, but it's incorrect for Windows passwords. As shown above, the correct NT hash starts with 8846.
That's because the Windows algorithm uses Unicode, not ASCII, to encode the characters. Specifically, it uses a very old version of Unicode that uses only lengths of 16 and 32 bits to encode characters. Microsoft is now moving to UTF-8, but that process is only beginning.
Modify your program to use Unicode, as shown below. (NOTE: the code for Unicode is "UTF-16LE" with the letters in lowercase, NOT "utf-161e".)
from md4 import md4
h = md4('password'.encode("utf-16le"))
print(h)
Flag VP 300.1: Hash Dictionary (10 pts)
Create a program that calculates the NTLM hashes for all two-digit passwords from 00 to 99, as shown below.Find the hash containing baad. That complete hash value is the flag.
Flags VP 300.2-4: Windows Hashes (15 pts)
The following Windows passwords are constructed according to this system:CCSF-username-PINWhere "username" is the username in lowercase and PIN is a two-digit number.For example, a user named "Sam" might have a password like this:
CCSF-sam-01Crack these passwords, which were collected from a Windows 7 machine with Cain.Note that the NTLM hash is the rightmost part of each line, after the last colon.Ming:"":"":AAD3B435B51404EEAAD3B435B51404EE:52C4859C0617E4A8FEC24BA890C5FC57
Mohammed:"":"":AAD3B435B51404EEAAD3B435B51404EE:39057EF3A9FE57D98E7A9BAB7CD2F4F9
sam:"":"":AAD3B435B51404EEAAD3B435B51404EE:19A641D2520B983ABB7C931CEFF933FAThe passwords are the flags, as shown below:
- VP 300.2: Ming's password
- VP 300.3: Mohammed's password
- VP 300.4: Sam's password
Flags VP 300.5-7: MD5 Hashes with Several Rounds (15 pts)
This code calculates a md5 hash:The company using the Windows passwords in the previous challenge sets up an online system, with passwords formed the same way.import hashlib h = hashlib.md5("password".encode('utf-8')) print(h.hexdigest())Somewhere in the Terms of Service, it strongly warns users not to re-use the same password as their Windows password.
In addition, it is now much more secure, because it uses MD5 instead of MD4, and not only that, it uses many rounds of MD5. The number of rounds is less than 100.
It doesn't use Unicode encoding.
Crack these hashes.
Ming: 7621eca98fe6a1885d4f5f56a0525915
Mohammed: b2173861e8787a326fb4476aa9585e1c
sam: 42e646b706acfab0cf8079351d176121The passwords are the flags, as shown below:
- VP 300.5: Ming's password
- VP 300.6: Mohammed's password
- VP 300.7: Sam's password
Flags VP 300.8-10: Many Rounds of MD5 and SHA-1 (15 pts)
Somehow, evil hackers broke into the previous Web application.So the new, super-enhanced system uses a much larger number of MD5 rounds, followed by an even larger number of SHA1 hash rounds. Of course, the total number of hashing rounds is less than 500, because management is sure that's enough.
And now each user has to click "I Agree" to a pop-up box requiring them not to re-use passwords, so only a complete idiot would do that.
Crack these hashes if you can! Send in the correct passwords to collect credit.
Ming: ce788ed5f855e51e6fd78f923b43a6407467c5f2
Mohammed: 582d99006950cddeb2df9f40b3f65ebc283dc378
sam: da660655f4d4714fe605e9063d1ded4b749c50a9The passwords are the flags, as shown below:
- VP 300.8: Ming's password
- VP 300.9: Mohammed's password
- VP 300.10: Sam's password
user:$6$jeWFhYPiV3G.U2Kw$J8PgrCnOgw2n2wd2Ua2qM3R.09oc4q4JzbjsKSEbE5A
xtLAlFvJUdyZKV0B5R0mJX0MI3yaV3QhWnS3flBSG41:18448:0:99999:7:::
python3
import crypt
crypt.crypt("password", "$6$jeWFhYPiV3G.U2Kw")
Flags VP 300.11-13: Linux Hashes (15 pts)
The following Linux passwords are constructed according to this system:CCSF-username-PINWhere "username" is the username in lowercase and PIN is a two-digit number.For example, a user named "Sam" might have a password like this:
CCSF-sam-01Crack these passwords, which were collected from a Debian 10 machine.Note that the NTLM hash is the rightmost part of each line, after the last colon.The passwords are the flags, as shown below:
- VP 300.11: Ming's password
- VP 300.12: Mohammed's password
- VP 300.13: Sam's password
Flags VP 300.14-16: Lastpass-Type Hashes (15 pts)
Lastpass reportedly uses "a random salt and 100,000 rounds of server-side PBKDF2-SHA256" hashing.Crack these passwords, in the same form as the previous challenges, using PBKDF2
with these parameters:
- Salt: SIXTEEN_TONS_OF_
- Interations: 100.000
- Hash function: SHA256
- Derived Key Length: 256 bits
The passwords are the flags, as shown below:
- VP 300.14: Ming's password
- VP 300.15: Mohammed's password
- VP 300.16: Sam's password