Start your Metasploitable 2 VM and log in as msfadmin with the password msfadmin
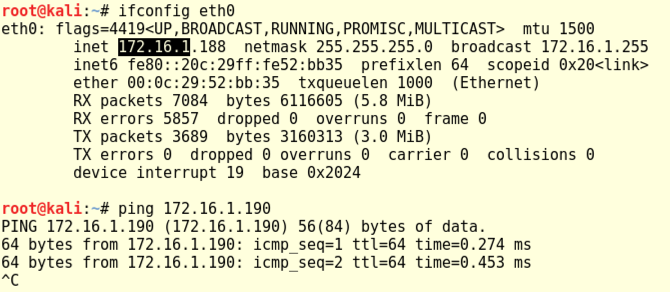
Execute the ifconfig command on both machines and ping from one to the other. Make sure you get replies, as shown below.

Replace the subnet address below with the correct subnet for your machine. Usually all you need is the first 3 bytes of the IP address, as highlighted in the image above.
netdiscover -r 172.16.1.0/24
Press Ctrl+C to exit netdiscover.
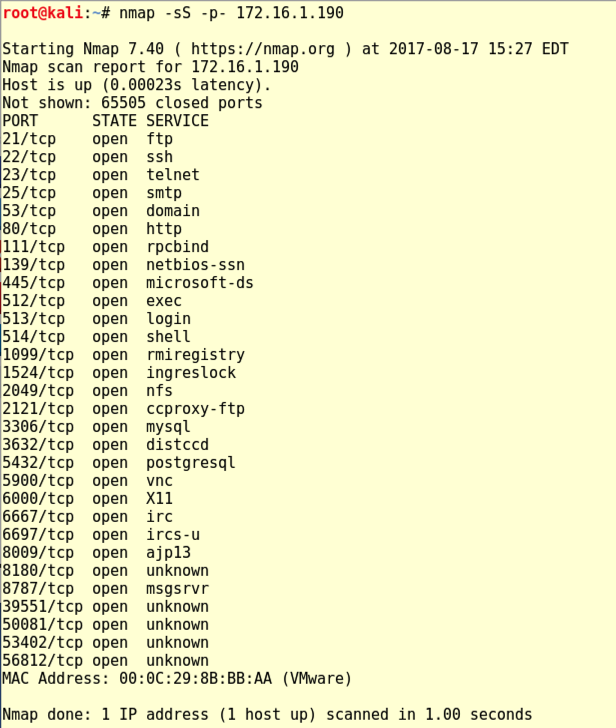
Execute this command to scan all 65,536 TCP ports on the target, replacing the IP address with the IP address of your Metasploitable 2 VM.
nmap -sS -p- 172.16.1.190
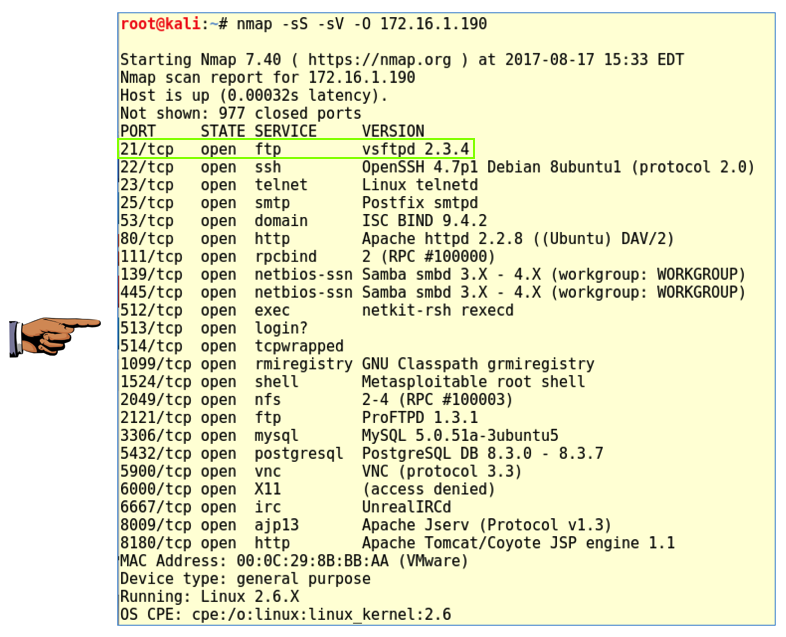
Execute this command to scan 1000 common ports on the target, with version detection and OS detection. Replace the IP address with the IP address of your Metasploitable 2 VM.
nmap -sS -sV -O 172.16.1.190
Capture a whole-desktop image and save it as "Proj 5a".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
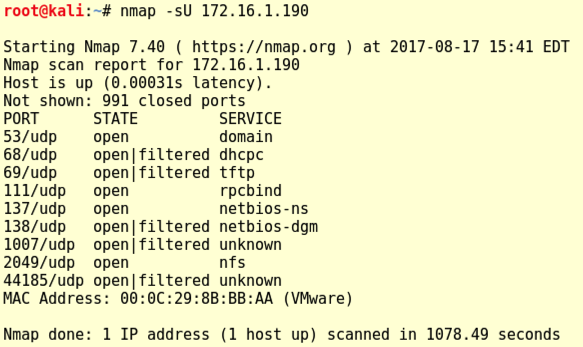
Replace all the IP addresses in commands below with the IP address of your Metasploitable 2 target machine.Execute this command to scan UDP ports on the target.
nmap -sU 172.16.1.190
When it finishes, it finds several UDP-based services, as shown below.
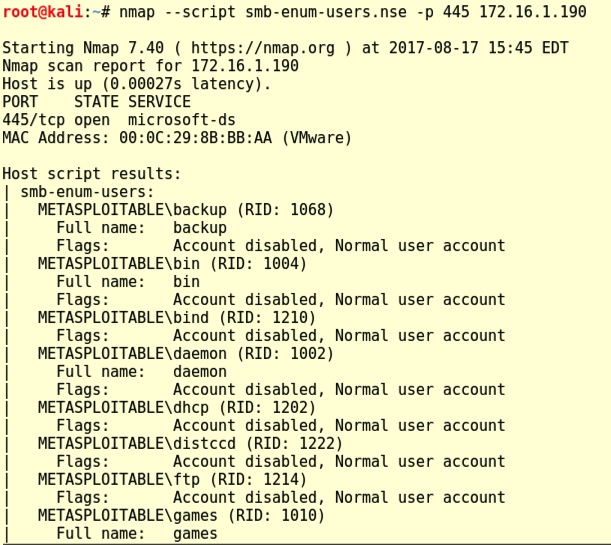
nmap --script smb-enum-users.nse -p 445 172.16.1.190
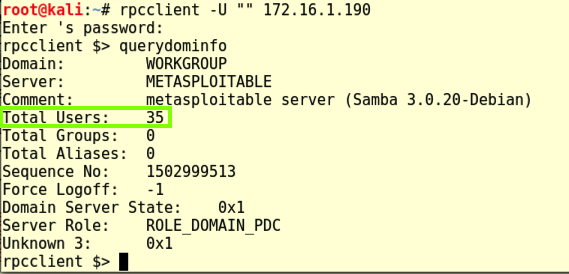
rpcclient -U "" 172.16.1.190
This displays an "rpcclient $>" prompt. Execute this command:
querydominfo
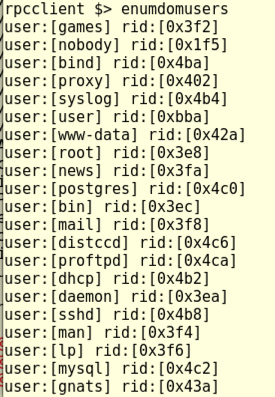
Execute this command to list all 35 user accounts.
enumdomusers
Execute this command to get more information about the "msfadmin" account.
queryuser msfadmin
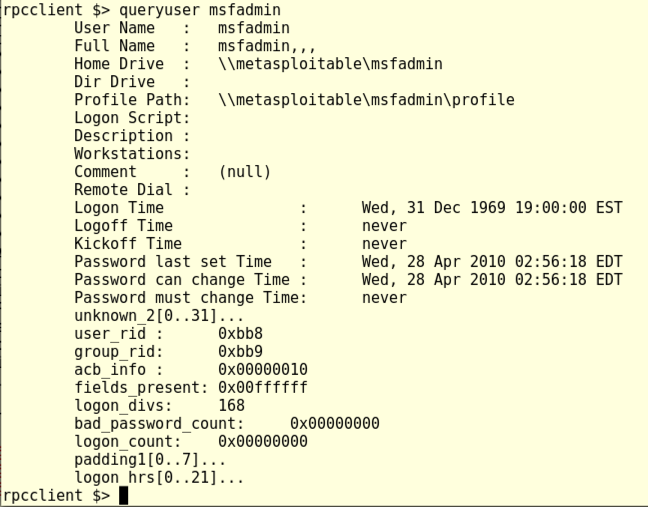
Execute the exit command to leave "rpcclient".
Execute this command to see the options for the enum4linux command.
enum4linux --help
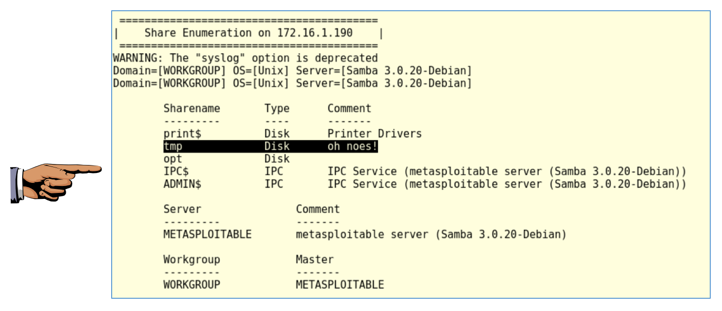
enum4linux 172.16.1.190
Then a "Share Enumeration" appears, showing that the /tmp folder is shared, as shown below. This has a note of "oh noes!" because /tmp is world-writeable. This means we can probably upload scripts into that folder and execute them :).
Capture a whole-desktop image and save it as "Proj 5b".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Send a Cc to yourself.
Last Modified: 8-17-17 1:19 pm