These sites are not infected, but are being used to bounce attacks via the Pingback vulnerability.
1. Attack Logs (12-6-13)
2. Notification of EDU Domains
3. Notification of All Domains
4. How to Clean Your Blog (not recommended)
5. Pingback Vulnerability: How to Fix It (Recommended)
6. Analyzing the Attack and Identifying the Attackers
7. NetSpoof Attack Service
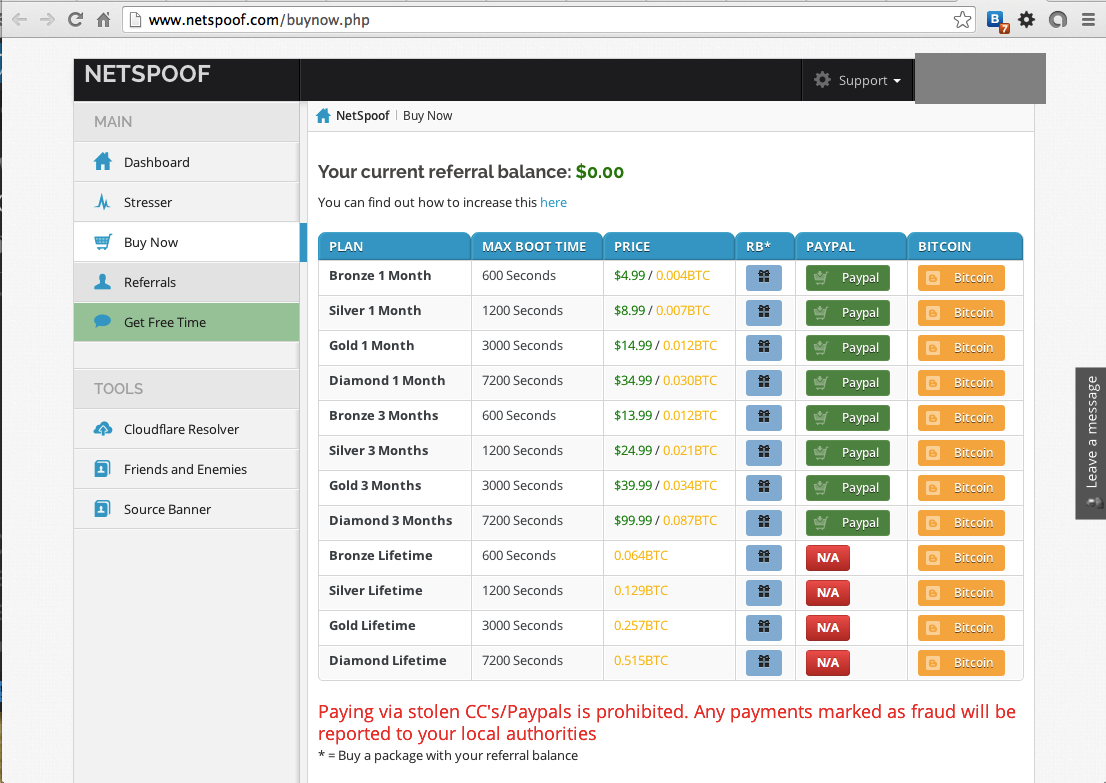
Here is a complete list of the 2155 Wordpress bots used in this attack:
wpbots-dec1-4-13.htm (348 KB)They were both from the same botnet of WordPress sites.
There were a lot of bots involved, but I only analyzed the EDU ones for now.
Here are the results from the 12/4 attack, which contained all the EDU bots:
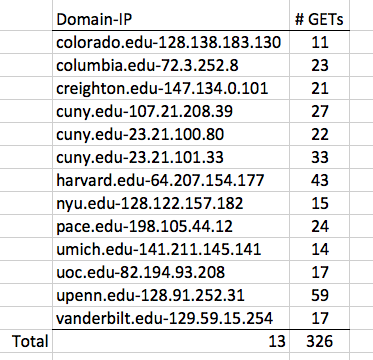
I'll forward this to those schools, so they know they are pwned.
dec1.txt (6,651,036 bytes)
ddos4dec13.txt (4,831,724 bytes)
security@colorado.edu OfficeOfThePresident@cu.edu
ranna_farzan@harvard.edu scott_fields@harvard.edu
records@colum.edu skauffman@colum.edu clientservices@colum.edu security@colum.edu
security@creighton.edu info@creighton.edu
chancellor@cuny.edu security@cuny.edu
alison.leary@nyu.edu security@nyu.edu john.sexton@nyu.edu
security@pace.edu jbaez@pace.edu ccapone@pace.edu
4HELP@umich.edu security@umich.edu presoff@umich.edu
security@uoc.edu csigales@uoc.edu
security@upenn.edu presweb@pobox.upenn.edu
chancellor@vanderbilt.edu security@vanderbilt.edu
president@harvard.edu abuse@harvard.edu security@harvard.edu
Notification done 10:07 pm 12-6-13
So I used this bash script to extract admin emails from whois:
while read line
do
echo $line " " `whois $line | grep "Admin Email:" | cut -d " " -f 3`
done < "$1"
That script stopped after 326 queries on Comcast,
so I switched to Sprint through my phone and it
completed--apparently Sprint has no whois query
limit.
Approximately half the domains had Admin Email addresses. I notified them all, grouping them together in groups of 30, 100, or 200 to make it more efficient. As of 12-9-13, they have all been notified. I got 3 replies from administrators of blogs so far.
One unfortunate aspect of this project is that I have no way to know if it's working, except replies, and from my previous notifications I know replies are very rare and do not necessarily indicate that the infection will be fixed.
I don't recommend it anymore, because most blogs are not in fact infected; what you need to do is disable the Pingback feature, as detailed below.
Hi Sam,Unfortunately, the only way to clean the site was to wipe the install and reinstall WP from scratch. It looks like the malware (unidentified) was injected into some javascript files that were a part of WP's core library. Sadly, Sucuri does not have a name for it - I'm guessing it exploited some vulnerability in either the JavaScript
This is what worked for me:
1. Scanning the website with http://sitecheck.sucuri.net/scanner/ and making sure that there was an infection.
2. Backing up my wordpress install.
3. Moving any important files out of the install (e.g. /wp-content/uploads, /wp-content/themes/) to a separate folder on my web host.
4. Making a note of the username, password, database name and hostname in wp-config.php (super important)
5. Deleting the wordpress folder, downloading the current version of Wordpress, and reinstalling it. I used the username and password from step 4.
6. Moving files from step 3 back into their proper places.After that, it's a case of reinstalling plugins. I ran Sucuri site scanner again, and the site was now clean of malware.
The entire process takes less than an hour. Hardening the site against future infections requires a whole lot of other work.
hope that helps,
Chris Lepine
Details and how to fix it are here:
Ahhh gotcha. This plugin for WP solves this new vuln:http://wordpress.org/plugins/prevent-xmlrpc/
(better than deleting xmlrpc.php, which will get reinstalled when WP core is upgraded)
From Chris Lepine
Just use facl to remove all rwx entirely on xmlrpc.php - can't be used OR replaced during upgrades. Easy fix.WordPress Default Pingback Exploitable To DDoS -- FIX EXPLAINED HERE
DDOS ATTACK -- THIS BLOG VIA XMLRPC.PHP
WordPress Default Leaves Millions of Sites Exploitable for DDoS Attacks
YOUR BLOG HAS BEEN HACKED. ACTUALLY, MAYBE NOT. THE PINGBACK EXPLOIT
WordPress Bug Report, 7 years old, closed :(
@sambowne @Fantastikk @akrabat my server load showed a strong demand on the xmlrpc.php for that time. That's how I found out about it.Another blog administrator sent me this by email:
This looks to have been the xmlrpc pingback exploit. I've disabled the xmlrpc.php script...And this!
The originating IP making the requests is 65.126.16.84, FWIW. Go yell at them.More info about the attacker:
We've seen 65.126.16.84 our logs as well but the request size is always too small to carry an actual payload, I think it's just a bot that scans for xmlrpc's. Also this IP showed up immediately in my honeypot and lacks any get or post parameters.Another report of the attacking IP address:65.126.16.84 - - [30/Nov/2013:22:24:06 -0500] "POST /xmlrpc.php HTTP/1.0" 200 370 "-" "Mozilla/4.0 (compatible: MSIE 7.0; Windows NT 6.0)" "-"
65.126.16.84 - - [30/Nov/2013:22:24:47 -0500] "POST /xmlrpc.php HTTP/1.0" 200 370 "-" "Mozilla/4.0 (compatible: MSIE 7.0; Windows NT 6.0)" "-"
mysql> SELECT * FROM `log` WHERE `ipaddress` LIKE '65.126.16.84'\G
*************************** 1. row ***************************
id: 32
ipaddress: 65.126.16.84
datetime: 2013-12-09 12:22:49
vhost: www.hostingcon.com
uri: /xmlrpc.php
get: []
post: []
cookie: []
*************************** 2. row ***************************
id: 33
ipaddress: 65.126.16.84
datetime: 2013-12-09 12:22:51
vhost: www.hostingcon.com
uri: /xmlrpc.php
get: []
post: []
cookie: []
2 rows in set (0.00 sec)
The actual attacker appears to be 184.154.10.69
The two logs that make this apparent:
184.154.10.69 - - [30/Nov/2013:22:22:24 -0500] "GET /blog/explore-ways-grow-hosting-company/?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+Hostingcon+(HostingCon) HTTP/1.0" 200 9238 "http://www.hostingcon.com/" "Mozilla/5.0 (iPad; CPU OS 6_1_3 like Mac OS X) AppleWebKit/536.26 (KHTML, like Gecko) Version/6.0 Mobile/10B329 Safari/8536.25" "-"
184.154.10.69 - - [30/Nov/2013:22:22:25 -0500] "POST /xmlrpc.php HTTP/1.0" 200 212 "http://www.hostingcon.com/blog/explore-ways-grow-hosting-company/?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+Hostingcon+(HostingCon)" "PHP/5.2.10"
The user agent change was what first alerted me. The timestamp also coincides with the first time one of our IPs shows up in your log file
From Mat Sumpter
I will speak to my webhost but I can see from looking at my logs that xmlrpc.php has been requested ~80,000 times from IP address 65.126.16.84I will disable pingbacks and take a look at that WP plugin you suggest in your blogpost
The tool is advertised on
HackForums.net (registration required)
Here is the ad I saw:
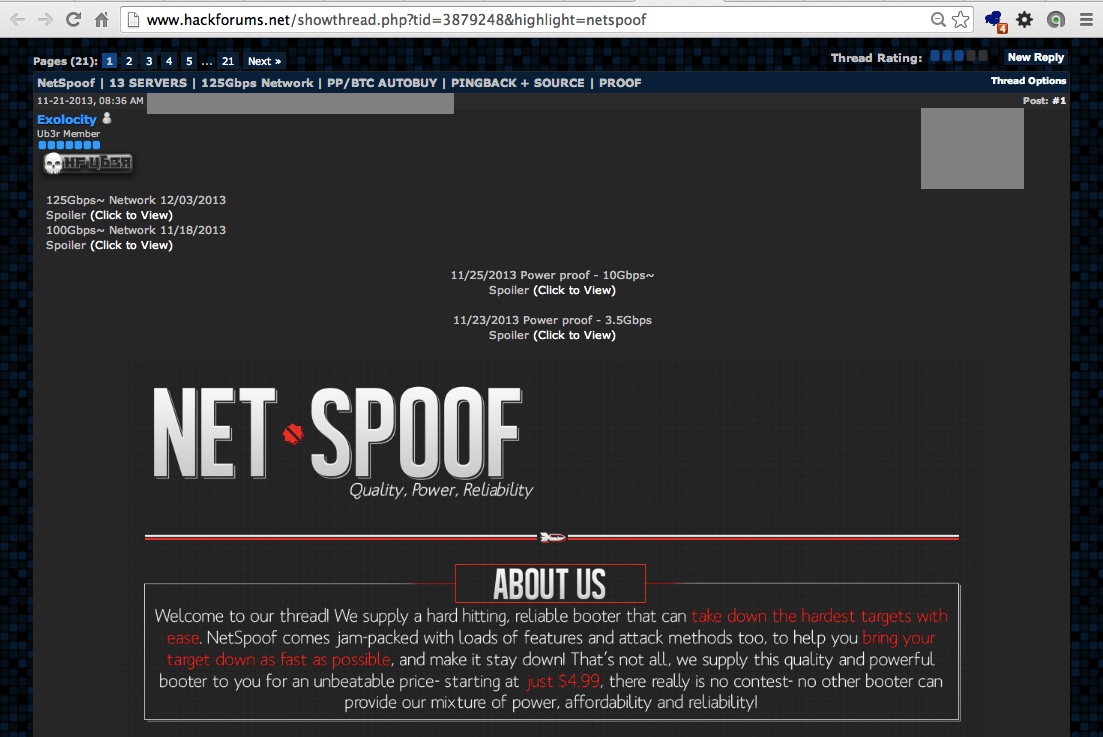
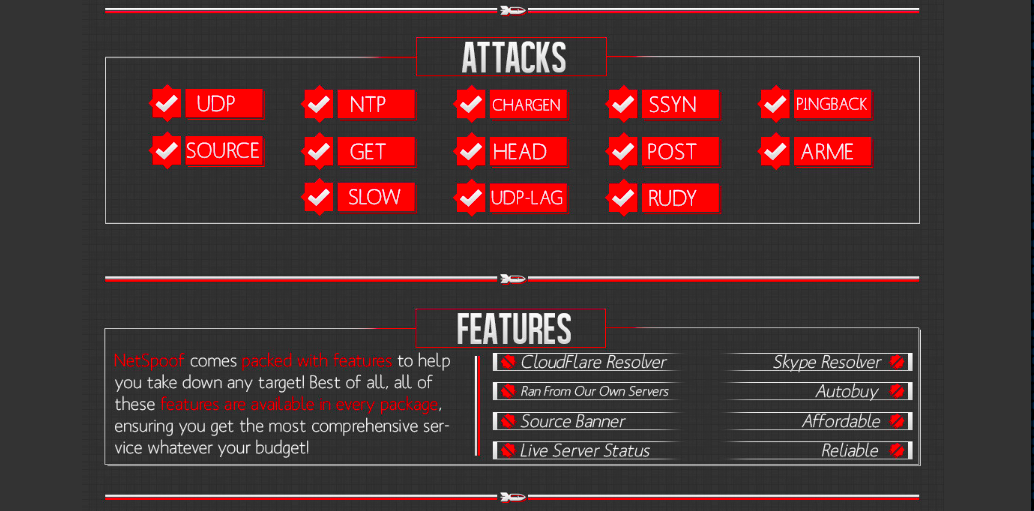

Here's the tool's home: Netspoof.com