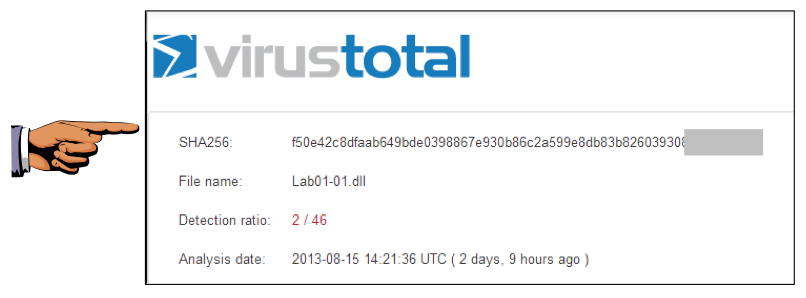
As shown below, some of the engines detect Lab01-01.dll.

The files were both compiled on the same date within a minute of each other, indicating that they are part of the same package.
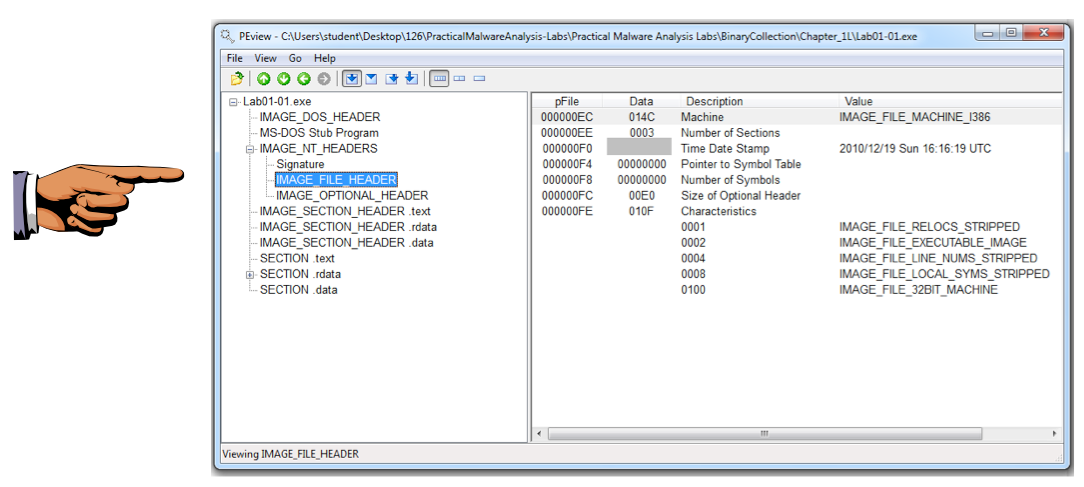
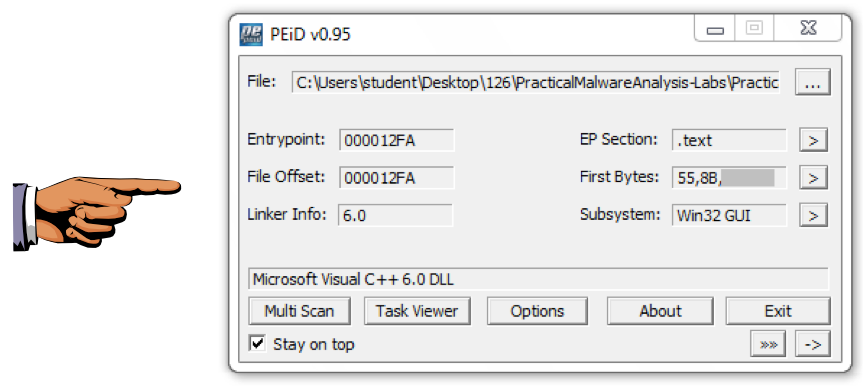
These files are identified as "Microsoft Visual C++" files, which shows that they are unpacked.
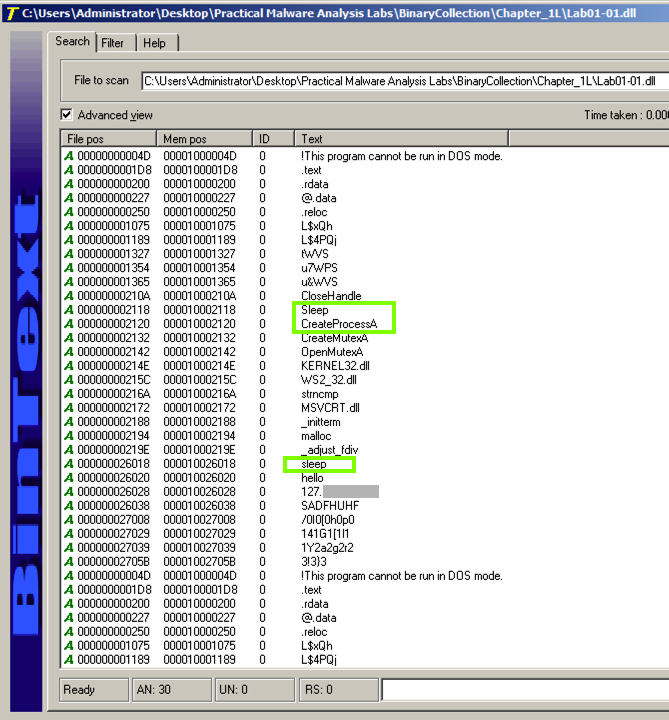
Look at the strings for Lab01-01.dll.
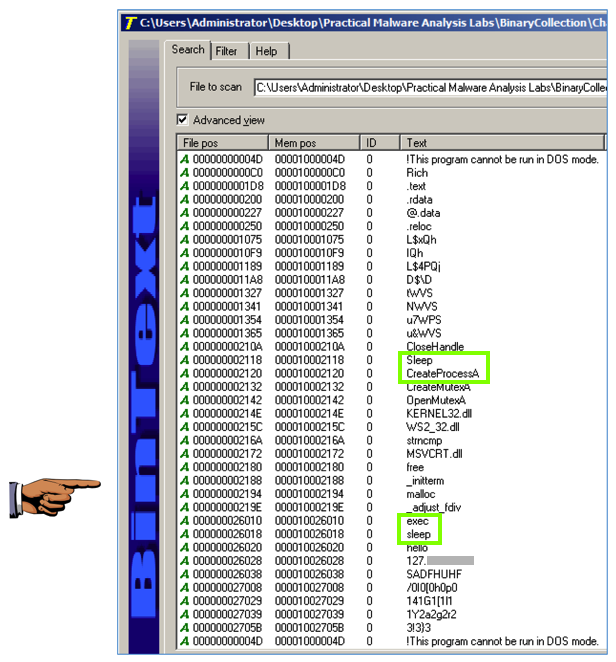
Notice these items, as shown below:
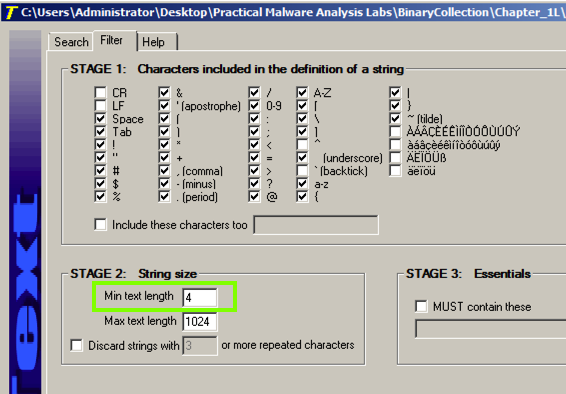
The command to launch a program is missing. To see it, click the Filter tab and adjust the "Min. text length" to 4 as shown below.
Click the Search tab. At the top right, click Go.
Now you can see that the command to launch a program is exec, as shown below.
Then collect the strings from the Lab01-01.exe file.
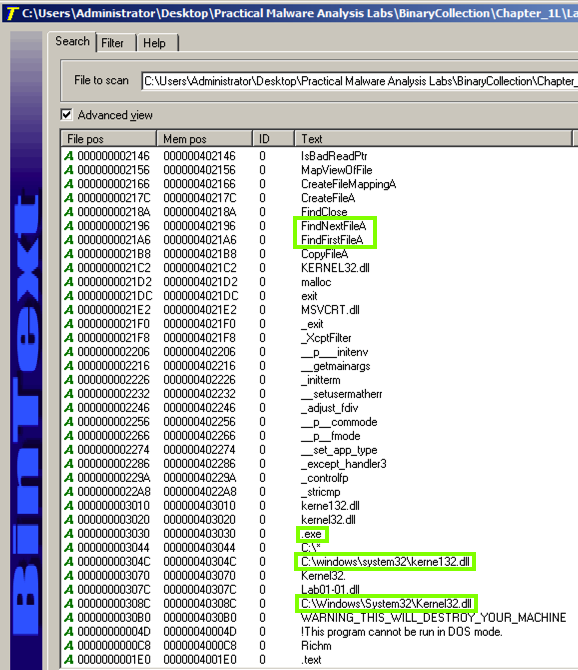
Notice these items, as shown below:
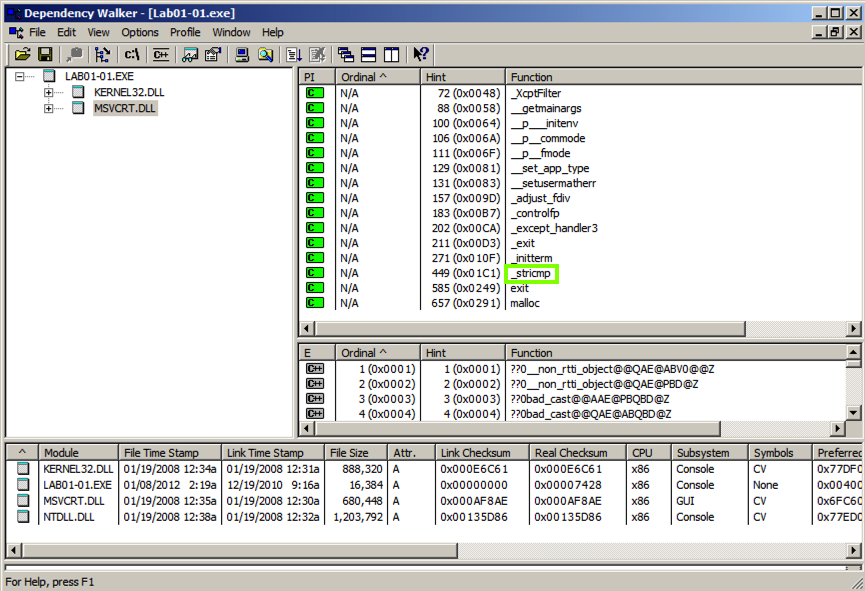
The top left pane is the In the top left pane is called "Module Dependency Tree View". It shows the EXE file and the two Windows libraries it uses: MSVCRT.DLL and KERNEL32.DLL.
In the top left pane, click MSVCRT.DLL. The top right pane shows "Parent Imports". These are the functions the EXE file uses from the library file.
As shown below, this executable uses only a small number of library functions, and none of them indicate much about its purpose. One of them is named _stricmp, which indicates that this progam performs a string copmarison, but that's a very common operation.
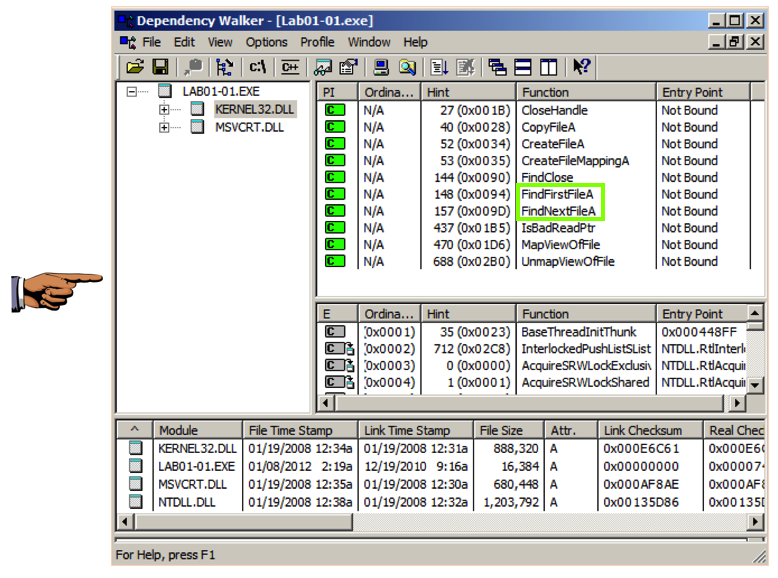
In the top left pane, click KERNEL32.DLL.
The top right pane shows that this file uses several functions that manipulate files, including FindNextFileA and FindFirstFileA, as shown below.
This suggests that the malware searches through the file system and can open and modify files.
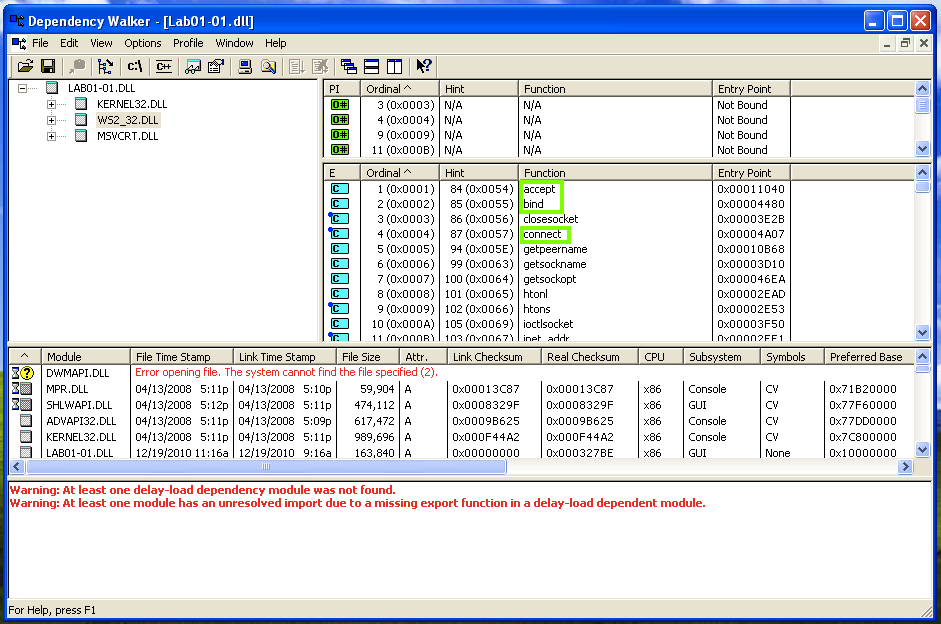
Open Lab01-01.dll in Dependency Walker. In the top left pane, partially collapse the tree to match the image below and click WS2_32.DLL.
The top right pane doesn't show function names this time, it only shows "Ordinal" numbers. This is called Linking by Ordinal, and it's an annoyance to us because we can't easily see what functions are in use.
However, the center-right pane shows the Exports of WS2_32.DLL, which include accept, bind, and connect. These are the standard Berkeley Sockets functions used for networking. This suggest that the malware performs some networking functions, such as connecting to a server and opening a listening port.
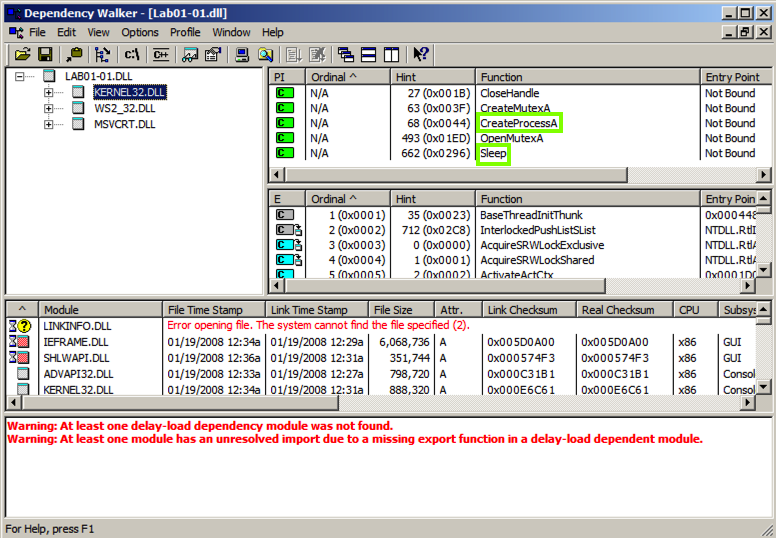
In the top let pane, click KERNEL32.DLL. The top right pane shows the "Parent Imports", which include CreateProcessA and Sleep, as shown below.
For more information about using Dependency Walker, see ths tutorial:
Analyzing dependencies with Dependency Walker
It downloads a file from this domain: practicalmalwareanalysis.com
That file's name is the flag.
It imports a function from WINTRUST.DLL
That function's name is the flag.
Hint: a function name looks like this:
AdjustTokenPrivileges