https://github.com/fireeye/capa/releases
In the left column, click the green "Latest release" button.
At the bottom of the next page, download the correct version for your system. There are versions for Linux, MacOS, and Windows.
Unzip the downloaded file. It's a command-line utility.
(On a Windows system, omit the "./".)
cd Downloads
./capa
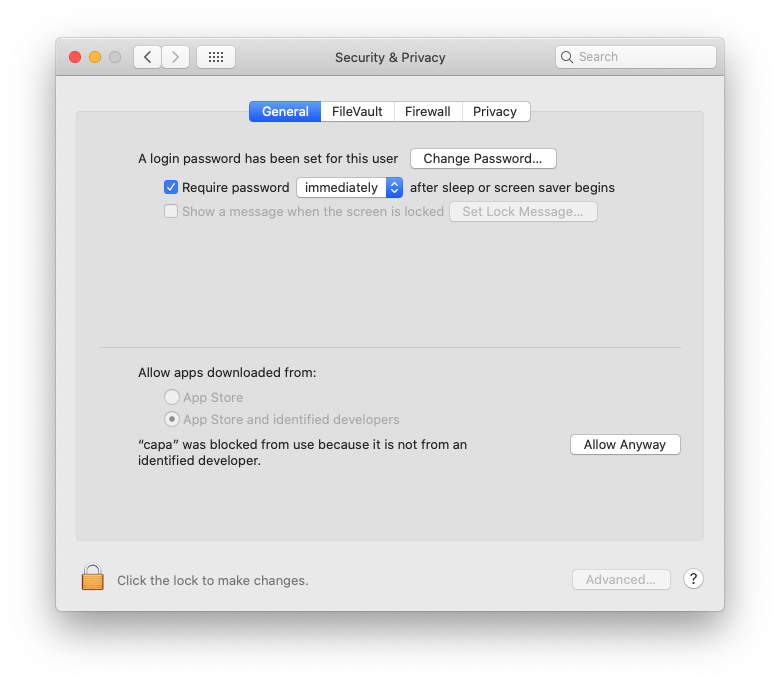
In System Preferences, click "Security & Privacy". On the General tab, in the lower section, you see a message saying capa was blocked, as shown below.
Click the "Allow Anyway" button.
Close Preferences.

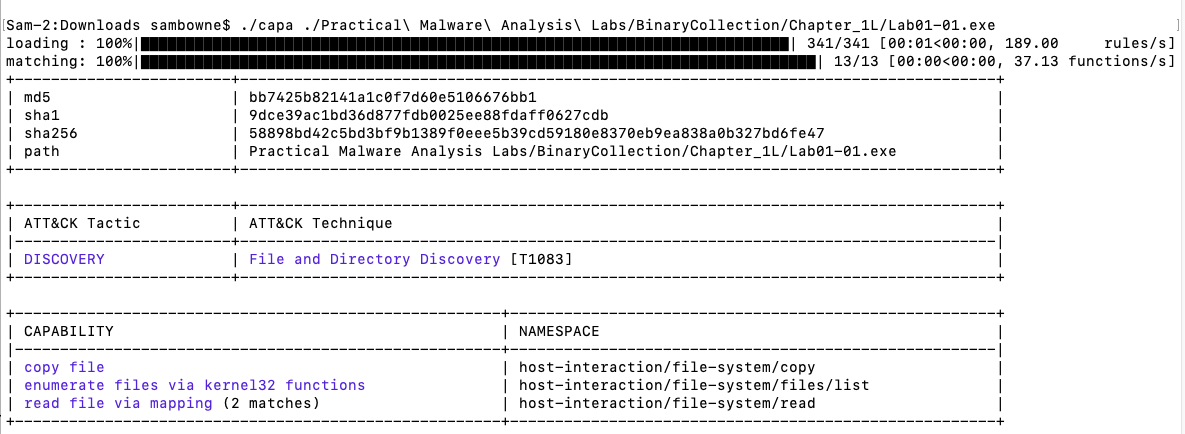
Now you will be able to run capa from the Terminal, as shown below.
https://github.com/mikesiko/PracticalMalwareAnalysis-Labs
Click PracticalMalwareAnalysis-Labs.7z.
On the next page, right-click Download and click "Save Link As...", as shown below.
The password to open the .7z file is malware
On Windows, extract the executable with 7-zip and run it.
On a Mac, use The Unarchiver twice to extract the files.
PMA 110.1: Lab01-01.dll (10 pts)
Analyze Lab01-01.dll. This file has networking capabilities, as shown below. Find the word covered by a green box in the image below.That's the flag.
PMA 110.2: Lab01-04.exe (5 pts)
Analyze Lab01-04.exe. This file uses three ATT&CK tactics, as shown below.Find the word covered by a green box in the image below.
That's the flag.
Posted 9-8-2020
Flag images updated 3-22-2021