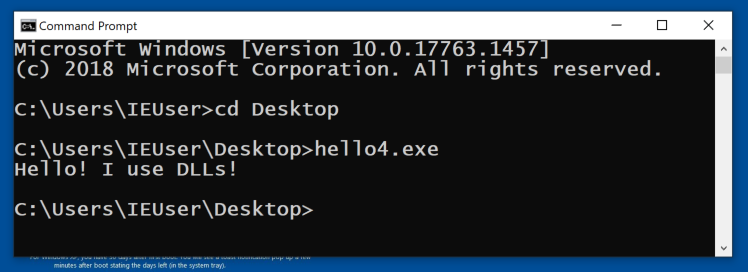
In a Command Prompt, execute the program. It prints out a short message, as shown below.

Here's the source code for that program. It uses only one function: printf. How complicated could that be?
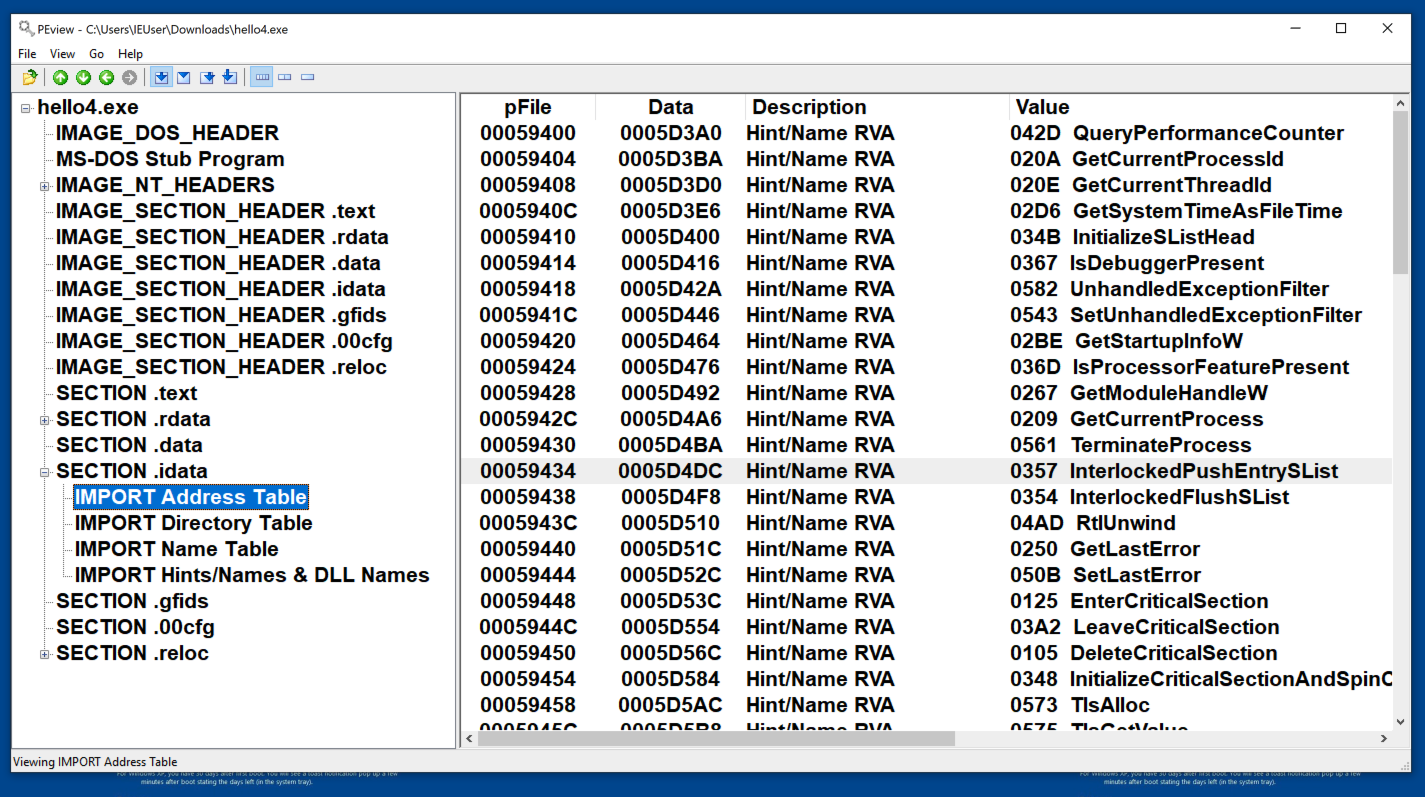
Examine the IMPORT Address Table. As shown below, this program uses dozens of Windows API calls.
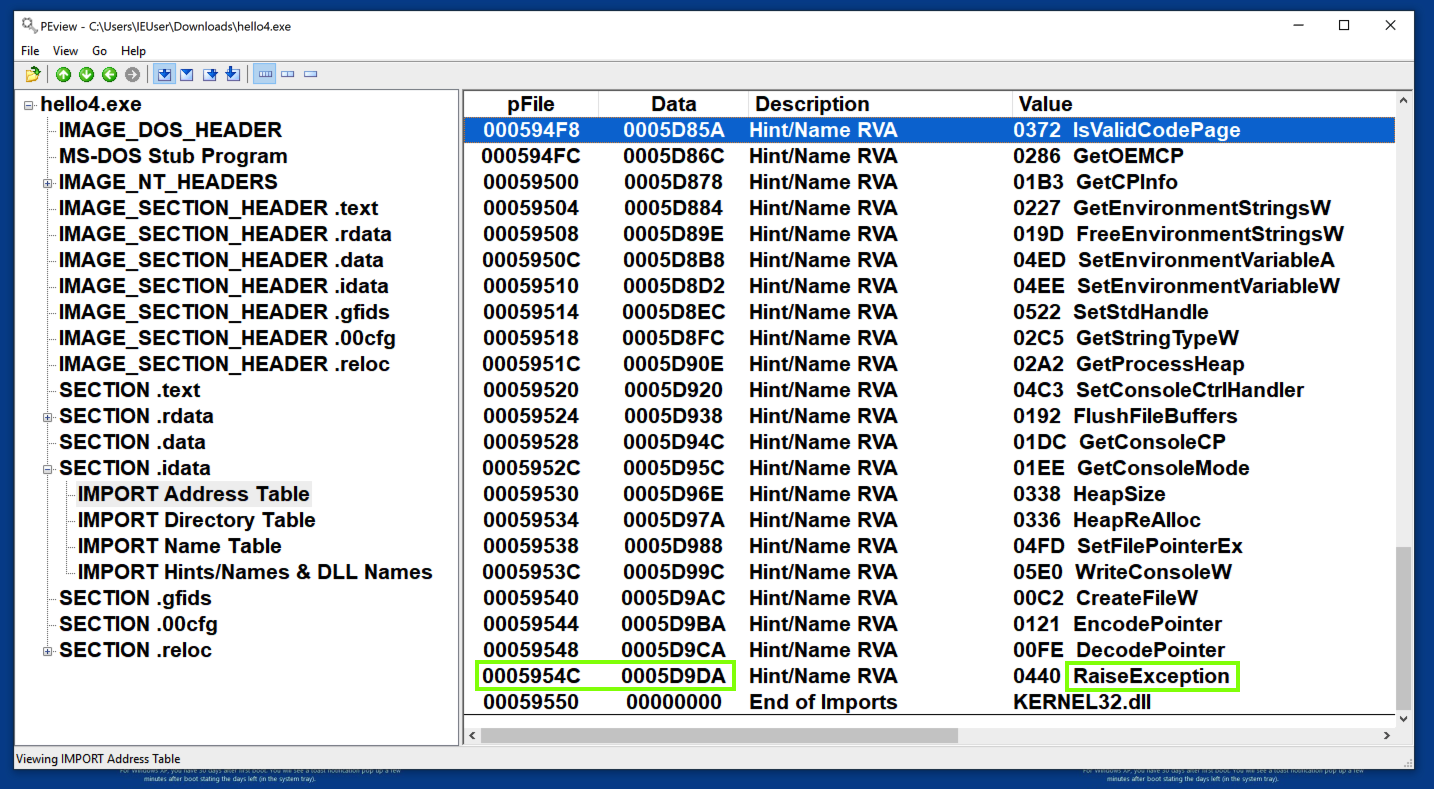
Scroll to the bottom to see the DLL name. All these API calls come from a single library: KERNEL32.dll, as shown below.
Examine the .idata section, as shown below.
Here you see a raw hexadecimal dump of the file contents, with the 32-bit word at 5954C containing the value 5D9DA in little-endian order, as shown below.
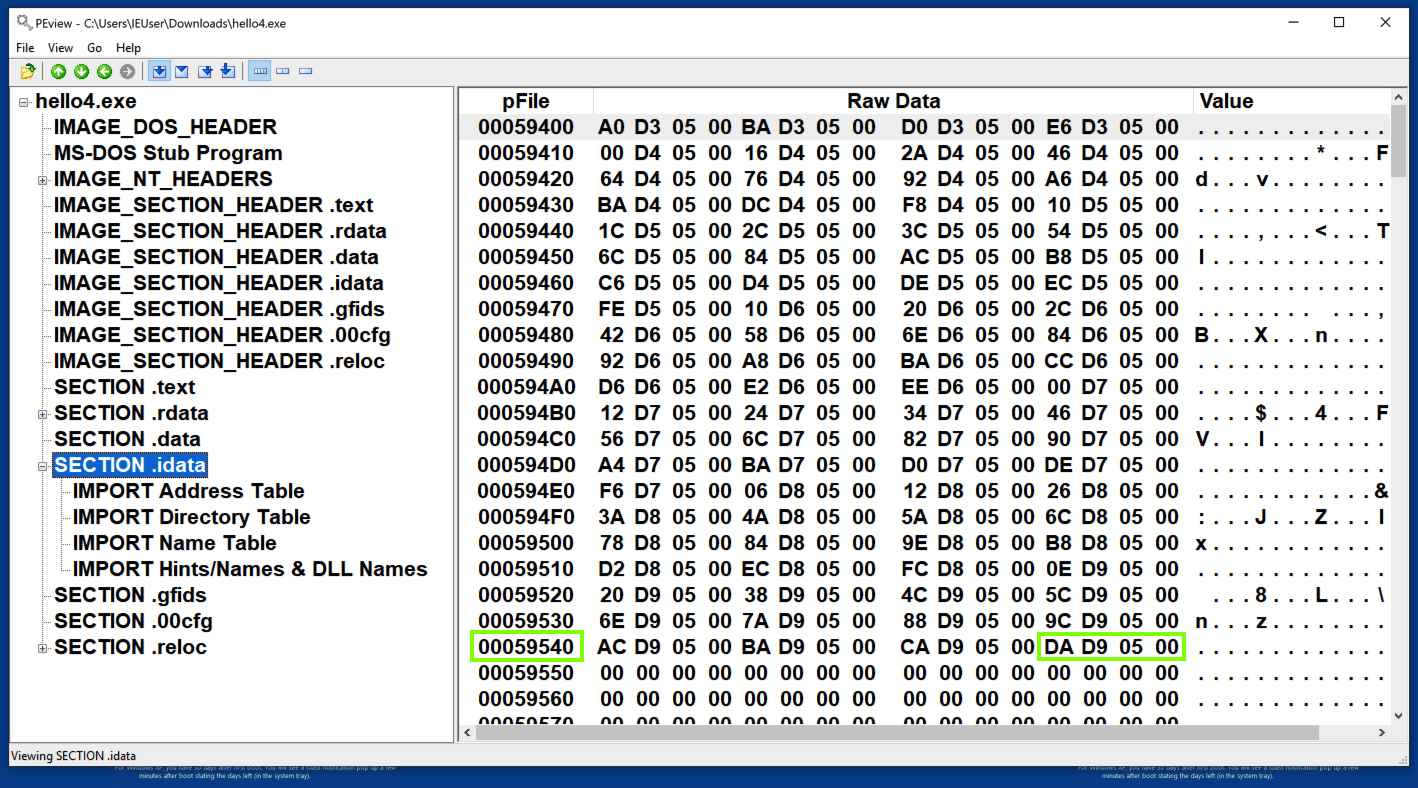
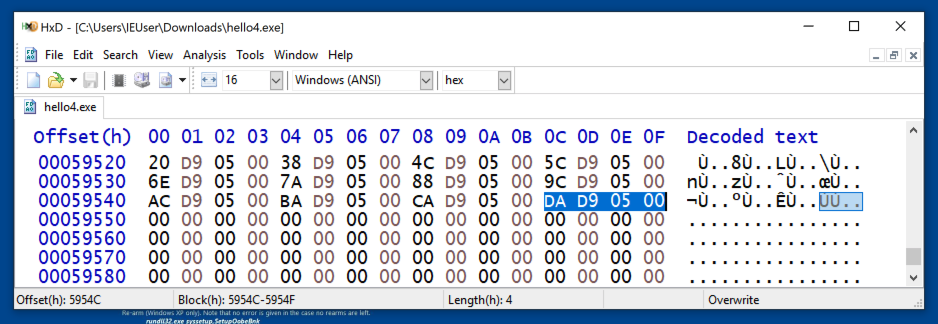
pFile addresses are actual locations in the PE file itself, which you can verify by examining the file with HxD, as shown below.
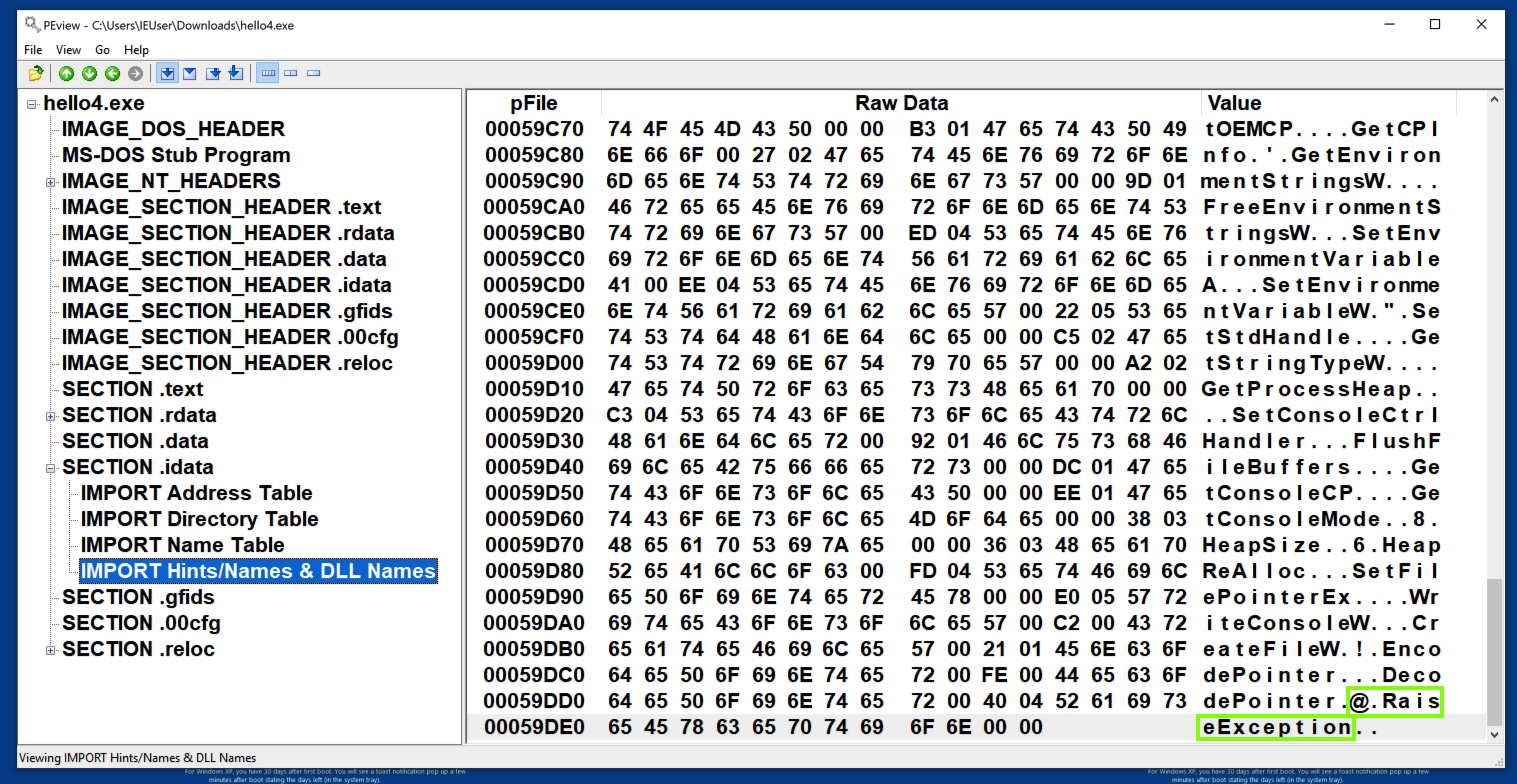
in Peview, examine the "IMPORT Hints/Names & DLL Names" section. RaiseException is at address 59DDA, as shown below (preceded by a 2-byte hint).
This address is 3C00 bytes lower than the Data of 5D9DA.
The value 5D9DA is a RVA (Relative Virtual Address) -- the location in RAM of the object, relative to its Base Address.
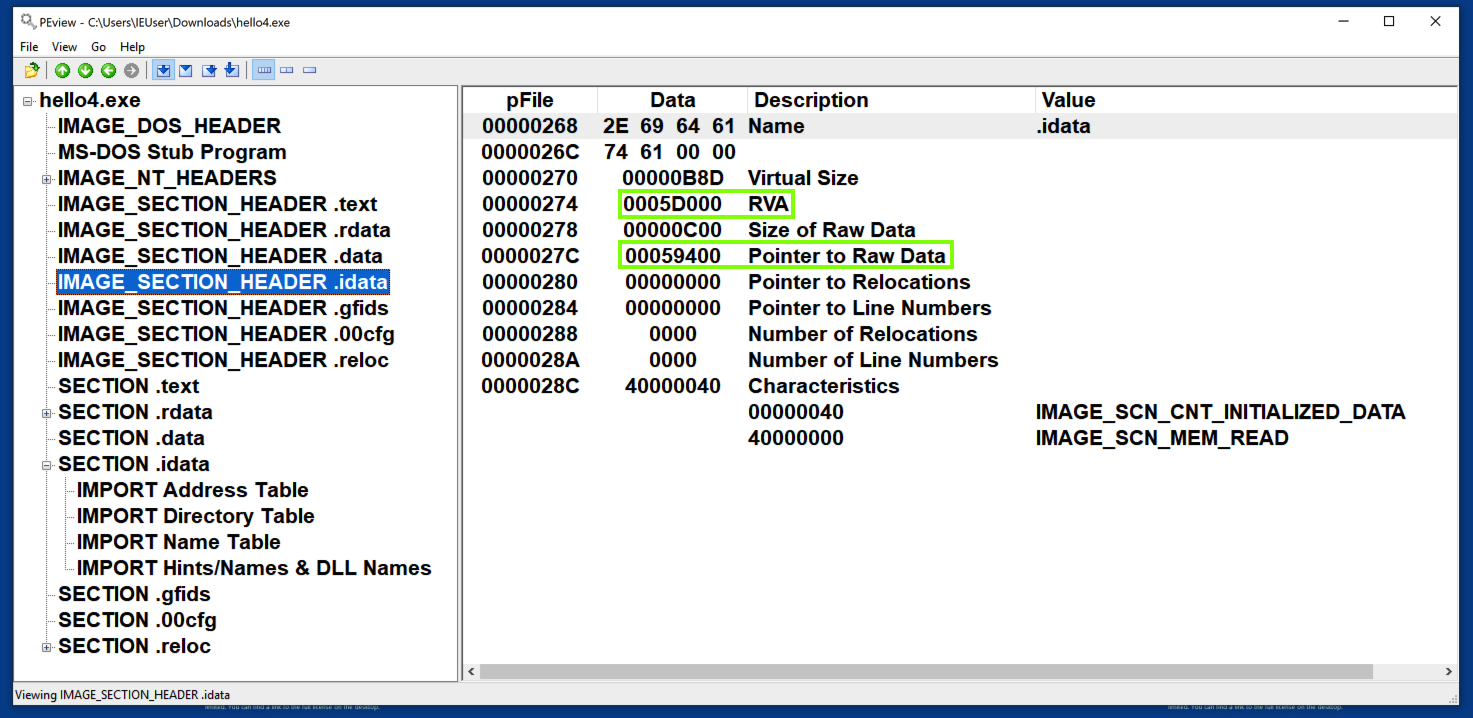
To understand that, examine the IMAGE_SECTION_HEADER for the .idata section.
This section loads at an RVA of 5D000, but the "Pointer to Raw Data" (pFile address) is 59400, 3C00 bytes lower, as shown below.
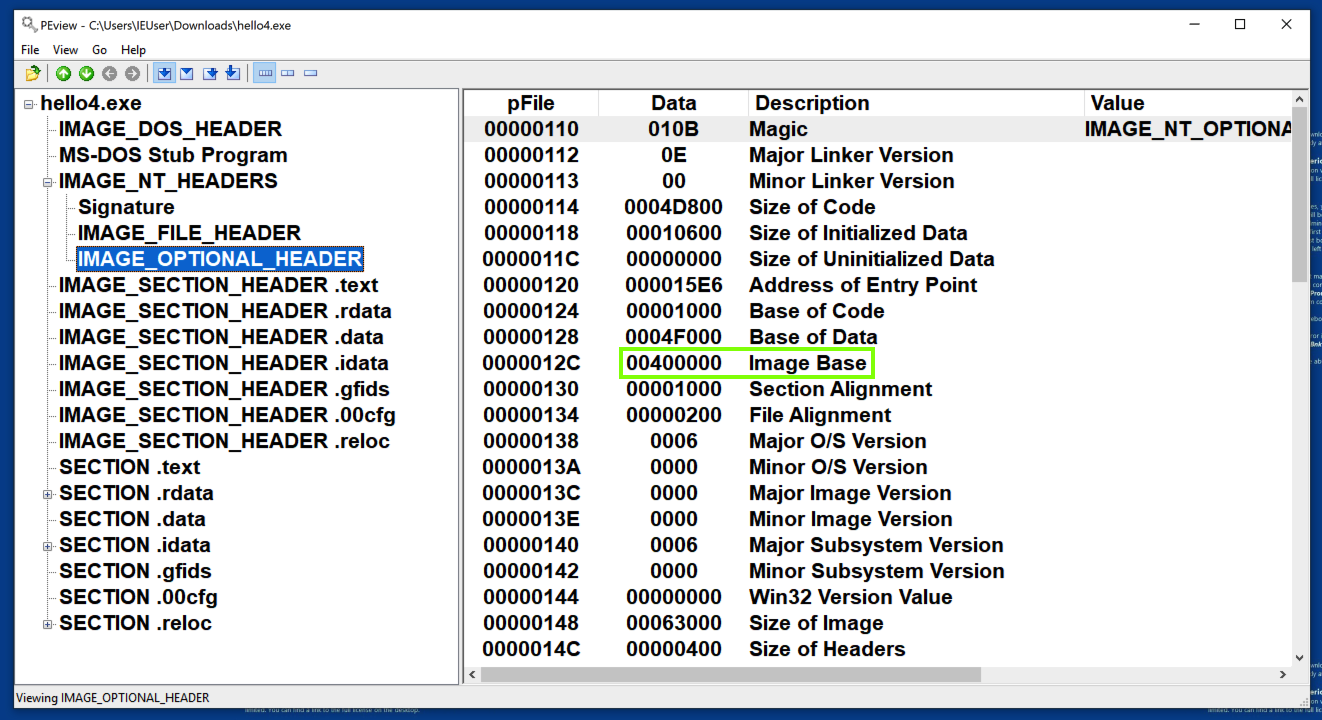
The program loads at a Base Address different from the preferred address of 400000, as shown below. (Your address may be different from the one shown below.)
That's the effect of ASLR, an annoyance we don't need.
https://blog.didierstevens.com/2010/10/17/setdllcharacteristics/
Download the file, as shown below.
Unzip the file you downloaded, and place the setdllcharacteristics.exe in the same folder you have the hello4.exe file in.
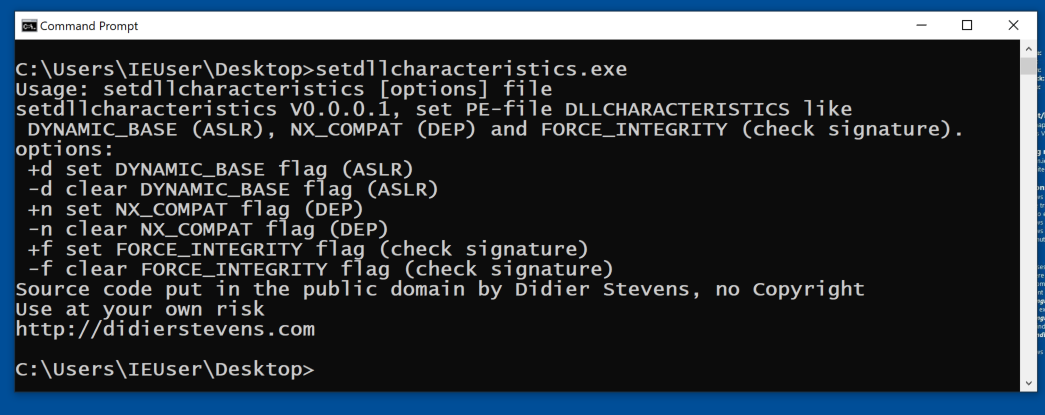
In a Comand Prompt, in that folder, execute this command:
setdllcharacteristics.exe
Close PEview and OllyDbg, if they are still open.
Then, in the Comand Prompt, execute this command:
setdllcharacteristics -d hello4.exe
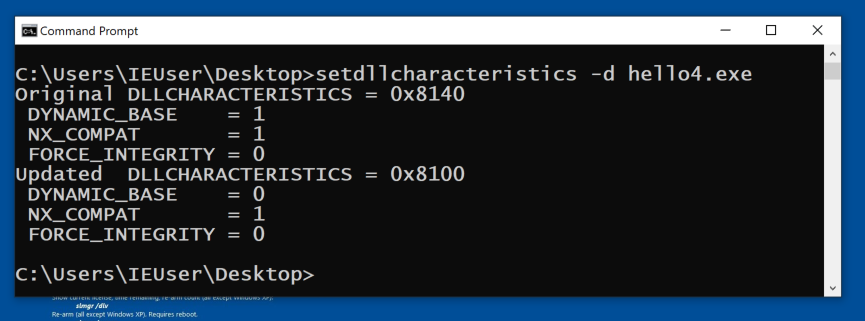
Now the code loads at 400000.
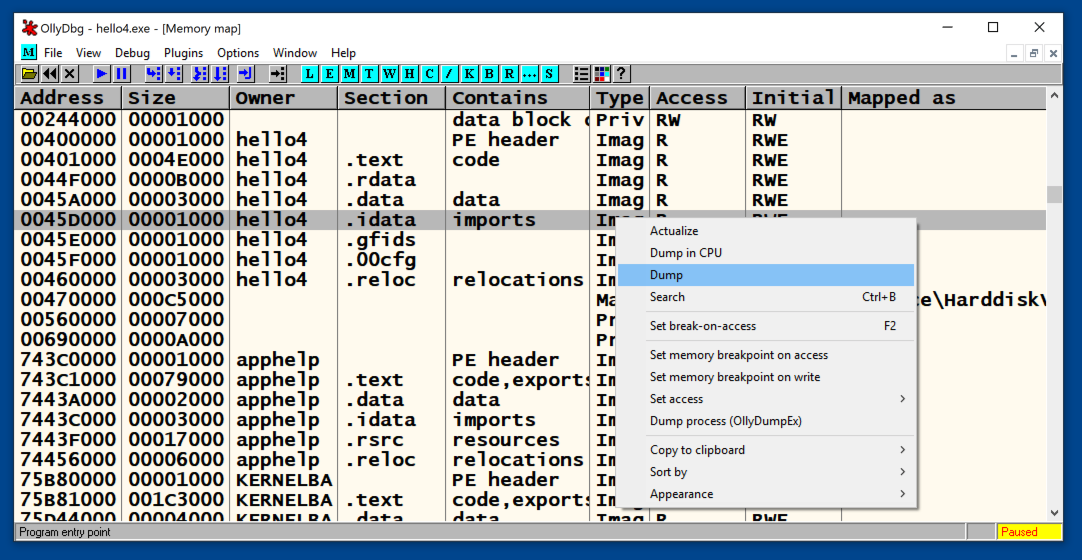
Left-click, then right-click the .idata section, and click Dump, as shown below.
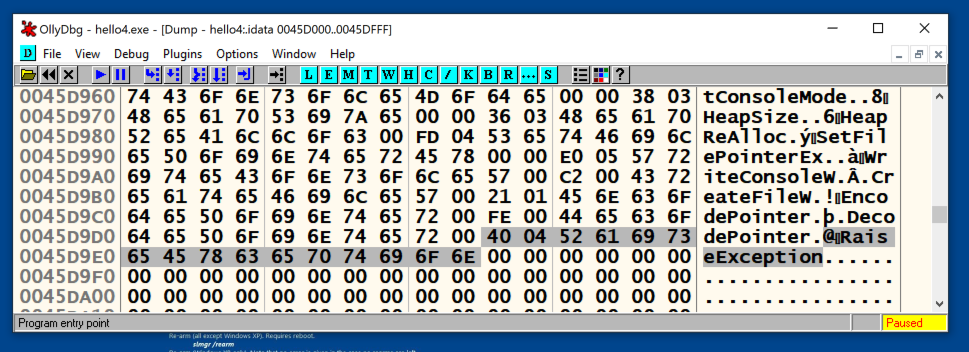
Scroll down and find the RaiseException data, at address 45D9DA, as shown below.
It's easy to see that this location is the RVA of 5D9DA plus the Base Address of 400000.
PMA 123.1: KERNEL32 "Hint" (10 pts)
In PEview, open hello4.exe.Examine the "IMPORT Directory Table", as shown below. Notice the addresses covered by a gray rectangle in the image below.
In OllyDbg, find the text KERNEL32.dll, as shown below.
The flag is the two bytes preceding that text, covered by a green rectangle in the image below.
PMA 123.2: DLL Name (5 pts)
Download this file:The file uses two DLLs. One is KERNEL32.dll. The flag is the name of the other DLL.
PMA 123.3: KERNEL32 Address (10 pts)
Use the same file as the previous challenge.Turn off ASLR, load the file in OllyDbg, and examine the .rdata section.
Find the address of the line containing KERNEL32, which is covered by a green rectangle in the image below.
That's the flag.
Hint: Even with ASLR turned off, this file won't load at 400000. Check the Image Base address in PEview.
PMA 123.4: Broken (20 pts)
Download this file:The file is damaged and cannot run.
Fix it and run it to see the flag.
Hint: here's some of the source code:
Hint: Google the functions in the source code to find out what DLL it comes from.
Posted 9-29-2020
RaiseException address fixed 9-28-2021
References to FLARE-VM removed 9-20-22
Hints added to last two flags 2-27-24
Video added 3-26-25