sudo apt update
sudo apt install gcc make zlib1g zlib1g-dev zlib1g:i386
sudo apt install python build-essential
export "CC=gcc -std=gnu89"
sudo ln -s /usr/lib/x86_64-linux-gnu/libmpfr.so.6 /usr/lib/x86_64-linux-gnu/libmpfr.so.4
cd /tmp
wget https://github.com/upx/upx/archive/master.zip
cd
unzip /tmp/master.zip
cd /tmp
wget http://www.oberhumer.com/opensource/ucl/download/ucl-1.03.tar.gz
cd
mkdir -p local/src
cd local/src
tar xzfv /tmp/ucl-1.03.tar.gz
cd ucl-1.03
./configure "CC=gcc -std=gnu89"
make all
export UPX_UCLDIR=$HOME/local/src/ucl-1.03
cd /tmp
mkdir lzma
cd lzma
wget https://github.com/upx/upx-lzma-sdk/archive/master.zip
unzip master.zip
cd
cd upx-master/src
mv /tmp/lzma/upx-lzma-sdk-master/* lzma-sdk/
cd /tmp
wget https://github.com/upx/upx-stubtools/releases/download/v20160918/bin-upx-20160918.tar.xz
cd
cd local
mkdir bin
cd bin
tar xvf /tmp/bin-upx-20160918.tar.xz
mv bin-upx-20160918 bin-upx
cd
cd upx-master
cd src/stub/src
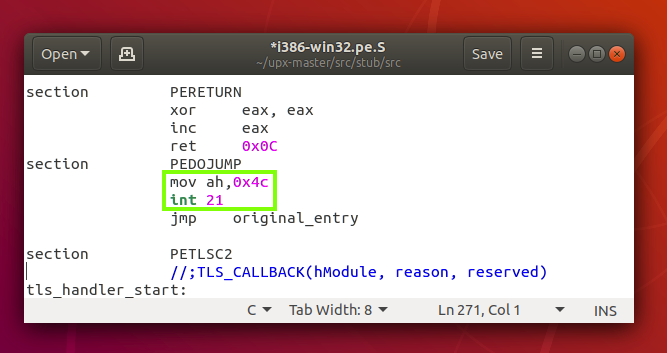
gedit i386-win32.pe.S
mov ah,0x4c
int 21

Save the file. Close gedit.
In the Terminal, execute these commands:
cd ..
make all
cd ../..
make all
src/upx.out
PMA 131.1: Option 1 (10 pts)
Find the word covered by a green box in the image below.That's the flag.
Posted 9-17-2020