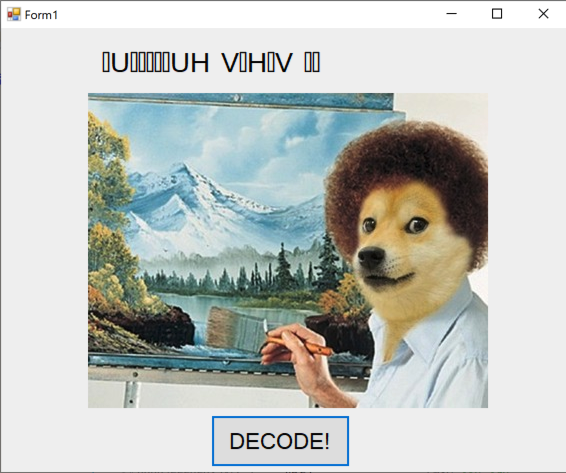
Unzip it to get two files: Challenge1.exe and PMA132.exe.
If a window appears asking you to install DOT NET, do that.
If you are using my "Windows 10 with tools" image, the installation will probably fail. Download and run this offline installer:
Net Framework 3.5 Offline Installer Win_10 V1.1.zip
If you're using Windows 11, do this:

The text changed to unreadable characters. We want to analyze that decoding process.
Close the Challenge program.
The File Type is "Portable Executable 32 .NET Asembly", as shown below.
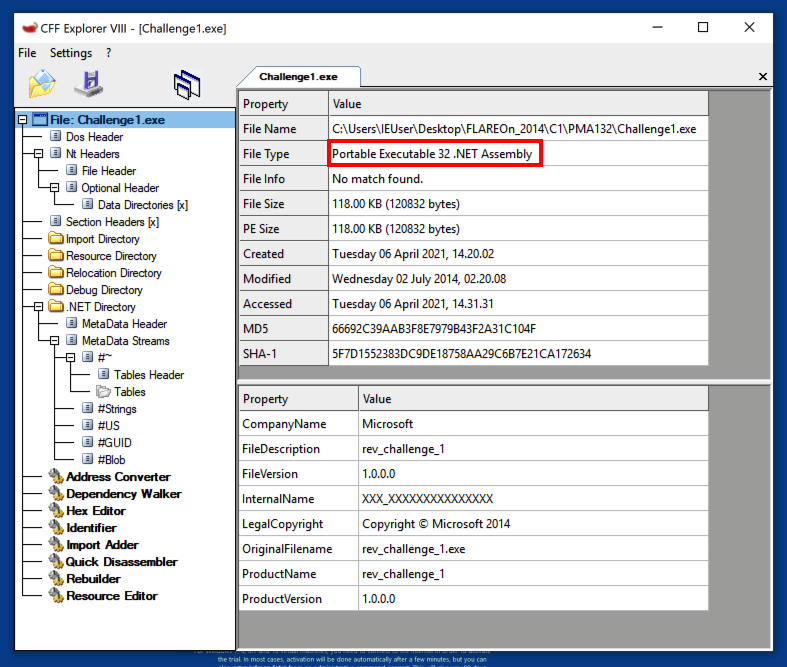
Close CFF Explorer.
To decompile them, we'll use ILSpy.
Launch ILSpy.
If you are prompted to install DotNet Runtime, do that.
In ILSpy, open Challenge1.exe.
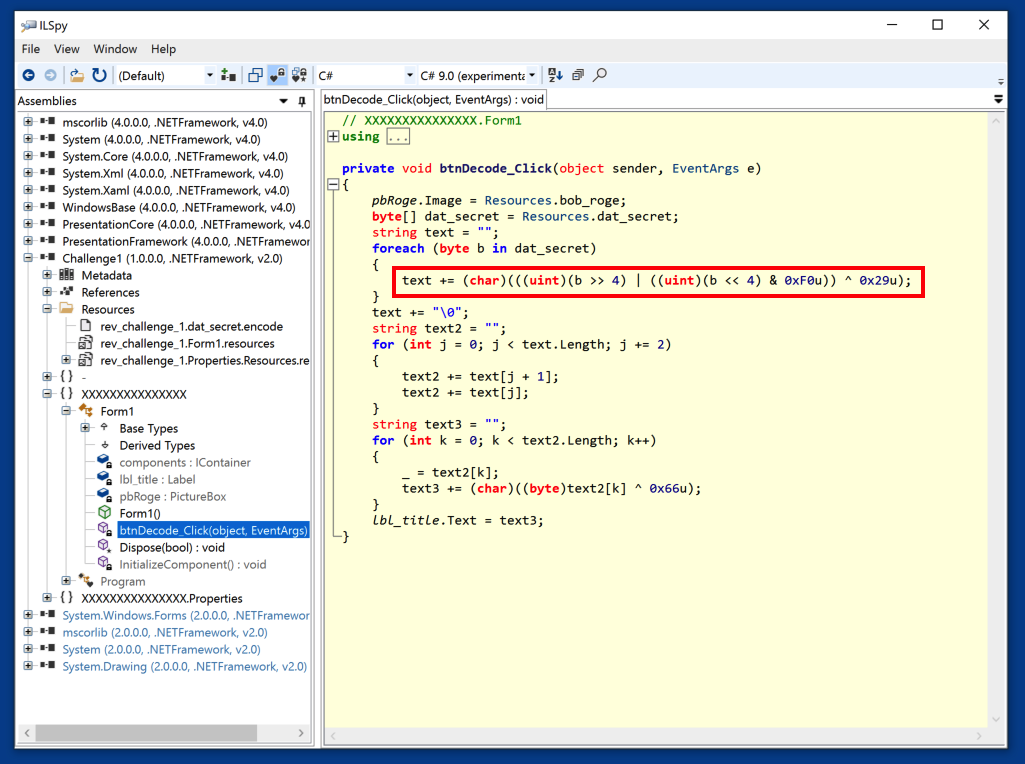
In the left pane, navigate to the btnDecode.Click method and click it.
Decompiled C# code appears in the right pane.
The first decoding step uses the line of C# code outlined in red in the image below.
Now we need to find the input data to decode, which is in the Resource dat_secret.
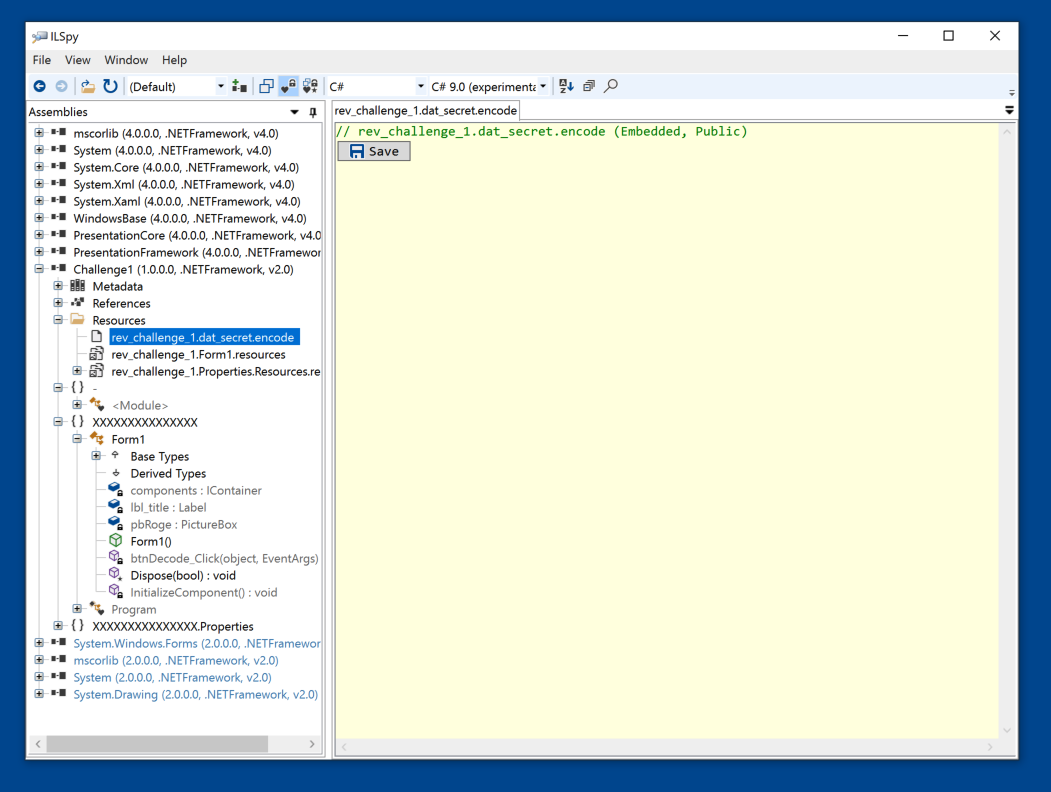
In the left pane, navigate to rev_challenge_1.dat_secret.encode, as shown below, and click it.
In the right pane, click the Save button.
Save the file in the same folder as Challenge1.exe with the name dat_secret
PMA 132.1: Decoding with Python (10 pts)
In Notepad, create a solution.py script, as shown below, and run it to find the flag, which is covered by a green rectangle in the image below.
PMA 132.2: Second File (10 pts)
Repeat the process to find the flag in the PMA132.exe file.Hint: Look carefully at the left pane of ILSpy. It retains old files there unless you manually remove them.
It's easy to keep looking at the old file when you are trying to analyze a new one.
PMA 132.3: MemeCat (20 pts)
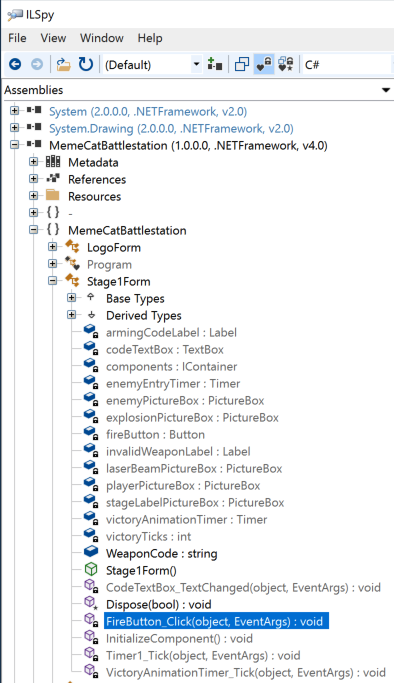
Download this file:The game asks for two "weapon arming codes". To find them, examine the two methods shown below.
After entering both the correct arming codes and shooting the enemies, you win, revealing the flag, covered by a green box in the image below.
Posted 4-6-2021
References to FLARE-VM removed and software installation instructions added 11-9-21
Minor updates to links 11-1-22
.NET offline installer link added 6-21-23
.NET link updated to use my server 3-17-25
.NET install intructions for Windows 11 added 3-17-25
Minor text updates, video added, 3-27-25