https://www.bowneconsultingcontent.com/pub/EH/proj/cloud/ED301c_tkp/ED301c_tkp.htm
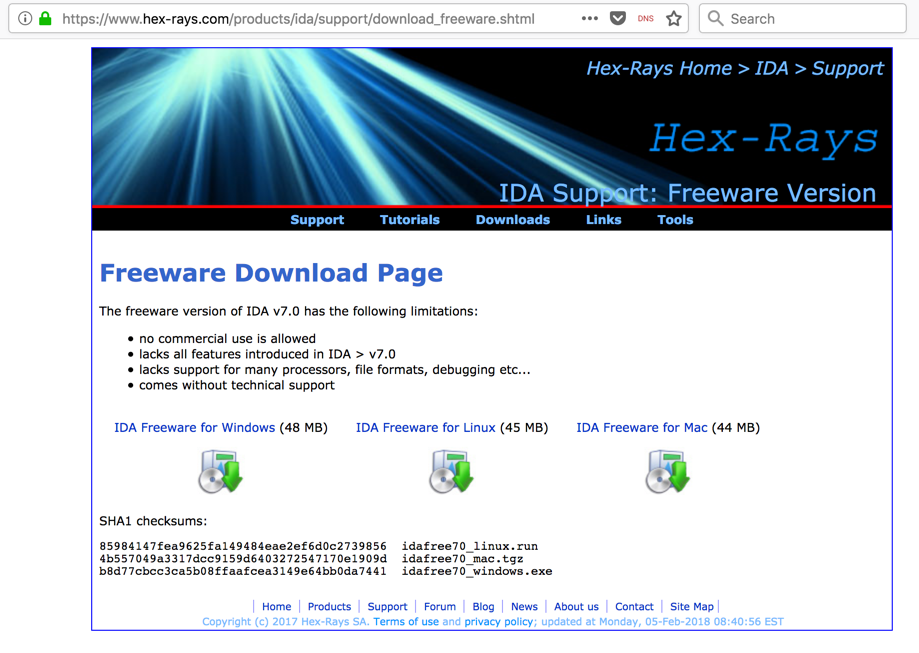
https://www.hex-rays.com/products/ida/support/download_freeware.shtml
Click the "IDA Freeware for Windows" link, as shown below.

Install the software with the default options.
In the Developer Command Prompt window, execute these commands:
mkdir c:\decomp
cd c:\decomp
notepad print.cpp
#include <iostream>
using namespace std;
void main()
{
printf("%d %s\n", 2, "HELLO");
}
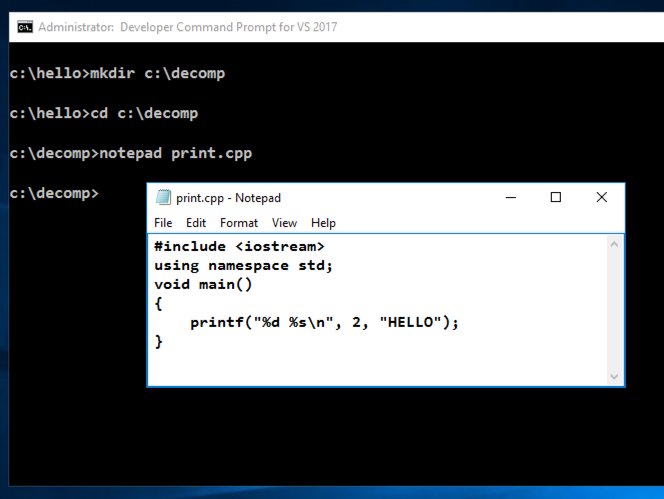
In Notepad, click File, Save.
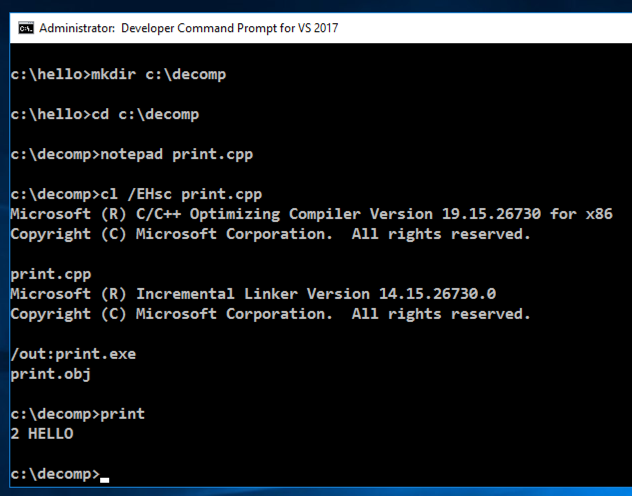
In the Developer Command Prompt window, execute these commands:
cl print.cpp
print
2 HELLO
as shown below.
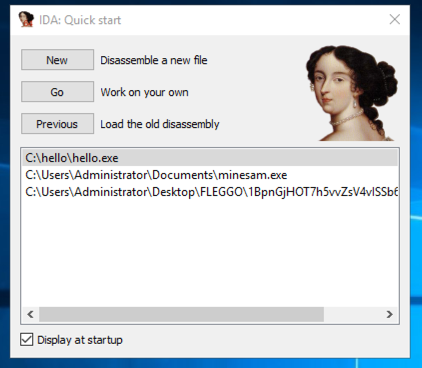
In the "IDA Quick start" box, click the New button, as shown below.
In the "Select file" box, navigate to C:\decomp and double-click print.
In the "Load a new file" box, click OK.
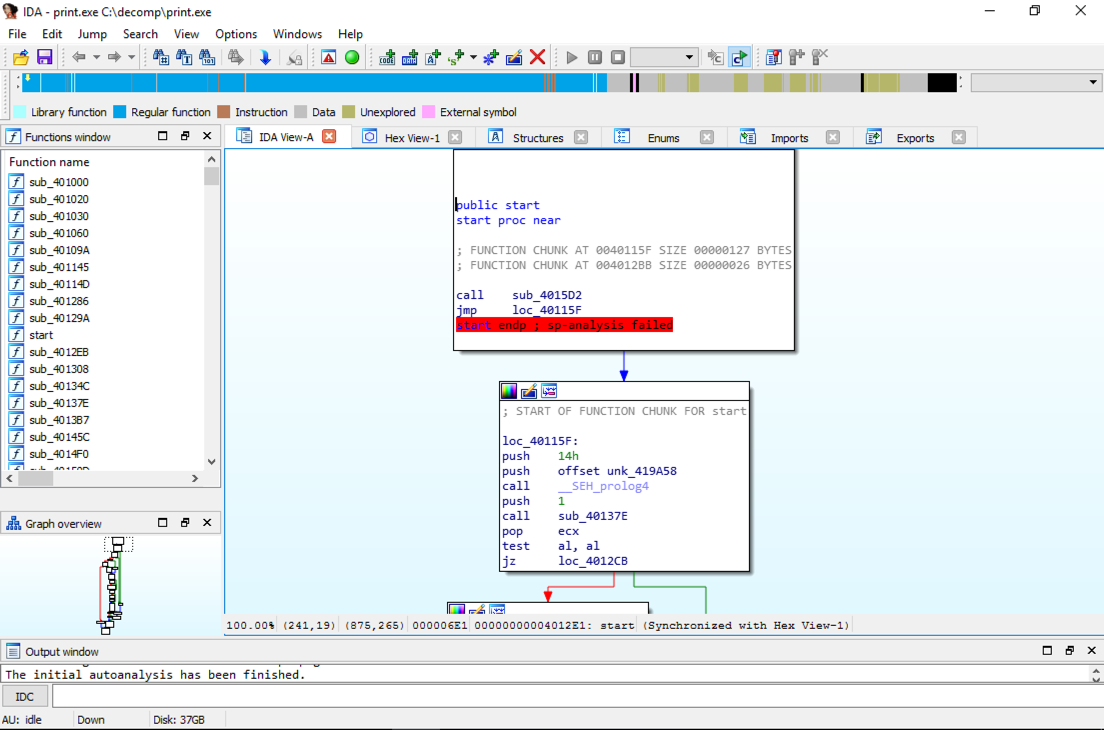
IDA opens, showing some of the code that launches print, as shown below.
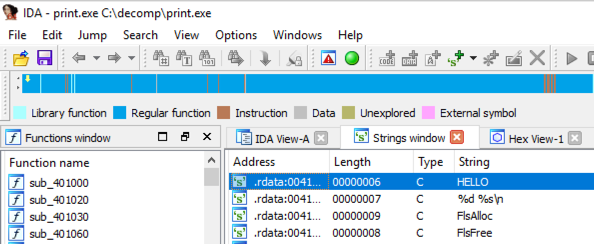
From the IDA manu bar, click View, "Open subviews", Strings. In the Strings pane, double-click HELLO, as shown below.
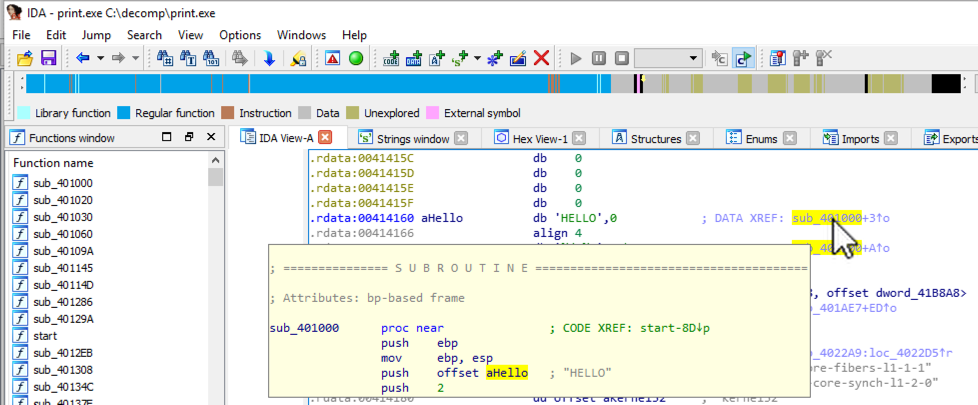
The address in the rdata section where that string is stored appears, as shown below. On the right side, point to the address labelled "DATA XREF". The code that uses this string appears in a pop-up box, as shown below.
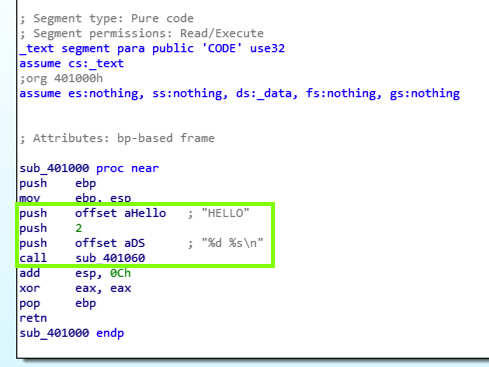
Double-click the address labelled "DATA XREF". The assembly code appears, as shown below.
The assembly code in the green box performs this C command:
printf("%d %s\n", 2, "HELLO");
cd c:\decomp
notepad glob.cpp
#include <iostream>
using namespace std;
int g=2; // GLOBAL VARIABLE
void main()
{
int l = 3; // LOCAL VARIABLE
printf("%d %d\n", g, l);
}
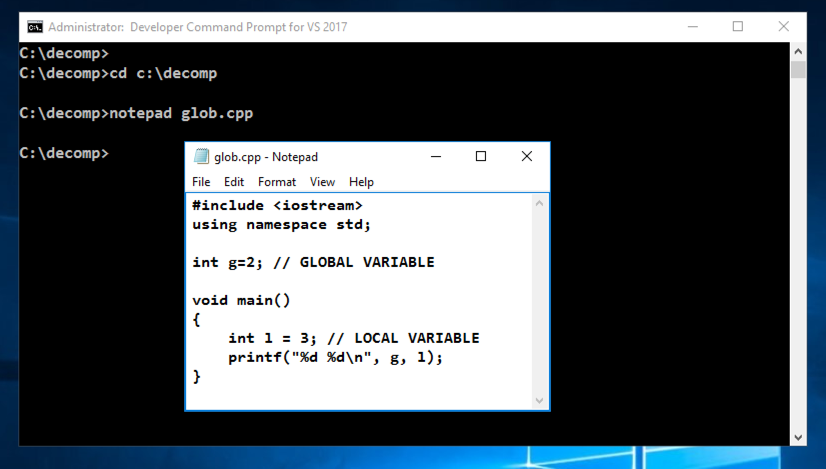
In Notepad, click File, Save.
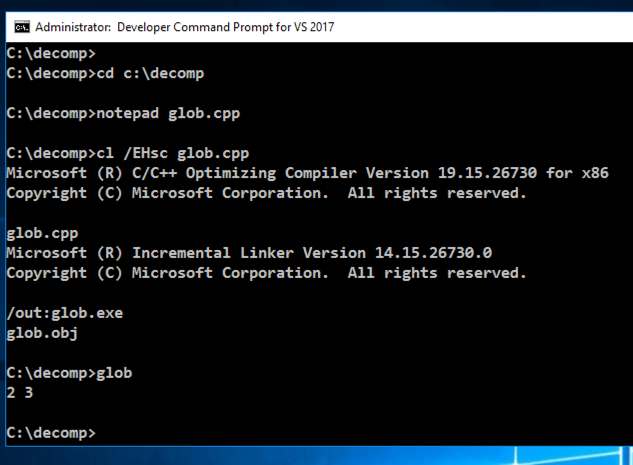
In the Developer Command Prompt window, execute these commands:
cl glob.cpp
glob
2 3
as shown below.
In the "Save database" box, check "DON'T SAVE the database" and click OK.
In the "Select file" box, navigate to C:\decomp and double-click glob.
In the "Load a new file" box, click OK.
IDA opens, showing the launcher.
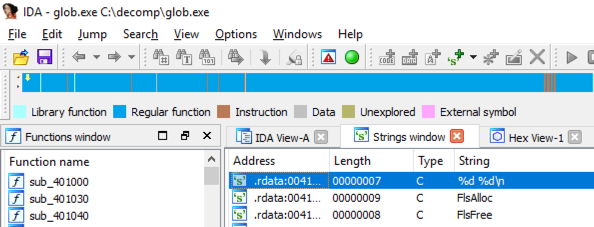
From the IDA manu bar, click View, "Open subviews", Strings.
In the Strings pane, double-click "%d %d\n", as shown below.
On the right side, point to the address labelled "DATA XREF". The code that uses this string appears in a pop-up box, as shown below.
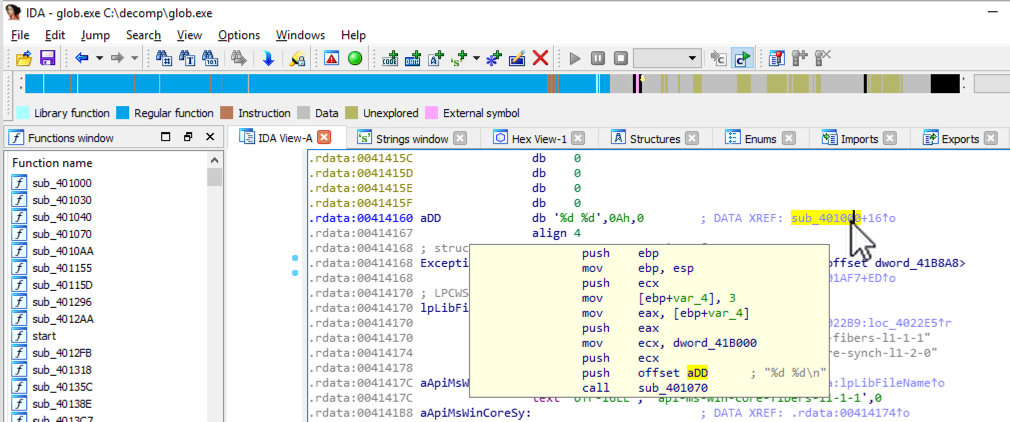
Double-click the address labelled "DATA XREF". The assembly code appears, as shown below. Notice these features:
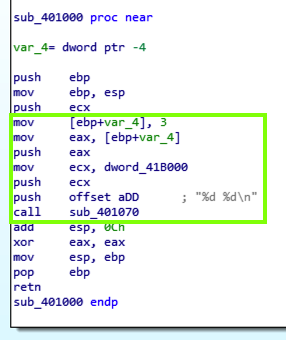
PMA 304.1: Analyzing an Unknown Binary (15 pts)
Download this file:Disassemble it in IDA Pro. Find the code shown below.
Find the value covered by a green box in the image below. That's the flag.
Posted: 10-2-18
Link to Visual C++ Build Tools instructions added 4-6-21
Windows 10 w Tools info added 9-28-2021
cl switch removed, format updated 11-16-21
Video added 4-22-24