http://www.rohitab.com/apimonitor
On the right side, in the Contents box, click Download.
Install the 64-bit version.
Launch API Monitor (64-Bit).
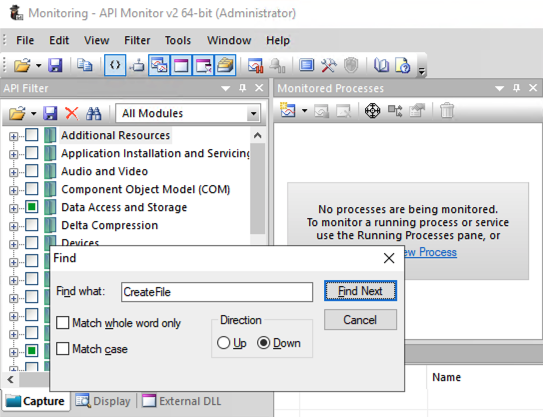
Search for CreateFile, as shown below.

Click the "Find Next" button.
There are a lot of API calls containing that string.
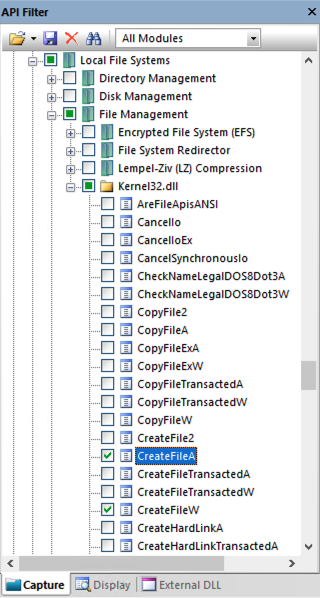
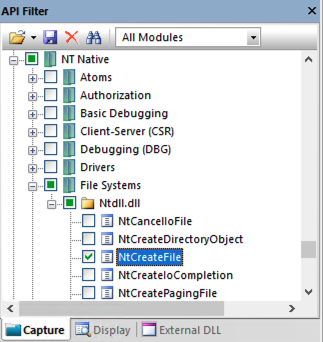
Find and check these three, as shown below.
Kernel32!CreateFileA
Kernel32!CreateFileW
ntdll!NtCreateFile
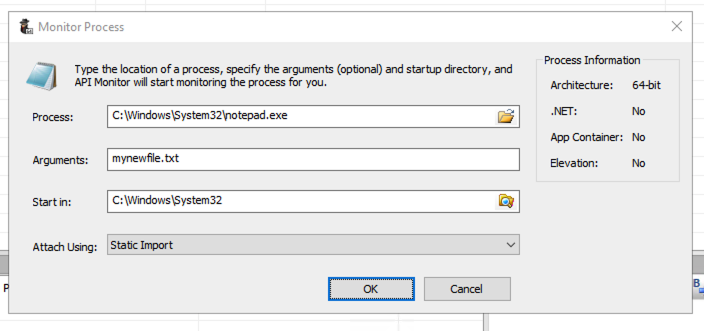
In the "Monitor Process" box, in the Process field, click the yellow folder icon.
Browse to
C:\Windows\System32\notepad.exe
and double-click it.
In the Arguments field, enter mynewfile.txt as shown below.
Click OK.
A Notepad box pops up, as shown below asking if you want to create a new file.
Click Yes.
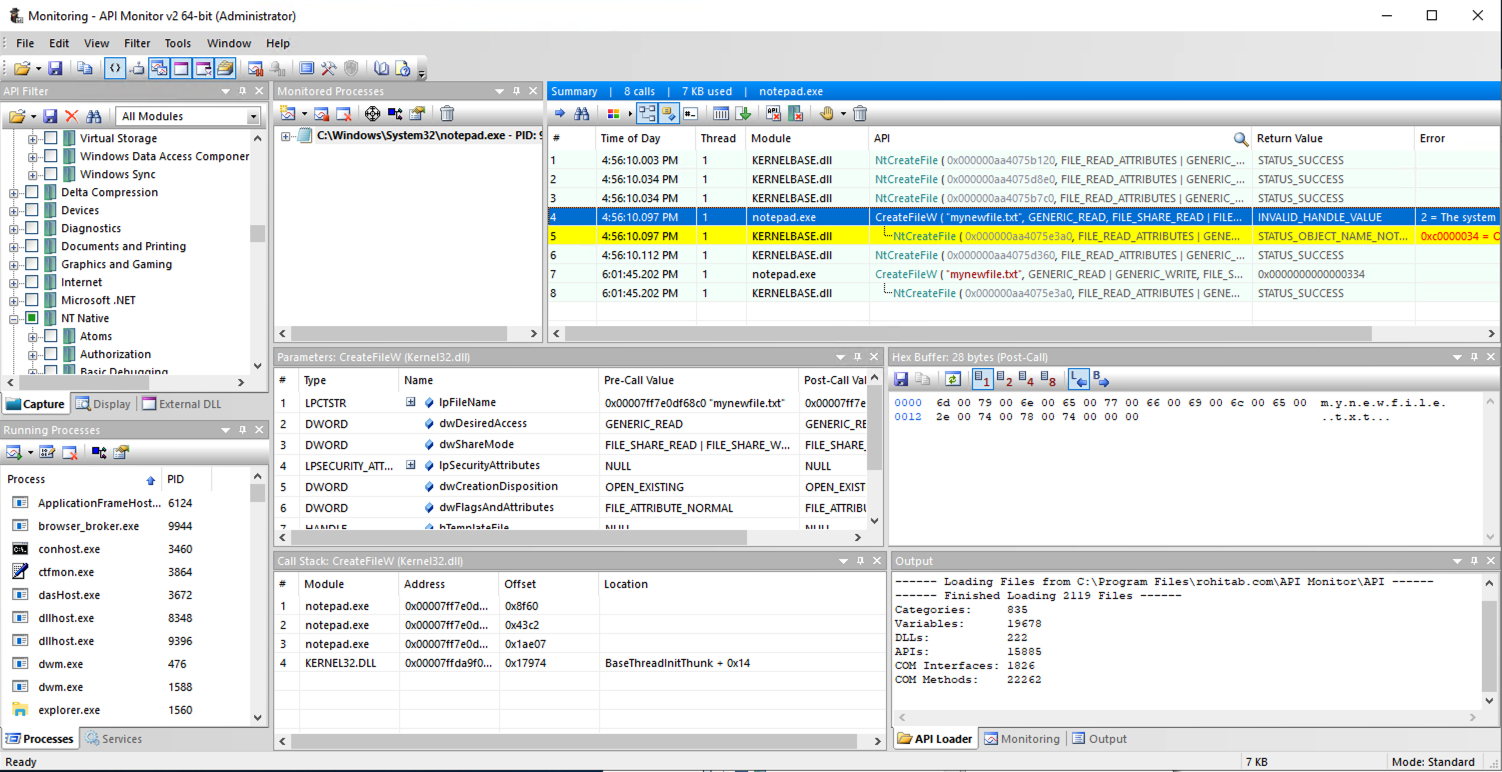
At the top right, the Summary pane shows the API calls Notepad made, as shown below.
Click one of those calls. The Parameters pane shows the layout of the parameters, and their values pre-call and post-call.
PMA 403.1 dwFlagsAndAttributes (5 pts)
In the Summary pane, click the last call to CreateFileW, the call that returned a numerical value (a handle).In the Parameters pane, find the Post-Call Value of the dwFlagsAndAttributes parameter, covered by a green box in the image below. That's the flag.
Note: One student had a Windows 10 machine that did not have any API calls to CreateFileW during this process, and could not find this flag. If that happens, try using this version of notepad:
Unzip it and run it.
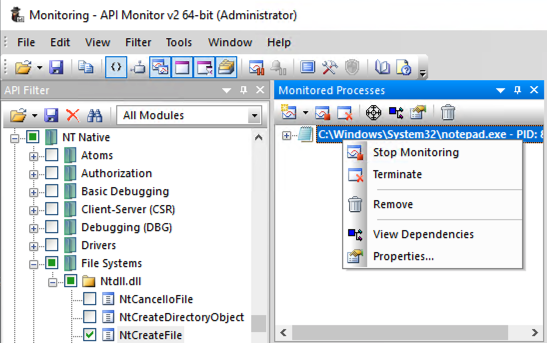
Right-click notepad again and click Remove.
A "Confirmation Remove Process" box pops up.
Click "Yes, Remove Process".
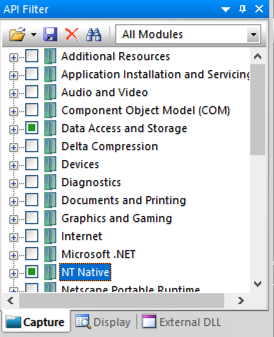
Click in the boxes containing green squares to clear them, as shown below.
One simple way to get that is to create a second Azure Windows 10 machine.
You can also my server:
wind.samsclass.info
In the first box, at the bottom, click "Show options".
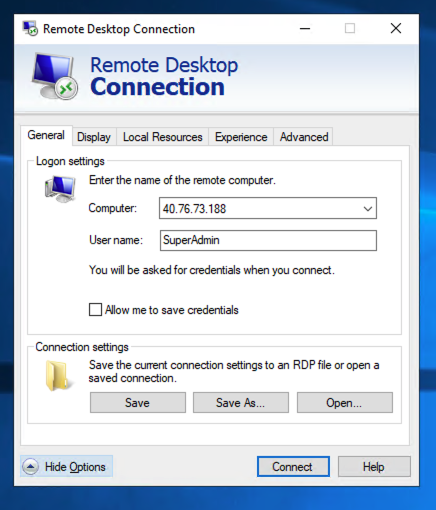
Enter the IP address and user name for your server, as shown below.
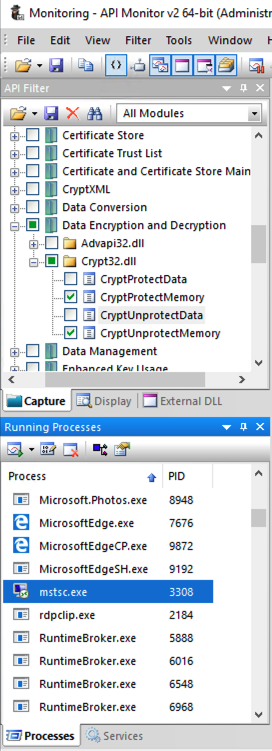
In the "API Capture Filter" pane, check the two items shown below.
Enter anything for the password and click OK.
PMA 403.2 dwFlags (10 pts)
In the Summary pane, click one of the captured API calls.Look in the Hex Buffer pane for your password.
If it's not there, try another captured API call.
When you see your password in the Hex Buffer pane, the flag appears in the Parameters pane, covered by a green box in the image below.
Posted 10-19-20
Note about missing Notepad flag added 3-23-21
My server name added 8-1-2021
Background color changed 2-26-24