Proj 10: Analyzing Malicious Windows Programs (Lab 7-1) (15 pts.)
What you need:
- A Windows XP or Windows 7 machine with IDA PRO
- The textbook: "Practical Malware Analysis"
Purpose
You will practice the techniques in chapter 7.
You should already have the lab files, but if
you don't, do this:
Downloading the Lab Files
In a Web browser, go here:
http://practicalmalwareanalysis.com/labs/
Download and unzip the lab files.
Analyzing the Malware
Follow the instructions for Lab 7-1 in the
textbook. There are more detailed solutions
in the back of the book.
You will see these features:
- A persistence mechanism
- A mutex
- A host-based signature
- A network-based signature
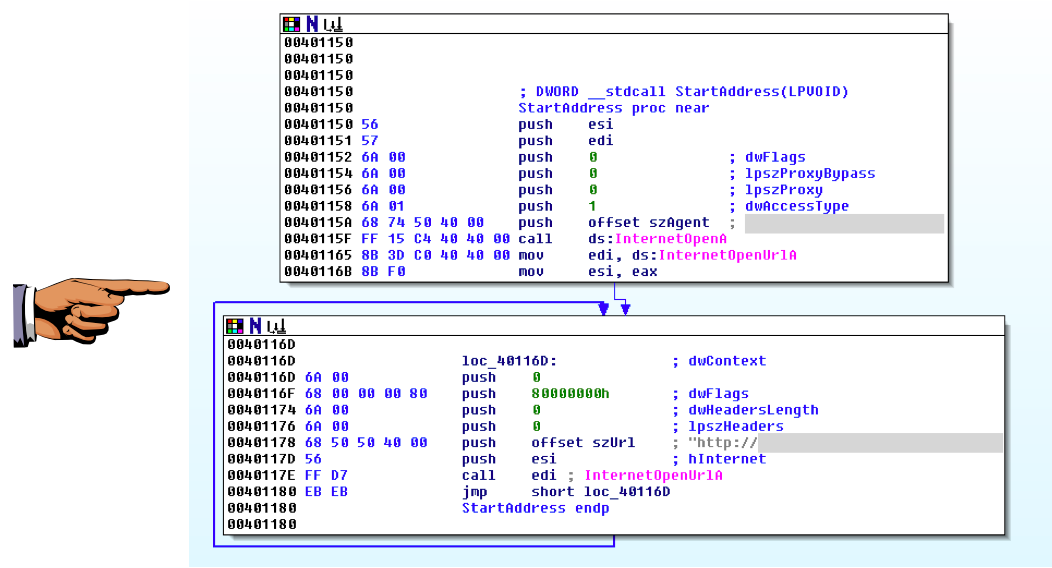
This malware uses a function named StartAddress
to perform a DDoS attack.
When answering Q: 4, you find the user agent it uses
to perform the attack, and the URL it will attack.
Save a screen capture of the IDA Pro
screen showing those two values,
as shown below (with the
important items grayed out).
Save this image with the filename
"Proj 10 from YOUR NAME".
Turning in your Project
Email the image
to cnit.126sam@gmail.com with the subject line:
Proj 10 from YOUR NAME
Last modified 5-14-16

