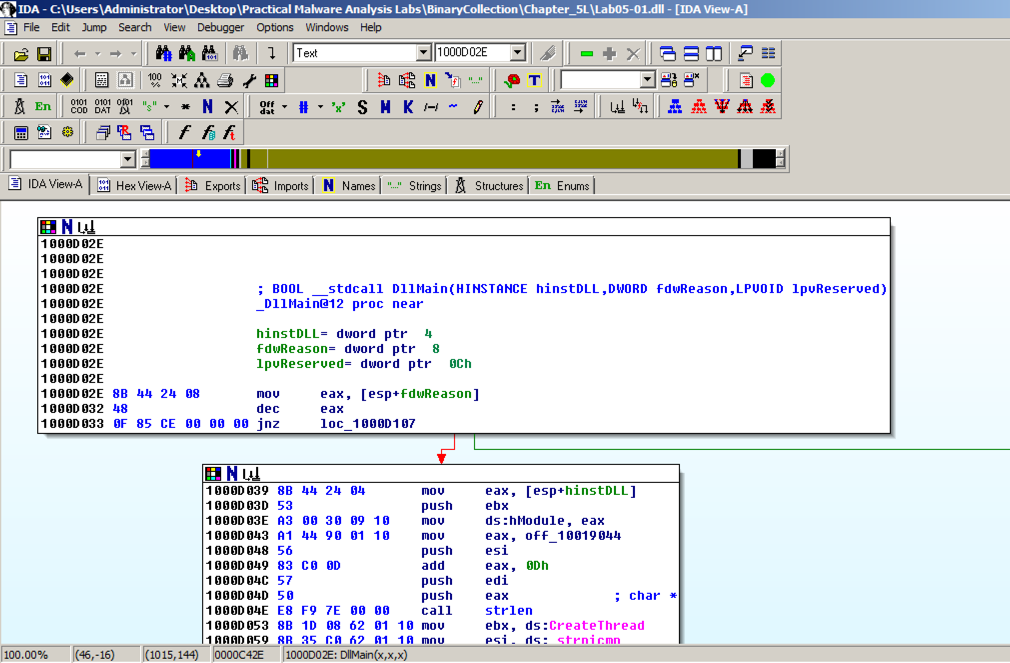
In the "Welcome to the PE Dynamic Library file loading Wizard" box, click Next , Next , Finish .在“欢迎使用PE动态库文件加载向导”框中,单击下一步 , 下一步 , 完成 。 IDA opens the file, as shown below: IDA打开该文件,如下所示:

The code doesn't show line numbers or hexadecimal instructions.该代码不显示行号或十六进制指令。 To fix that, click Options , General .要解决该问题,请单击选项 , 常规 。
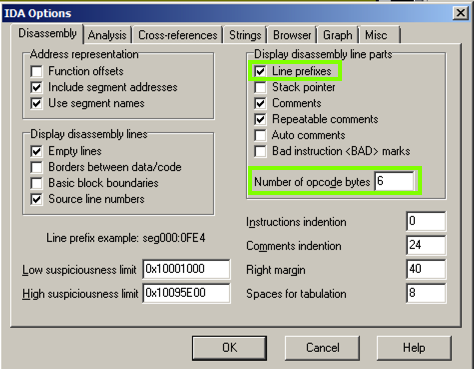
In the IDA Options box, in the top right, in the '"Display disassembly line parts" pane, make these changes, as shown below:在IDA选项框右上角的'“显示反汇编行部分”窗格中,进行这些更改,如下所示:
The "graph mode" display is more informative now, as shown below. “图形模式”显示现在更具信息性,如下所示。
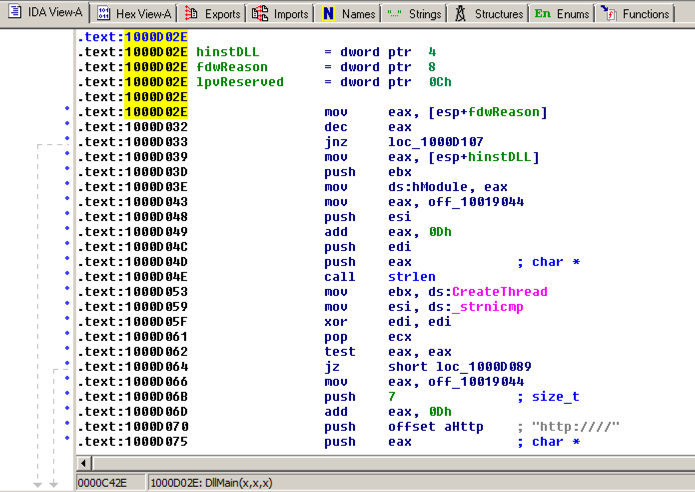
IDA shows the assembly code in a text-only view, as shown below. IDA在纯文本视图中显示汇编代码,如下所示。
Press the SPACEBAR again to return to Graph Mode.再次按空格键返回到图形模式。
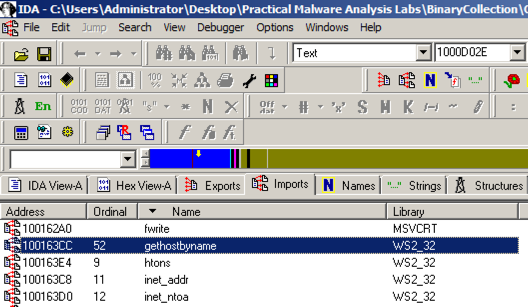
In IDA Pro, click View , " Open subview ", Imports .在IDA Pro中,单击查看 ,“ 打开子视图 ”, 导入 。 Click the Name header to sort by name.点击名称标题按名称排序。 Find "gethostbyname", as shown below.找到“gethostbyname”,如下所示。 (Note that capital letters and lowercase letters sort into separate groups.) (请注意,大写字母和小写字母分为不同的组。)
Double-click gethostbyname .双击gethostbyname 。
The code for the function opens in Text mode, as shown below.该功能的代码以文本模式打开,如下所示。
Click gethostbyname .点击gethostbyname 。 Yellow highlights appear on both occurrences of that name, as shown below.黄色突出显示出现在该名称的两次出现中,如下所示。 Press Ctrl+x to open the "xrefs to gethostbyname" box shown below.按下Ctrl + x打开下面显示的“xrefs to gethostbyname”框。
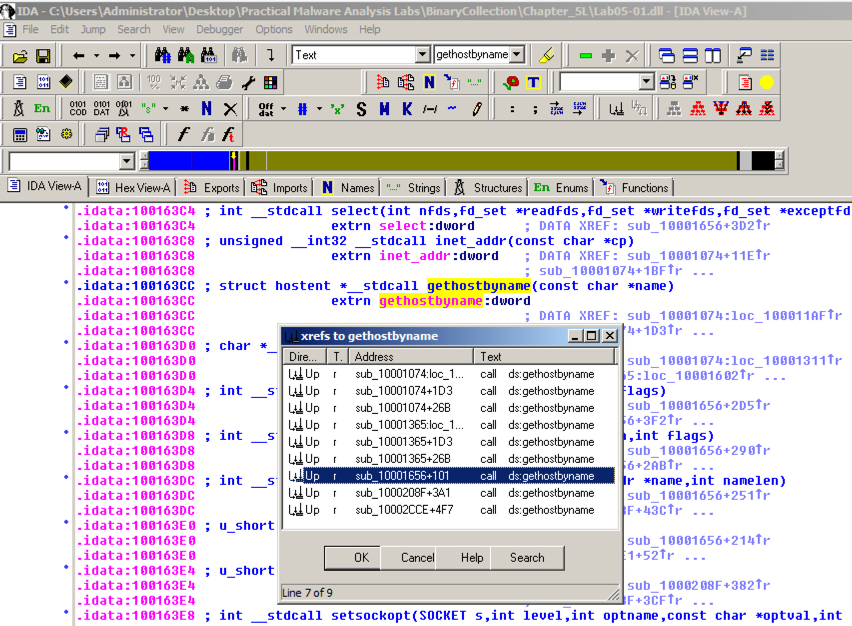
There are nine calls to gethostbyname in five different functions.在五个不同的函数中有9个对gethostbyname的调用。 Double-click the third one from the bottom, at an address of 1001656+101 , as highlighted in the image above.双击底部第三个,地址为1001656 + 101 ,如上图所示。
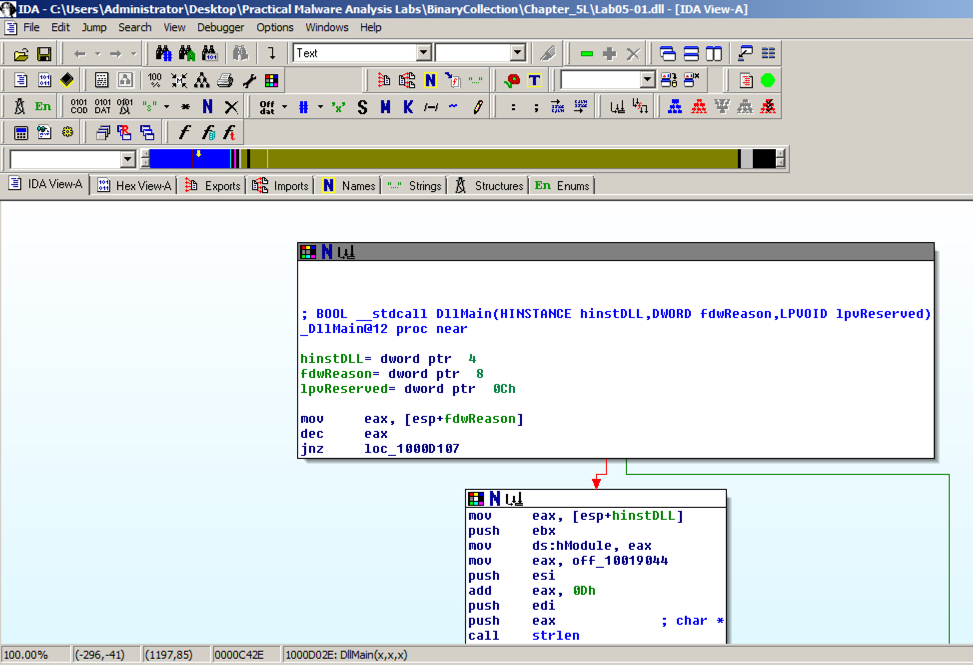
The function appears, as shown below.该功能出现,如下所示。 It loads an address named off_10019040 into register eax, adds 13 to it (0d in hexadecimal), pushes that address onto the stack, and calls gethostbyname.它将一个名为off_10019040的地址加载到寄存器eax中,并将其添加13(十六进制中的0d),将该地址压入堆栈并调用gethostbyname。
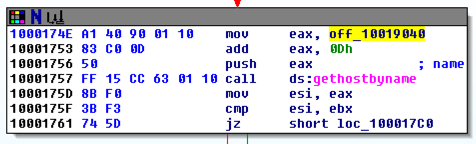
Double-click off_10019040 .双击off_10019040 。
The Text view shows that this location contains a pointer to a string containing "praticalmalwareanalys", as shown below. Text视图显示这个位置包含一个指向包含“praticalmalwareanalys”的字符串的指针,如下所示。
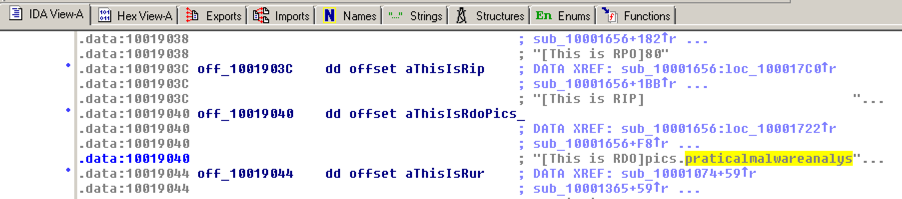
For a clearer view, click the " Hex View-A " tab.要获得更清晰的视图,请单击“ 十六进制视图-A ”选项卡。
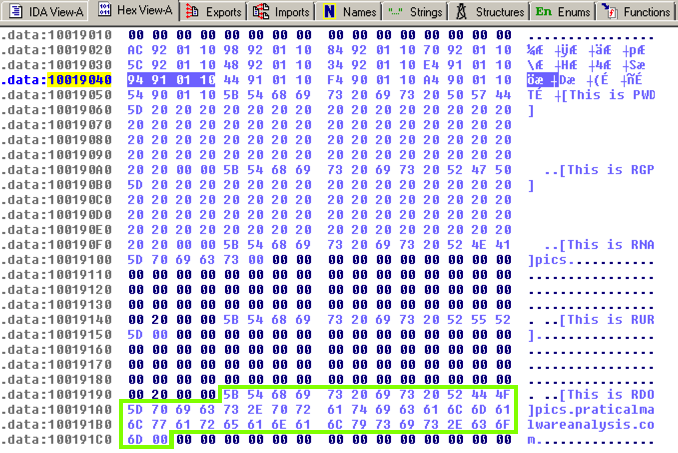
The four bytes starting at 10019040 contain a 32-bit address in little-endian order, as highlighted in blue in the figure below.从10019040开始的四个字节以小端顺序包含一个32位地址,如下图蓝色部分所示。 That address is 10019194. There's a series of ASCII values at that address, outlined in green in the figure below.该地址为10019194.该地址有一系列ASCII值,如下图绿色部分所示。 Skipping the first 13 bytes leaves the string跳过前13个字节会留下字符串
pics.praticalpalwareanalysis.com pics.praticalpalwareanalysis.com
as shown below.如下所示。 This is the domain that will be resolved by calling gethostbyname.这是将通过调用gethostbyname来解决的域。
Scroll down about 3/4 of the way, and find the String " \\cmd.exe /c ", as highlighted in the image below.向下滚动大约3/4的路径,并找到字符串“ \\ cmd.exe / c ”,如下图所示。
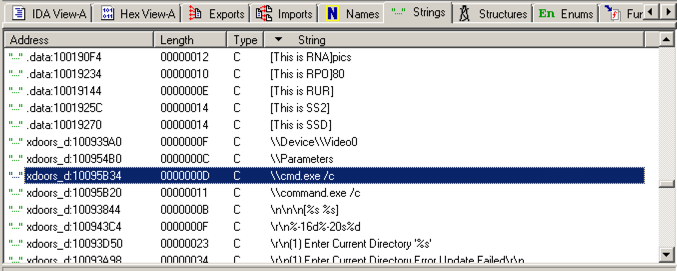
Double-click " \\cmd.exe /c ".双击“ \\ cmd.exe / c ”。 Click the "b>IDA View-A " tab.点击“b> IDA View-A”选项卡。
The string appears in text mode, as shown below.该字符串以文本模式显示,如下所示。 Click in the word cmd so it's highlighted and press Ctrl+x .单击cmd一词,使其突出显示,然后按Ctrl + x 。 A "xrefs to aCmd_exeC" box appears, as shown below.出现“外部参照aCmd_exeC”框,如下所示。
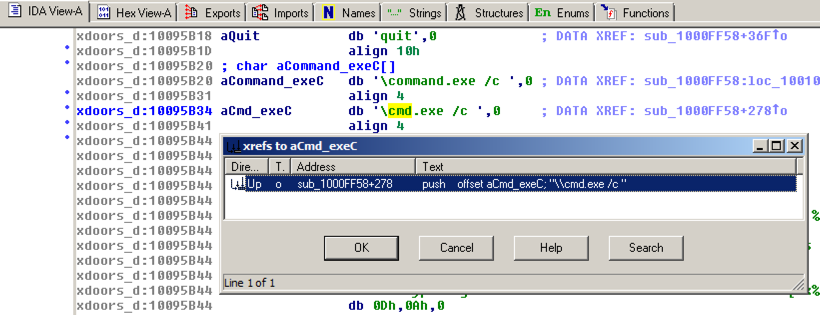
In the "xrefs to aCmd_exeC" box, double-click sub_1000FF58+278 .在“xrefs to aCmd_exeC”框中,双击sub_1000FF58 + 278 。
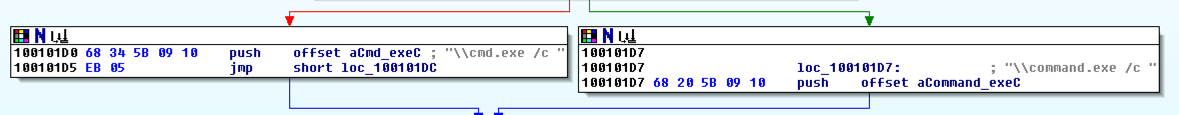
You see the code that uses this string.您会看到使用此字符串的代码。 There are two boxes of code, one that starts a string with "cmd.exe -c" and the other that starts it with "command.exe /c".有两个代码框,一个用“cmd.exe -c”启动一个字符串,另一个用“command.exe / c”启动它。 This looks like a remote shell, executing commands from the botmaster for either a 32-bit or 16-bit system.这看起来像一个远程shell,执行来自botmaster的32位或16位系统的命令。
Drag the code boxes down to see the module containing " Hi, Master ", as shown below.向下拖动代码框以查看包含“ Hi,Master ”的模块,如下所示。
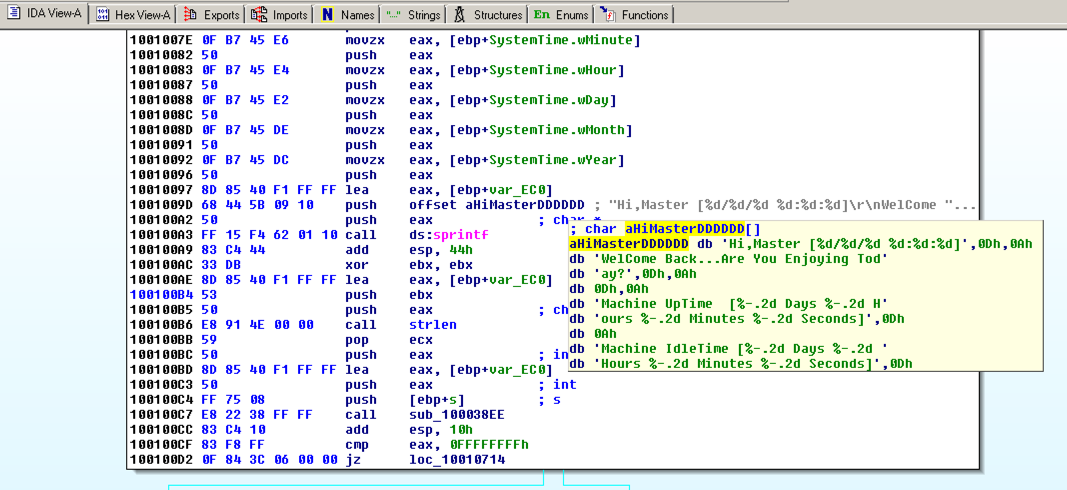
Hover the mouse over aHiMasterDDDDDD to see more of the referenced strings, as shown below.将鼠标悬停在aHiMasterDDDDD上以查看更多引用的字符串,如下所示。
This looks like a message the bot sends to the botmaster, further confirming that this is a RAT (Remote Administration Tool).这看起来像是机器人发送给botmaster的消息,进一步确认这是一个RAT(远程管理工具)。