YOU MUST SUBMIT WHOLE-DESKTOP IMAGES TO GET FULL CREDIT!

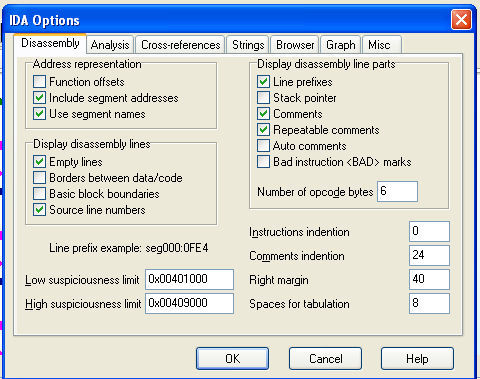
Click Options, General.
Check "Line Prefixes" and set the "Number of opcode bytes" to 6, as shown below.
Find the code shown below, near the start of main():
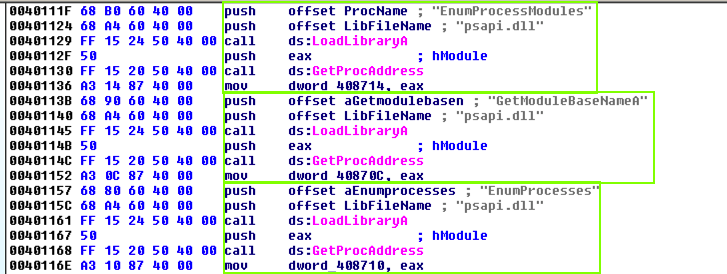
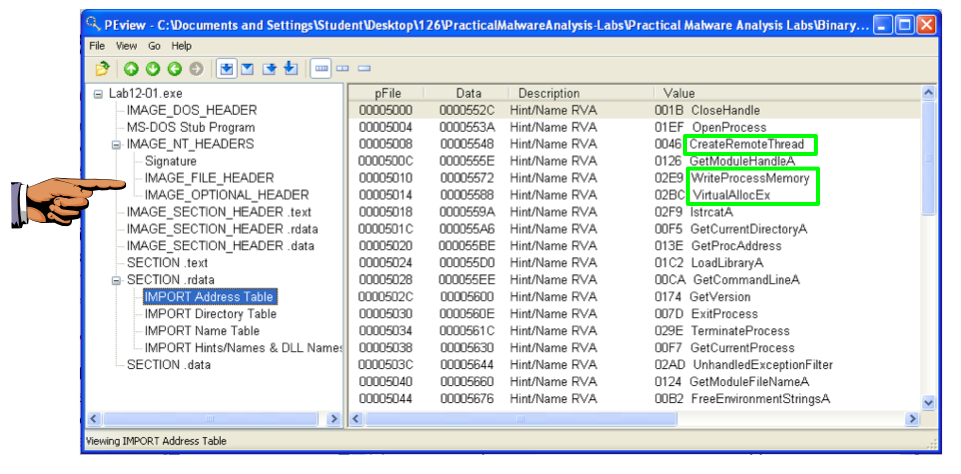
This code uses psapi three times to locate a Windows API function and store its address in a numerical address. This obfuscates the code, so later calls to these functions will be difficult to recognize.
We'll assign labels to these memory addresses in IDA Pro to make later analysis easier.
The first section of code assigns a pointer to the function EnumProcessModules.
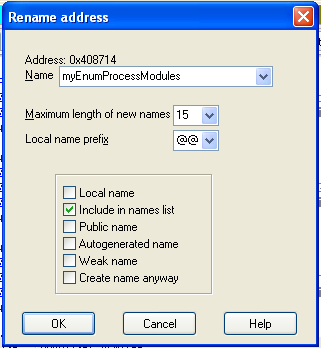
In the line starting with address 00401136, right-click dword_408714 and click Rename.
Enter a new Name of myEnumProcessModules in the box, as shown below. Click OK.
Increase the length limit when you are prompted to.
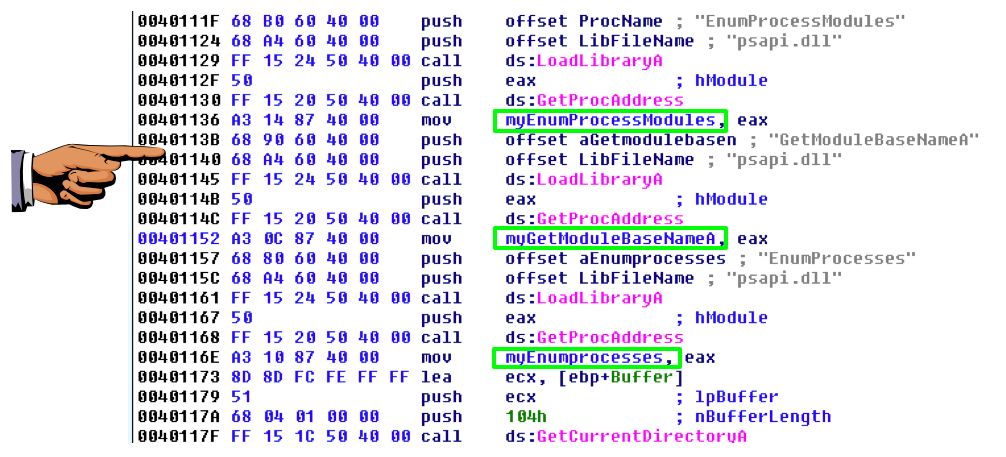
Repeat the process to rename dword_40870C to myGetModuleBaseNameA
Repeat the process to rename dword_408710 to myEnumProcesses
Save an image showing the three renamed locations, as shown below, with the filename "Proj 15c from YOUR NAME".
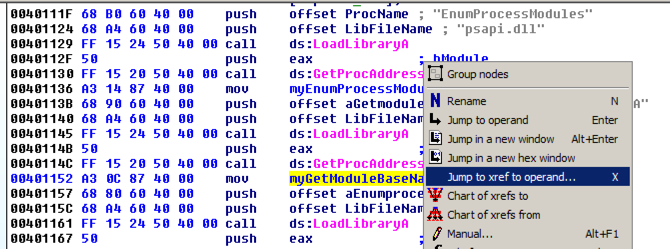
Right-click myGetModuleBaseNameA and click "Jump tp xrefs of operand", as shown below:
An xrefs box pops up, as shown below, showing that this address is only used once, in sub_401000.
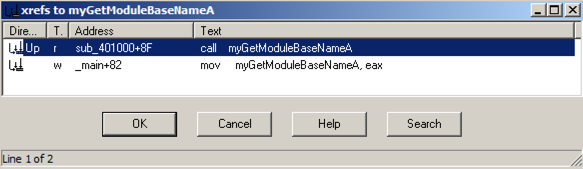
In the xrefs box, click OK.
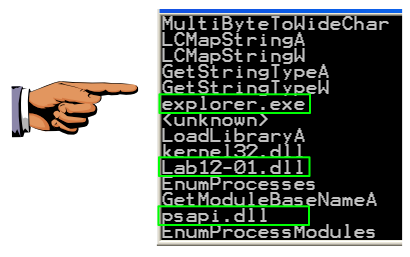
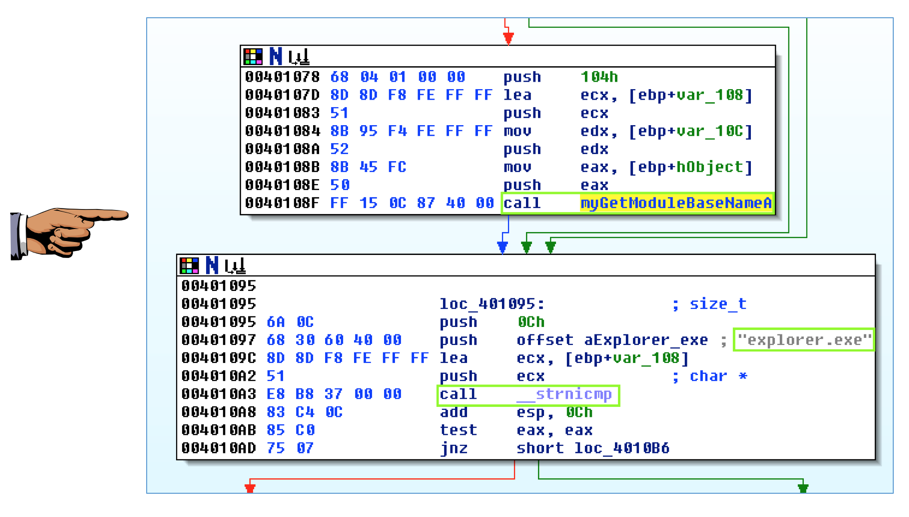
This routine enumerates the modules and compares each module name to "explorer.exe", to find the module into which to inject code.
Make sure you can see these three items on your screen, as shown below:
Save an image showing the three items highlighted below, with the filename "Proj 15d from YOUR NAME".
A box pops up saying "Press OK to reboot". as shown below. Drag this box out of the way.
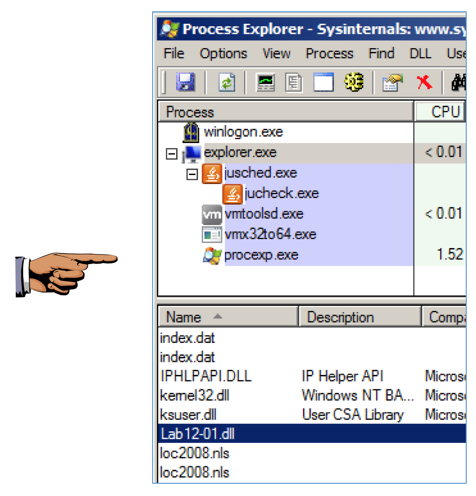
Open Process Explorer.
In the upper pane, scroll to the bottom of the list. Click explorer.exe to select it.
In Process Explorer, from the menu bar, click View and make sure "Show Lower Pane" is checked.
In Process Explorer, from the menu bar, click View, "Lower Pane View", DLLs.
In the lower pane, find the Lab12-01.dll that has been injected into explorer.exe, as shown below.
Save an image showing the Lab12-01.dll library, as highlighted below, with the filename "Proj 15e from YOUR NAME".