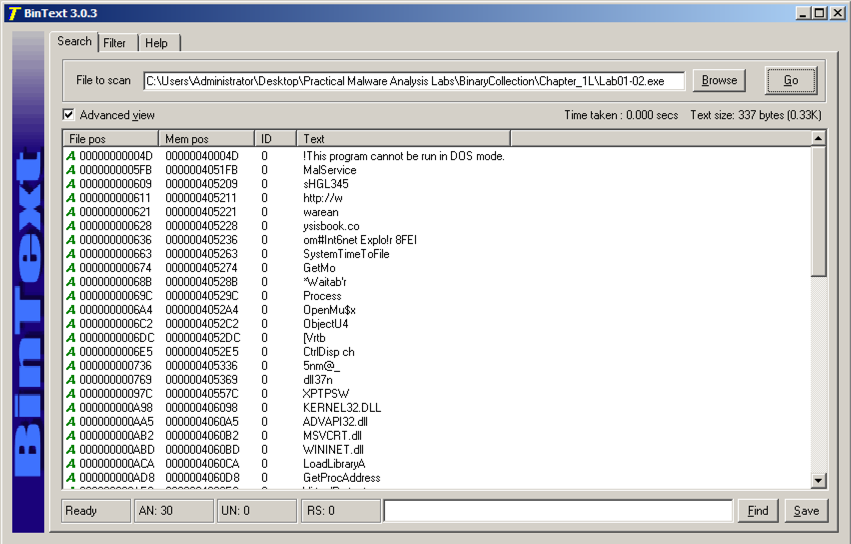
There are only a few strings, and they call only a few ordinary Windows API commands, as shown below.只有几个字符串,它们只能调用一些普通的Windows API命令,如下所示。
These strings aren't from the malware--they are from the UPX packer, as we will show below.这些字符串不是来自恶意软件 - 它们来自UPX打包程序,如下所示。

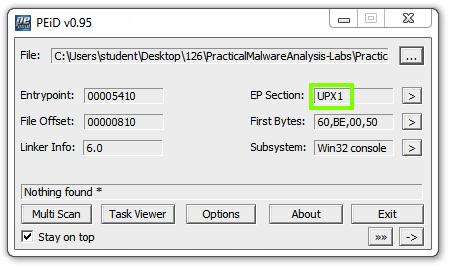
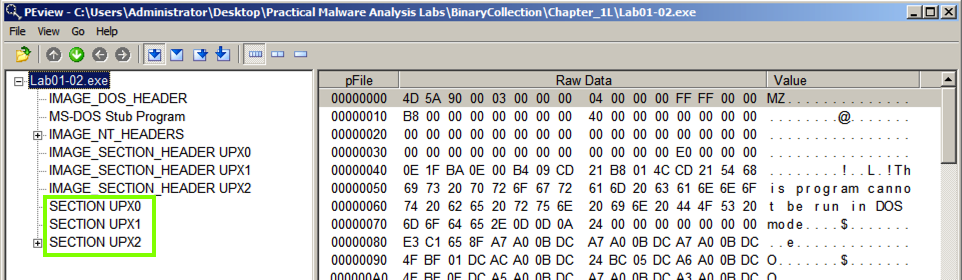
These are section names produced by the UPX packer.这些是由UPX打包机生成的部分名称。
UPX You see a UPX help message, as shown below:你会看到一个UPX帮助信息,如下所示: 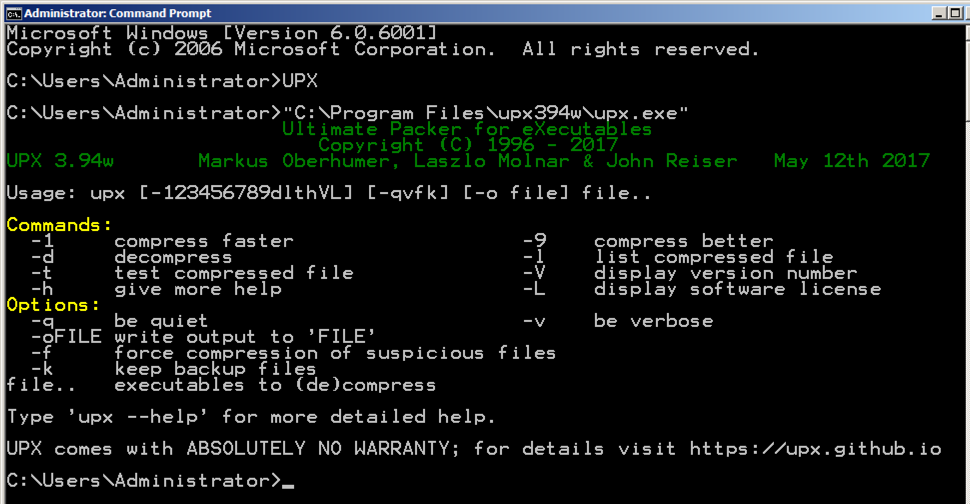
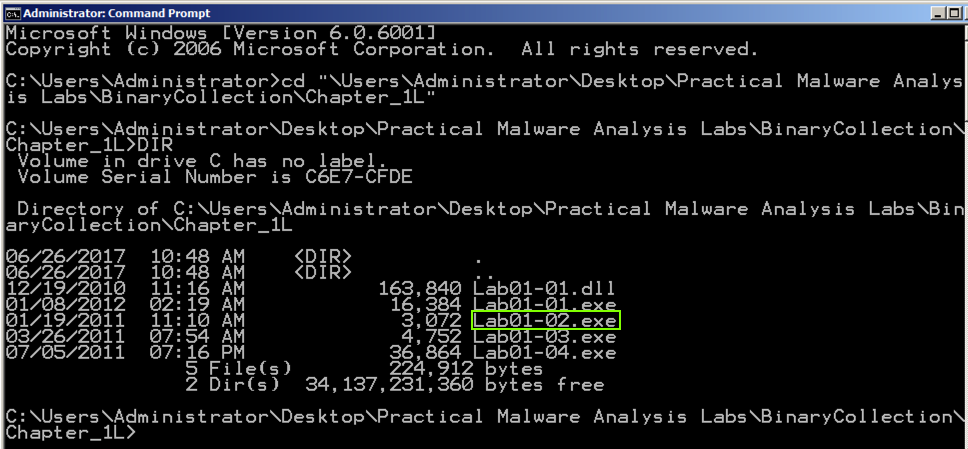
Execute these commands to move to the directory containing the malware samples, and list the files there:执行这些命令以移至包含恶意软件样本的目录,并在其中列出文件:
You see several malware samples, including Lab01-02.exe , as shown below:您会看到几个恶意软件样本,包括Lab01-02.exe ,如下所示:cd "\Users\Administrator\Desktop\Practical Malware Analysis Labs\BinaryCollection\Chapter_1L"DIR DIR
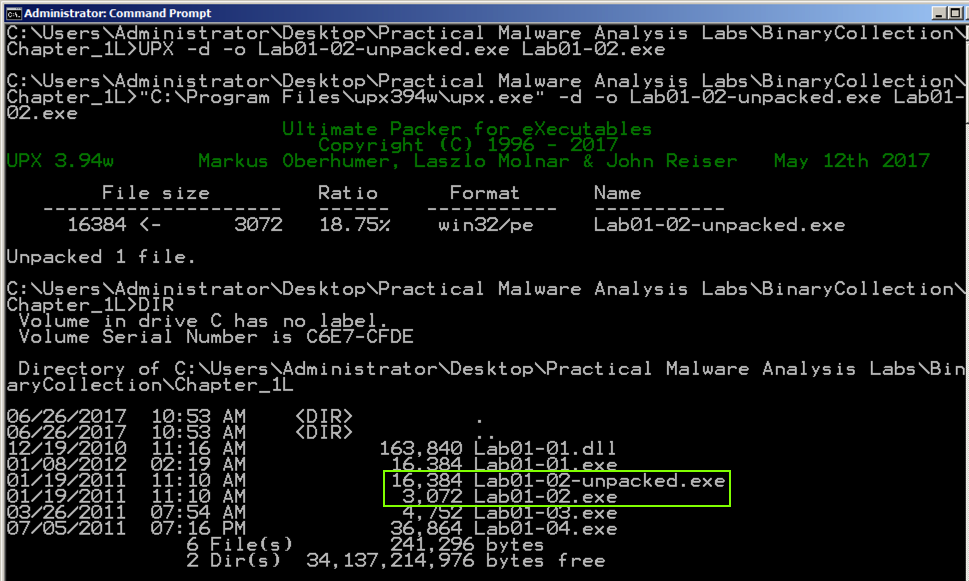
Execute these commands to unpack the file, and list the files again:执行这些命令来解压文件,并再次列出文件:
The unpacked file is much larger than the original file, as shown below:解压后的文件比原始文件大得多,如下所示:UPX -d -o Lab01-02-unpacked.exe Lab01-02.exeDIR DIR
Analyze the unpacked file with PEiD.用PEiD分析解压后的文件。 It now is regognized as a "Microsoft Visual C++ 6.0" file, as shown below.现在它被重新识别为“Microsoft Visual C ++ 6.0”文件,如下所示。
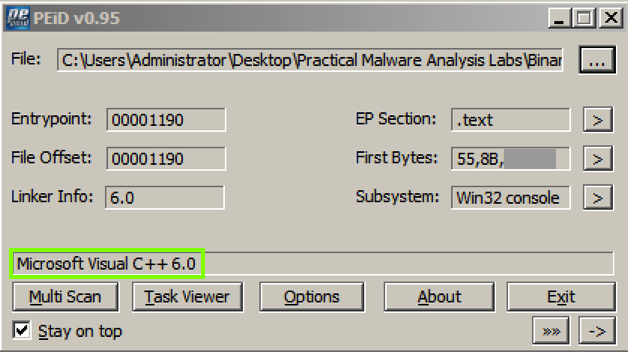
On the right side of the PeID box, find the "First Bytes" value.在PeID框的右侧,找到“First Bytes”值。 The last 2 bytes are redacted in the image above.最后2个字节在上图中被编辑。
Use the form below to put your name on the WINNERS PAGE .使用下面的表格将您的姓名放在赢家页面上 。
The imports from KERNEL32.DLL, ADVAPI32.DLL, and MSVCRT.DLL are uninformative generic functions used by almost every program.从KERNEL32.DLL,ADVAPI32.DLL和MSVCRT.DLL进口是几乎所有程序都使用的非信息泛型函数。
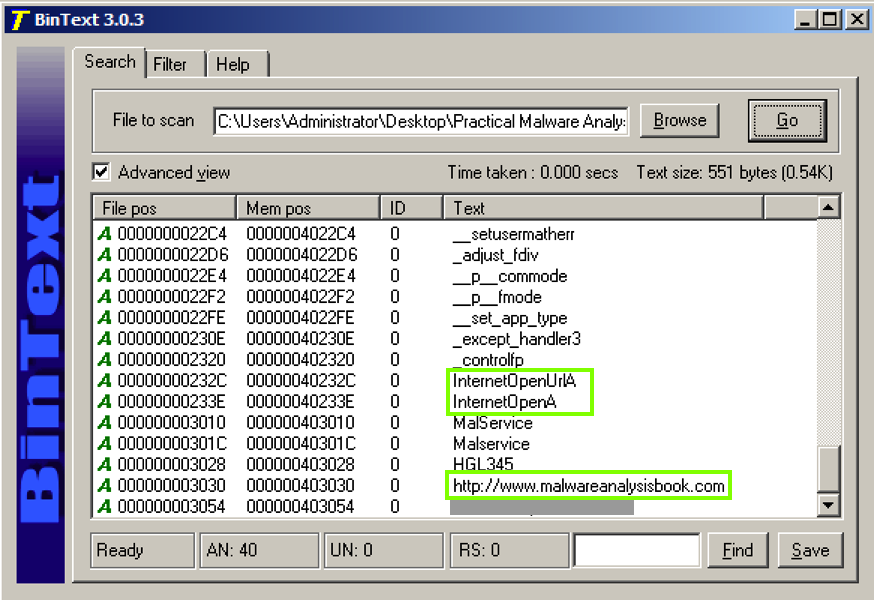
However, the WININET.DLL imports are InternetOpenUrlA and InternetOpenA , as shown below.但是,WININET.DLL导入是InternetOpenUrlA和InternetOpenA ,如下所示。 This indicates that the malware connects to a URL.这表明恶意软件连接到一个URL。
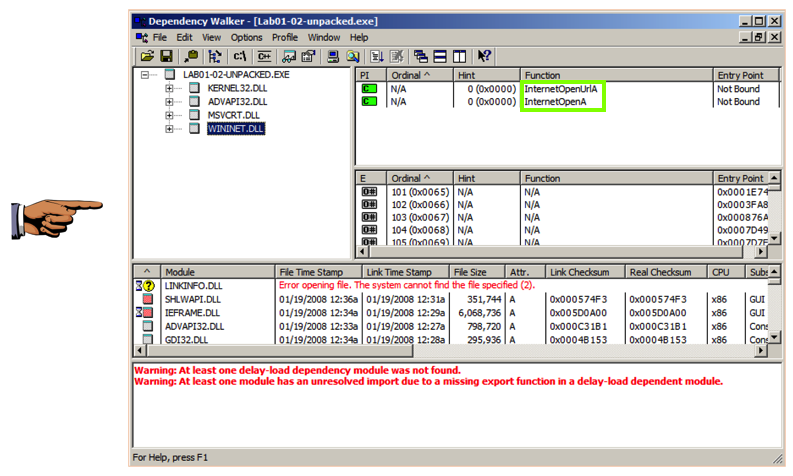
You should see the API names InternetOpenURLA and InternetOpenA , and the Command-and-Control URL http://www.malwareanalysisbook.com , as shown below.您应该看到API名称InternetOpenURLA和InternetOpenA ,以及命令和控制URL http://www.malwareanalysisbook.com ,如下所示。
These suggest that infected machines will connect to http://www.malwareanalysisbook.com .这些表明受感染的机器将连接到http://www.malwareanalysisbook.com 。 The name of the running service, MalService , is also visible.正在运行的服务的名称MalService也是可见的。
The last string is redacted in the image above.最后一个字符串在上图中被编辑。
Use the form below to put your name on the WINNERS PAGE .使用下面的表格将您的姓名放在赢家页面上 。