NOTE: Windows 7 will not work for this project!
This project follows Lab 3-1 in the textbook. There are more detailed solutions in the back of the book.
In order to download software, you need to configure a real DNS server, such as 8.8.8.8.
Double-click "Internet Protocol (TCP/IP)".
Set your DNS server to 8.8.8.8
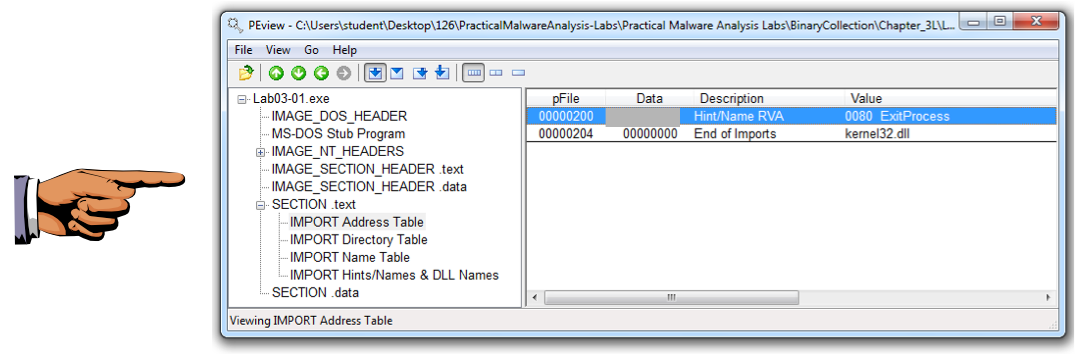
Turn in the image showing the imports of Lab03-01.exe as shown below.
We will grade it by checking the Data value.

Press the PrntScrn key to capture an image of the whole desktop.
Open Paint and paste the image in with Ctrl+V.
Save this image with the filename "Proj 4a from YOUR NAME".
YOU MUST SUBMIT WHOLE-DESKTOP IMAGES TO GET FULL CREDIT!
Above "advpack" there is a string starting with "j".
We will grade it by checking that string.
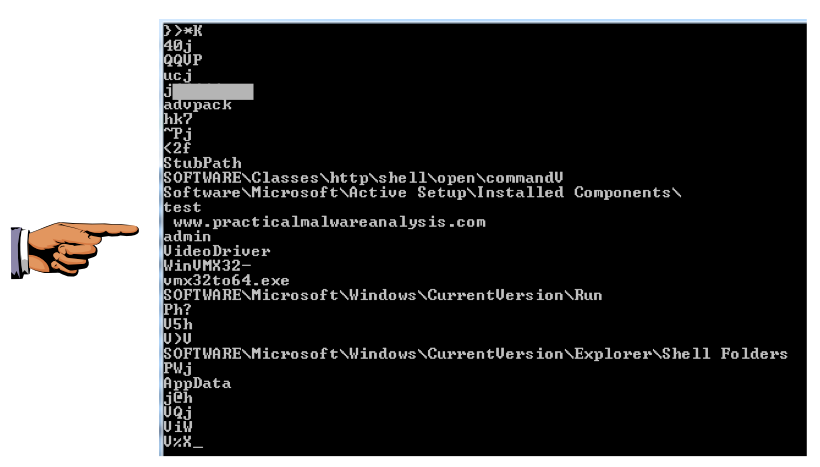
Save this image with the filename "Proj 4b from YOUR NAME".
Here is the process detailed below:
In Linux, start inetsim, as you did in the previous project.
Set the Windows DNS server to the Linux machine's IP address, as you did in the previous project.
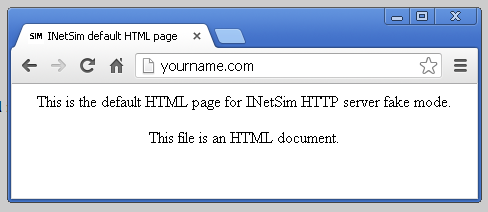
Test it by opening a Web browser to this URL: YOURNAME.com
You should see the "INetSIM HTTP server" page, as shown below:
Double-click "Internet Protocol (TCP/IP)".
Set your DNS server to the Kali Linux machine's IP address, as show below:

In the folder you unzipped Process Monitor into, double-click Procmon.exe.
If a Security Warning box pops up, allow the software to run.
Agree to the license.
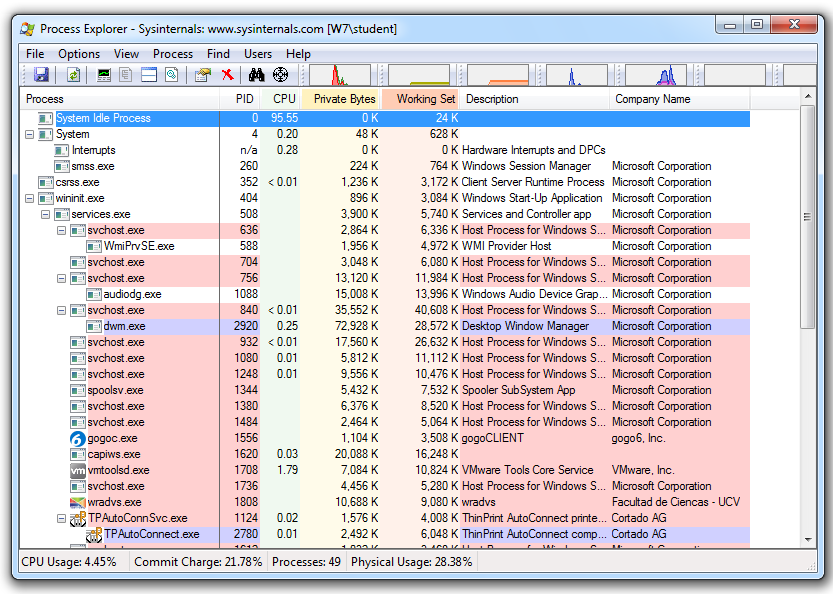
You should see Process Monitor, with a lot of processes visible, as shown below:
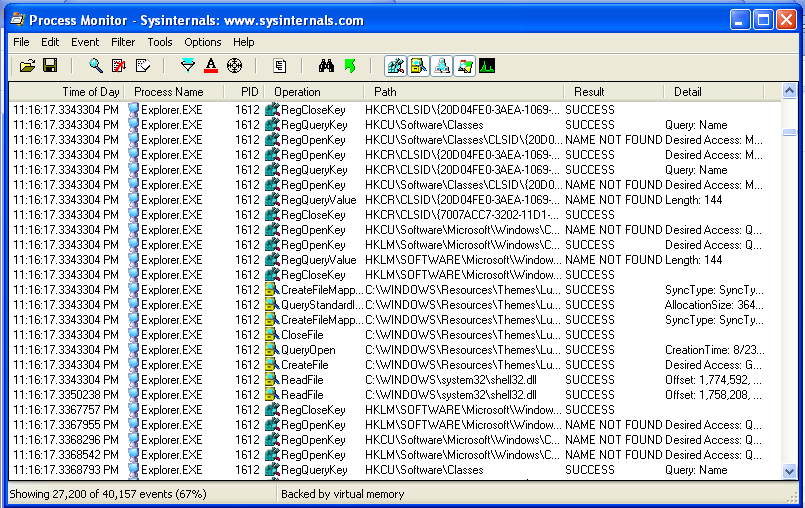
In Process Monitor, right-click the name of one of the visible processes, such as lsass, and click "exclude 'lsass.exe'", as shown below:
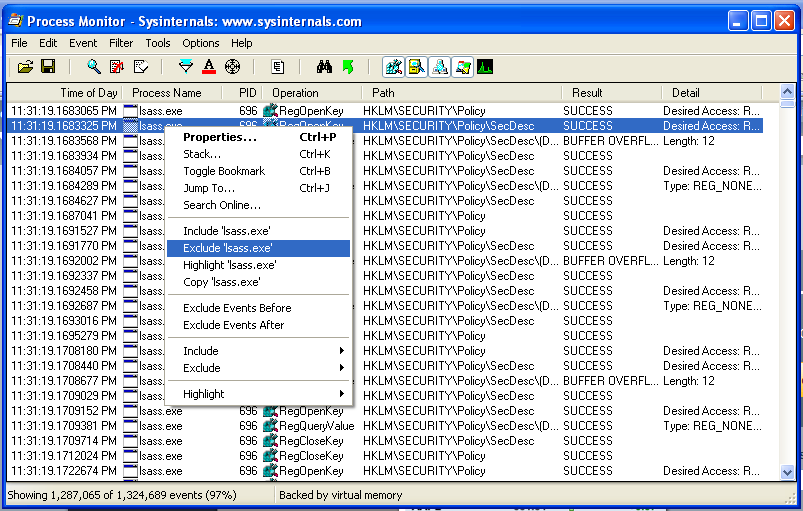
Wait while the event filter is applied.
Right-click a remaining process, such as "svchost.exe" and exclude it too.
Repeat the process until all current processes are hidden, as shown below. When I did it, the remaining processes to exclude were csrss.exe, explorer.exe, services.exe, vmtoolsd.exe, iexplore.exe, VMwareTray.exe, verclsid.exe, winlogon.exe, wmiprvse.exe, wuauclt.exe, regshot.exe, spoolsv.exe, alg.exe, rundll.exe, WMIADAP.EXE, GoogleUpdate.exe, GoogleCrashHandler.exe, chromeinstaller.exe, and setup.exe.
Troubleshooting
If the Lab03-01.exe process does not appear in Process Explorer, that probably means that the malware has already been run on this VM.To make the malware run properly again, restart the VM, press F8, enter Safe Mode, and delete this file:
C:\Windows\System32\vmx32to64.exe
Then restart the VM in normal mode.
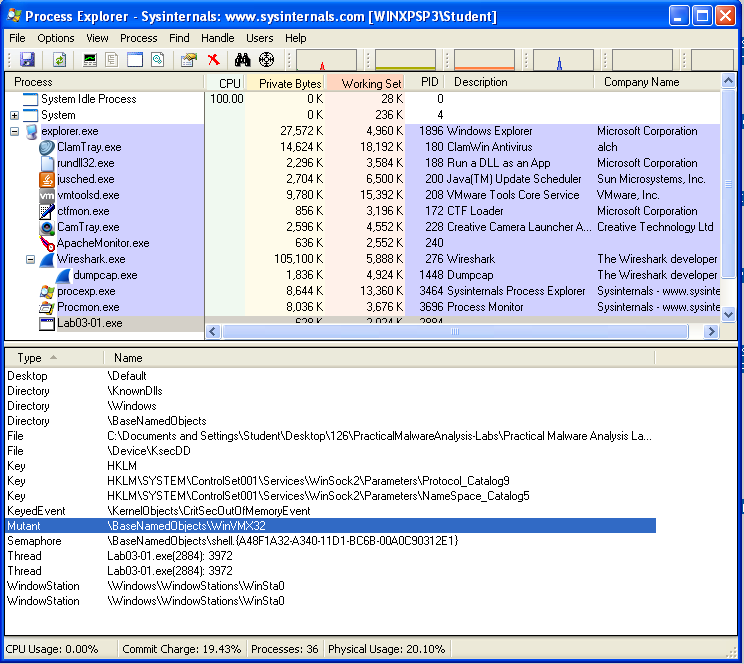
In Process Explorer, click View, "Lower Pane View", Handles.
You see the WinVMX32 mutant, as highlighted below. A mutant, also called a mutex, is used for interprocess connunication. A wonderful explantion of mutexes in terms of rubber chickens is here.
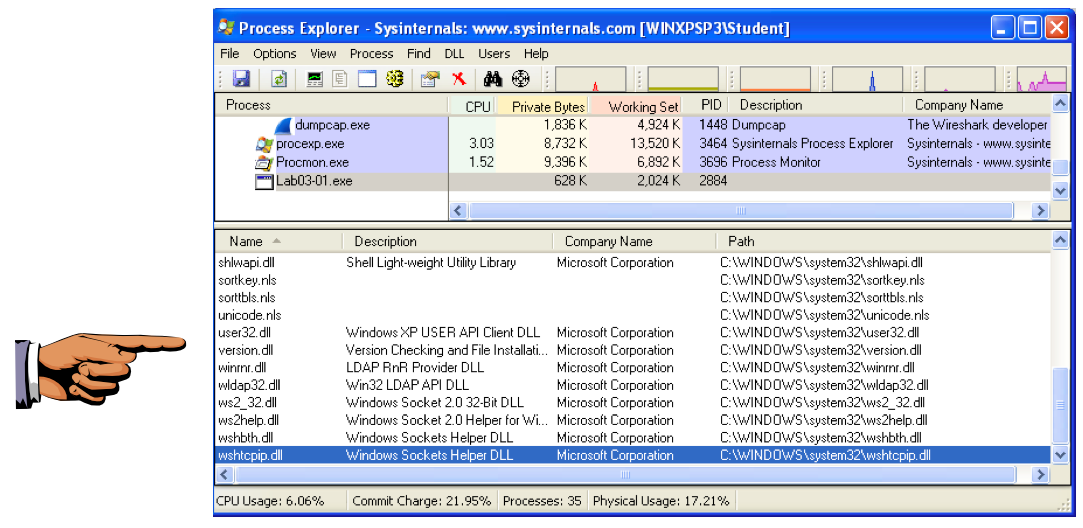
In Process Explorer, click View, "Lower Pane View", DLLs.
Scroll to the bottom to find ws2_32.dll and wshtcpip.dll, as shown below. This shows that the malware has networking functionality.
Save this image with the filename "Proj 4c from YOUR NAME".
Make sure it contains the ws2_32.dll and wshtcpip.dll items. (In Server 2008, the second item appears in capital letters like this: WSHTCPIP.DLL
In Process Monitor, click Filter, Filter. Enter a Filter for "Process Name" is Lab03-01.exe, Include, as shown below.
Click Add to add the filter.
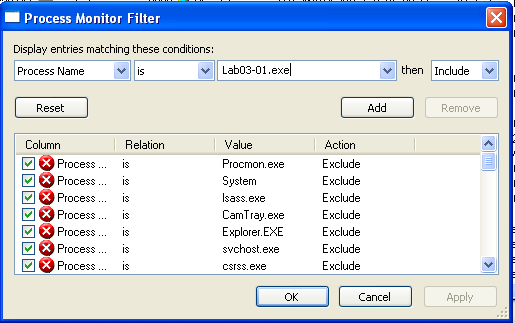
Add two more filters:
You end up the two events shown below. (Windows XP has an additional 8 events with Paths ending in "Cryptography\RNG\Seed" -- if you see those events, just ignore them.)
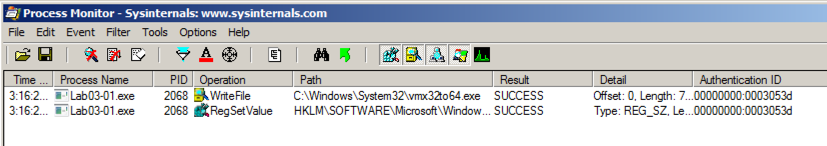
Eight of them are random number seed generation events and uninteresting. Only the second and third events are interesting.
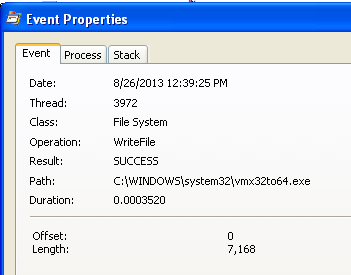
Double-click the event with a Path ending in vmx32to64.exe. The Properties sheet shows that this event creates a file named vmx32to64.exe, as shown below.
As explained in more detail in the book, this event has copied the malware itself to a file named vmx32to64.exe, so that filename is a useful indicator of infection.
Double-click the with a Path ending in VideoDriver.
This creates a new a Run key in the registry named "VideoDriver" with a value of "C:\WINDOWS\system32\vmx32to64.exe" -- this is a persistence mechanism, to re-launch the malware when the machine restarts.|
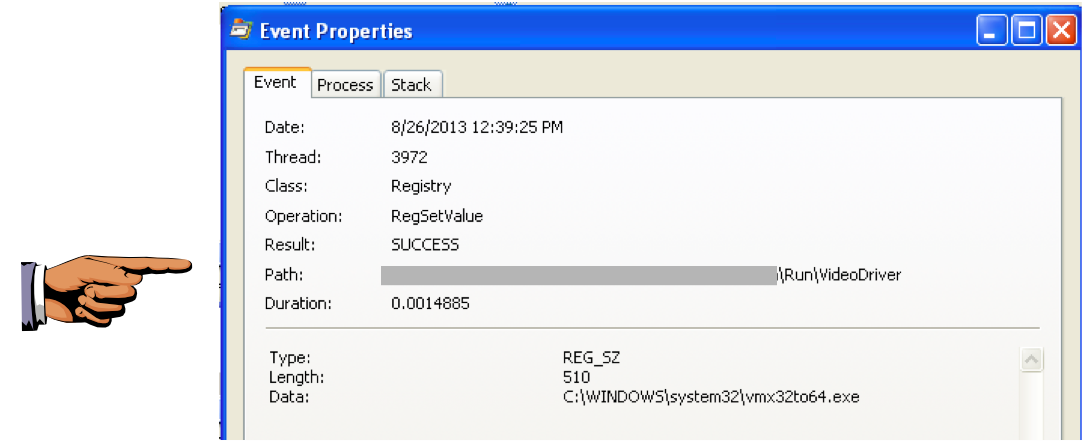
Save this image with the filename "Proj 4d from YOUR NAME".
We will grade it based on the start of the Run registry key that is redacted above.
Press Ctrl+C. A message appears telling you where the Report file is, as shown below:
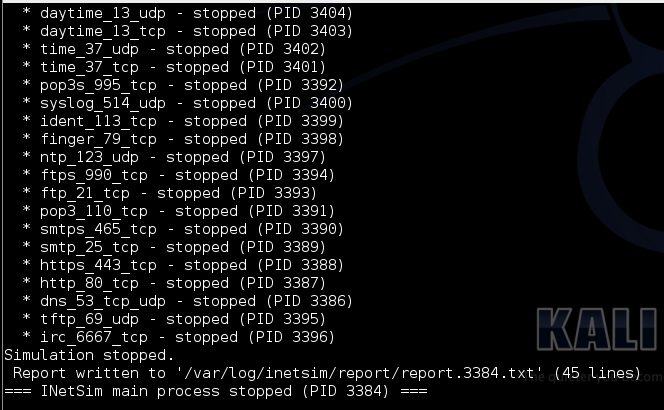
In the Linux machine, execute this command, replacing "report.3384.txt" with the correct name of your report file.
nano /var/log/inetsim/report/report.3384.txt
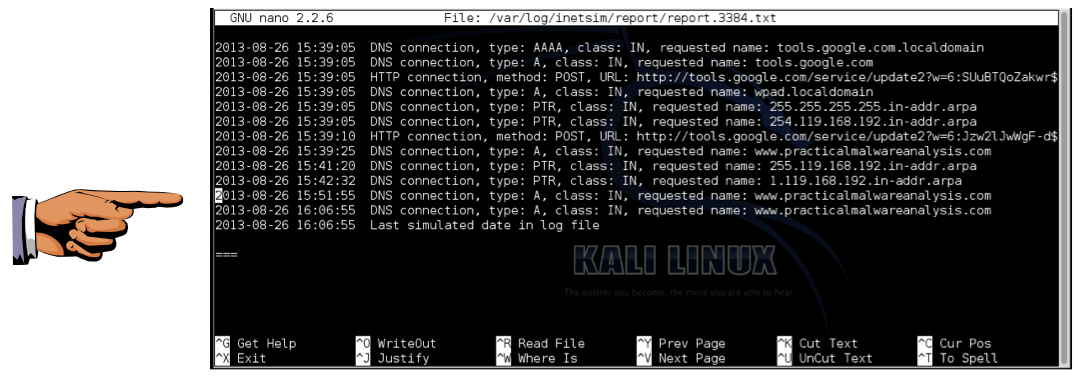
Save this image with the filename "Proj 4e from YOUR NAME".
Make sure "www.practicalmalwareanalysis.com" is visible.
At the top left of the Wireshark window, in the Filter bar, type a filter of
frame contains practicalmalwareanalysis
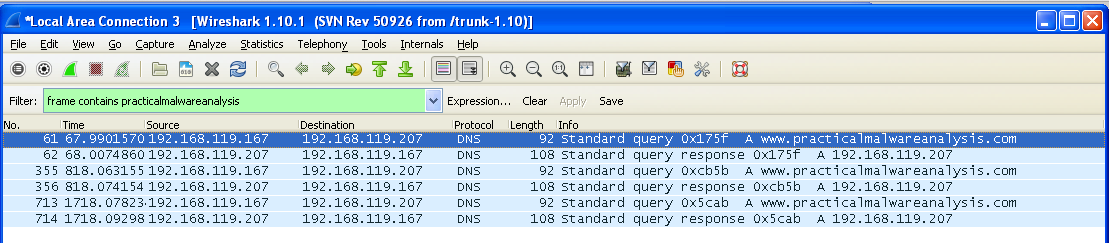
Click the line showing the first DNS request for www.practicalmalwareanalysis.com -- in the example above, it is packet 61.
In the top center of Wireshark, click the Clear button to clear the filter. The packets following the DNS request appear, as shown below.
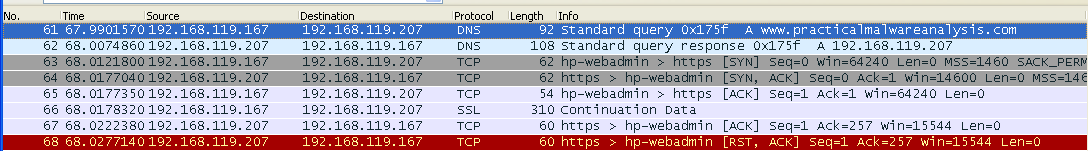
There is a TCP handshake here, but no actual HTTPS connection. A real HTTPS connection contains many more packets, such as "Client Hello", "Server Hello", and "Change Cipher Spec".
Find the SYN packet sent to the https port, which may be marked "443". In the example above, it is packet 63. Right-click it and click "Follow TCP Stream".
You see "Stream Content" containing 256 bytes of random packets, as shown below. These are beacons and are used by malware to notify the Command and Control server that the machine is infected and ready to use.
Since the data is random, your image will look different than the example below, but it should be 256 bytes in size.
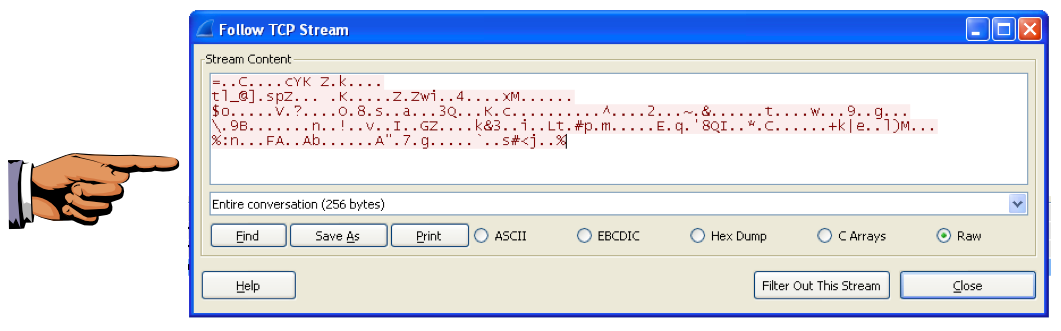
Save this image with the filename "Proj 4f from YOUR NAME".
Make sure the "(256 bytes)" message is visible at the bottom.