You should already have the lab files, but if you don't, do this:
http://practicalmalwareanalysis.com/labs/
Download and unzip the lab files.
https://www.hex-rays.com/products/ida/support/download_freeware.shtml
Download "IDA Freeware" and install it.
If that link is down, use this alternate download link:
https://samsclass.info/126/proj/idafree50.exe
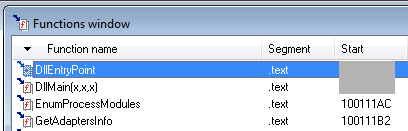
Click the "Function name" header to sort by name and scroll to the top.
Your image should show the location of DLLMain, as shown below:

Press the PrntScrn key to capture an image of the whole desktop.
Open Paint and paste the image in with Ctrl+V.
Save this image with the filename "Proj 6a from YOUR NAME".
YOU MUST SUBMIT WHOLE-DESKTOP IMAGES TO GET FULL CREDIT!
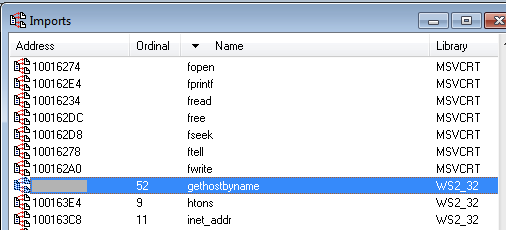
Widen the Address column to make the entire address visible.
Your image should show the location of gethostbyname, as shown below:
Save a full-desktop image with the filename "Proj 6b from YOUR NAME".
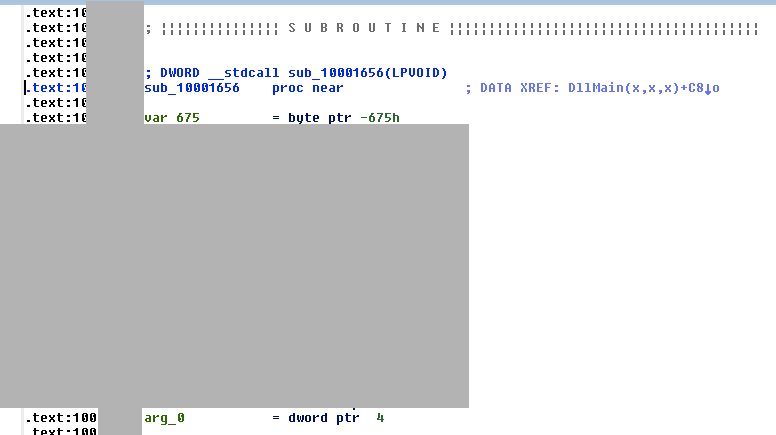
Press g to Go. Enter the address 0x10001656 and click OK.
Scroll up to show the comments IDA added to the start of the function, listing its local variables, as shown below:
Save a full-desktop image with the filename "Proj 6c from YOUR NAME".
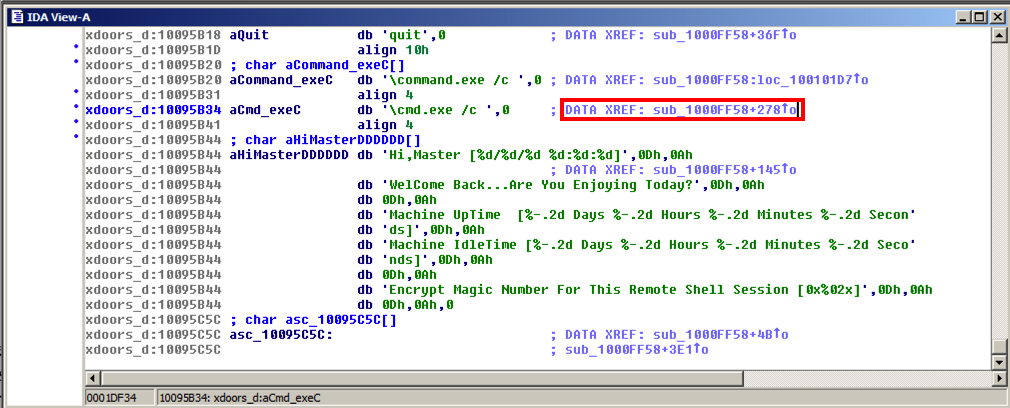
In the line containing "\\cmd.exe /c", double-click the address to the right of "XREF", as indicated by the red outline in the image below.
Press the SPACEBAR to get to graph view, as shown below. "\\cmd.exe /c" is used in the little routine on the left.
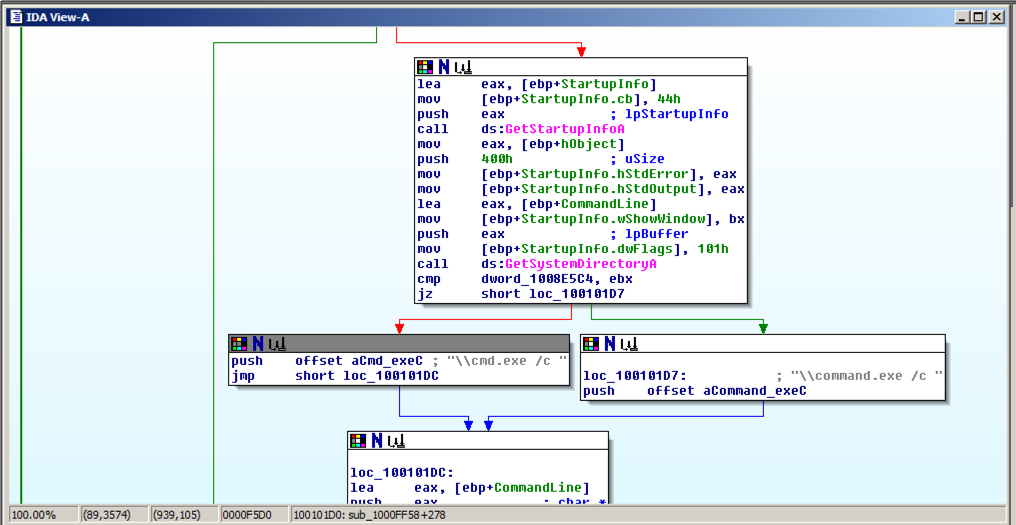
Drag the graph view down to see the subroutines before it. About three boxes up you should find text beginning with "Hi, Master", as shown below.
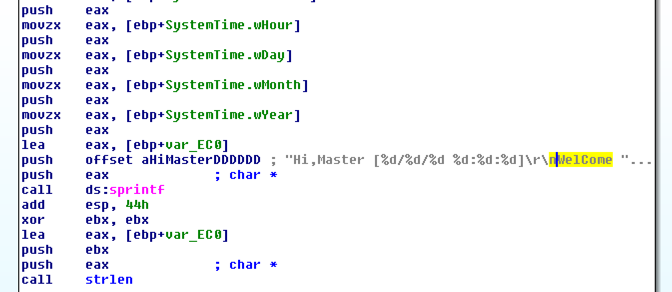
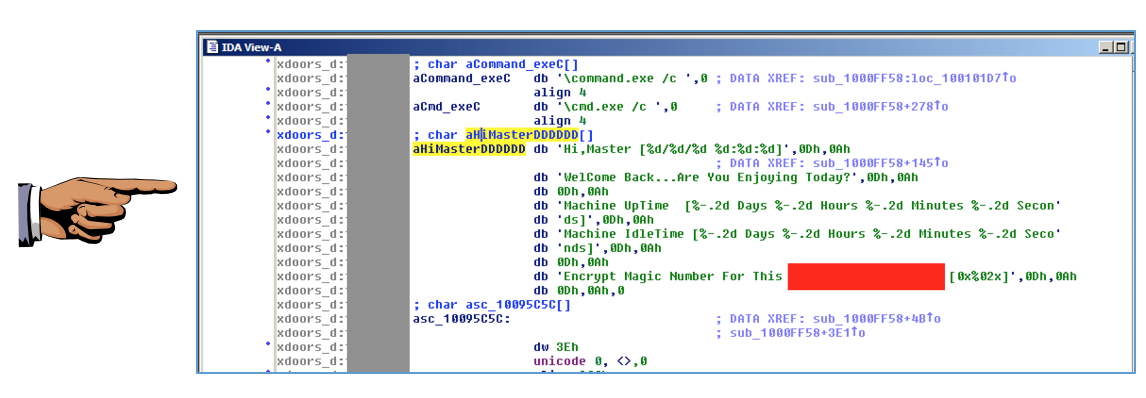
Double-click aHiMasterDDDD to find the complete message. The purpose of the malware is clearly stated.
Your image should show what the code is doing, as shown below. The purpose is behind the red rectangle in the image below.
Save a full-desktop image with the filename "Proj 6d from YOUR NAME".