14: Patching EXEs with Ollydbg
What You Need
- A Windows machine, real or virtual. I used a Windows Server 2008 virtual machine.
- You need several files to examine. They are all in the Documents folder of the VM your instructor handed out. If you don't have that, download them with these links:
Purpose
To practice disassembling and modifying binaries, and
using Python scripts.
Challenge A: Patching an EXE (10 pts.)
Getting the EXE
In the Documents folder of the VM handed out
by your instructor, find the
00000.exe file.
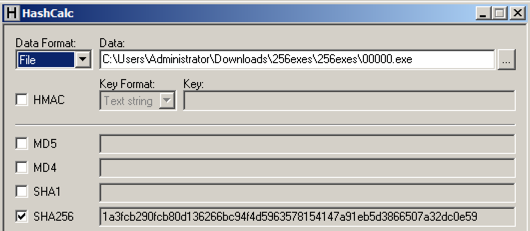
Checking the Hash
Calculate the SHA256 hash of the file.
It should match the value shown below.
Running the EXE
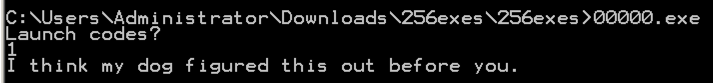
Run 00000.exe in a Command Prompt. It
asks for a "Launch code" and if you guess
wrong, it insults you,
as shown below.
Examining the EXE with Ollydbg
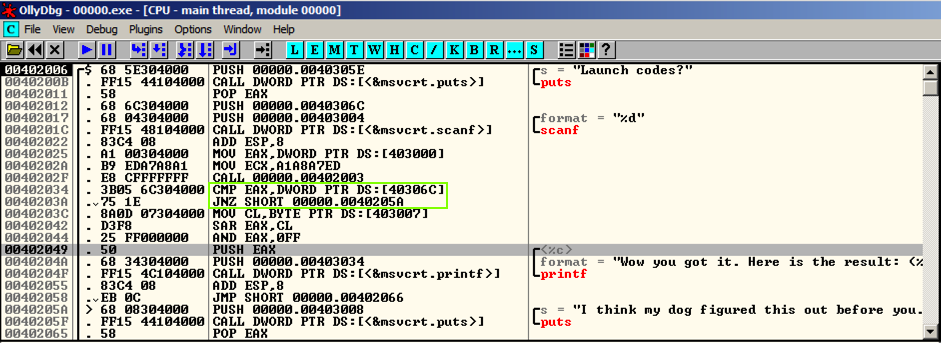
Open the file in OllyDbg,
as shown below.
Look at the rightmost
section, and you can easily see what the
program does; it prints out "Launch codes?",
reads in a decimal number (%d), and then
chooses to print either a winning message
with a result,
or an insult.
The choice is performed by two
instructions:
CMP (Compare) and JNZ (Jump if Not Zero),
outlined in green in the image below.
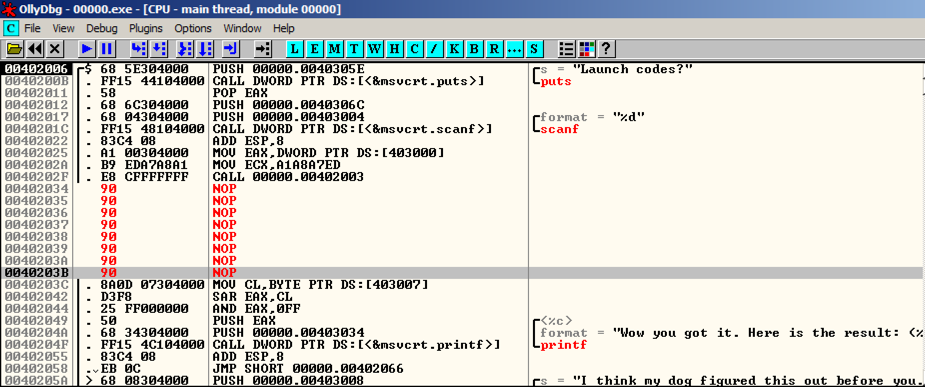
Replace those instructions with NOP (No Operation),
as shown below. Save the patched file.
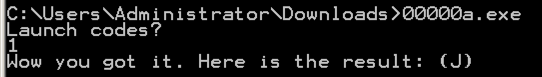
Running the Patched File
The patched file will accept any Launch
code, as shown below.
Checking the Hash
Calculate the SHA256 hash of the patched file.
It should match the value shown below.

Challenge A: Submit the CRC32 (10 pts)
Calculate the CRC32 hash of the patched file.
Use the form
below to
get your points.
Challenge B: Patching Three EXEs (10 pts.)
Getting the EXEs
In the Documents folder of the VM handed out
by your instructor, find the
3EXEs.zip file.
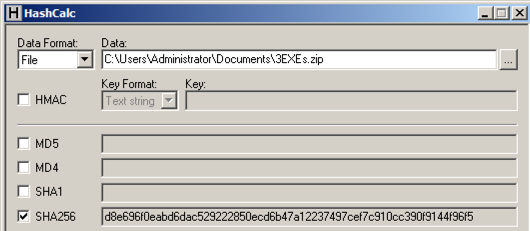
Checking the Hash
Calculate the SHA256 hash of the file.
It should match the value shown below.
Patch the Files
Patch all 3 files so they will accept any
input.
Gather the Results
Run the three patched files. Each one returns
a single character as a result. Keep the
files in alphabetical order, by filename,
like this:
- File 00000.exe Result C
- File 0000a.exe Result A
- File 000a1.exe Result T
If those were the results, the answer would be CAT
The actual results are different, of course.
Challenge B: Submit the Results (10 pts)
Use the form
below to
get your points.
Challenge C: Patching 19 EXEs (30 pts.)
Getting the EXEs
In the Documents folder of the VM handed out
by your instructor, find the
easy.zip file. Unzip it.
There are 19 EXEs in it.
Goal
Patch all 19 files, run them,
and combine the Results to get a
19-character flag.
Hints
There are hints
here.
Challenge C: Submit the Results (30 pts)
Use the form
below to
get your points.
Challenge D: Patching 256 EXEs (50 pts.)
Getting the EXEs
In the Documents folder of the VM handed out
by your instructor, find the
256exes.zip file. Unzip it.
There are 256 EXEs in it.
Goal: Gather the Results
Patch all 256 files and run them.
Each file will give you one "Result"
character. Gather all those characters
into a file 256 bytes long.
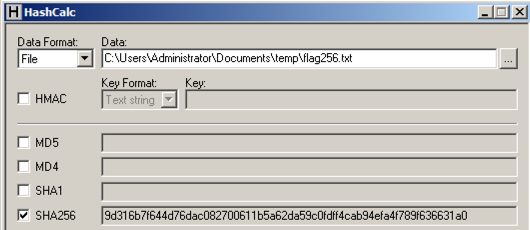
Calculate the SHA256 hash of that file.
It should match the value shown below.
Calculate the CRC32 of that file to win.
Submit the CRC32 (50 pts)
Calculate the CRC32 hash of the 256-byte file.
Use the form
below to
get your points.
Credit
This is based on the 67k Challenge from EasyCTF 2017.
Modified 1-7-19








