section .text
global _start
_start:
mov edx, len
mov ecx, msg
mov ebx, 1
mov eax, 4
int 0x80
mov eax, 1
int 0x80
section .data
msg db "Hello World!"
len equ $ - msg
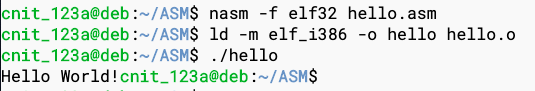
nasm -f elf32 hello.asm
ld -m elf_i386 -o hello hello.o
./hello

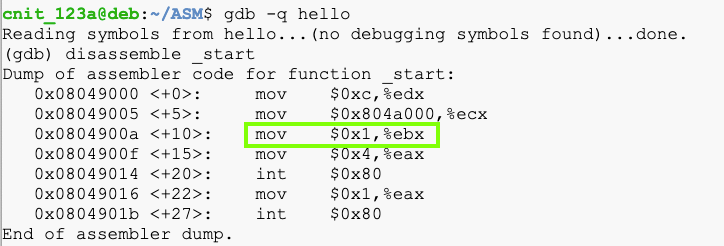
gdb -q hello
Execute this command to disassemble the code from the _start location:
disassemble _start
The command we entered in the hello.asm source code was:
mov ebx, 1
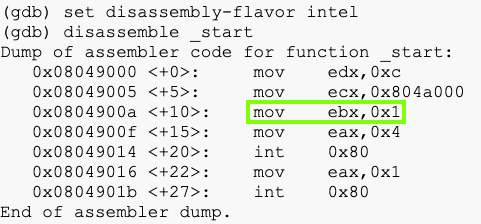
set disassembly-flavor intel
disassemble _start
Compare that output to the assembly code you wrote and notice these things:
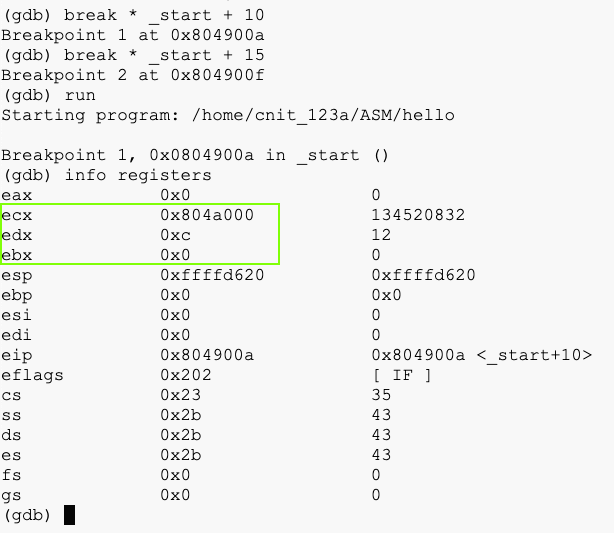
break * _start + 10
break * _start + 15
run
info registers
Notice these things:
In gdb, execute these commands:
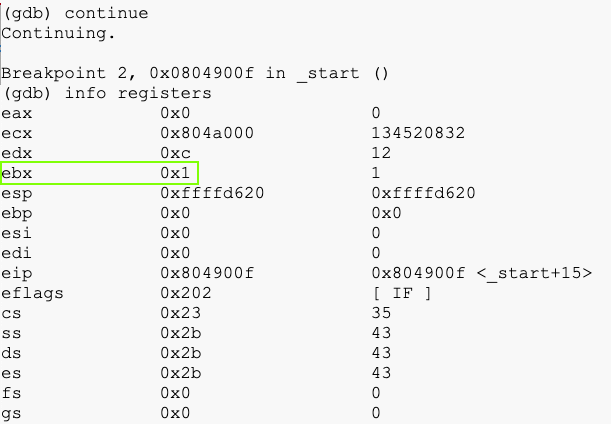
continue
info registers
Now ebx contains 0x1.
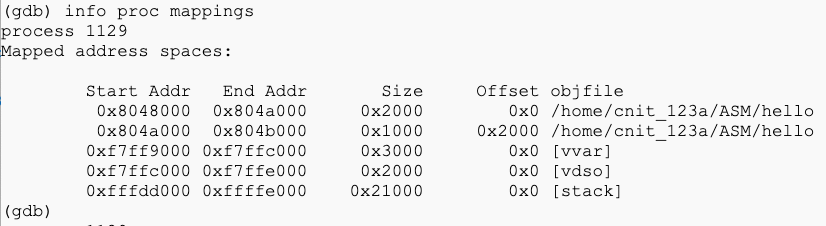
info proc mappings
ASM 110.1: Data (5 pts)
In gdb, execute this command:The flag is covered by a green rectangle in the image below.
After getting the flag, execute these commands to exit gdb:
ASM 110.2: Extra Command (10 pts)
In the shell, execute these commands:The program prints out a lot of extra garbage after the desired "Hello, World!" message, as shown below.
There is one extra line of assembly code in the program causing that problem. Find the extra line. Submit that entire line as the flag.
ASM 110.3: Crash (15 pts extra)
In the shell, execute these commands:The program crashes with a "Segmentation fault" error.Find the command that caused the crash. That command, in Intel format, is the flag.