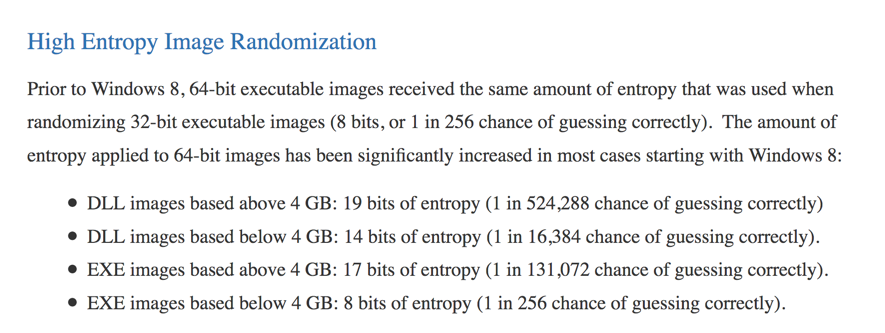
Here's what Microsoft says about ASLR randomness:

It seems like there's a 1 in 256 chance of guessing correctly for many EXE files!
Click the Start button, scroll to the V secton, expand "Visual Studion 2017", and click "Developer Command Prompt for VS 2017", as shown below.
mkdir c:\127a
cd c:\127a
notepad esp3.cpp
Enter this code, as shown below:
#include <iostream>
using namespace std;
void main() {
int data = 0;
__asm {
mov data, esp
}
cout << hex << data << endl;
}
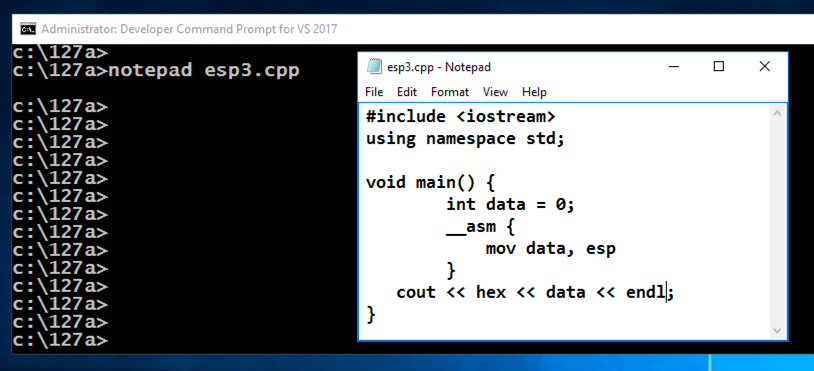
In Notepad, click File, Save.
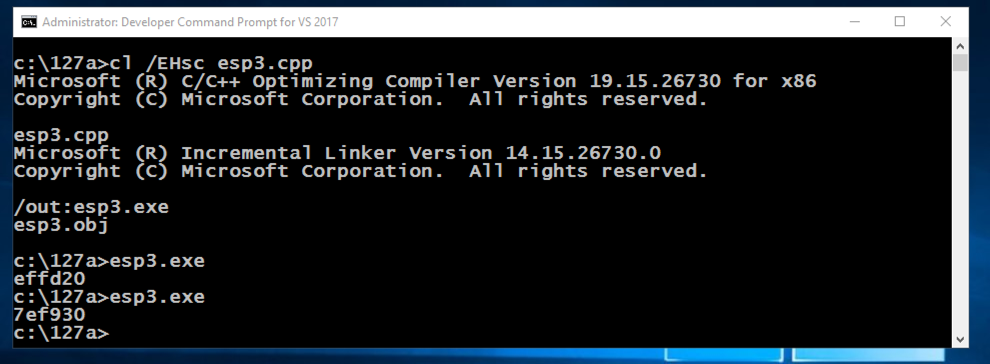
cl /EHsc esp3.cpp
esp3.exe
esp3.exe
copy esp3.cpp esp4.cpp
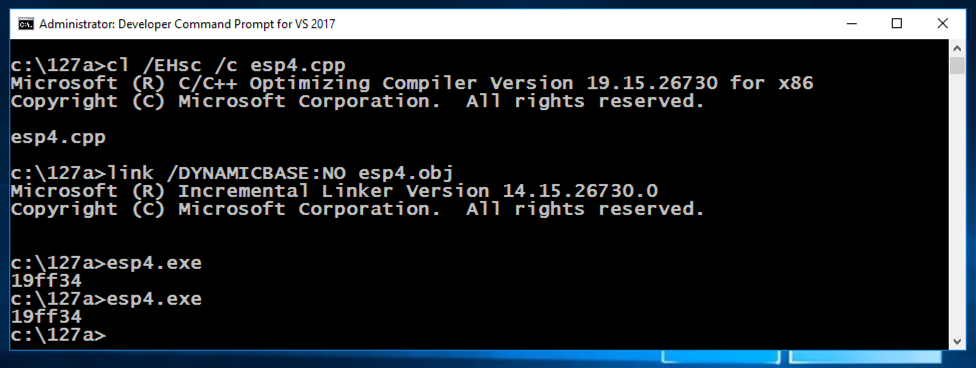
cl /EHsc /c esp4.cpp
link /DYNAMICBASE:NO esp4.obj
esp4.exe
esp4.exe
In the Developer Command Prompt window, execute these commands:
cd c:\127a
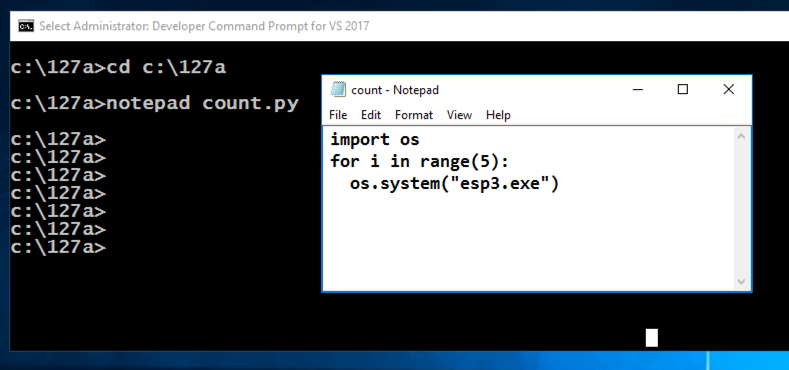
notepad test.py
Enter this code, as shown below. It will run the esp3.exe program 5 times and print out the results.
import os
for i in range(5):
os.system("esp3.exe")
In Notepad, click File, Save.
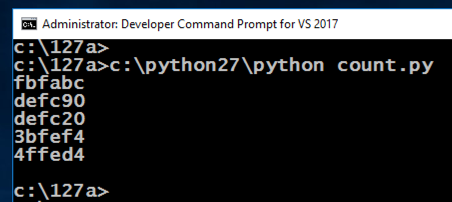
c:\python27\python test.py
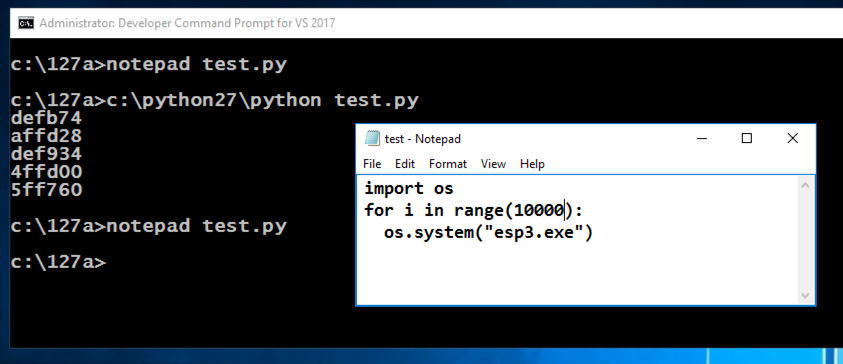
notepad test.py
In Notepad, click File, Save.
c:\python27\python test.py > 10k.txt
notepad 10k.txt
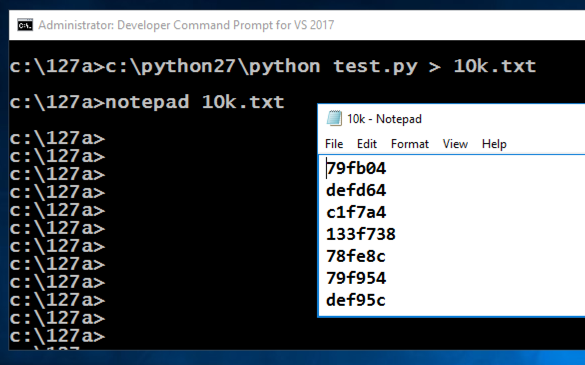
In the Developer Command Prompt window, execute this command:
notepad count.py
Enter this code, as shown below. It will print all the lines starting with 19ff.
Note: when I did this on Windows 11, the actual prefix was 19fe. Use the correct value shown by running esp4.exe on your system.
import re
f = open("10k.txt", "r")
for line in f:
if re.match("^19ff", line):
print(line)
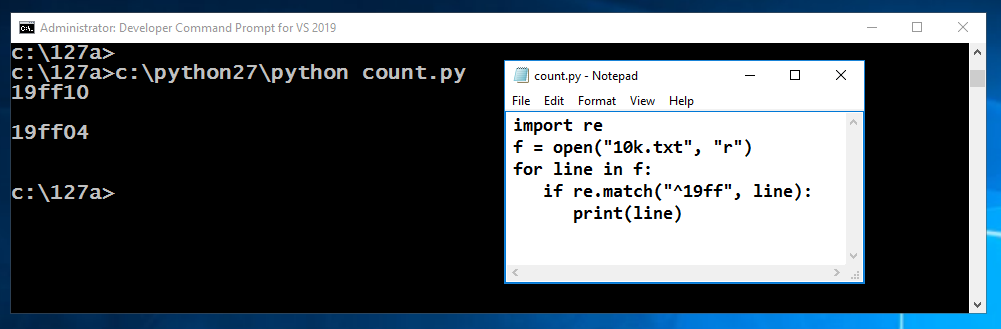
In Notepad, click File, Save.
c:\python27\python count.py
As you can see, when I did it, the chance was 2 in 10,000.
ED 303.1: Analyze My File (5 pts)
In the Developer Command Prompt window, execute these commands:The flag is covered by a green rectangle in the image below.Note: to see the flag, make sure your program is looking for 19ff prefixes.
From the Immunity menu bar, click File, Open. Navigate to C:\127a\esp4.exe and double-click it.
Immunity loads the program.
From the Immunity menu bar, click Debug, Run.
From the Immunity menu bar, click View, Memory.
Notice the Address of these items, as shown below:
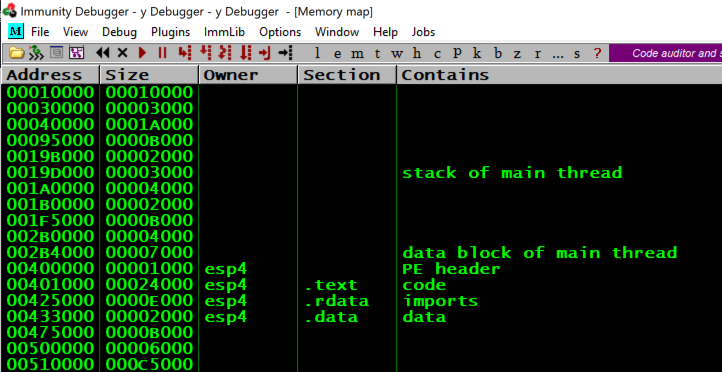
From the Immunity menu bar, click Debug, Run.
From the Immunity menu bar, click View, Memory.
Notice that the esp4 memory addresses remain the same, as shown above, because ASLR is disabled for esp4.exe.
cd c:\127a
notepad mem.cpp
Enter this code, as shown below.
#include <cstdio>
#include <cstdlib>
#include <iostream>
using namespace std;
int d; /* in .data section */
void main()
{
int i=1, j;
int * p; /* pointer */
char buf[5]; /* Activate stack cookie protection */
strcpy(buf, "HERE"); /* To help find code in IDA */
__asm {mov edx, LABEL
mov d, edx
LABEL: NOP}; /* in .text */
char * heapbuf;
heapbuf = (char*) malloc(1); /* on heap */
printf("Address in .text: %08x\n", d);
printf("Address in .data: %08p\n", (void *) &d);
printf("Address in .heap: %08p\n", (void *) heapbuf);
printf("Address in stack: %08p\n", (void *) &i);
printf("\nStack:\n");
p = &i;
for (j=0; j<9; j++) {
printf("%d %08p %08x\n", j, (void *) p, *p);
p++;
}
__asm int 3
}
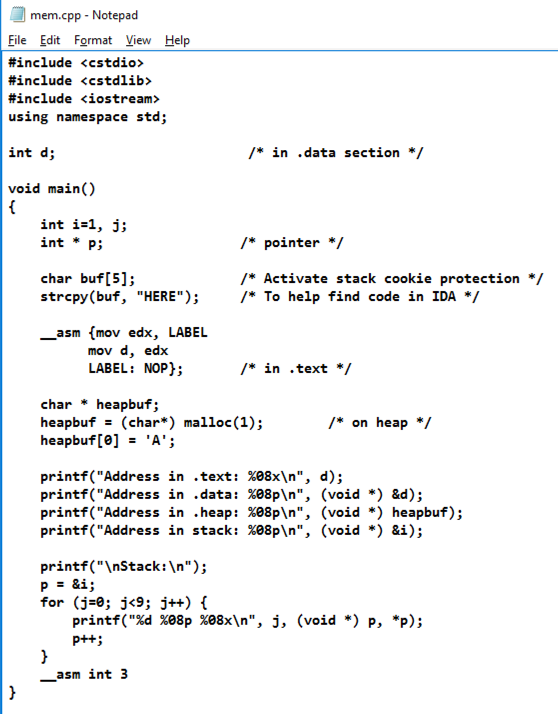
In Notepad, click File, Save.
cl /EHsc mem.cpp
mem.exe
In the box showing "mem.exe has stopped working", click the "Close program" button.
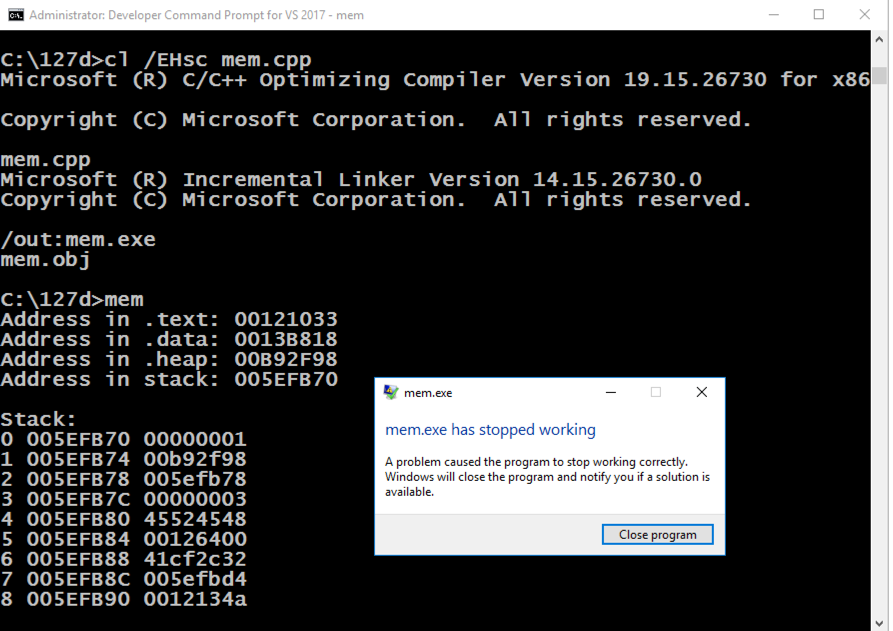
From the Immunity menu bar, click File, Open. Navigate to C:\127a\mem.exe and double-click it.
Immunity loads the program.
From the Immunity menu bar, click Debug, Run.
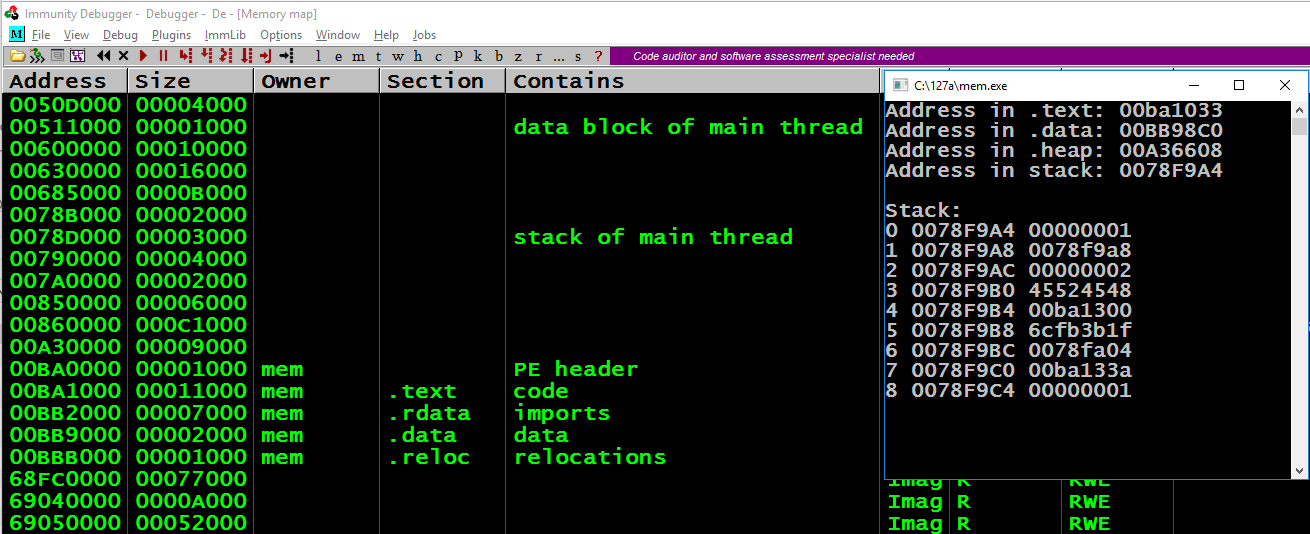
From the Immunity menu bar, click View, Memory.
Press Alt + Tab to make the Command Prompt running "mem.exe" visible, as shown below.
Notice these items:
Press Alt + Tab to make the Command Prompt running "mem.exe" visible, as shown below.
Notice these items, referred to by the word number that count from 0 to 8 in the Command Prompt window:
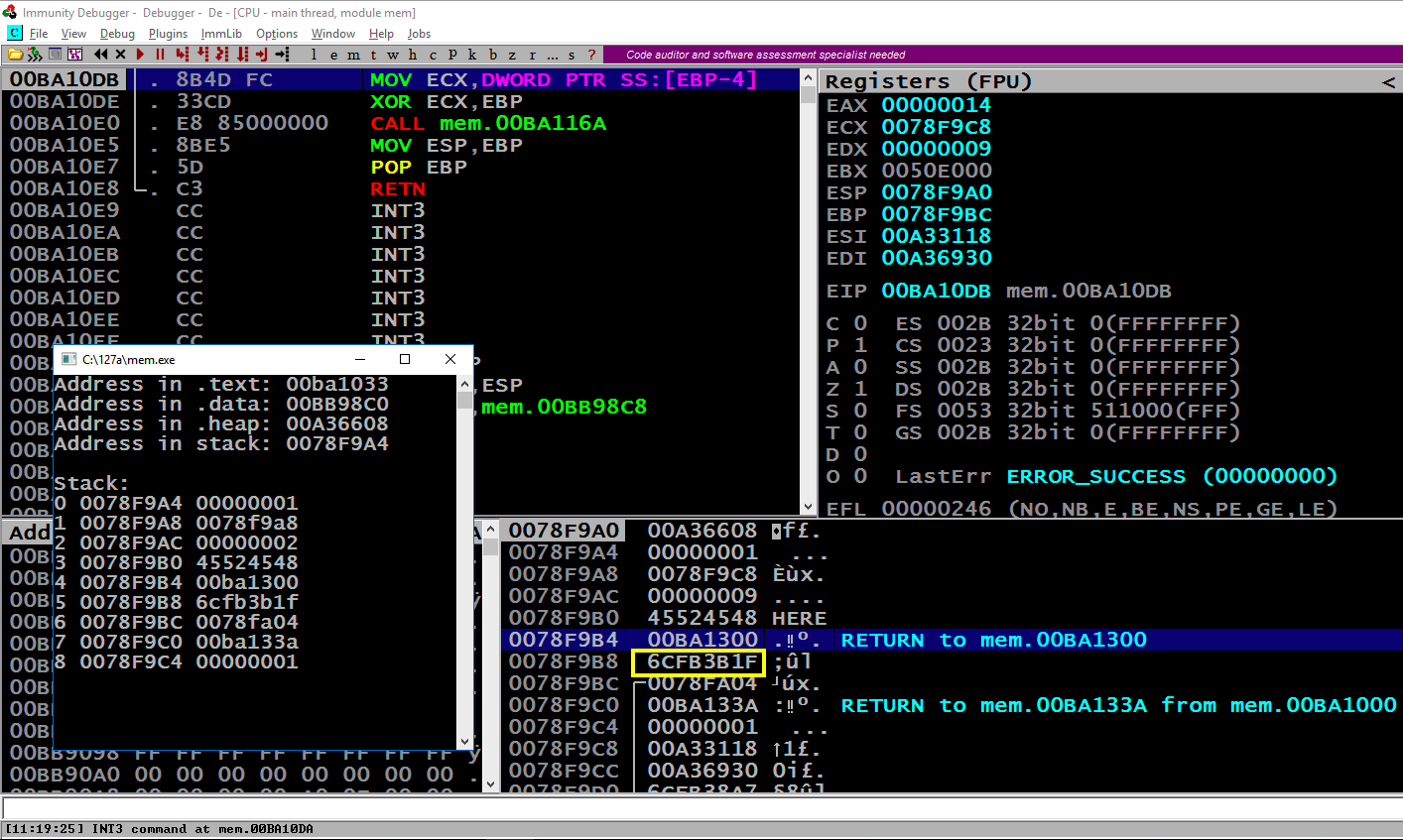
Close Immunity.
copy mem.cpp mem1.cpp
notepad mem1.cpp
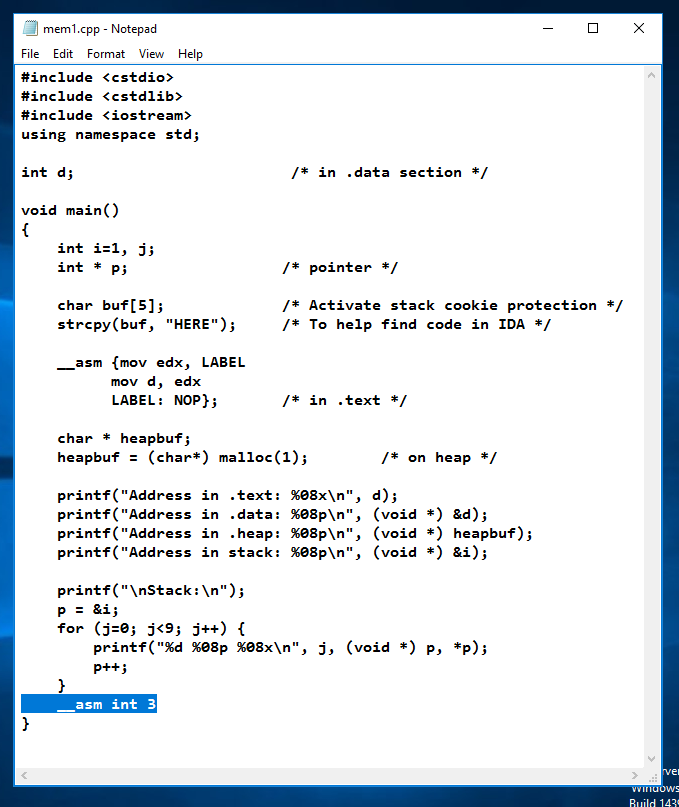
Save the file and close Notepad.
Execute these commands to compile the mem1 program with ASLR enabled, and with stack cookies.
cl /EHsc mem1.cpp
mem1.exe
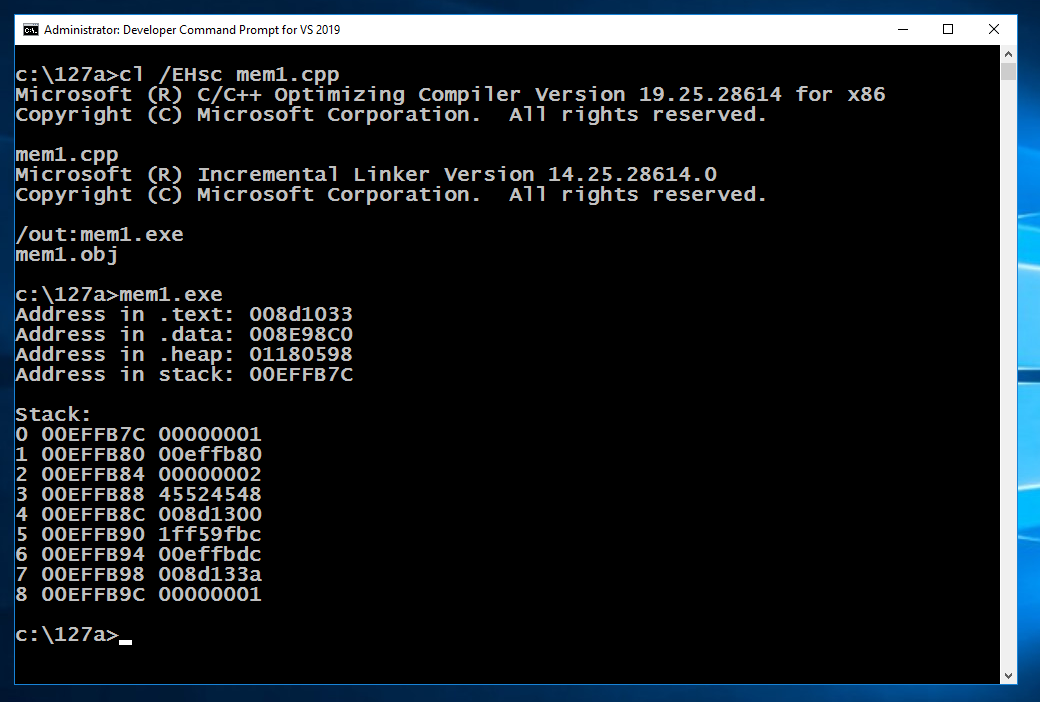
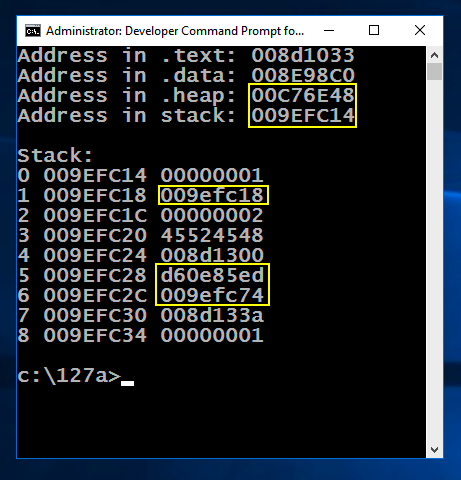
cls && mem1.exe
You should see the values outlined in yellow in the image below changing, while the other values stay the same.
Note these items:
copy mem1.cpp mem0.cpp
cl /EHsc /c /GS- mem0.cpp
link /DYNAMICBASE:NO mem0.obj
mem0.exe
Notice that the .text section is near the classical value of 400000, which we've seen before.
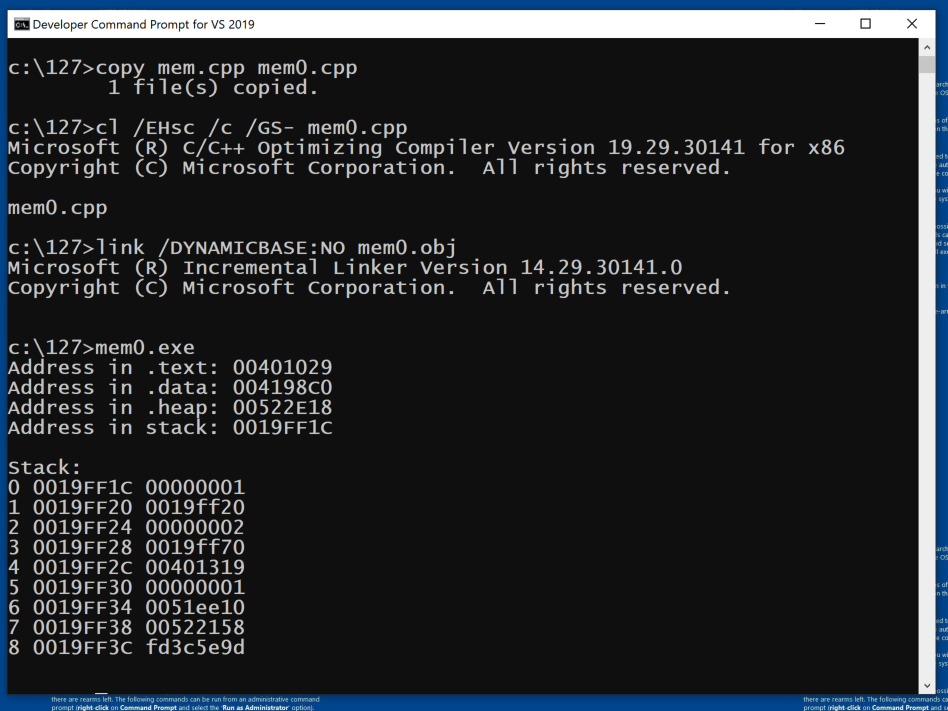
cls && mem0.exe
You should see the values outlined in yellow in the image below changing, while the other values stay the same.
Note these items:
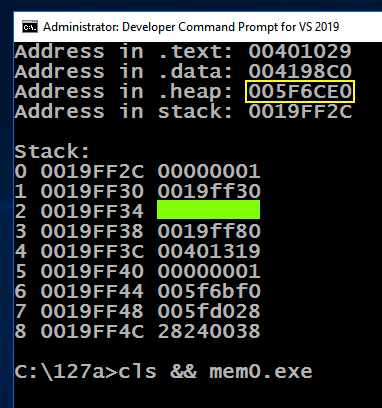
ED 303.2 Word 2 (10 pts)
Find the value of word 2 on the stack, covered by a green box in the image above. That's the flag.
Posted: 11-9-18
Typo in C code: i -> j 12-11-18
Updated extensively 4-25-2020
Updated for Windows 10 3-14-22
Win 11 notes and video added 5-5-25