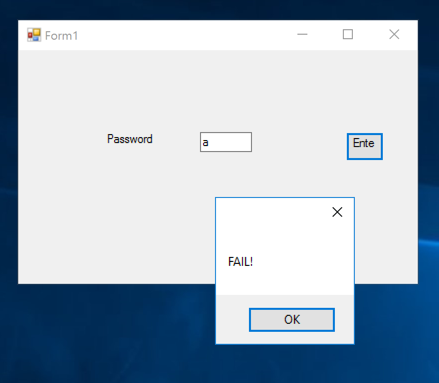
Double-click it to run it. It's a simple password-guessing game, as shown below.
If Windows Defender blocks the file, right-click it and click Properties. Click Unblock. Click OK.

Open this page:
https://www.red-gate.com/dynamic/products/dotnet-development/reflector/download
Download and install the software with the default options.
It will say it can't install the Visual Studio extension, that's OK.
In the "Welcome to .NET Reflector" box, click Close.
In the "Start 'Default' Assembly List" box, click OK.
In the ".NET Reflector 10.1 Trial" window, from the menu bar, click File, "Open Assembly...".
Navigate to the ED331-1.exe file and double-click it.
In the left pane of .NET Reflector, expand the "WindowsFormsApp5 (1.0.0.0)" container and the containers inside it and click the "button1_Click(Object, EventArgs) : Void" item.
The decompiled C# source code containing the password appears, as shown below.
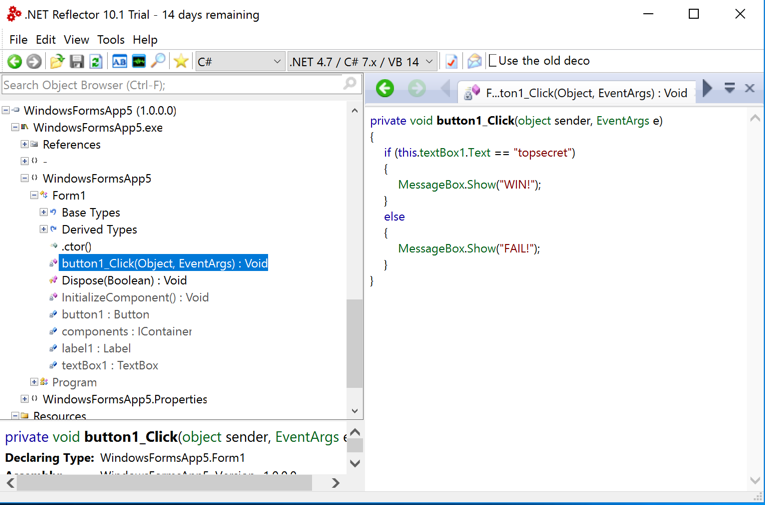
This is the actual code in a .NET app. It's in "Microsoft Intermediate Language" or MSIL, which is executed in a runtime environment named Common Language Runtime (CLR), and converted to x86 or x86-64 native instructions by a Just In Time (JIT) compiler.
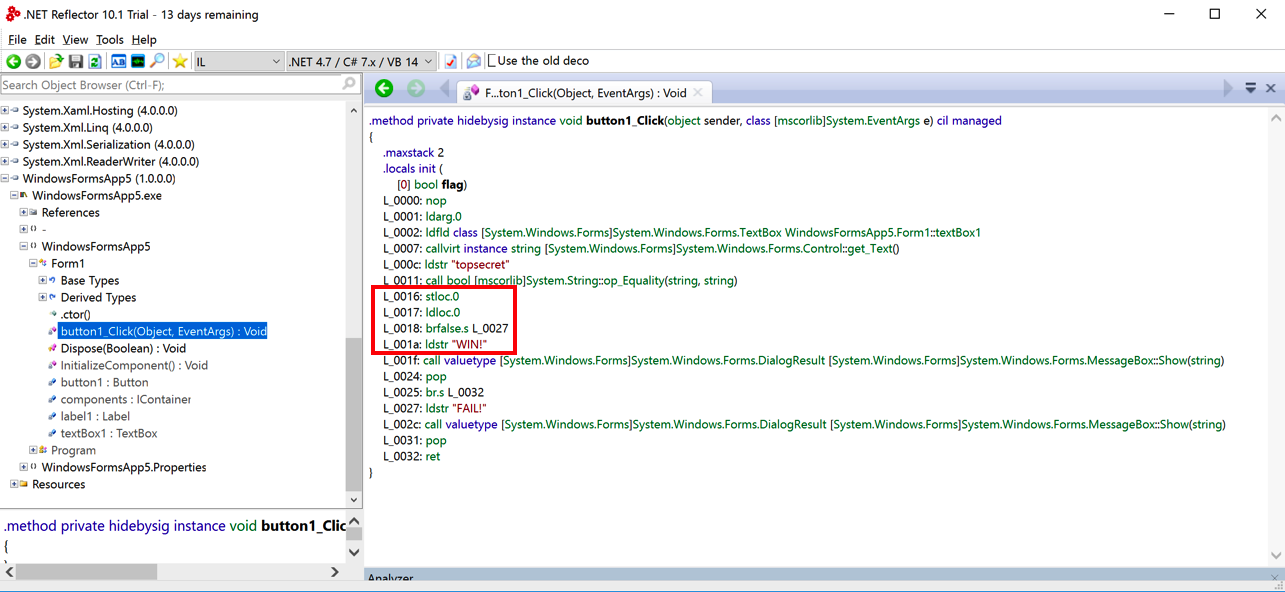
Notice the outlined instructions in the image above:
L_0016: stloc.0
L_0017: ldloc.0
L_0018: brfalse.s L_0027
L_001a: ldstr "WIN!"
stloc.0 0A
ldloc.0 06
brfalse.s 2C ??
ldstr "WIN!" 72 ?? ?? ?? ??
The hexadecimal code for "brtrue.s" is 2D, as you can verify on this list of MSIL hex codes:
https://en.wikipedia.org/wiki/List_of_CIL_instructions
https://mh-nexus.de/en/downloads.php?product=HxD20
Open the ED331-1.exe file.
Press Ctrl+F. On the Hex-Values tab, search for these hex values:
0A 06 2C
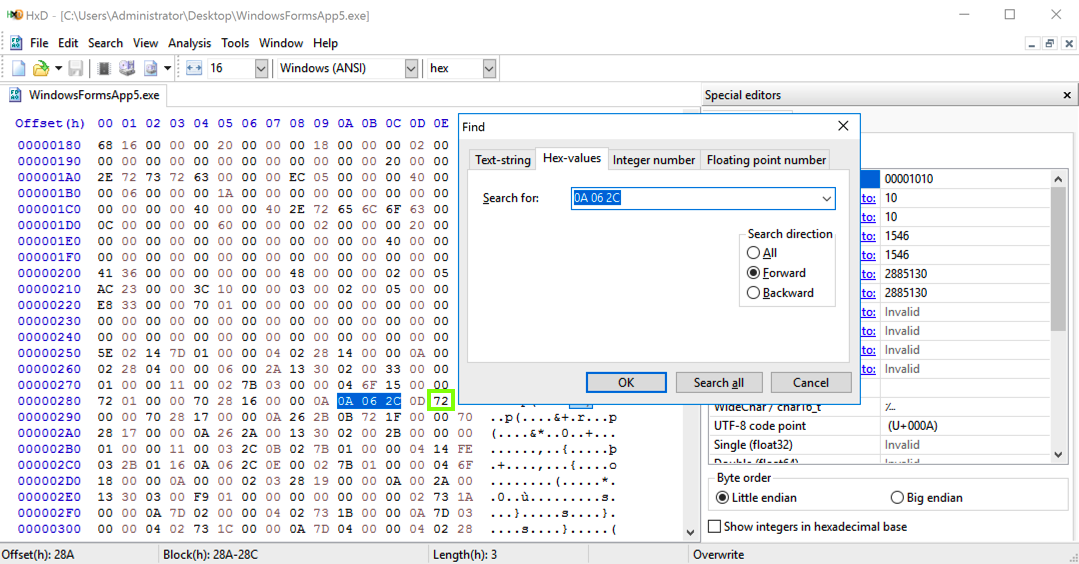
As shown above, brfalse.s is 2C. brtrue.s is 2D.
In HxD, click on the 2C byte and change it to 2D. That byte turns red, as shown below.
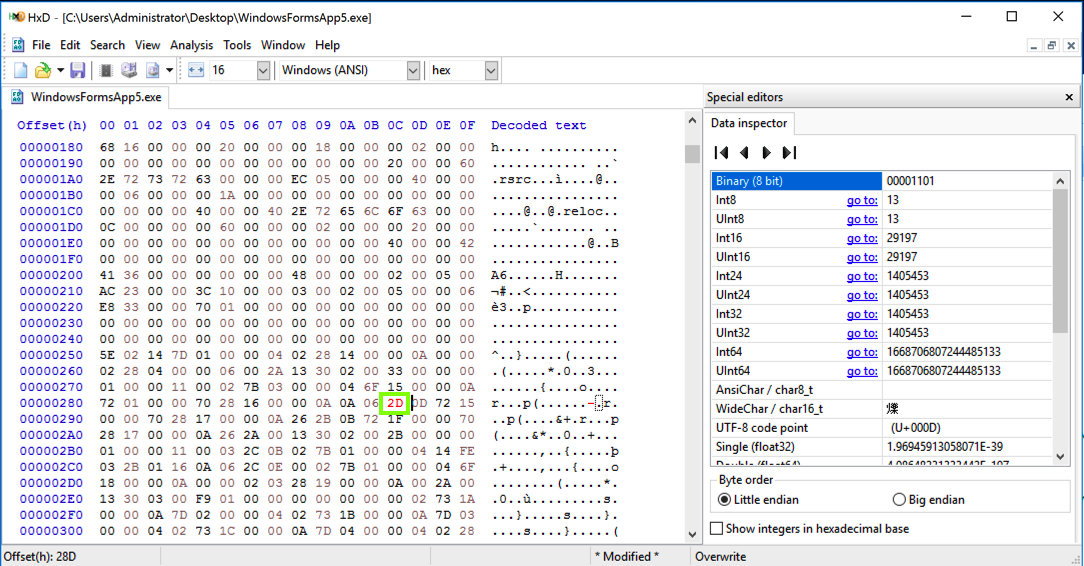
In HxD, from the menu bar, click File, "Save As...". Save the file on your desktop as WindowsFormsApp5mod.exe.
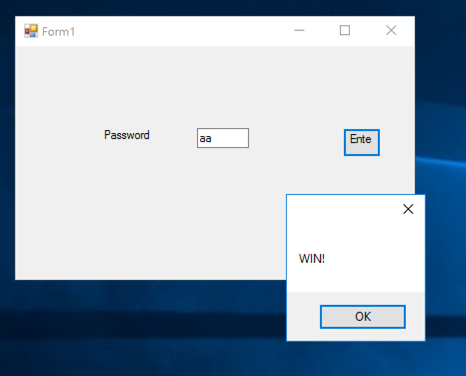
Enter any password, such as aa. You see "WIN!", as shown below.
Flag ED 331.1: CRC32 (10 pts extra)
You need to have 7-Zip installed. If you don't have it, get it here.In File Explorer, right-click the modified file you just made. Click "Show more options", 7-Zip, "CRC SHA", and CRC-32.
The flag is covered by a green rectangle in the image below.
Flag ED 331.2 (10 pts extra)
Download this file:Unzip it and analyze the ED331-2.exe app. Find the flag.
Flag ED 331.3 (5 pts extra)
From the archive you downoaded in ED 331.2, analyze the ED331-3.exe app. Find the flag.
Flag ED 331.4 (20 pts extra)
From the archive you downoaded in ED 331.2, analyze the ED331-4.exe app. Find the flag.
Posted 10-16-19
Typo fixed 10-30-19
Filename fixed to open in HxD 11-6-19
Tested with FLARE-VM 4-26-2021
Tested with Win 10 4-26-22
Tested with Win 11 ARM64 (failed) 4-4-23
Video added 4-5-23
Hashcalc reference removed 3-27-25
ARM64 note added 4-21-25